Customize the Secure Access PAC File
You can create custom PAC files to use with the browsers on the user devices in the organization.
To bypass domains, add domains in Secure Access where the web traffic on these domains will bypass the secure web gateway (SWG). Secure Access includes the configured bypass domains in the Secure Access PAC file. For information about bypass domains, see Manage Internet Security Bypass.
After you download the Secure Access PAC file from Secure Access, you can edit the file and add more domains. Then, upload the custom PAC file to Secure Access or host this PAC file in your environment. Secure Access does not modify a custom PAC file. Secure Access only modifies the Secure Access PAC file with the bypass domains that you add in Secure Access.
Note: Secure Access supports IP-based domains. You must enter the IP in the browser’s address bar as the domain portion of the URL. For example, https://1.2.3.4/URLpath/. The PAC file does not resolve a domain to IP before matching an IP-based domain for bypass.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- To download the Secure Access PAC file or custom PAC files on a user device in the organization, the device must either:
- Connect to Secure Access on a Registered Network or Network Tunnel, or
- Deploy the Cisco Secure Client with the Umbrella Roaming Security module on the user device.
For more information, see Manage PAC Files.
Procedure
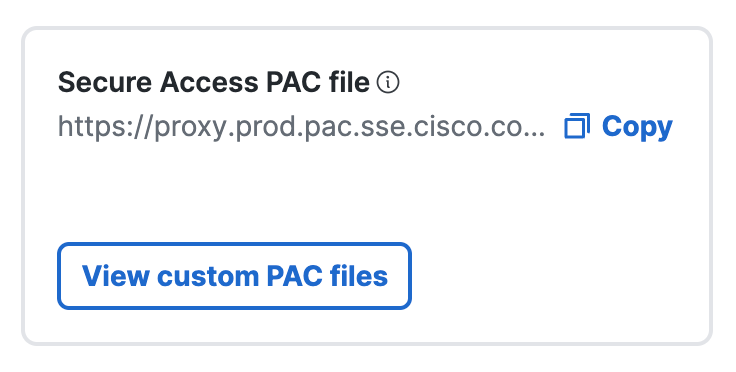
Copy the Secure Access PAC File URL. Then, enter the PAC file URL in your browser and download the PAC file. Open the Secure Access PAC file in an editor and update the file.
Copy the Secure Access PAC File
-
Navigate to Connect > End User Connectivity > Internet Security.
-
For Secure Access PAC File, click Copy to get the PAC file URL.
Download the Secure Access PAC File
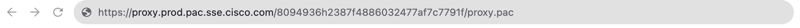
- Paste the copied PAC URL into a browser's address bar and then press Enter or Return to download the PAC file.
Edit the PAC File
- Open the downloaded PAC file with a text editor.
- Add the internal domains that the web proxy will bypass to the PAC file, and then save the file.
Note: Provide a comma-delimited list of domain names and surround each domain name in the list with quotation marks. The wildcard character asterisk * is supported and treated as any value of any length. Use caution when using wildcards as well as periods. For example, *.example.com bypasses www.example.com, mail.example.com, and c.23.example.com. *example.com bypasses www.example.com as well as phishingexample.com. - Save the PAC file.
function FindProxyForURL(url, host) {
//------------------------Customer Section------------------------
//Add your internal domains within quotations marks like "wwwin.acme.com"
//after the right parenthesis below. Please remove the two examples
//below and add your own internal domains.
var dont_proxy_customer_list = ["121.12.11.11","*.121.12.11.11","aaa","*.aaa","abc.com","*.abc.com","addingboth.com","*.addingboth.com","alibaba.com","*.alibaba.com","capfix.com","*.capfix.com","capissuefix.com","*.capissuefix.com","ci.com","*.ci.com","example.com","*.example.com","flipkart.com","*.flipkart.com","google.com","*.google.com","internal.com","*.internal.com","internaldomain.com","*.internaldomain.com","nnn.com","*.nnn.com","qeqfqgeag.com","*.qeqfqgeag.com","resolvewithdns.com","*.resolvewithdns.com","something.com","*.something.com","ss.com","*.ss.com","test1.com","*.test1.com","testing.com","*.testing.com","testing2.com","*.testing2.com","testing3.com","*.testing3.com","testnew.com","*.testnew.com","bypassproxy.com","*.bypassproxy.com","external.com","*.external.com","externalexample.com","*.externalexample.com","test.com","*.test.com"];
//Warning to Administrators: Touching any section after this point might
//affect your users browsing experience and lead to considerable number
//of issues and loading your customer support.
//---------------------End Customer Section-----------------------
for(var iter = 0; iter < dont_proxy_customer_list.length; ++iter) {
if(shExpMatch(host, dont_proxy_customer_list[iter])) {
return "DIRECT";
}
}
Deploy the Secure Access PAC File for macOS < Customize the Secure Access PAC File > Upload Custom Pac Files to Secure Access
Updated 6 months ago
