Troubleshooting
Check the scenarios below if you have difficulty validating the Secure Access module for Cisco Secure Client for Android OS after first installing it.
Table of Contents
- First Launch of App
- Is this a VPN to Secure Access?
- An Internal Site Isn’t Loading
- Configuration Issues
- Check for VPN Connection and Policy
- Check Block Page
- Get the Android ID
- Fail Close/Open Scenario
- Check Device Registration
- Missing CA Certificate
- Org ID on Policy Page is 0
- App Installation is Blocked
- Offboarding Users
- Known Issues
First Launch of App
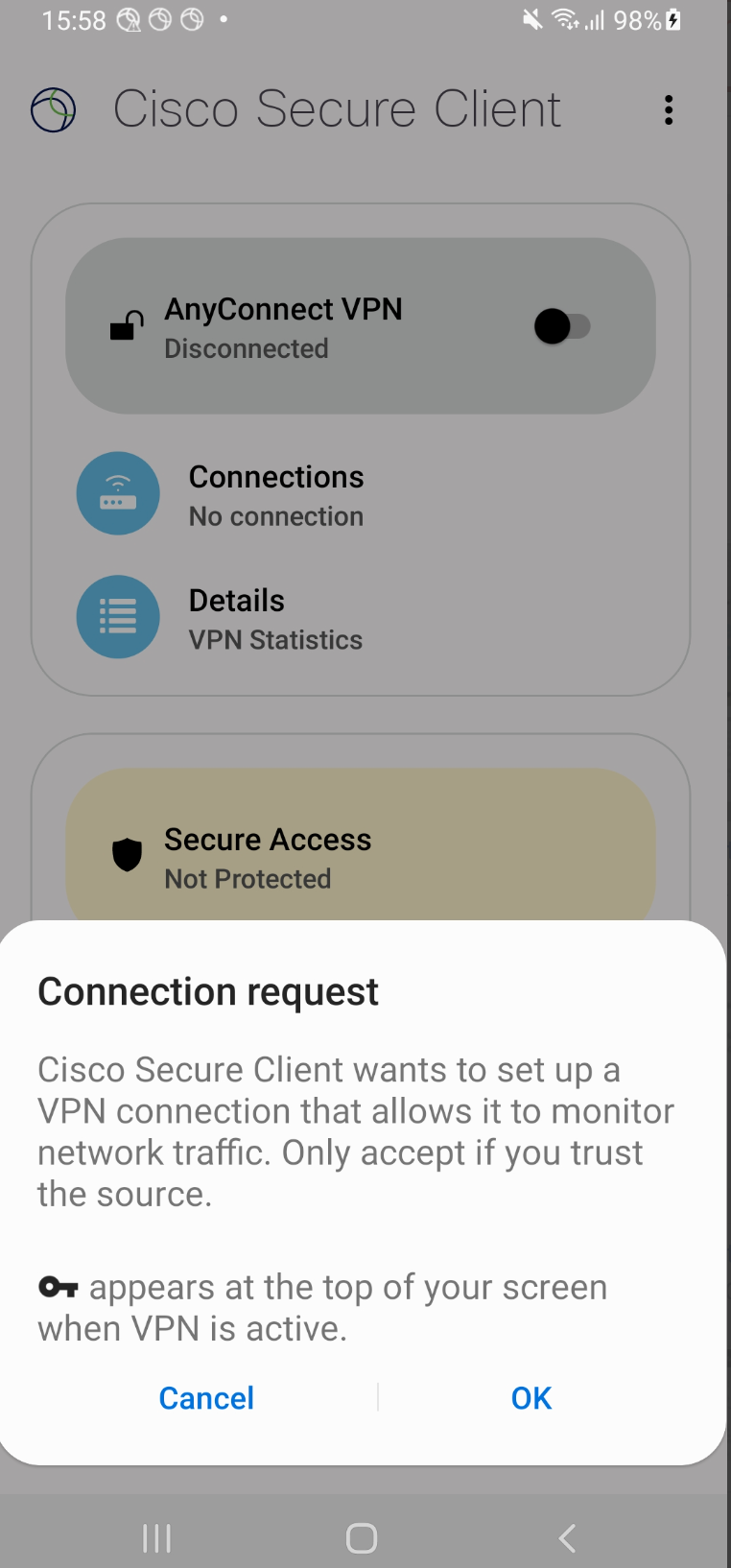
On the first launch, there should be a request for Cisco Secure Client VPN session as shown below. You must accept the connection request by clicking “OK” for the Secure Access protection to start.
