Enable Logging to a Cisco-Managed S3 Bucket
You can configure Cisco Secure Access to log events to an Amazon S3 bucket, which is managed by Cisco.
Cisco configures all Cisco-managed buckets to use Amazon Server-Side Encryption with S3-Managed Keys (SSE-S3, AES-256). The encryption and keys are managed by Amazon. Cisco and the Secure Access user account (customer) don’t exchange keys, but the data is still encrypted at rest. More information about S3 buckets and encryption is available on the Amazon website by searching for "SSE-S3, AES-256”.
Secure Access provides access to Cisco-managed S3 buckets using Amazon's IAM system. When the S3 bucket is provisioned, Secure Access provides the S3 bucket's key and secret in the Admin > Log Management page. You must copy your S3 bucket key credentials to your environment. Secure Access does not store your keys during the generation process. If you lose your keys, you can not recover them. Instead, you must rotate the keys in Secure Access.
A Cisco user account can write files to the S3 bucket, and the customer IAM user can read from the S3 bucket. A customer IAM user can rotate their keys at any time.
Note: Customer logs are also encrypted in transit between Cisco’s log management infrastructure and Amazon S3.
Table of Contents
- Best Practices for Rotating an S3 Bucket Key
- Prerequisites
- Procedure
- Verify Your Access to an S3 Bucket
- Download Files From the S3 Bucket Locally
Best Practices for Rotating an S3 Bucket Key
Beginning on May 15, 2025, Secure Access requires that an organization with a Cisco-managed S3 bucket rotate the IAM key credentials on their S3 bucket every 90 days.
- Rotating IAM keys every 90 days only applies to Cisco-managed S3 buckets not self-managed S3 buckets. If your organization is unable to rotate the IAM keys on their Cisco-managed S3 bucket, we recommend that the organization uses a self-managed Amazon S3 bucket.
- If the IAM keys on a Cisco-managed S3 bucket are not rotated within 90 days from when the keys were last rotated, the organization will lose access to the Cisco-managed S3 bucket.
Note: Secure Access continues to log events to the Cisco-managed S3 bucket, but the S3 bucket is not accessible. - Secure Access provides periodic notifications about the expiry date of the IAM key on the Cisco-managed S3 bucket.
About the Notifications for the IAM Key
- Secure Access sends email notifications to the email account that was used during the initial purchase or renewal of your Cisco Secure Access license. If the organization does not rotate the IAM key, Secure Access sends email notifications on 30 days, 7 days, and then 1 day before the S3 bucket key will expire.
- If the organization does not rotate the Cisco-managed S3 bucket key, the organization loses access to the S3 bucket. When the S3 bucket key expires, Secure Access continues to log events to the organization's Cisco-managed S3 bucket.
- After you successfully rotate your S3 bucket key, Secure Access removes the IAM key notification on the Overview page.
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- To run the Amazon command-line interface (CLI) locally, install the AWS CLI in your environment. For information about installing the AWS CLI, see the Amazon S3 documentation.
Procedure
- Configure a Cisco-Managed S3 Bucket
- Rotate Keys on a Cisco-Managed S3 Bucket
- Get the S3 Bucket Data Path
Configure a Cisco-Managed S3 Bucket
In Secure Access, create a Cisco-managed Amazon S3 bucket to store the event logs for the organization.
- Navigate to Admin > Log Management, navigate to Amazon S3, and then choose Use a Cisco-managed Amazon S3 bucket.
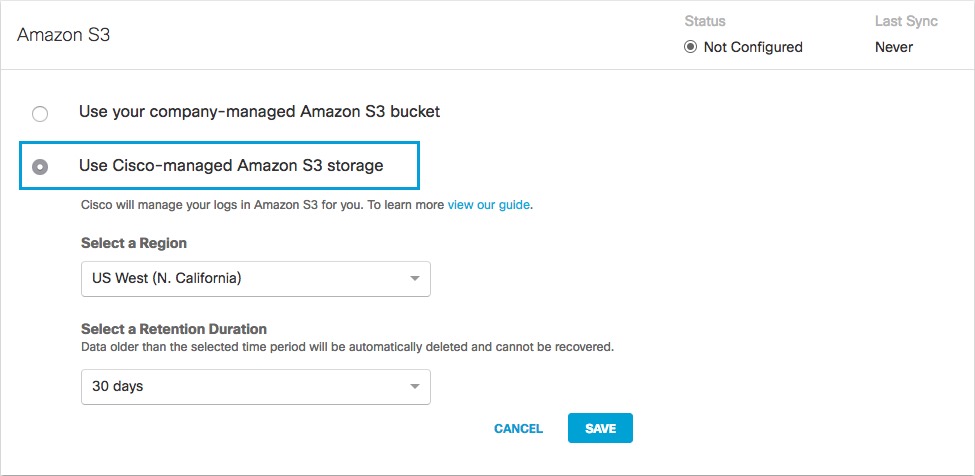
- Select a Region and a Retention Duration.
