About Configuring Destinations in Internet Access Rules
The Cisco Secure Access policy is a collection of an organization's internet and private access rules. On internet access rules, you can configure DNS and web security and intrusion prevention system (IPS) settings, and define both source and destination components.
You can add pre-configured destination components or create composite destinations. Composite destinations may include IP addresses, CIDR blocks, wildcard masks, fully-qualified domain names (FQDNs), ports and port ranges, and transport protocols.
This guide describes the configuration options for destination components on internet Access rules.
Table of Contents
- Number of Destinations in a Rule
- Guidelines: Adding Destination Components on Internet Access Rules
- Pre-Configured Destinations on an Internet Rule
- Composite Destinations for Internet Access Rules
- Combining Multiple Destinations in a Rule (Boolean Logic)
Number of Destinations in a Rule
You can include up to 5000 destinations in an internet access rule. However, for optimal performance, include no more than 100 destinations in a rule.
Guidelines: Adding Destinations on Internet Access Rules
- We recommend that you pre-configure destinations in Secure Access. For descriptions and links to configuration instructions for each component type, see Components for Internet Access Rules.
- You can also specify web sites by their content categories, individual web application, or web application categories without creating content category lists or application lists. On an internet rule, choose Content Categories or Application Categories.
- Depending on the destinations you select (for example certain applications, application lists, or application categories) other options may appear in the rule.
- If you see an option to Select All, this selects all existing items in the group at the time you select it, but the rule will not include items added to the group in future.
- When you select a list or group, entities that are added to the list or group in the future are automatically included. For example, if you select a Destination List, any destinations that you add to that destination list later are automatically included.
- If this rule involves tenant controls, you must include the relevant application as a destination in the rule, as well as configuring the applicable tenant control profile and specifying that profile in the Security Controls section of the rule. For more information, see Manage Tenant Control Profiles.
- When specifying applications, it is not possible to search for an application with fewer than three letters in its name—for example, QQ or YY. You must pick the applications manually from the tree under their respective categories or use a wildcard in search—for example, QQ*. This behavior is by design.
For more information, see Add an Internet Access Rule—Pre-Configured Destinations.
Pre-Configured Destinations on an Internet Rule
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.

-
Navigate to Specify Access and then click on the search bar under To.
-
Click Select destinations, and then choose the destinations for the rule.
Note: If the rule action is Block, Secure Access displays the Geolocations destinations.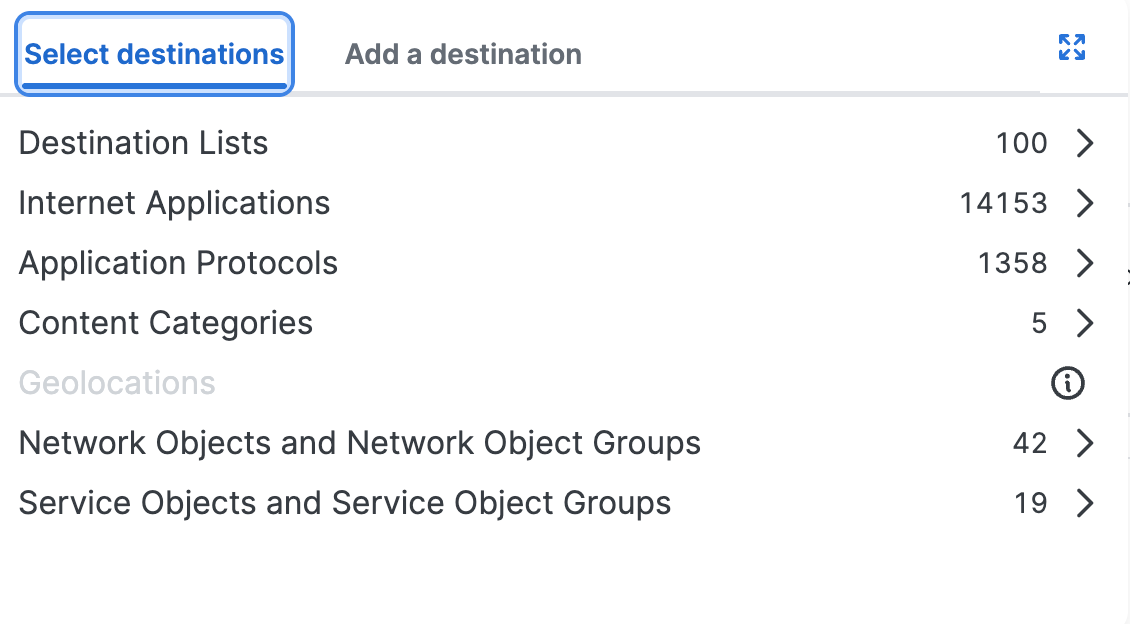
Application Lists and Application Categories on an Internet Rule
In Secure Access, internet applications are pre-configured application lists, application categories, and individual applications. You can add internet applications on an internet rule in your policy.