Mandatory Security Step
This cannot be bypassed; the behavior is built into Android OS for security reasons.
Is this a VPN to Secure Access?
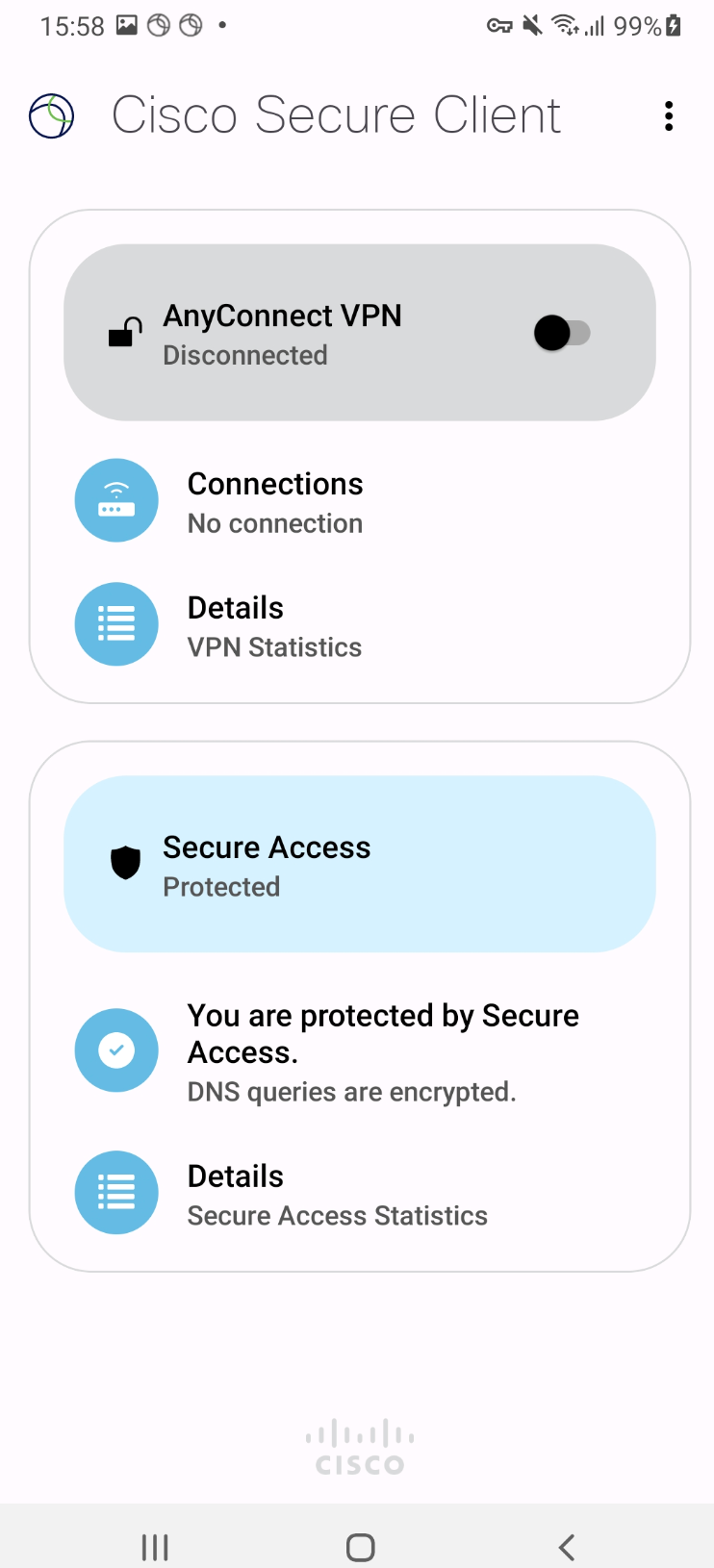
The Secure Access Module for Cisco Secure Client uses a VPN-like mechanism, but it is not in a traditional VPN. This VPN-like mechanism is used to intercept DNS queries so that the module can process them (add metadata, encrypt and forward to Secure Access). The Android operating system’s user interface does not show this distinction, so it appears as if a VPN were running.