- Select a Region—Regional endpoints are important to minimize latency when downloading logs to your servers. The regions that are listed match those available in Amazon S3. Not all regions are available.
Pick a region that is closest to you. If you wish to change your region in the future, you will need to delete your current settings and start over. - Select a Retention Duration—Select 7, 14, or 30 days. Beyond the selected time period, all data will be purged and cannot be retrieved. We recommend a smaller time period if your ingestion cycle is regular. The retention duration can be changed at any time.
- Select a Region—Regional endpoints are important to minimize latency when downloading logs to your servers. The regions that are listed match those available in Amazon S3. Not all regions are available.
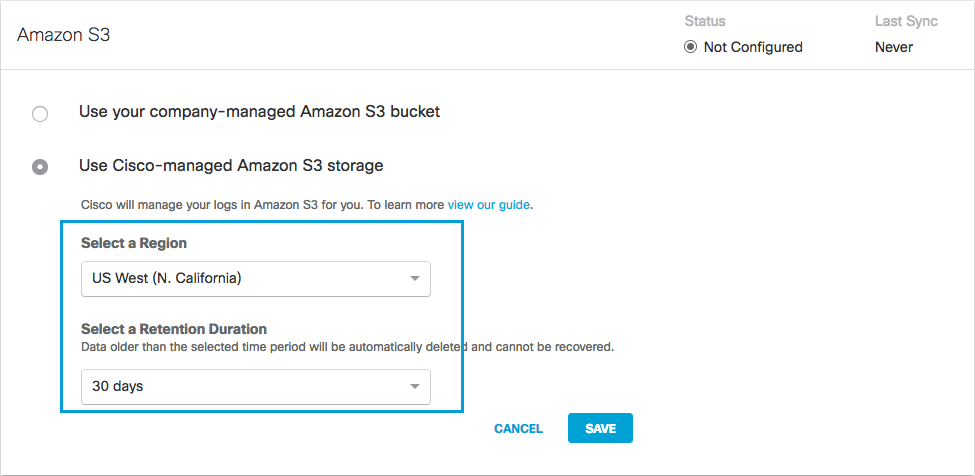
- Click Save and then Continue to confirm your settings.
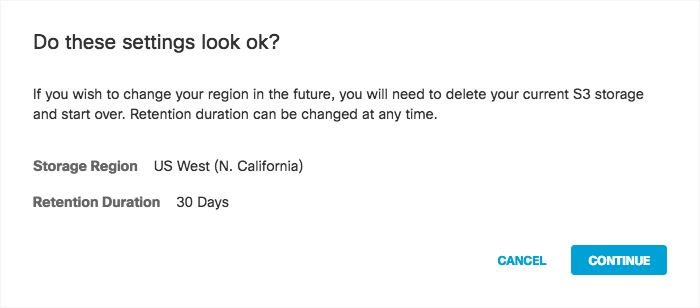
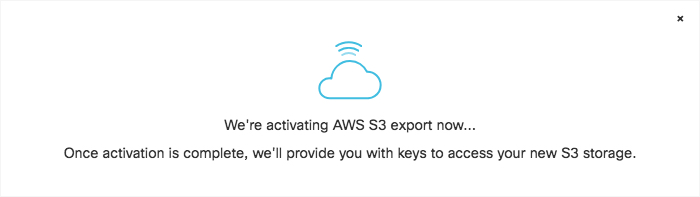
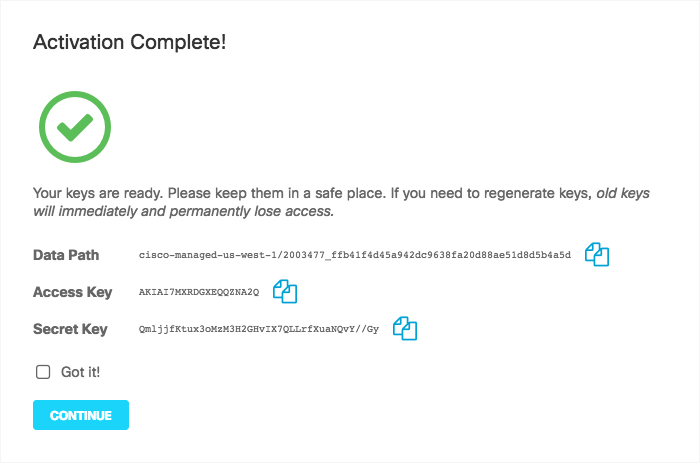
Secure Access activates its ability to export to an AWS S3 account. When activation is complete, the Amazon S3 Summary page appears.