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.
-
Navigate to Specify Access and then click on the search bar under To.

-
Click Select destinations, and then expand Internet Applications.
a. For Application Lists, select the pre-configured application lists.
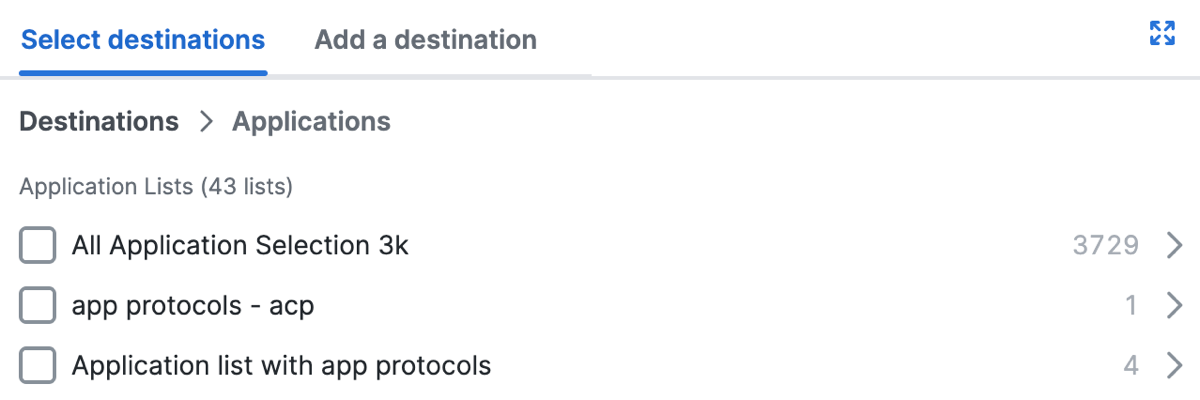
b. For Application Categories, select an entire application category or expand a category and select individual applications.
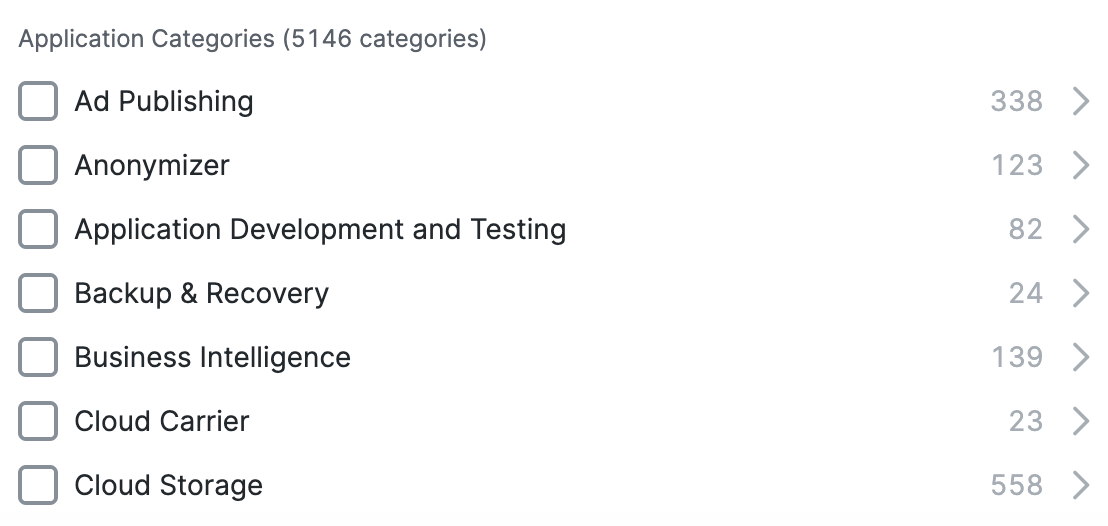
After you add pre-configured destinations, click +1More to view the list of destinations that you added to the rule.
