Configure Tunnels with Cisco Adaptive Security Appliance
Follow the steps in this guide to connect a Cisco Adaptive Security Appliance (ASA) firewall through an IPsec (Internet Protocol Security) IKEv2 (Internet Key Exchange, version 2) tunnel to Cisco Secure Access.
Table of Contents
Prerequisites
You must meet licensing, hardware, and network access prerequisites for the tunnel to work successfully.
Licensing and Hardware
- A valid Cisco Secure Access account.
- A Cisco Secure Access organization ID. For more information, see Find Your Organization ID.
- A Cisco ASA router with a security K9 license to establish an IPsec tunnel. Other devices may work but have not been tested.
- ASA Base or Security Plus license to establish an IPsec tunnel.
- A network tunnel group configured on Cisco Secure Access; see Add a Network Tunnel Group.
Network Access
- When you add a network tunnel, we recommend that you choose the IP address based on the data center located closest to you.
- Open UDP ports 500 and 4500.
Cisco ASA version 9.16 or lower devices require static public routable IPv4 address(es) configured on the interface that connects to the public internet and the Cisco Secure Access data center. This static public routable IPv4 address must not be subject to a NAT. If NAT is present, the tunnel will fail. This is because Cisco ASA IKEv2 PSK authentication automatically uses this directly configured IPv4 address as its IKE ID. This ID in combination with the PSK is used to successfully authenticate the ASA with Secure Access.
ASA 9.17 or above supports per tunnels identity and IKEv2 FQDN identity. Now that the ASA can be behind NAT, configure the tunnel in Secure Access as follows:
- Tunnel type: Other
- Authentication: FQDN
- ASA IPsec profile configuration should include the extra command with tunnel identity (set ikev2 local-identity email-id [email protected])
Configure Tunnels in Secure Access
- Follow the steps in Add Network Tunnel Group.
The new tunnel appears in the Secure Access dashboard with a status of UnEstablished. The tunnel status is updated once it is fully configured and connected with the ASA.
Configure ASA
- Configure the IKEv2 policy. Define the settings according to the supported IPsec parameters. Choose the policy number based on your ASA's existing policies.
- Replace the default device name called
outsidewith the name configured on your device. The device name refers to the public facing interface which the VPN uses to connect.
- Replace the default device name called
crypto ikev2 policy 10
encryption aes-gcm-256
integrity null
group 19
lifetime seconds 86400
crypto ikev2 enable outside
- Configure the Group Policy and Tunnel Group parameters.
- Enter the IP of a Secure Access data center.
- Replace
[Portal_Tunnel_Passphrase]with the Passphrase you configured in the previous section, Add Network Tunnel Group.
group-policy sse-policy internal
group-policy sse-policy attributes
vpn-tunnel-protocol ikev2
tunnel-group <sse_dc_ip> type ipsec-l2l
tunnel-group <sse_dc_ip> general-attributes
default-group-policy sse-policy
tunnel-group <sse_dc_ip> ipsec-attributes
ikev2 remote-authentication pre-shared-key 0 [Portal_Tunnel_Passphrase]
ikev2 local-authentication pre-shared-key 0 [Portal_Tunnel_Passphrase]
Validate that the command crypto isakmp identity is set to the default value "auto" to determine the correct ID Method for ISAKMP Peers.
- Configure IPsec proposal and profile parameters.
- Define the settings according to the Supported IPsec parameters.
crypto ipsec ikev2 ipsec-proposal Secure-Access-Ipsec-Proposal
protocol esp encryption aes-gcm-256
protocol esp integrity sha-1
crypto ipsec profile Secure_Access
set ikev2 ipsec-proposal Secure Access-Ipsec-Proposal
!
!Note: below command applies for v9.17+ only
set ikev2 local-identity email-id [email protected]
- Create a virtual tunnel interface (VTI).
- Enter the IP of a Secure Access data center.
- Replace the Sample IP with any non-existing IP address that is not being used for a VLAN, subnet or existing VLAN connection in your network.
interface Tunnel1
nameif vti
ip address x.x.x.1 255.255.255.0 **An unused range**
tunnel source interface outside
tunnel destination<sse_dc_ip>
tunnel mode ipsec ipv4
tunnel protection ipsec profile Secure_Access
- Configure policy-based routing. In the following examples, the LAN subnet is
192.168.20.0/24and the LAN interface isGigabitEthernet1/2.- Configure PBR to send the internal traffic through the tunnel interface to reach the Secure Access data center.