When Secure Access protection starts, a green checkmark appears under the Secure Access UI subheading with the text “You are protected by Secure Access.”
Virtual Appliance in the Network
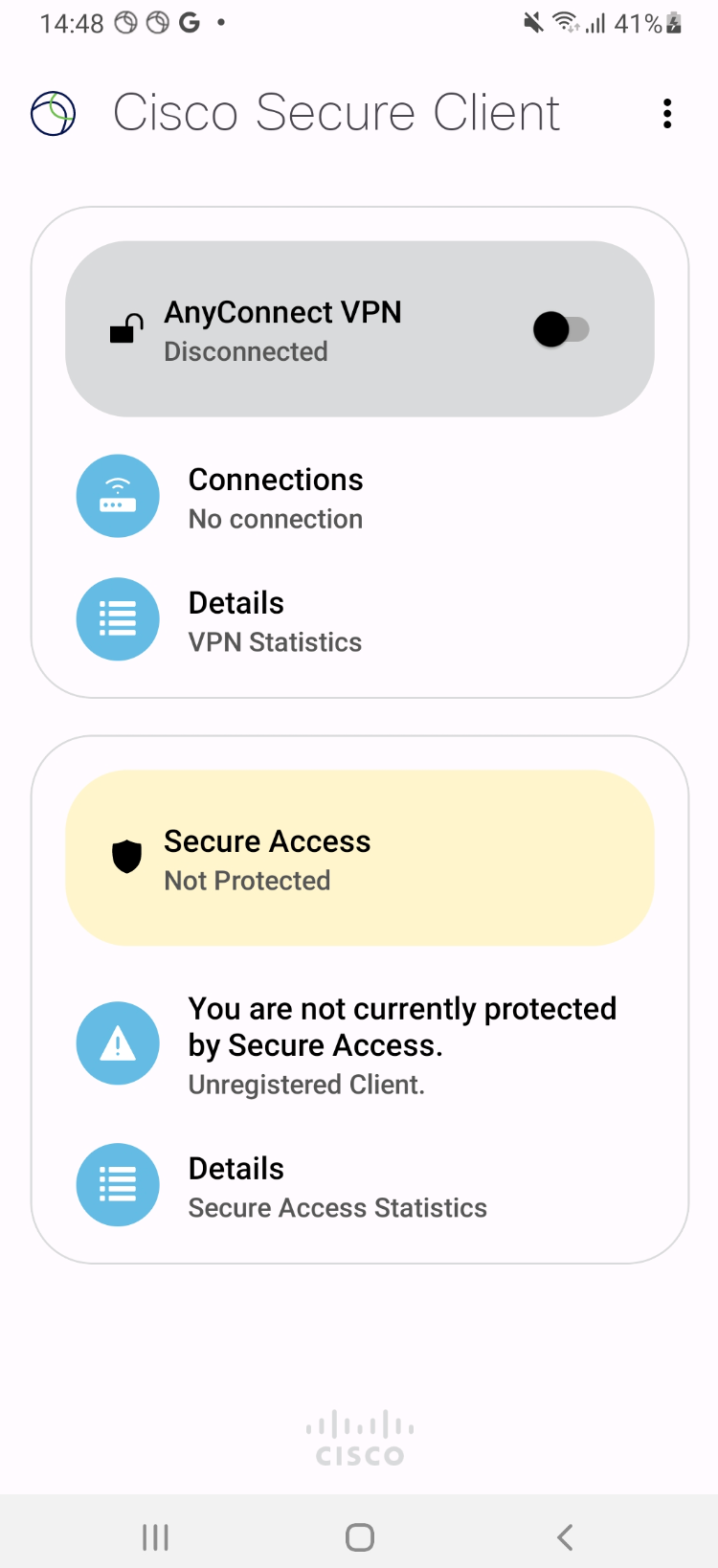
If an Secure Access Virtual Appliance (VA) supporting HTTPS is configured in the network, the Secure Access module detects this and backs off. If a VA is not present, or is present but does not support HTTPS, then the Secure Access module remains active.
