Hybrid Private Access Workflow
The Set up hybrid private access workflow shows you how to configure universal Zero Trust Network Access (ZTNA), in a sequence. Note that you can modify any part of the configuration, as required.
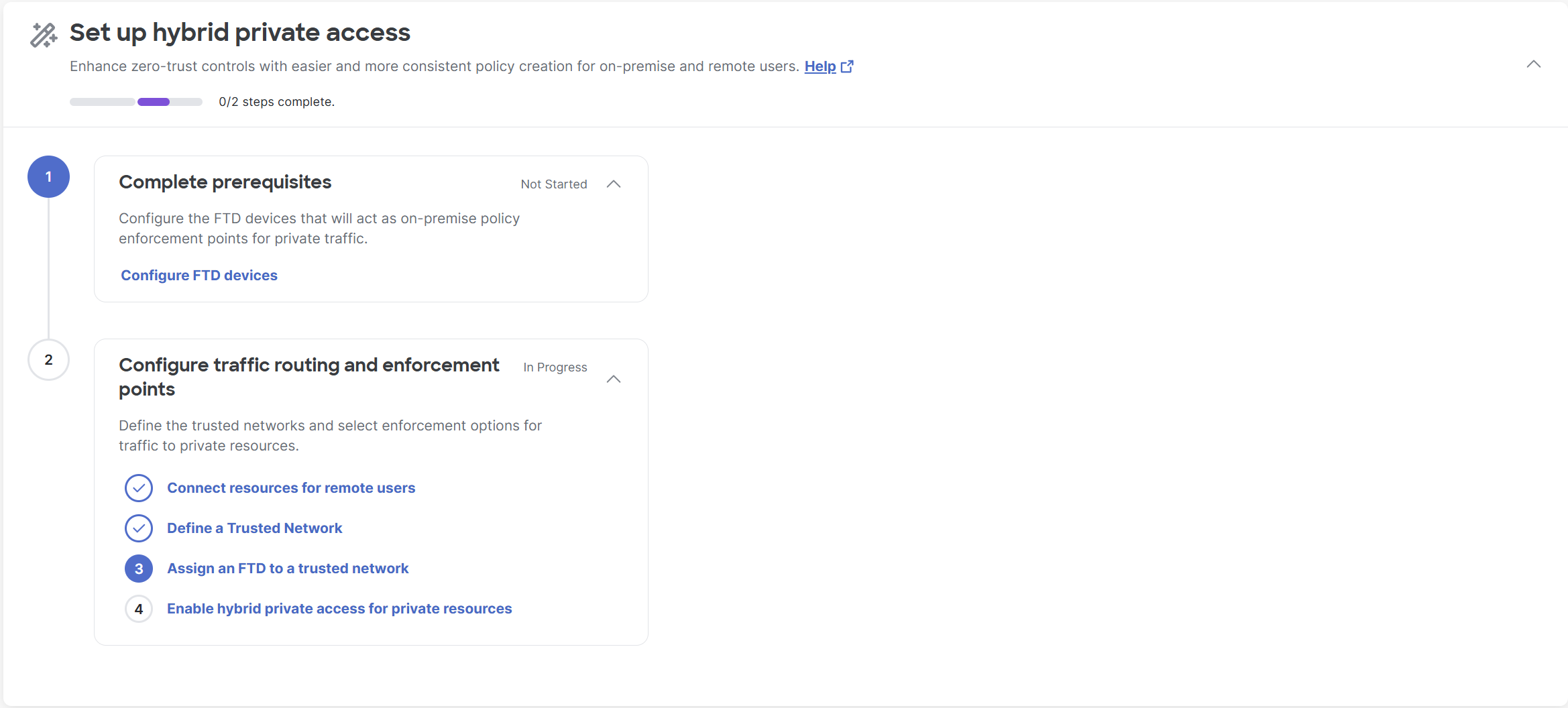
The Set up hybrid private access workflow consists of these broad steps:
- Configure FTD devices:
This step guides you through the process of configuring the Firewall Threat Defense devices in Security Cloud Control to enable universal Zero Trust Network Access. After configuration, the Threat Defense devices are displayed in Secure Access under Connect > Network Connections > FTDs, from where you can configure traffic routing and enforcement points. - Configure traffic routing and enforcement points. This step consists of four tasks:
- Connect resources for remote users:
This task guides you through the process of adding resource connector groups or network tunnel groups. A resource connector group supports remote network connections using Zero Trust Network Access to private resources. - Define a trusted network:
This task guides you through the process of adding trusted networks. These networks enable the system to recognize when an endpoint device is connected to a predefined trusted network, allowing the system to enforce security policies and control access to associated private resources. - Assign an FTD to a trusted network:
This task guides you through the process of assigning trusted networks to a Threat Defense device. In turn, the Threat Defense device enforces policies for the private resources associated with the assigned trusted network. - Enable hybrid private access for private resources:
This task guides you through the process of associating private resources with a Threat Defense device to ensure on-premises rule enforcement instead of on-cloud enforcement.
