Add Customer CA Signed Root Certificate
You can use a certificate signed by your Certificate Authority (CA) to enable secure connections between user devices in your organization and Cisco Secure Access.
A root certificate is required for Block Pages and Internet Decryption.
- For Block Pages, if you visit a blocked domain through HTTPS, a certificate must be installed so that Secure Access presents a block page rather than a browser error. For more information, see Manage Notification Pages.
- For HTTPS decryption and inspection, if a domain is proxied, install a certificate so that Secure Access can decrypt HTTPS traffic without the browser presenting an error. For more information, see Manage Traffic Decryption.
You can use either the Cisco Secure Access root certificate or your own CA-signed certificate. To use your own CA-signed certificate, upload a certificate signed by your CA to Secure Access.
Table of Contents
Prerequisites
- A Certificate Signing Request (CSR) file downloaded from Secure Access.
- Microsoft Certificate Services, Active Directory Certificate Services, or OpenSSL to sign the CSR with your CA.
Certificate Requirements
When you issue a certificate signed by your own CA, you must meet the following requirements:
- The encoding must use UTF8String.
- You must use the same character encoding for all certificates in your certificate chain.
- The “Subject Name” in the CSR file downloaded from Secure Access must be honored.
- The certificate must be valid for no more than three years.
- The certificate must be an X509v3 certificate with an RSA public key not less than 2048 and no more than 4096.
- Use one of the following signature algorithms:
- SHA256withRSA
- SHA384withRSA
- SHA512withRSA
- Include the following X509v3 extensions:
- X509v3 Basic Constraints marked as critical: CA:TRUE
- X509v3 Key Usage, marked as critical: Certificate Sign, CRL Sign
Install Root Certificate in Browsers
For information about how to install certificates in browsers, see Install the Cisco Secure Access Root Certificate.
Procedure
- Navigate to Secure > Certificates > Internet destinations, and click Add custom CA-signed certificate.
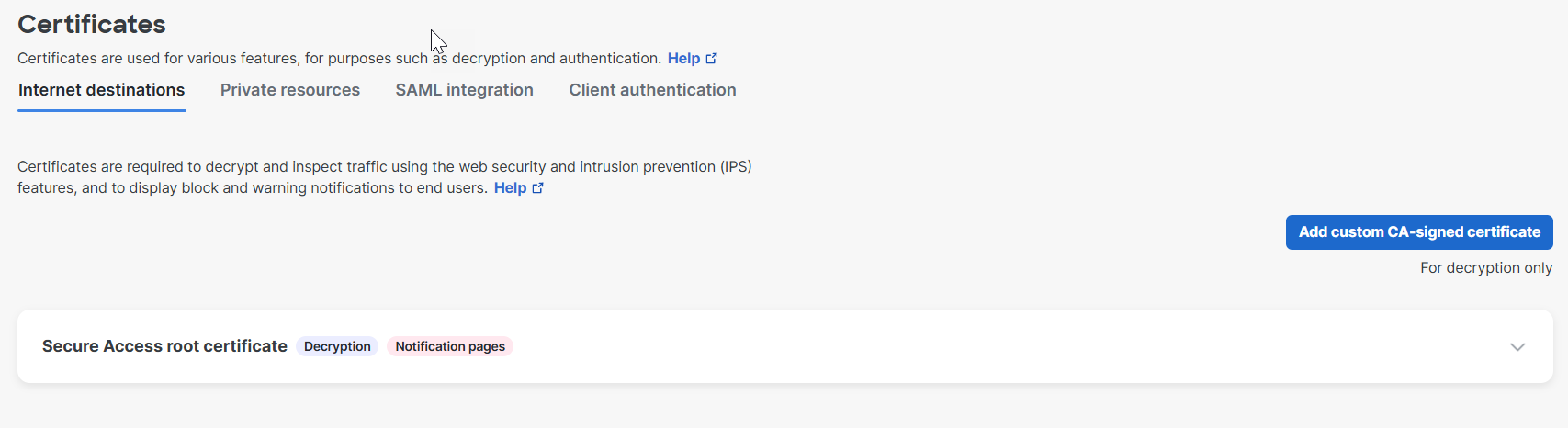
- Enter a descriptive name for your certificate, and then click Next.
