Virtual Appliance Deployment Guidelines
Cisco Secure Access supports various deployments and configurations of Secure Access Virtual Appliances (VAs).
Note: You must configure the Internal Domains for your organization. The endpoints must use the Secure Access Virtual Appliances as the primary DNS server.
Table of Contents
Deploy Virtual Appliances in Pairs
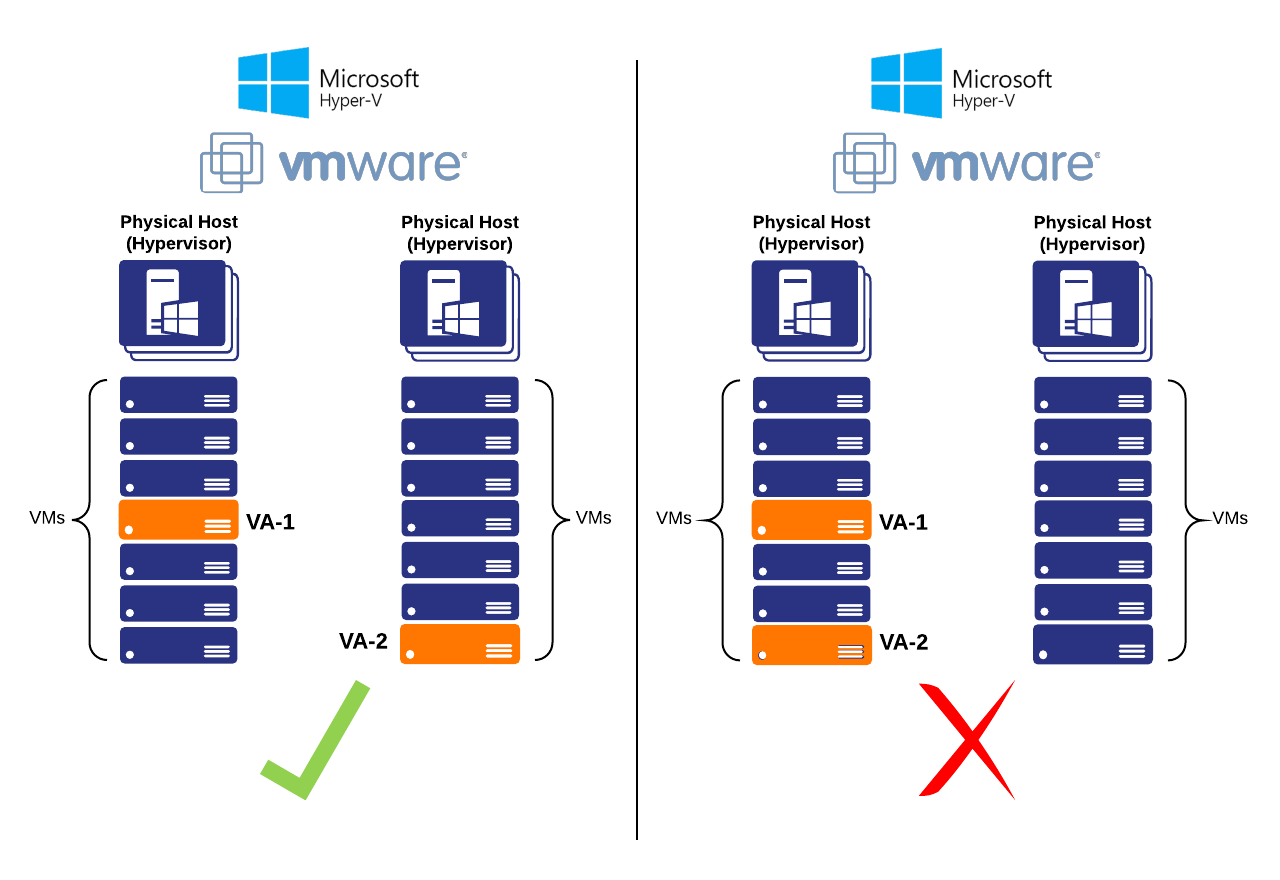
VAs must always be deployed in pairs. Running two or more VAs offers high availability in case of system updates. This ensures that there is no interruption in Internet service during an update, and allows you to configure updates for scheduled maintenance windows or off-hours.
- No downtime associated with upgrades
When an upgrade takes place, individual virtual appliances will restart, causing up to 20 minutes of downtime. During this time, any DNS queries routed to the virtual appliance will time out and you will lose internet connectivity. Running two VAs ensures that there is no interruption in Internet service. - Ability to schedule updates
Running two VAs allows for scheduling updates. You can schedule updates for off-hours or during scheduled maintenance windows. - High availability
If issues arise in one of your VAs, or if you would like to rebuild or move a VA to another host, you can take action without interruptions.
To set up a second virtual appliance, repeat the procedure for setting up the first one. For more information, see Deploy Virtual Appliances.
Whenever possible, deploy VAs on separate physical hypervisor hosts. If a hypervisor hosting a VA becomes unavailable, the second VA will continue serving DNS requests without interruption.
Multiple DNS Egresses
In most cases where multiple offices or points of presence exist, each office sends and receives its DNS traffic. An office independently sends DNS queries directly to Secure Access. In this case, each office requires its own pair of VAs. When using Secure Access, DNS queries always route to the closest Secure Access data center.
Single DNS Egress
In some cases, especially if the networks are geographically close to one another, a single egress may handle all DNS traffic originating from multiple networks. This topology is typically used to route traffic through security appliances, Active Directory Domain Controllers, or other network and security devices at a central location to avoid deploying and managing them at every location. This is usually accomplished with a Site-2-Site VPN or an MPLS circuit.
In this case, only the office which sends and receives public DNS queries requires VAs.
Double NAT
Endpoints and Virtual Appliances that are not behind the same Network Address Translation (NAT) address result in the VAs seeing the IP address of the NAT device instead of the endpoint's IP address.
With Secure Access Virtual Appliance deployments, we do not recommend a double NAT environment. A double NAT environment can limit both the ability to create granular rules and endpoint-level reporting in Secure Access. However, you can still create a separate rule for the NAT IP address, which would be useful for Guest Wi-FI situations, where knowing the endpoint IP address may not necessarily be helpful, but having a separate rule for that group of endpoints is important.
Prerequisites for Virtual Appliances < Virtual Appliance Deployment Guidelines > Virtual Appliance Sizing Guide
Updated 11 months ago