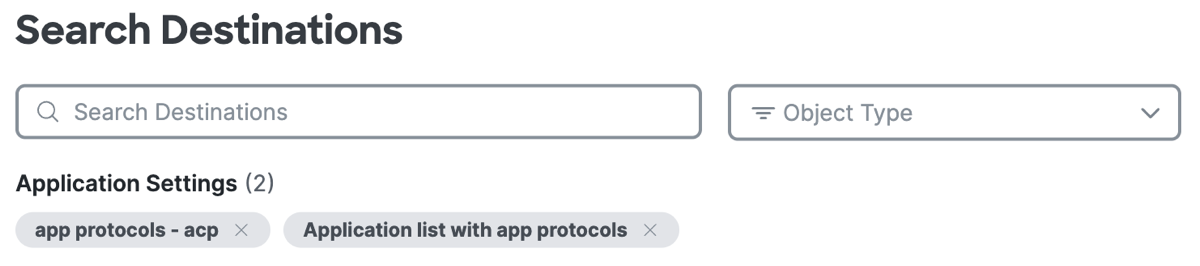
Application Protocols on an Internet Rule
You can select application protocols on a internet rule. Once you add the application protocols, click +AND to add composite destinations with the application protocols on the rule.
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.
-
Navigate to Specify Access and then click on the search bar under To.

-
Click Select destinations, expand Application Protocols, and then select the application protocols to add to the internet rule.
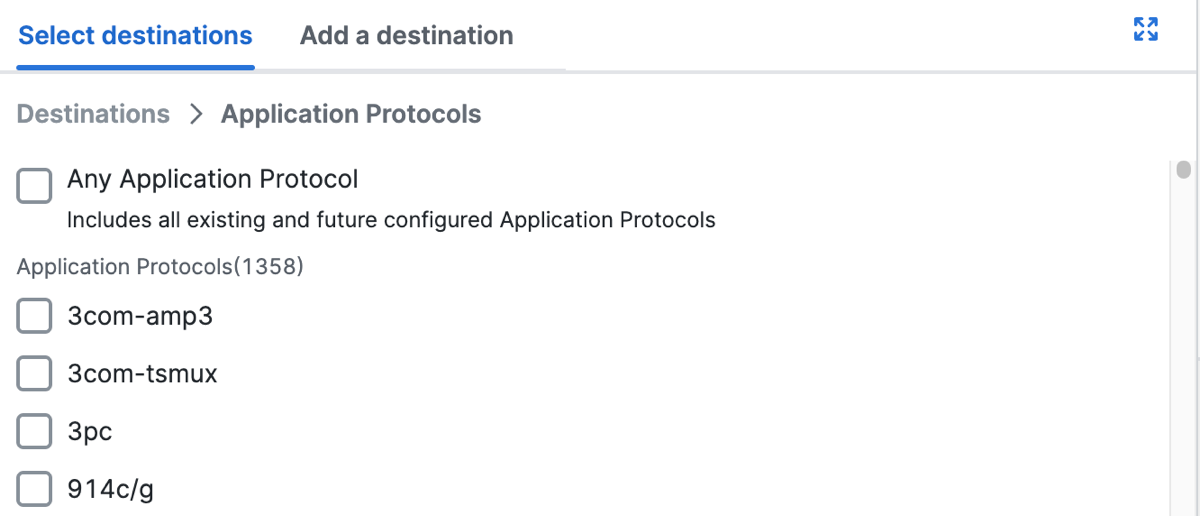
-
Click +More to view the added application protocols.
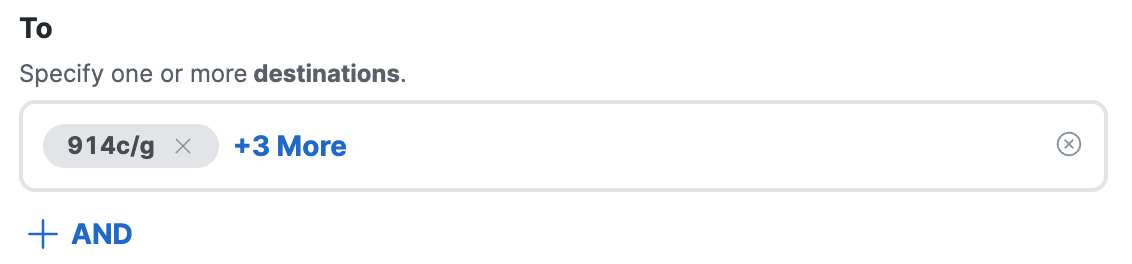
-
View or search for the added application protocols.
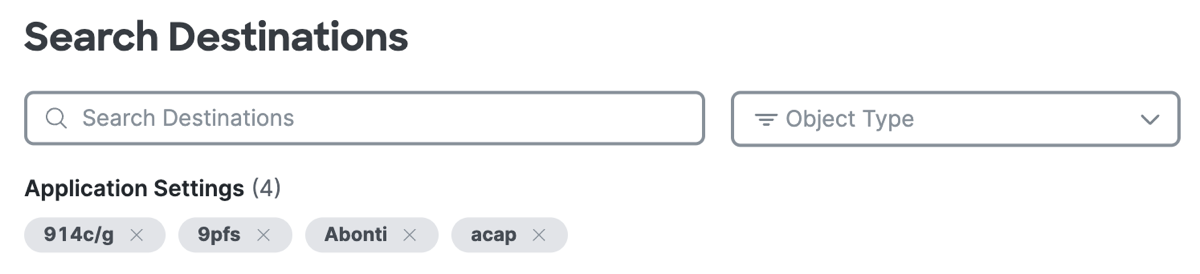
-
(Optional) Click +AND, and then click on the Select destinations text area.
