Components for Internet Access Rules
Cisco Secure Access supports configuring security controls for sources and destinations (resources) on internet access rules. You can create access rules in the organization's Access policy by adding components that you or others have previously created. Components described in this topic are reusable; you can use the same component (such as a source) in multiple rules.
Before you can add resources in Secure Access, deploy the resources in the organization's environments. Also configure resources for destinations in Secure Access: content categories, destination lists, and application lists. Once you register the resources in Secure Access, you can select these components on the internet access rules.
For example, you can define a set of users as a source, then use the same source in an internet access rule and in a private access rule for the same set of users. Some components are profiles, or groups of settings bundled together that you choose as a unit when configuring a rule.
Table of Contents
Sources
You can configure internet access rules for specific source-destination pairs. Sources are the users, groups of users, or other entities that comprise the "From" end of traffic where Secure Access applies an access rule.
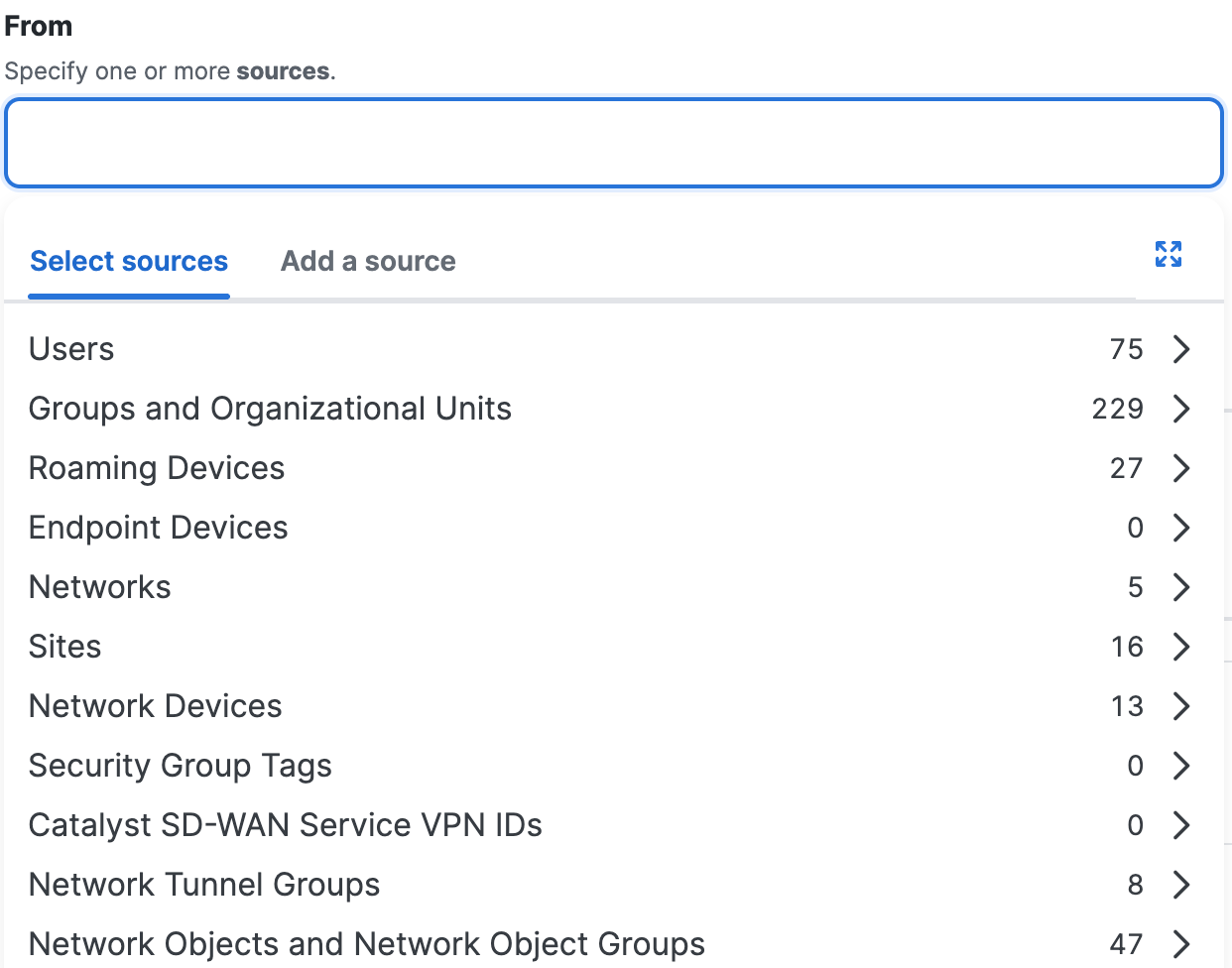
You can use these reusable sources on internet access rules:
- Users
You can apply rules to the traffic for the users in the organization. - Groups and Organizational Units
You can apply rules to the traffic for users in AD Groups and Google Workspace Organizational Units. - Roaming Devices
You can apply rules to traffic originating from managed devices that have the Cisco Secure Client installed, but that may not currently be on the corporate network. - Network Objects
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects. - Network Object Groups
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects in Network Object Groups. - Endpoint Devices
You can apply internet access rule security controls to AD devices in Secure Access. Once provisioned, AD devices are available as sources on internet access rules. You can select all AD devices or individual AD devices identified by device name. For more information about AD device provisioning, see Manage Users, Groups, and Endpoints Devices. - Registered Networks
You can apply rules to traffic originating from IP addresses in network segments defined by Registered Networks.