- Set the IP address in
next-hopto the same subnet assigned to the VTI.
access-list ACL-sse line 1 extended permit ip 192.168.20.0 255.255.255.0 any4
route-map sse-PBR permit 10
match ip address ACL-sse
set ip next-hop x.x.x.2
interface GigabitEthernet1/2
policy-route route-map sse-PBR
Test and Verify
ASA CLI
You can verify the ASA tunnel status to Secure Access by using these commands:
show crypto ikev2 sa detail
show crypto ipsec sa detail
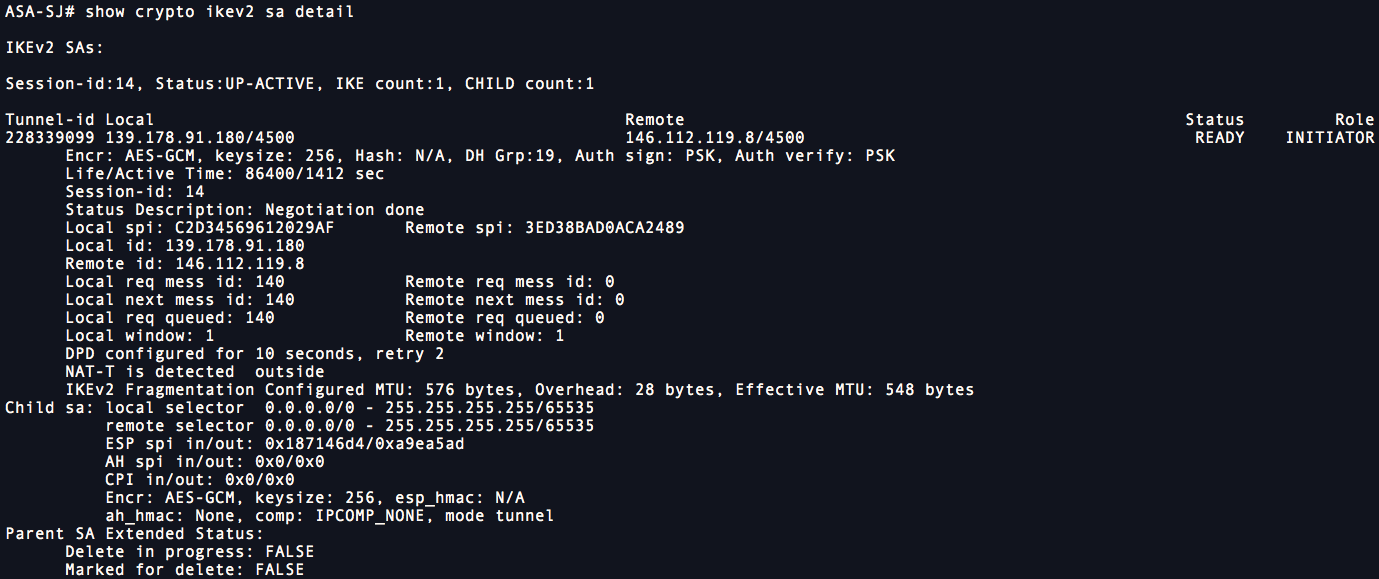
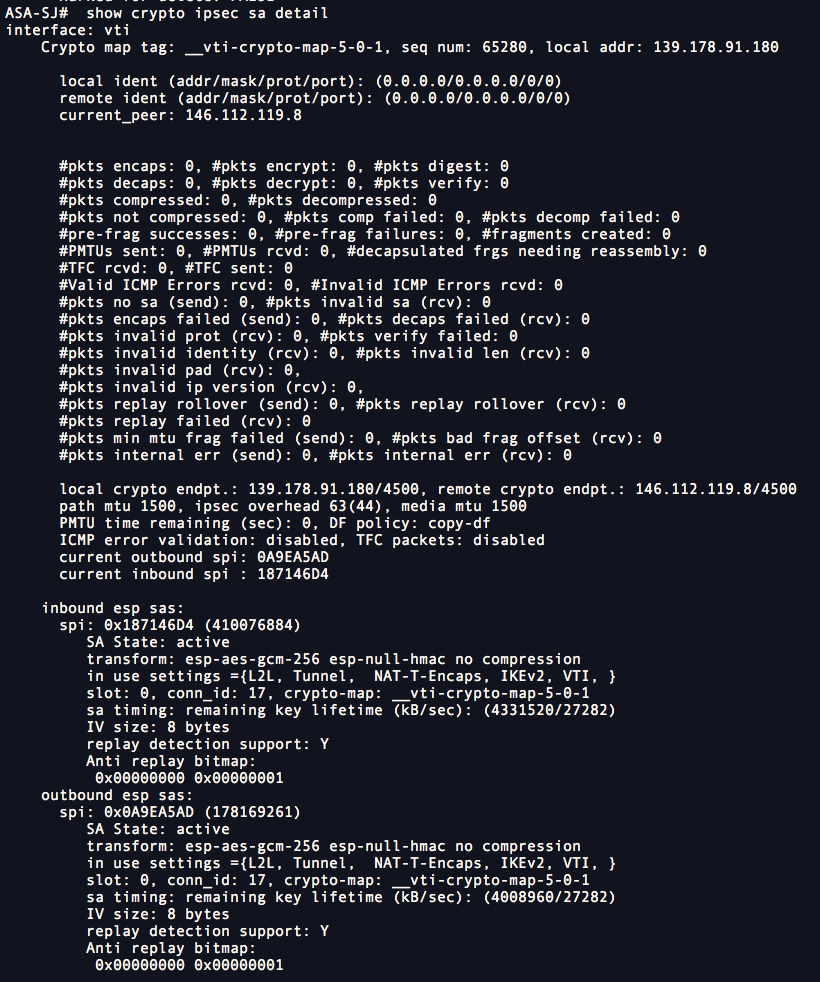
Use the following command to simulate a packet from the inside interface, with a specific source IP address and port and a specific destination IP address and port. The response indicates whether the packet flows through the tunnel.
packet-tracer input inside tcp 192.168.20.13 3520 72.163.4.161 443 detailed
Phase: 1
Type: ACCESS-LIST
Subtype:
Result: ALLOW
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d35d7da90, priority=1, domain=permit, deny=false
hits=3848, user_data=0x0, cs_id=0x0, l3_type=0x8
src mac=0000.0000.0000, mask=0000.0000.0000
dst mac=0000.0000.0000, mask=0100.0000.0000
input_ifc=inside, output_ifc=any
Phase: 2
Type: PBR-LOOKUP
Subtype: policy-route
Result: ALLOW
Config:
route-map sse-pbr permit 10
match ip address pbr-sse
set ip next-hop 11.11.11.12
Additional Information:
Matched route-map sse-pbr, sequence 10, permit
Found next-hop 11.11.11.12 using egress ifc vti
Phase: 3
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d34b62c90, priority=0, domain=nat-per-session, deny=false
hits=459, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 4
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x7f8d35d85db0, priority=0, domain=inspect-ip-options, deny=true