Add composite destinations with Services (Transport protocols, and ports or port ranges) and combine with the application protocols that you added on the rule using the AND operator.- Add IP addresses and CIDR blocks.
Type or paste a comma-separated list of IPv4 addresses, IPv6 addresses, and CIDR blocks.
For example:192.168.1.1, 192.168.1.0/24, fd00:b0fc:8844:3345:186a:6fd7:bab:5f72. - Add Services.
Select transport protocols or Any, and enter a comma-separated list of ports or port ranges.
Example port ranges and lists of ports:7800-7805,7800,8900,9006.
- Add IP addresses and CIDR blocks.
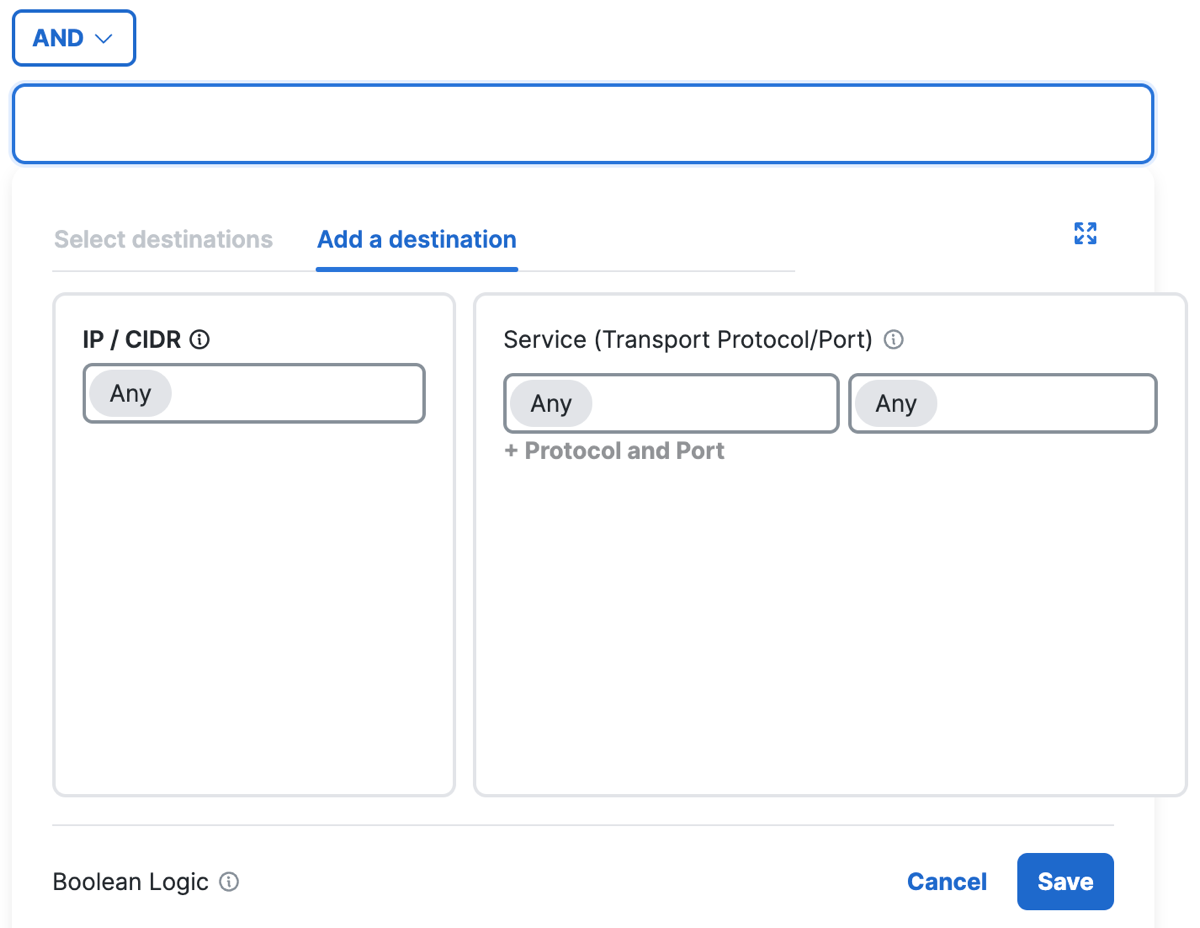
- Click Save.