-
Copy credentials from this page and store them in a safe place. This is the only time that the Access and Secret keys are made available to you. These keys are required to access your S3 bucket and download logs. If you lose these keys, they must be regenerated.
-
Once keys are copied and safe, select Got it and then click Continue.
Note: Continue is unavailable until you check Got it.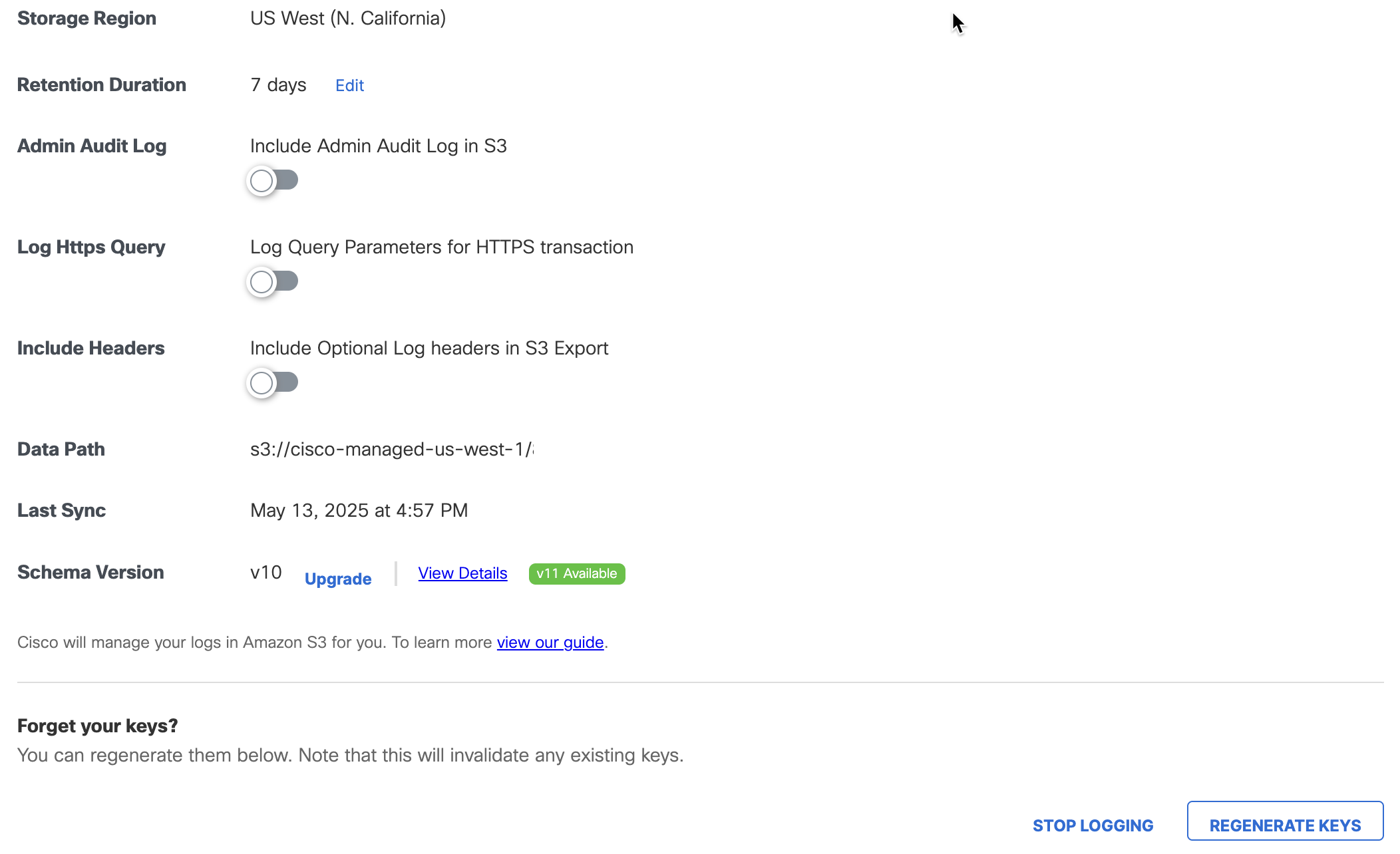
Rotate Keys on a Cisco-Managed S3 Bucket
Rotate the IAM keys on the Cisco-managed S3 bucket for the organization.
Note: Secure Access requires that the organization rotate the IAM keys on the Cisco-managed S3 bucket every 90 days.
-
In Secure Access, navigate to Admin > Log Management, and then navigate to Amazon S3.