hits=456, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=inside, output_ifc=any
Phase: 5
Type: VPN
Subtype: encrypt
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
out id=0x7f8d35dfabc0, priority=70, domain=encrypt, deny=false
hits=152, user_data=0x78dc, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=vti
Phase: 6
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d36c3cd90, priority=69, domain=ipsec-tunnel-flow, deny=false
hits=152, user_data=0x84dc, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=vti, output_ifc=any
Phase: 7
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d34b62c90, priority=0, domain=nat-per-session, deny=false
hits=461, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 8
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional Information:
Reverse Flow based lookup yields rule:
in id=0x7f8d35e547a0, priority=0, domain=inspect-ip-options, deny=true
hits=291, user_data=0x0, cs_id=0x0, reverse, flags=0x0, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=vti, output_ifc=any
Phase: 9
Type: FLOW-CREATION
Subtype:
Result: ALLOW
Config:
Additional Information:
New flow created with id 547, packet dispatched to next module
Module information for forward flow ...
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_encrypt
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Module information for reverse flow ...
snp_fp_inspect_ip_options
snp_fp_ipsec_tunnel_flow
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_fp_tracer_drop
snp_ifc_stat
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: vti
output-status: up
output-line-status: up
Action: allow
Configure Tunnels with Cisco ISR < Configure Tunnels with Cisco Adaptive Security Appliance > Configure Tunnels with Cisco Secure Firewall
Updated 9 months ago