How Application Protocols Combine with Composite Destinations
Secure Access uses boolean logic to combine the composite destinations on a rule with Services. Services are groups of transport protocols and port or port ranges.
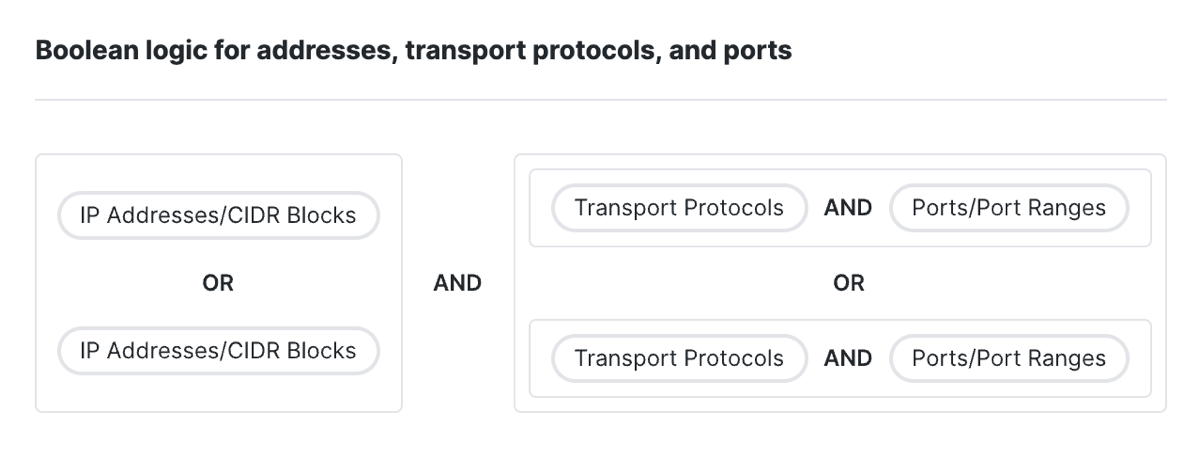
- First, Secure Access combines the individual composite destinations (IP addresses or CIDR blocks) together with the OR operator.
- Next, Secure Access combines each set of selected Service components together with the AND operator. Transport protocols are ANDed with the ports or port ranges.
- Next, Secure Access combines the Services together with the OR operator.
- Then, Secure Access combines the set of composite destinations with the set of Services using the AND operator.
Note: Secure Access does not support logical AND when combining pre-configured application lists, application categories, or destination lists.
Network and Service Objects on Internet Access Rules