-
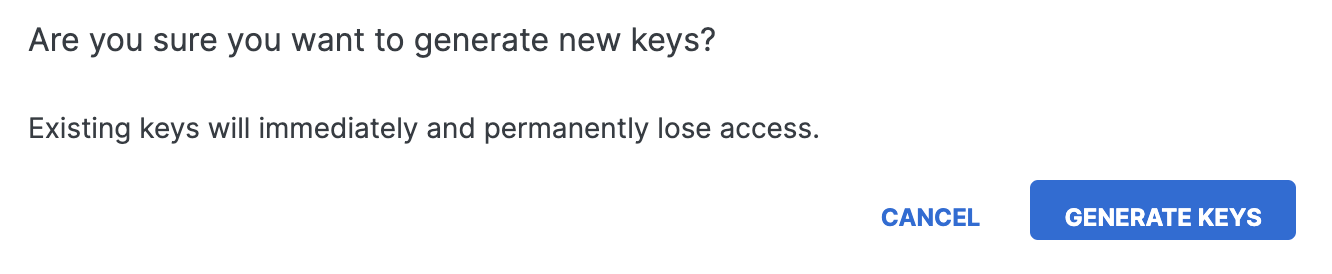
Click Regenerate Keys.
-
Click Generate Keys to confirm and update the IAM key on the Cisco-managed S3 bucket.
-
Copy the updated key and secret to your environment.
Note: After you regenerate the IAM keys on the Cisco-managed S3 bucket, copy the S3 bucket keys to any systems that integrate with the event logs from the Cisco-managed S3 bucket.
Get the S3 Bucket Data Path
The Secure Access Amazon S3 page provides a summary of the configured Cisco-Managed S3 bucket including the data path to your Amazon bucket.
- In Secure Access, navigate to Admin > Log Management, navigate to Amazon S3.
- Navigate to Data Path. The data path to your Amazon bucket is composed of several fields.
<AWS S3 bucket name>-<AWS region>/<AWS S3 bucket directory prefix>- AWS S3 bucket name and AWS region—the name of the AWS S3 bucket managed by Cisco (
cisco-managed), a dash (-), and the AWS region. - AWS S3 bucket directory prefix—the directory prefix (customer folder name) to the Cisco-managed AWS S3 bucket.
- AWS S3 bucket name and AWS region—the name of the AWS S3 bucket managed by Cisco (
Sample S3 Bucket Data Path
cisco-managed-us-west-1/2069997_6ff2802af17337def701c2e7816cf14913zf848a
Use the data path to your Cisco-managed S3 bucket to:
- Download log files with the AWS CLI.
- Set up your Cisco-managed S3 bucket with the Cisco Cloud Security App for Splunk. The Cisco Cloud Security App for Splunk enables you to analyze your Secure Access logs found in your AWS S3 bucket. For more information, see Cisco Cloud Security App for Splunk.
Verify Your Access to an S3 Bucket
To verify that you have access to a Cisco-managed S3 Bucket, you can configure the AWS CLI with your newly generated keys.
- In a shell, run
aws configure.
AWS Access Key ID [None]:
AWS Secret Access Key [None]:
Default region name [None]:
Default output format [None]: - List one of the saved logs in your Cisco-managed S3-Bucket.
- For example, run:
aws s3 ls s3://cisco-managed-us-west-1/<org_id>/<s3-bucket-instance>/dnslogs -recursive aws s3 ls s3://cisco-managed-us-west-1/<org_id>/<s3-bucket-instance>/auditlogs -recursive
Download Files From the S3 Bucket Locally
You can use the Amazon command-line interface (CLI) to download files from a Cisco-managed S3 bucket to your local directory.
Run the AWS CLI to download your files from a Cisco-managed S3 bucket to your local directory. To run the AWS CLI command in test mode (without syncing files), use the --dryrun flag.
AWS CLI command syntax:
aws s3 sync s3://DATAPATH/ /path/to/local/directory/
Note: You must append a forward slash (/) to the DATAPATH.
Sample Command
aws s3 sync s3://cisco-managed-us-west-1/2069997_6ff2802af17337def701c2e7816cf14913zf848a/ /opt/splunk/etc/apps/TA-cisco_umbrella/data/
Best Practices: Download Files From the S3 Bucket
- When you download files from a Cisco-managed S3 bucket, ensure that you only download one copy of each log file. If you download log files multiple times, Cisco reserves the right to suspend the download of logs from a Cisco-managed S3 bucket (through the rotation of keys or other methods).
- Once files are downloaded to a local directory, you can delete the files. Only delete files that are older than the Retention Duration value configured in Secure Access. Otherwise, the next sync command will download the deleted files again.
Enable Logging to Your Own S3 Bucket < Enable Logging to a Cisco-managed S3 Bucket > Change the Location of Event Data Logs
Updated 2 months ago