An Internal Site Isn’t Loading
The Secure Access module makes a best effort to automatically detect internal (intranet) sites and route DNS appropriately to the local DNS server. However, these mechanisms may not work in all scenarios. Therefore it’s important to enter your internal / intranet domains in the Domain Management tools in the Secure Access dashboard. For more details, refer to Manage Domains.
Configuration Issues
If the Secure Access Section in the Cisco Secure Client - AnyConnect app does not display a green checkmark, check the configuration details pushed from the MDM. If you don’t have access, contact your administrator.
You can check if the configuration is available by clicking on the menu button at the top right in Cisco Secure Client - AnyConnect > Diagnostics > Logging and System Information > System > Managed Configuration.
Verify that the managed configuration pushed by the administrator is available.
Check for VPN Connection and Policy
- Verify that the “key” icon (or something similar) is displayed in the notification panel for the VPN session created by Cisco Secure Client - AnyConnect.
- Open a browser.
- Clear the cache.
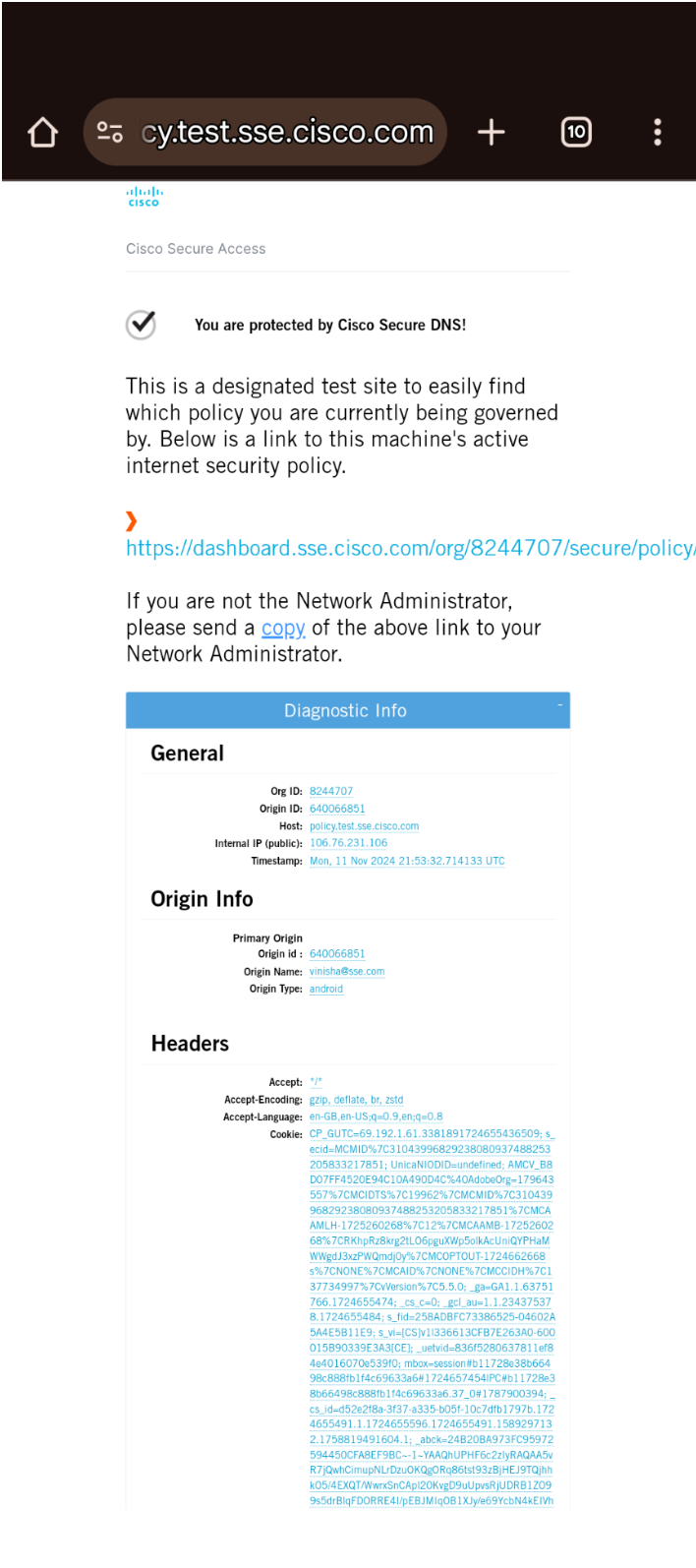
- Load
https://policy.test.sse.cisco.com/. The page should load and display a URL to the active policy in the Secure Access dashboard. The format of the URL should be:https://login.sse.cisco.com/o/<orgid>/#/configuration/policy/<policyid>. - Verify that the organization ID displayed in the URL is the same as your Secure Access organization ID.