You can select pre-configured Network Objects and Groups and Service Objects and Groups as destinations on internet access rules. When you choose the objects and groups, you have the option to combine the objects and groups with the logical AND operator. For more information, see Combine Destinations with Boolean Logic.
Note: If you do not add the logical AND operator with the selected destinations, Secure Access combines the destinations with the logical OR operator. For more information, see Combining Multiple Destinations in a Rule (Boolean Logic).
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.
-
Navigate to Specify Access and then click on the search bar under To.

-
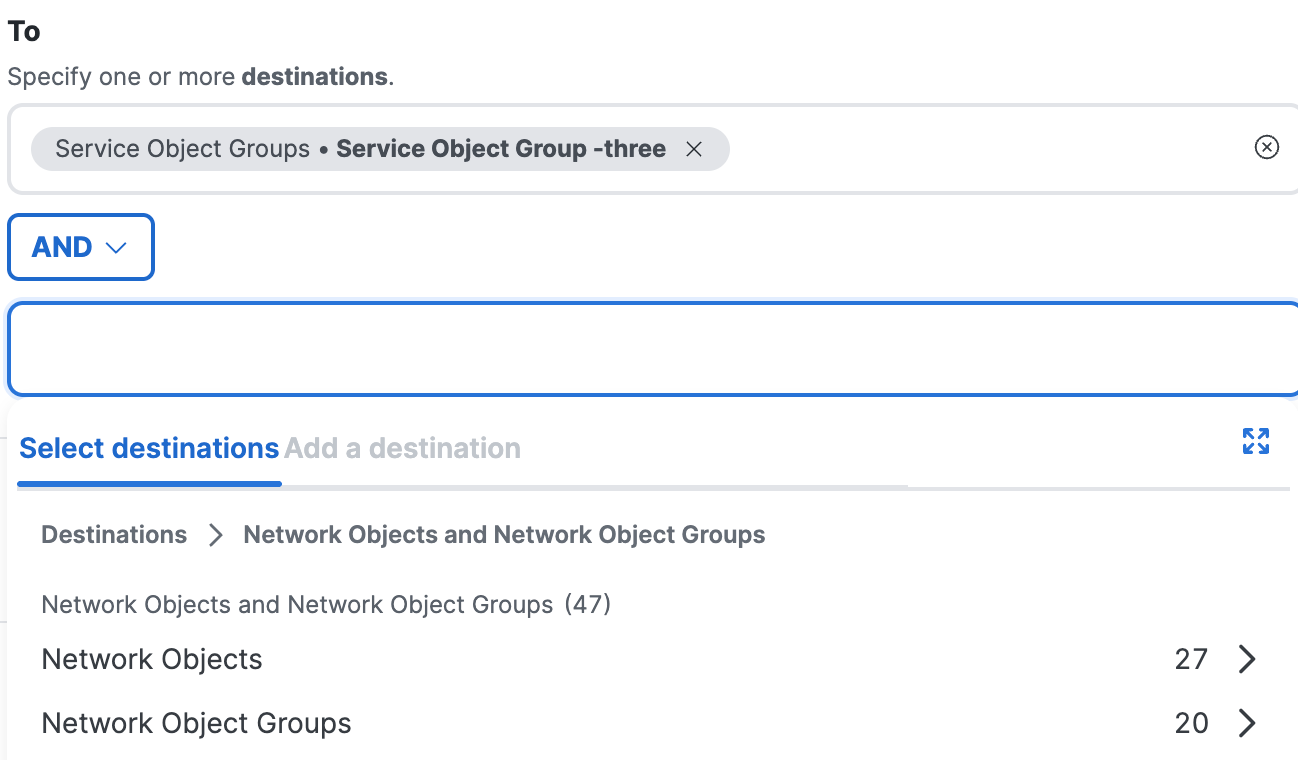
Select the Network Objects and Groups or Service Objects and Groups.
a. Click Select destinations, and then choose the Network Objects and Groups to add to the internet rule.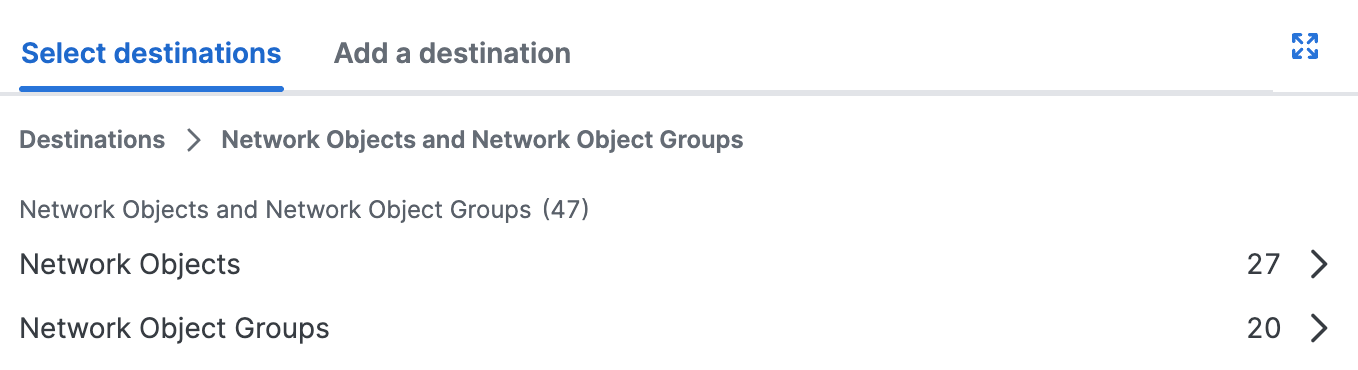
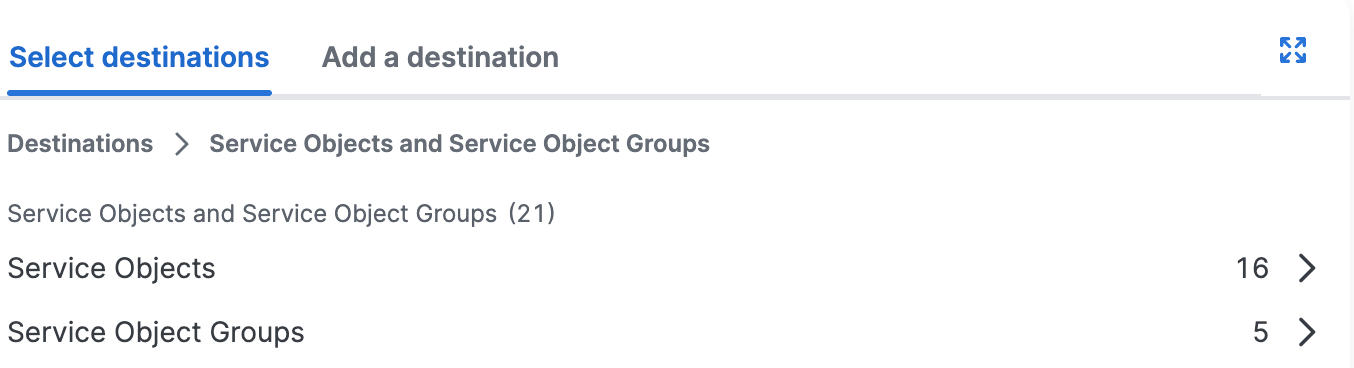
b. Click Select destinations, and then choose the Service Objects and Groups to add to the internet rule.