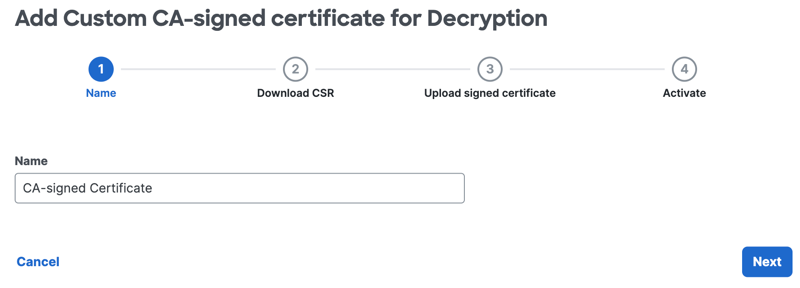
- Click Download CSR to save the Secure Access Certificate Signing Request (.csr) file to the local system, and then click Next.
Use a tool such as Microsoft Certificate Services or OpenSSL to sign the CSR with your corporate certificate signing authority (CA).
Note: You must download the Secure Access CSR file to complete the step.
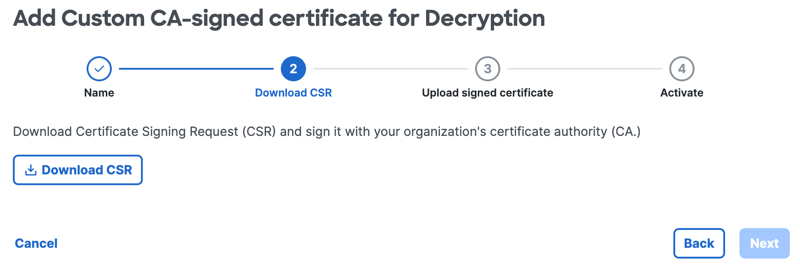
- Sign the downloaded CSR file with your corporate certificate authority (CA).
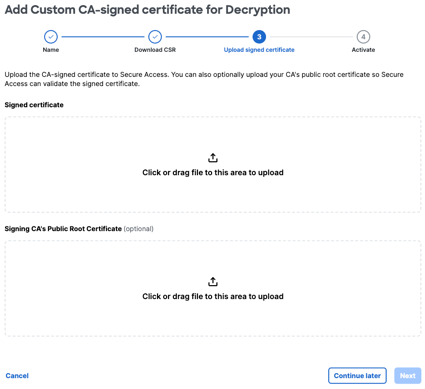
- Once you have signed the downloaded .csr file, click Upload signed certificate.
Certificate status isPending signed certificate uploaduntil you upload your own CA signed root certificate.
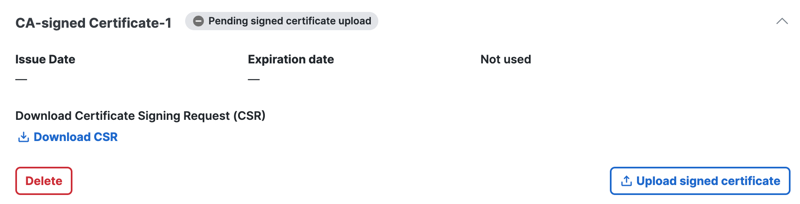
- Browse to the certificate that you have generated with the Secure Access CSR or drag the signed certificate file onto Secure Access, and then click Next.
You can optionally also upload your signing certificate authority's public root certificate to Secure Access. This allows Secure Access to validate the signed certificate that you uploaded.
- Confirm that end-user devices have the root certificate required to validate server certificates that are signed by your organization's CA. Managed devices typically already have the required certificate.
- For Activate, click Use for decryption to activate the CA signed certificate in Secure Access, and then click Start using for decryption.
Install the Cisco Secure Access Root Certificate < Add Customer CA Signed Root Certificate > View the Cisco Trusted Root Store
Updated about 2 months ago