Check Block Page
Open http://www.internetbadguys.com/. You should see an Secure Access block page displaying the domain that was blocked along with the IP address of your device and the reasons for blocking. If you do not see the Secure Access block page, follow these steps:
- Select Settings > Apps > Cisco Secure Client - AnyConnect > Force Close.
- Restart Cisco Secure Client - AnyConnect.
- Reopen
http://www.internetbadguys.com/and check for the Secure Access block page.
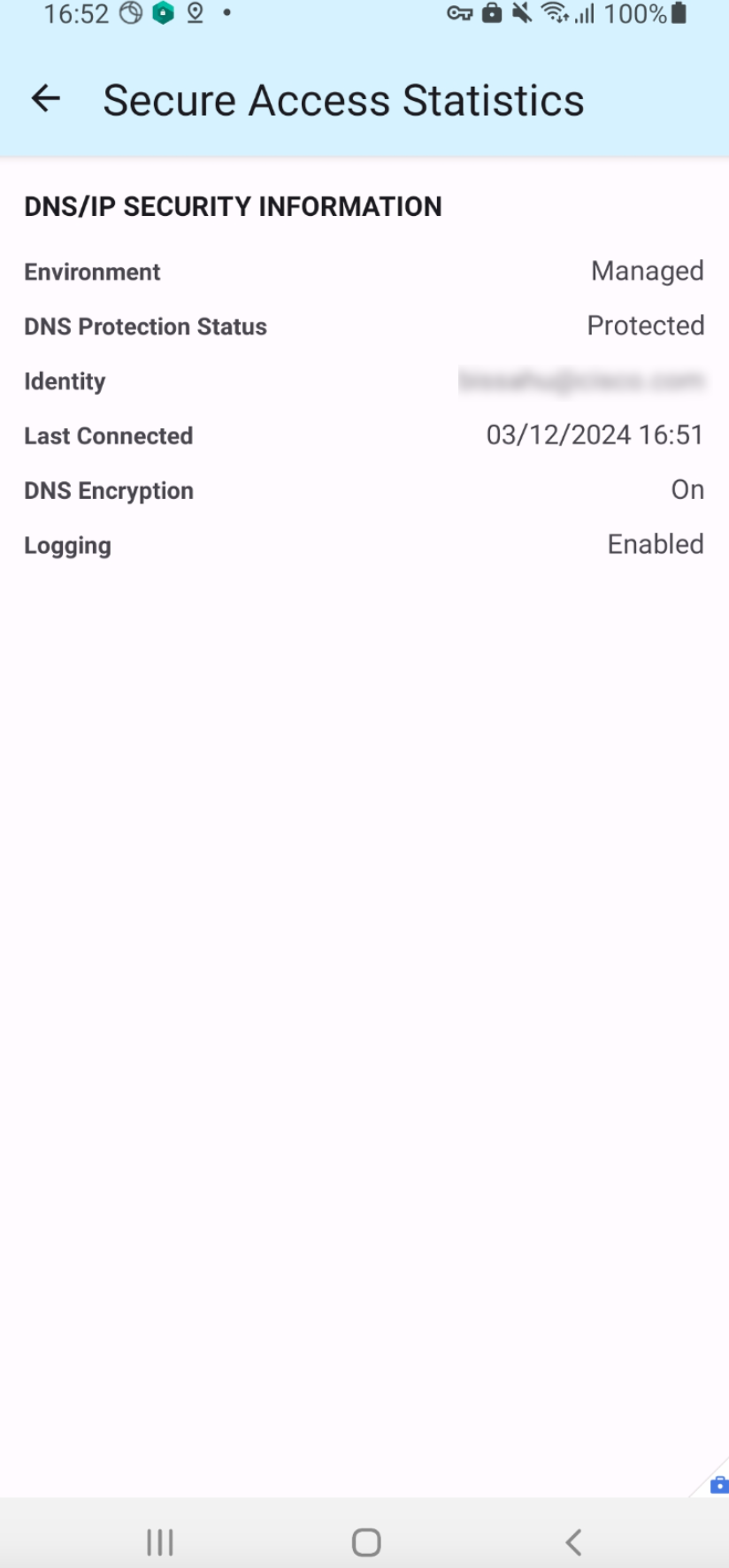
Get the Android ID
- Launch Cisco Secure Client.