-
(Optional) Click +AND.
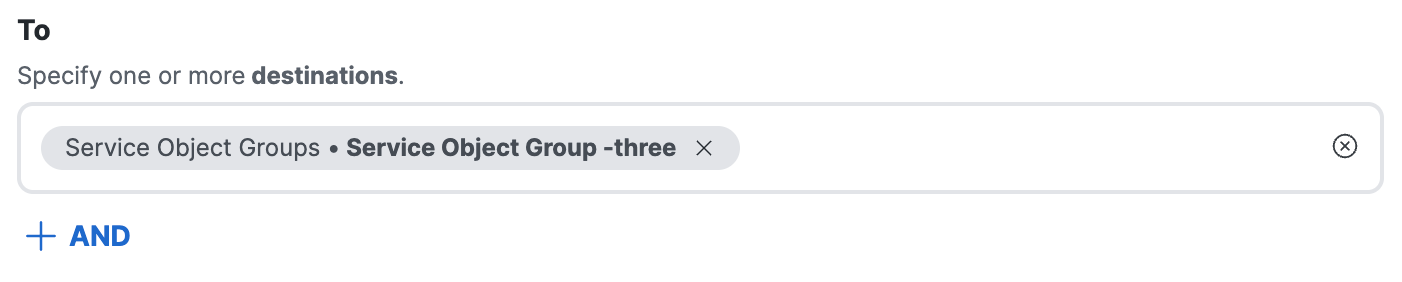
a. Click on the Select destinations text area.
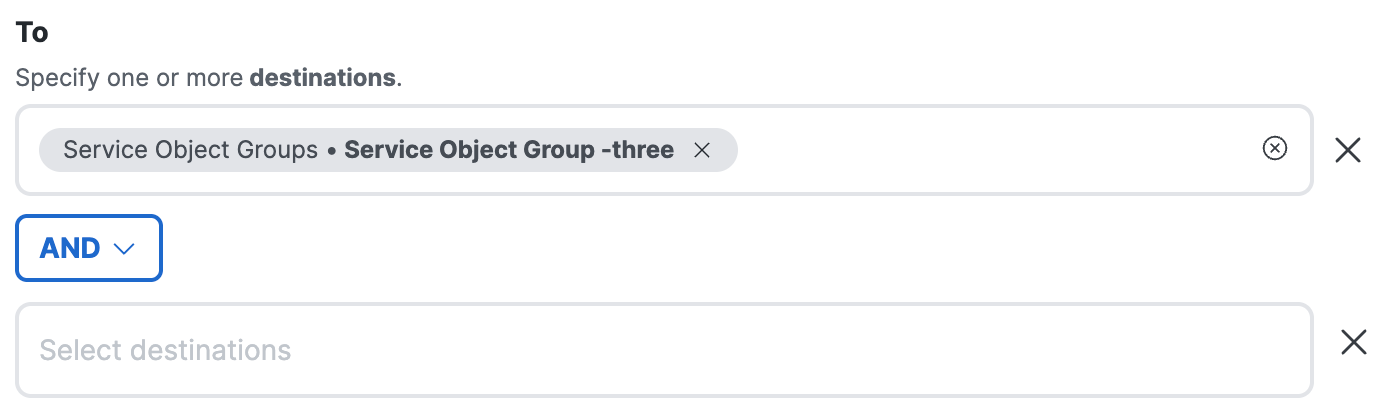
b. Choose a destination to combine with the other selected destinations using the logical AND operator. For more information, see AND Destinations: Network and Service Objects.