- When on a Registered Network, users devices can send traffic to the Secure Access DNS resolvers and the Secure Web Gateway (SWG) directly. In this scenario, user devices are not required to deploy the Cisco Secure Client with the Internet Security and VPN modules or deploy IPsec tunnels (RAVPN).
- If the user device has the Cisco Secure Client deployed with the Internet Security and VPN modules, then traffic is sent over IPsec tunnels to Secure Access.
- Sites
You can apply rules to traffic originating from IP addresses in network segments defined by Secure Access Sites. - Network Devices
You can apply rules to traffic originating from network devices. - Security Group Tags
You can apply rules to traffic originating from IP addresses in network segments that include Security Group Tags. - Catalyst SD-WAN Service VPN IDs
You can apply rules to traffic originating from IP addresses in network segments that include VPN IDs. Be aware that if the same VPN ID (VPN 88 for example) is assigned across different branches, then traffic coming into Secure Access from these branches is subject to the same policy. A Secure Access policy rule cannot differentiate traffic between branches using the same VPN ID. - Network Tunnel Groups
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Tunnel Groups.
In a rule, you can also specify sources by typing in IP addresses and subnets, but these are NOT reusable source components. If you do this, you can type in port and protocol in the rule's destination.
For more information, see About Configuring Sources in Internet Access Rules.
Destinations
You can configure internet access rules in the Access policy for specific source-destination pairs. Destinations are the web applications, web sites in particular categories, or other internet destinations that comprise the "To" end of traffic where Secure Access applies an access rule.
Rule Enforcement with Destination Lists and Fully Qualified Domain Names
Important: You can add destination lists that include fully qualified domain names (FQDNs) on internet access rules. To enforce the internet access rules with the destination lists and FQDNs, Secure Access requires that all DNS queries for these FQDNs use the Secure Access DNS servers. For more information, see Manage End-User Connectivity and Manage DNS Servers.
For information about decryption, see Security Profiles for Internet Access and Manage Traffic Decryption.
Reusable Destinations in Internet Access Rules
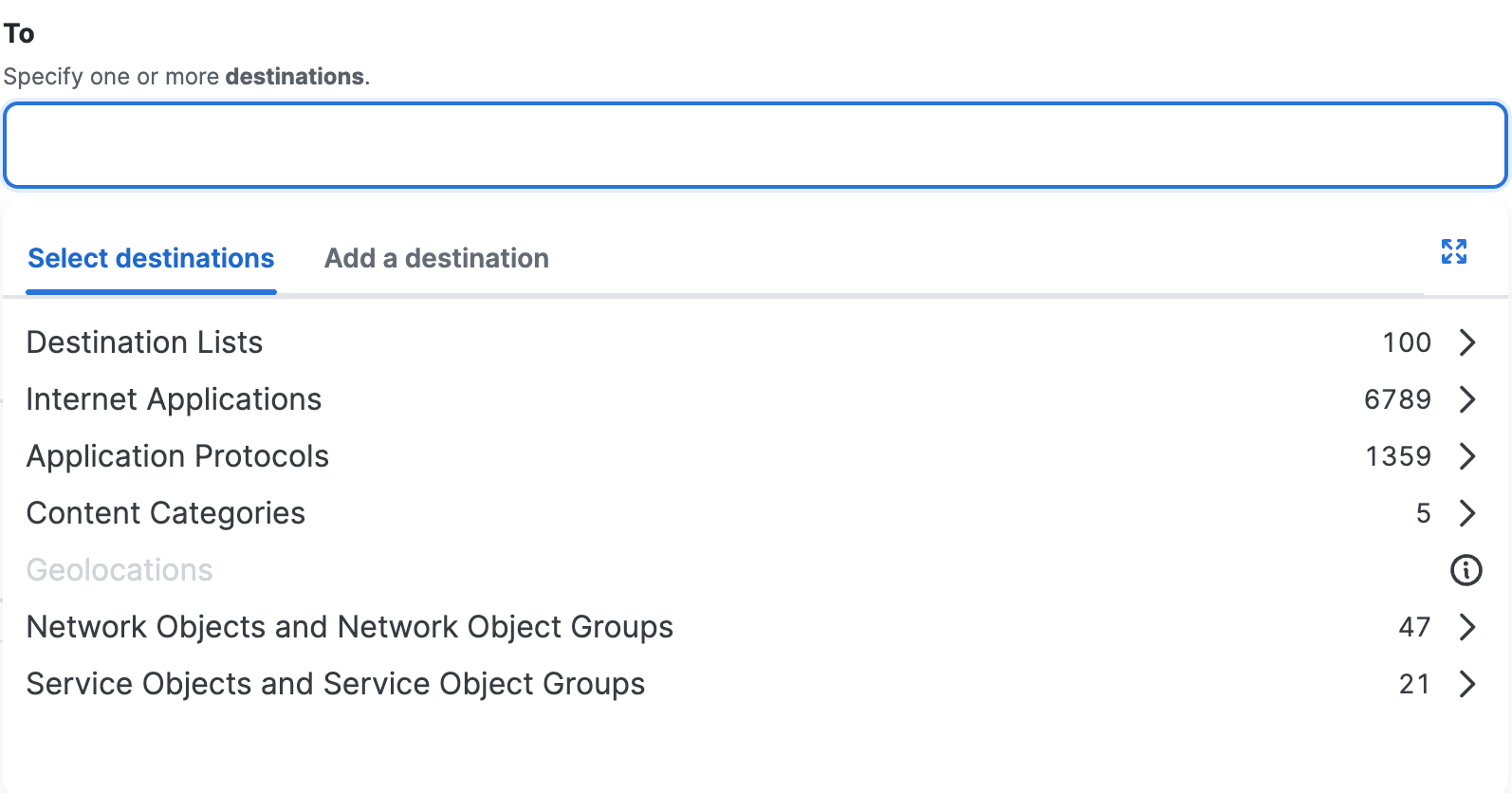
- Destination Lists
List groups of domains, URLs, IP addresses, and CIDR blocks to which you want to apply the same policy.
You can create custom lists of destinations based on any criteria you choose. - Content Category Lists
Create lists of web sites based on the content or type of the site, so you can control access to a variety of sites as a group. For example, you might create a content category list that includes all sites belonging to the Adult, Child abuse, and Pornography categories. - Application Lists