- Open Secure Access Security.
- Click Options, then open Secure Access Statistics. The Android ID is listed in that window.
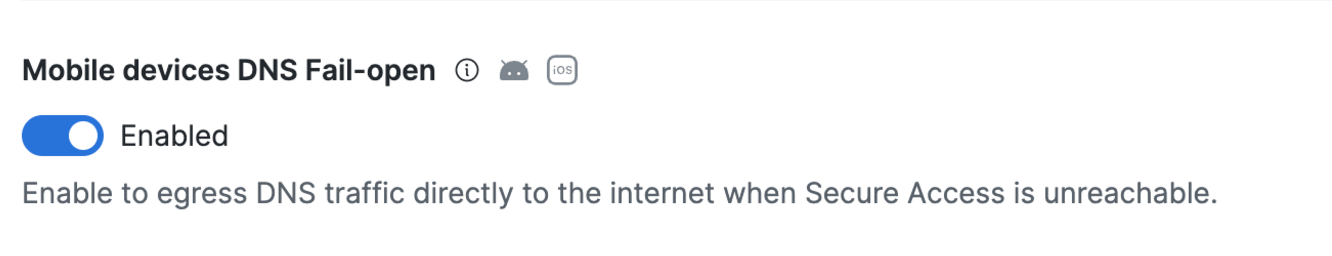
Fail Close/Open Scenario
Navigate to Cisco Secure Client settings > Advanced, and enable the Mobile devices DNS Fail-open field to egress DNS traffic directly to the internet when Secure Access is unreachable.
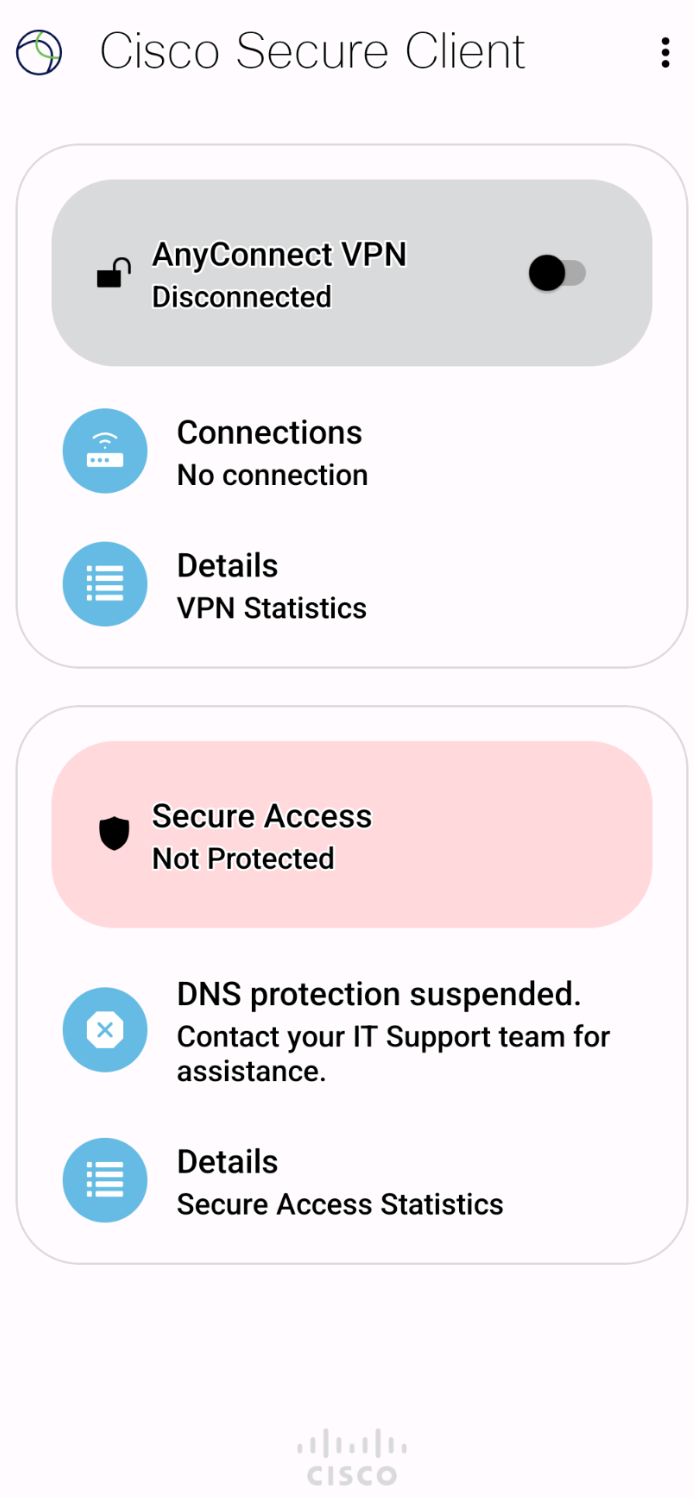
In case of internal errors, such as the Secure Access Resolver is not reachable or the DNSCrypt Certificate is not available, the Secure Access UI displays an error.
Check Device Registration
- Find the
android_idfor your Android device. - Login to
https://login.sse.cisco.com/, - Choose the
org idassociated with the device. - Navigate to Resources > Roaming Devices > Mobile Operating Systems.
- Verify that the
android_idis listed.
Missing CA Certificate
If the Secure Access block page is not displayed but you see, instead, a warning about an insecure page, then there might be an error due to a missing Secure Access root certificate.
- Download the Cisco Secure Access root certificate. For more information about downloading the root certificate, Install the Cisco Secure Access Root Certificate.
- Secure the device with your PIN, password or pattern lock.
- Install the certificate you downloaded.
- Select the certificate file.
- Reload the block page in your browser.
Org ID on Policy Page is 0
If the https://policy.test.sse.cisco.com/ URL shows 0 for the org id and bundle (policy) id, then refresh the page. Alternatively, clear the browser cache, try an incognito window, or try a different browser.
App Installation is Blocked