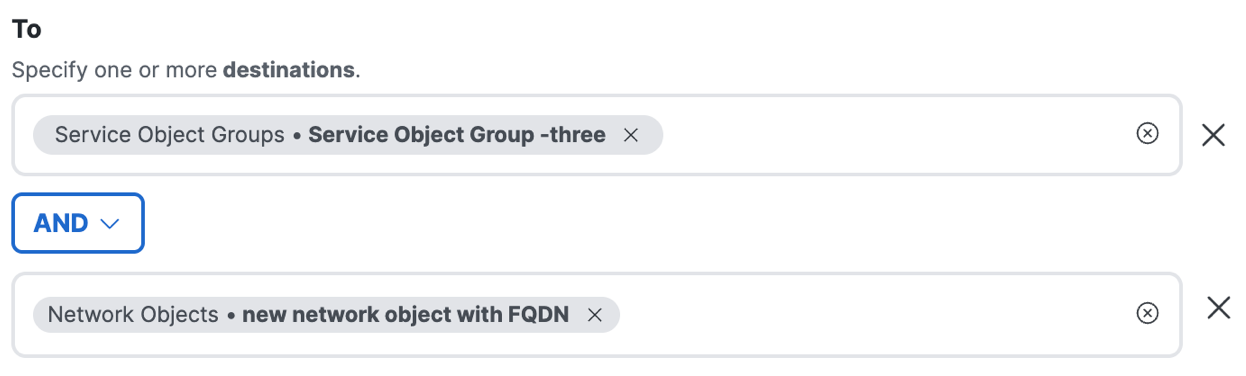
c. After you select the objects and groups to use with the AND operator, you can remove the destinations and then add new destinations.
Note: You have to select all destinations at the same time for each side of the AND option. Once selected, you can not go back and add more destinations.
- Click Next.
Composite Destinations for Internet Access Rules
You can define a destination from multiple network address components. A composite destination accepts IP addresses, CIDR blocks, wildcard masks, ports 80 and 443 for web traffic or all ports on non-web traffic, and the TCP, UDP, and ICMP transport protocols. You can choose ANY to select all available protocols on a destination.
This option is useful if you need to quickly address a specific issue that arises, for example to immediately allow access to a necessary destination that is being blocked by another rule, or to immediately block access to a problem destination.
Limitations of Composite Destinations
- Internet rules with composite destinations only support the Allow and Block actions.
- Composite destinations do not accept private non-routable IP addresses.
IP Addresses, CIDR Blocks, and Wildcard Masks
- Destinations accept valid public IP addresses, CIDR blocks, or wildcard masks.
For information about wildcard masks, see Using Wildcard Masks on Access Rules.
Ports
- Destinations accept ports 80 and 443 only for web traffic and all ports or port ranges for non-web traffic.
Protocols
- Destinations accept the TCP transport protocol. If you select TCP, the rule applies to web traffic and is protected by the secure web gateway.
- Destinations accept the UDP or ICMP protocols. If you select UDP or ICMP, the rule applies to non-web traffic and is protected by the IPS.
- For the protocol on the destination, you can choose ANY. If you select ANY, the rule applies to traffic on the TCP, UDP, and ICMP protocols. The traffic is protected by the secure web gateway.
Adding Composite Destinations
You can enter a single IPv4 address, CIDR block, or wildcard mask on an internet access rule.
Important: Secure Access does not support a comma-separated list of wildcard masks.
For more information, see Add an Internet Access Rule—Composite Destinations.
Combining Destination Components as a Single Destination
When you add individual network address components on a destination, Secure Access combines the field values to create a single destination entry. You can add multiple composite destinations on a rule.
- The ports added to the destination are OR'ed together. The rule applies to traffic on ports 80 or 443.
- The protocols added to the destination are OR'ed together. The rule applies to traffic on the selected protocols.
- The individual network component field values that you enter for Ports, Protocols, and IPs, CIDRs, or Wildcard Masks are AND'ed together to create a single destination. The rule applies to the traffic on the composite destination.
Note: You are not required to choose an IP, protocols, or ports to add a composite destination. Instead, you can choose the ANY protocol to define a destination that matches traffic on any IP or CIDR, with any port, on the available destination protocols.
Combining Multiple Destinations in a Rule (Boolean Logic)
If an internet access rule includes multiple destinations, the following boolean logic applies:
- All types of destinations, and all destinations within a type, are treated as using the boolean OR operator. Traffic to each destination that you specify in a rule matches the rule.
- For example, if you specify a content category and an application list as destinations in a single rule, traffic to any destination that is a member of either group will match the rule.
- If you specify ANY for the protocol, then all traffic on the protocols (TCP, UDP, ICMP) supported by internet rules matches the rule, regardless of any other destinations that you specify.
- If you enter in values of different types (IP address, port, protocol), traffic matches if any of the specified values match the rule.
- For example, if you specify an IP address and a port, traffic to any IP address on the specified port matches the rule, as does traffic to the specified address on any port.
About Configuring Sources in Internet Access Rules < About Configuring Destinations in Internet Access Rules > Ensure Rule Matching for Encrypted Internet Traffic
Updated 3 months ago