- Connect resources for remote users:
Prerequisites
To perform the steps in this wizard, you must have the Full Admin user role. For more information, see Manage Accounts.
Procedure
This procedure describes in detail, the steps listed in Set up hybrid private access.
-
Sign in to Security Cloud Control and navigate to Secure Access > Home.
-
Click Complete prerequisites.
-
Click Configure FTD devices.
The Onboard FTD Device page opens in a new tab. -
Configure the Firewall Threat Defense devices to be used for universal ZTNA.
For more information about onboarding Firewall Threat Defense devices using Firewall Management Center, see the "Register With the Management Center" section of the "Device Management" chapter in the Secure Firewall Management Center Device Configuration Guide.
For more information about onboarding Firewall Threat Defense devices using Cloud-Delivered Firewall Management Center(cdFMC), see Managing Firewall Threat Defense with Cloud-Delivered Firewall Management Center in Security Cloud Control.
For more information on configuring Firewall Threat Defense devices for universal ZTNA, see Configure Firewall in Security Cloud Control. -
Click Configure traffic routing and enforcement points.
-
Click Connect resources for remote users.
-
Add the required connector groups or network tunnel groups.
For more information on adding connector groups, see Manage Resource Connectors and Connector Groups.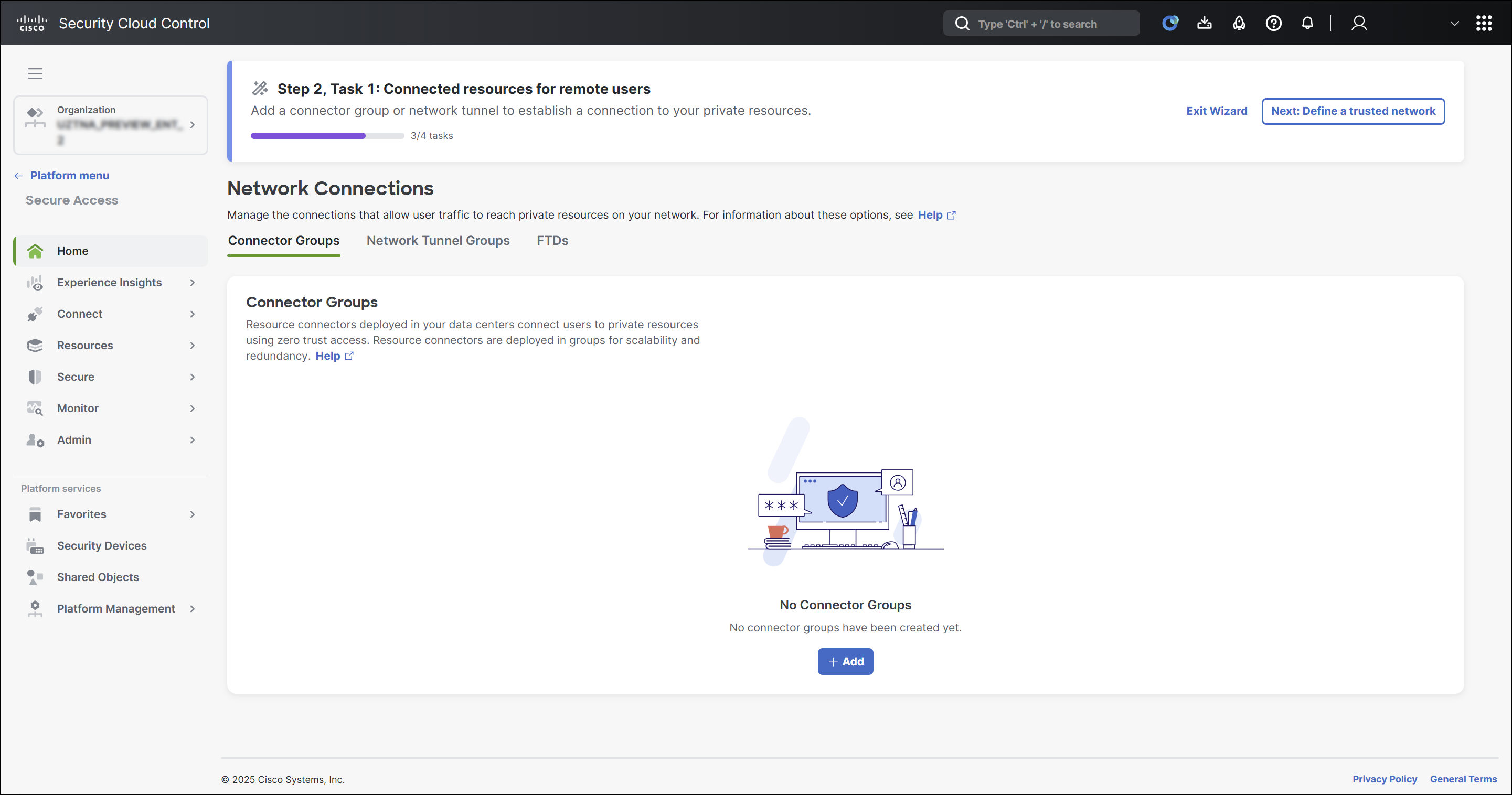
-
Click Next: Define a trusted network.
-
Define the required trusted networks.
For more information on defining a trusted network, see Trusted Networks for Zero Trust Access Connections.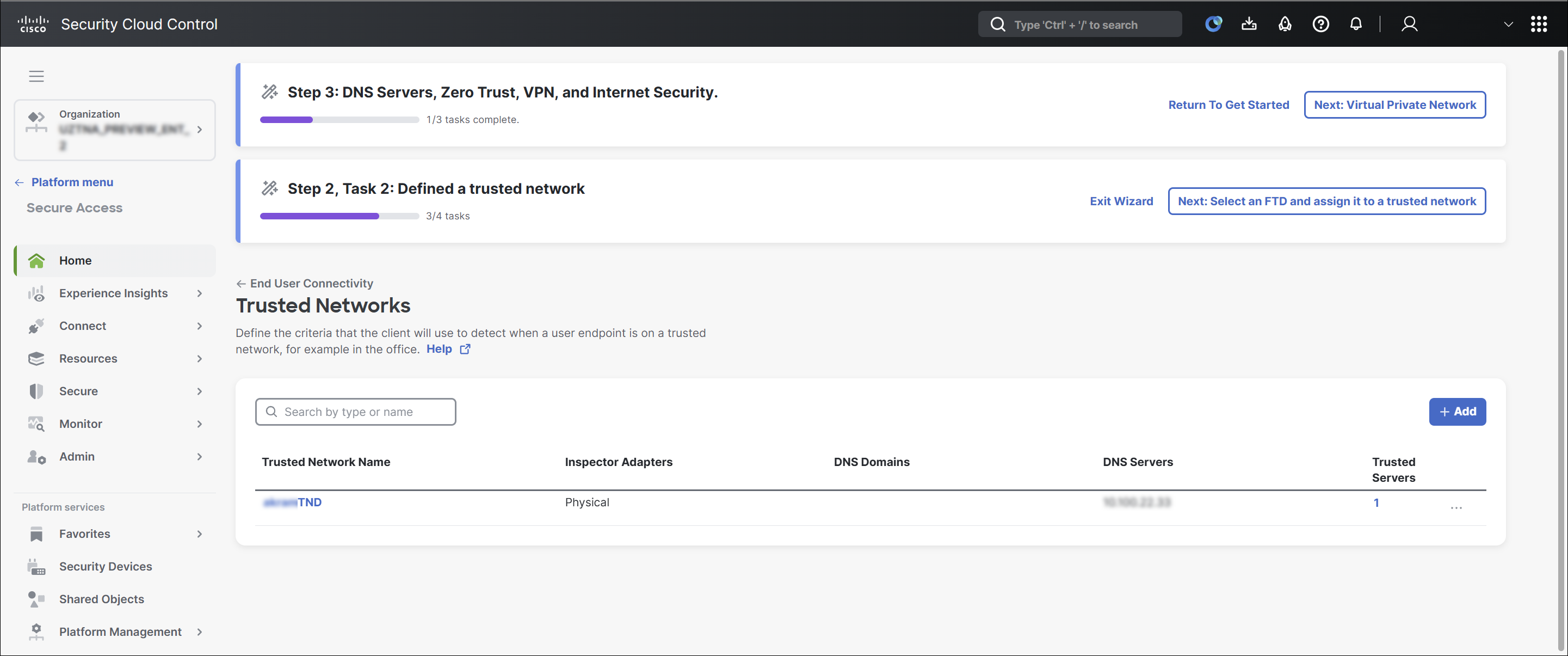
-
Click Next: Select an FTD and assign it to a trusted network.