In order to download apps from the Google Play Store, a Gmail ID should be configured in the MDM. If the ID is configured and the app still cannot be downloaded, the MDM admin may have chosen to disallow installation of apps from the Play Store.
Offboarding Users
In order to fully remove an end user there are two steps:
- Delete the user from the Mobile Devices page in the Secure Access Dashboard.
- Delete the Cisco Secure Access Module for Android OS from the user's device. This can be done by the MDM. The MDM app itself need not be removed from the user's device.
Known Issues
- App download fails in Google Play Store after enabling Cisco Secure client. This is a known limitation from Google on Android OS versions below v10. To avoid this, you must download Apps before enabling the Secure Access App. Google has fixed this behavior in their Android OS 10. Check the issue tracker.
- In Android 10 and later, Google restricts reading serial numbers from the device. As a result, the Serial number field in the Secure Access dashboard displays “unknown” for Android 10 and later devices.
- Avoid using the Wifi Assistant; it may conflict with Cisco Secure Client - AnyConnect and DNS interception.
- Private DNS must be turned off for DNS interception to function properly.
- Click for information about Unusual DNS queries showing in reports.
- Huawei phones, when running in Work Profile mode, do not automatically start Cisco Secure Client - AnyConnect, even when the app was previously open. This does not apply to Huawei phones in Fully Managed mode.
Export Device Data to CSV < Troubleshooting > Frequently Asked Questions
Updated about 1 month ago