Create lists of web-based applications to which you want to apply the same policy. For example, if you want to apply a single policy to all social media applications, you can create an application list that includes all applications in the Social Networking category.
For some web-based applications, you can allow access to the application, but block uploads, downloads, and posting or sharing information. You will see these options in each rule when you configure applicable destinations in the rule. For details, see Advanced Application Controls. - Network Objects
Network Objects represent IPv4 and IPv6 addresses, CIDR blocks, ranges of IPv4 addresses, wildcard masks, or fully-qualified domain names (FQDNs). Select the Network Objects on the access rules to apply security controls to the traffic on the networks. - Network Object Groups
Select the Network Object Groups on the access rules to apply security controls to the traffic on the networks in groups. - Service Objects
Service Objects represent a port, range of ports, protocol, or traffic on any protocols. Select the Service Objects on the access rules to apply security controls to the services. - Service Object Groups
Select the Service Object Groups on the access rules to apply security controls to the traffic on the services in groups.
Additional Configuration Options
- Specify web sites by content category, or specify web applications or categories of web application, without creating content category lists or application lists.
- Type destination IP addresses, ports, and protocols directly into the rule. We recommend that you create reusable destination objects. For more information, see About Configuring Destinations in Internet Access Rules.
- Apply an app risk profile to modify the list of destinations the rule targets. An app risk profile defines a list of risk characteristics you can apply to an access rule, causing that rule to take those characteristics into account when determining whether to flag an internet application a user accesses. These characteristics can include label status from the App Discovery Report, the application risk score ( calculated by Secure Access or assigned by you), business risk factors, and various security-related attributes such as security standard compliance, or resistance to various known vulnerabilities. For full details on the risk characteristics available to include in app risk profile, see Add an App Risk Profile.
Security Controls
Security controls make use of profiles and other pre-configured sets of settings.
The following types of security controls apply to internet traffic:
Intrusion Prevention (IPS)
Intrusion Prevention protects your network and assets by inspecting traffic for specified threat characteristics.
You will specify a single intrusion prevention profile in each access rule.
