View User Details
After an administrator provisions users in Cisco Secure Access, you can view details about the users including information about the access rules that apply to the users.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Procedure
View provisioned users in Secure Access.
View Users Provisioned in Secure Access
-
Navigate to Connect > Users, Groups, and Endpoint Devices, and click Users.
Secure Access lists the users that you provisioned in the organization.- Name—The first and last names of the user.
- User Principal Name (UPN)—The User Principal Name for the user.
- Auth Property—The property that Secure Access uses to authenticate the users in the organization.
- Source—The method or identity provider that provisioned the user.
- Directory—The name of the user directory for the identity provider (IdP) integration.
- Connected (VPN)—The number of connections with Secure Access virtual private network (VPN) from the user's devices.
- Enrolled (ZTNA)—The number of connections with Secure Access Zero Trust Access from the user's devices.
- Associated Rules—The number of access rules that include the user.
-
Navigate to a user.

View User Details
Get the information about a user provisioned in the Secure Access organization.
- Navigate to Connect > Users, Groups, and Endpoint Devices, and click Users.
- Navigate to a user, and then click on the name of a user to view the details.
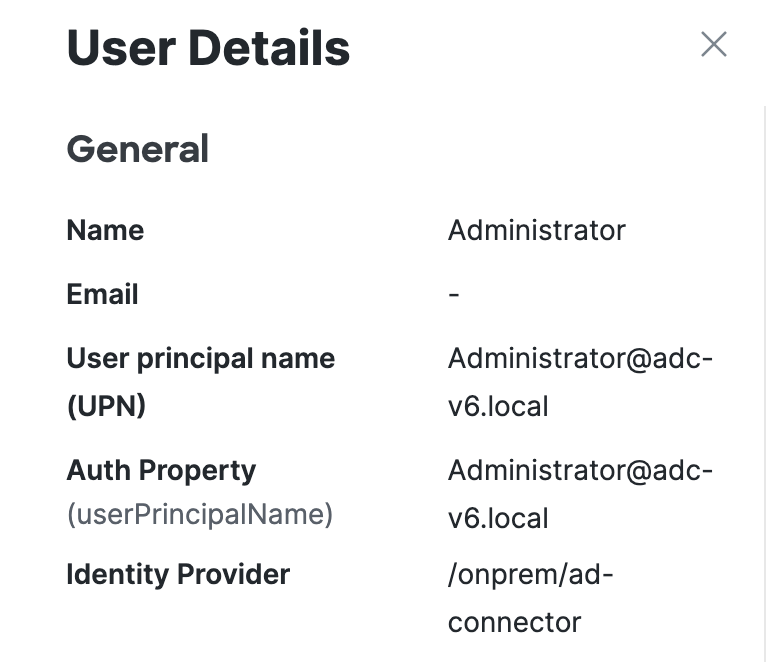
General
-
Name—The name of the user.
-
Email—The email of the user.
-
User Principal Name—The User Principal Name for the user.
-
Auth Property—The name and value of the property that Secure Access uses to authenticate the users in the organization.
-
Identity Provider—The identity provider that manages the user account.
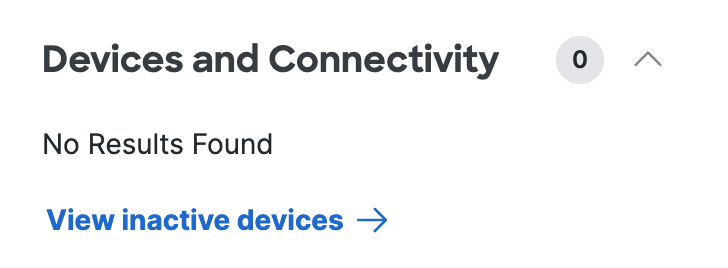
Devices and Connectivity
The number of user devices connected and the information about the devices.
-
Connection—The type of connection
-
IP address—The IP address of the device.
-
OS Version—The version of the device's operating system.
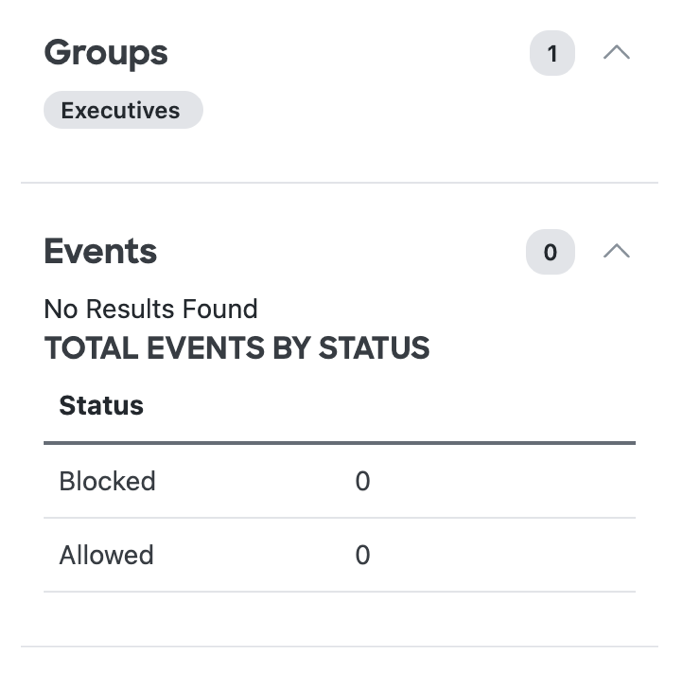
Groups and Events
- Groups—The number of groups that include the user and the name of the groups.
- Events—The number of events created by the user and the status of the events.
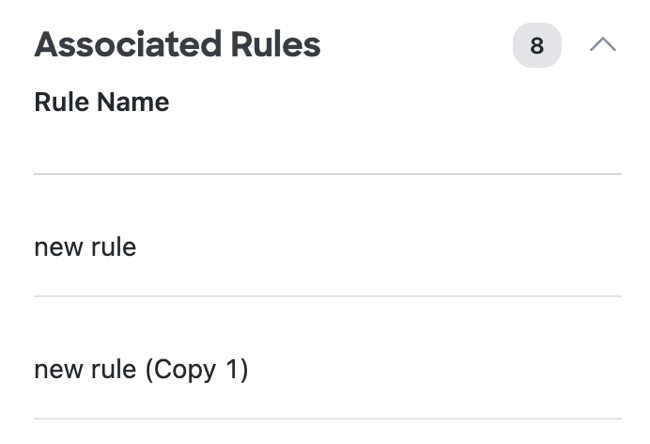
Associated Rules
The Secure Access rules in the Access policy that apply to the user.
Manage Users and Groups < View User Details > View Group and Organizational Unit Details
Updated about 6 hours ago