-
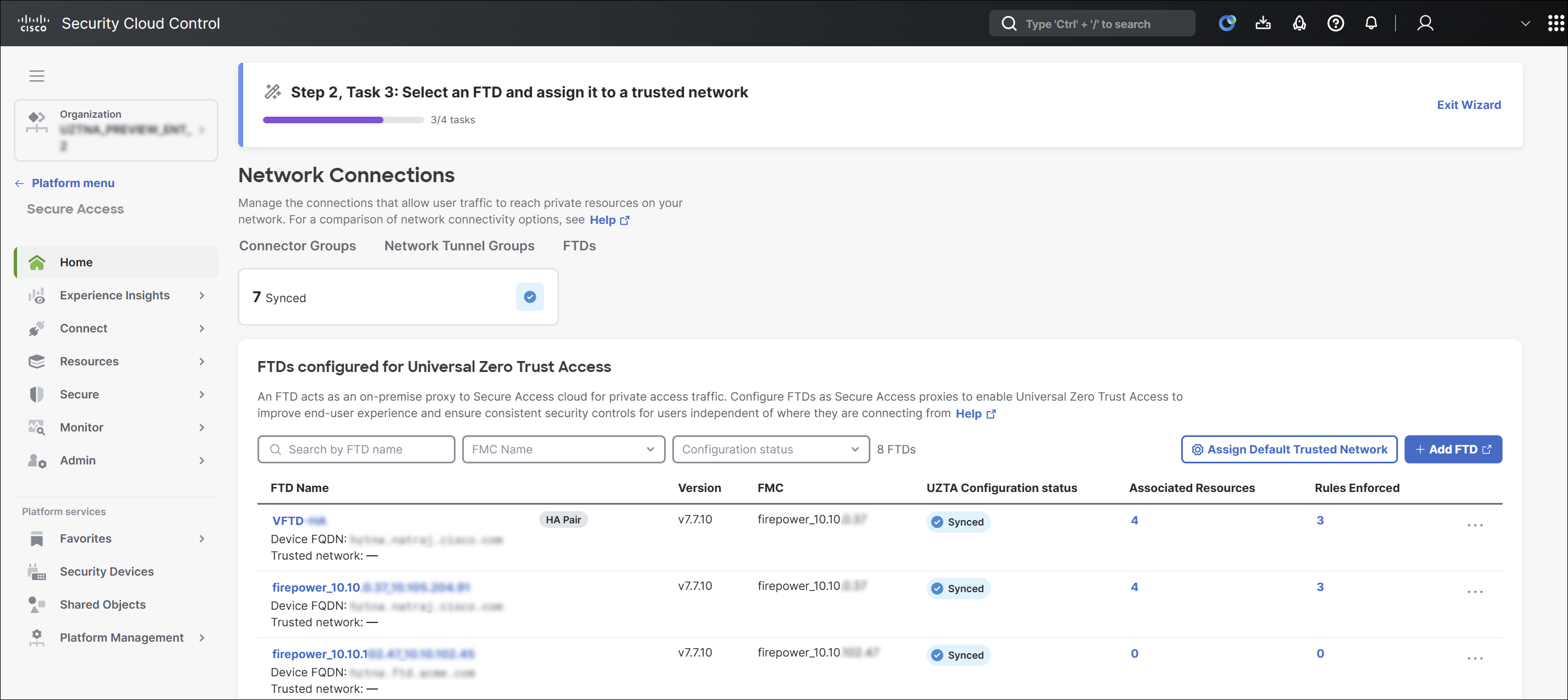
Assign trusted networks to the Threat Defense devices.
For more information on assigning trusted networks to Threat Defense devices, see Assign a Trusted Network to Threat Defense devices. -
Associate private resources with Threat Defense devices. For more information on associating private resources with Threat Defense devices, see Associate Private Resources with Threat Defense Devices.
-
Click Exit Wizard to close the wizard.
Secure Access Overview Dashboard < Hybrid Private Access Workflow > Quickstarts
Updated about 8 hours ago