- Set Up Certificates for Decrypting Internet Traffic
- Configure Intrusion Prevention (IPS) Profiles
- Configure the Do Not Decrypt List for IPS
Set Up Certificates for Decrypting Internet Traffic
Internet traffic must be decrypted in order to allow it to be inspected by the intrusion prevention and for web security features, for example those defined in a Security Profile. In order to decrypt this traffic, certificates are required. You may have already set up these certificates to decrypt traffic for web security features.
See Certificates for Internet Decryption.
Configure Intrusion Prevention (IPS) Profiles
Intrusion Prevention (IPS) detects a large number of known threats. Sets of settings are grouped together in profiles, which you can specify in access rules. Secure Access provides several pre-configured profiles that address common needs, such as Balanced Security and Connectivity or Maximum Security. Or you can create a custom profile using Snort signatures. You can also choose to block or just monitor traffic that matches a profile.
You can choose a different IPS profile for each access rule based on the balance of convenience vs. risk appropriate for the particular traffic.
For details, see Manage IPS Profiles.
Configure the Do Not Decrypt List for IPS
Secure Access must decrypt traffic in order to allow the Intrusion Prevention feature to inspect the traffic for threats.
However, decrypting traffic to certain sites, such as health-related or financial sites, may be restricted by privacy laws in some geographic regions.
Use the default Do Not Decrypt List to specify destinations that should not be decrypted by intrusion prevention processes (IPS.)
Web security features, for example those configured in a Security Profile, also require decryption in order to be effective; you can use this list for web security decryption, or you can create and use a different list or lists for web security.
For details, see Important Information About Do Not Decrypt Lists.
Security Profile
You will specify a single Security Profile in each internet access rule. Each security profile includes multiple components that you should pre-configure.
- Configure Threat Category Settings
- Configure SSO Authentication
- Set Up Certificates for Decrypting Internet Traffic
- Configure Do Not Decrypt Lists
- (Optional) Configure Custom End-User Block and Warn Notifications
- Configure Security Profiles for Internet Access
Configure Threat Category Settings
Choose the types of web-borne threats to block. Blocking some threat categories may affect legitimate traffic.
See Threat Categories.
Configure SSO Authentication
SSO authentication is required for some web security features.
See Security Profiles for Internet Access.
Set Up Certificates for Decrypting Internet Traffic
If you have already set up certificates for this purpose for the intrusion prevention feature, you may not need to do anything more.
Internet traffic must be decrypted in order to allow it to be inspected by the intrusion prevention and web security features, to apply acceptable use controls, for rules in which the rule action is Isolate or Warn, and to display end-user notifications when destinations are blocked.
In order to decrypt this traffic, certificates are required.
See Certificates for Internet Decryption.
Configure Do Not Decrypt Lists
Secure Access must decrypt internet traffic in order to allow Web Security features to protect your network effectively.
However, decrypting traffic to certain sites, such as health-related or financial sites, may be restricted by confidentiality law in certain geographic regions.
Use a Do Not Decrypt List to specify destinations that should not be decrypted by web security processes. You can create different Do Not Decrypt Lists for different regions or purposes.
You can use the same Do Not Decrypt List that you use for IPS, or create one or more Do Not Decrypt lists to use only for security features included in the security profile.
For details, see Important Information About Do Not Decrypt Lists.
(Optional) Configure Custom End-User Block and Warn Notifications
If you do not want to use the default Secure Access-branded notifications, configure the notifications that are presented to end users who attempt to access internet destinations that are blocked, and notifications to present when users attempt to access destinations that match a rule configured with the Warn action.
End-user notifications require decryption.
See Manage Notification Pages.
Configure Security Profiles for Internet Access
Sets of security security settings grouped into profiles control the following aspects of security for internet traffic:
- Decryption (including Do Not Decrypt lists)
See information above. - SSO Authentication
See information above. - Threat categories
See information above. - File inspection
File inspection detects threats using Cisco Advanced Malware Protection and Cisco Secure Malware Analytics.
See Manage File Inspection and File Analysis. - File type blocking
Block files based on their type. For example, you can prevent users from downloading executable files from the web.
See Manage File Type Control. - SafeSearch
SafeSearch filters out offensive, explicit, unsafe, and harmful results from searches in Google, YouTube, Yahoo, and Bing.
See SafeSearch - AI Supply Chain Blocking
AI Supply Chain Blocking controls end user access to files that can pose AI supply chain risk to security and compliance.
See AI Supply Chain Report - End-user notifications
Web pages shown to users who attempt to access blocked destinations or destinations allowed with a warning.
See information above.
You will enable these options in a security profile that you will choose in a rule. See Add a Security Profile for Internet Access.
Tenant Controls
If your company uses Microsoft 365, Slack, Google G-Suite, or Dropbox, see Manage Tenant Control Profiles.
Get Started With Internet Access Rules < Components for Internet Access Rules > Default Settings for Internet Access Rules
Updated 24 days ago
