View Firewall Events in Activity Search Report
The Activity Search report includes full details about Firewall requests that have been allowed or blocked by an Access Policy rule.
For more information about the Activity Search report, see View the Activity Search Report. For more information about your Access Policy rules, see Manage Access Policy.
Note: File Name and other fields related to file inspection and file type controls will only populate for events involving file access that match private access rules with File Inspection or File Type Control enabled. If no private access rules have File Inspection or File Type Control enabled, the file name and extension fields will remain blank for events with the Firewall request type. For more information, see Get Started With Private Access Rules, Manage File Inspection and File Analysis, and Manage File Type Controls.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Filter the Report by Firewall Requests
- Navigate to Monitor > Reports > Activity Search.
- Choose a time frame to view the report. You can view events from the last 24 hours (default), Yesterday, Last 7 Days, Last 30 Days, or a Custom range.
- The label FW in the Request column indicates a Firewall event.
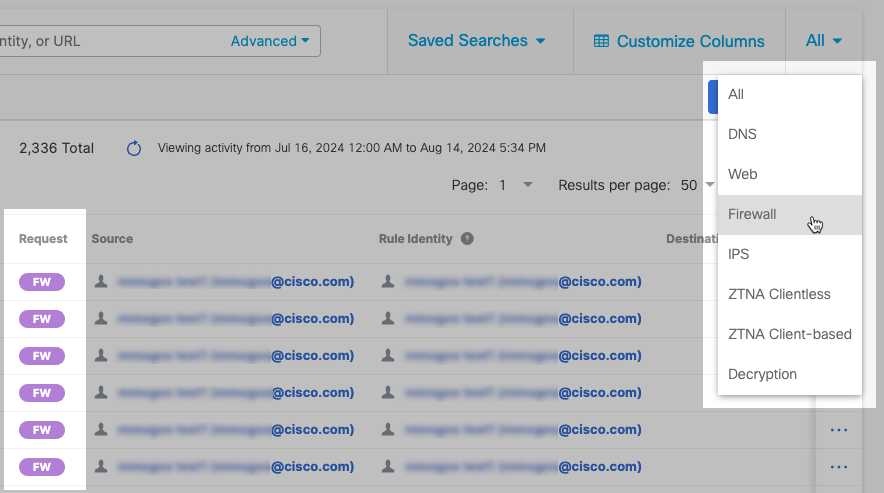
Select the Firewall option from the dropdown menu at the top right to filter the report for Firewall events. Columns and Filter options update to those that are relevant to Firewall events.
View Firewall Event Details
The Activity Search Report displays Event Details for each search result in a navigation drawer on the right. Click the row to view Event Details. The top part of an Event Details drawer is pictured below. For more information, see View Activity Search Report Actions.
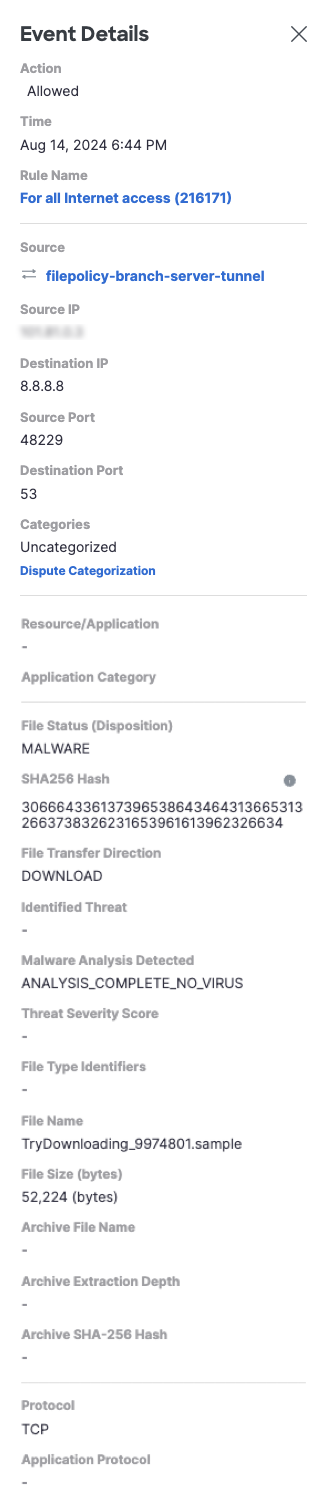
Firewall Event Details Fields
Firewall event details include the following fields that are also available as Activity Search report columns. For more information about these fields, see View and Customize the Activity Search Report.
- Action
- Time
- Rule Name
- Source
- Destination IP
- Categories
- File Name
- Protocol
- Application Protocol
Firewall event details also include the following fields that do not appear as Activity Search report columns.
| Field Name | Description |
|---|---|
| Source IP | The source IPv4 or IPv6 address. Supports both compressed and long-form IPv6 address formats. |
| Source Port | The source port. |
| Destination Port | The destination port. |
| Resource/Application | The name of the resource or application. |
| File Status (Disposition) | The file’s Cisco AMP disposition: - Clean: Indicates that the AMP cloud categorized the file as clean. - Malware: Indicates that the AMP cloud categorized the file as malware, or local malware analysis identified malware. - Unknown: Indicates that the system queried the AMP cloud, but the AMP cloud has not assigned the file a disposition. |
| SHA256 Hash | The checksum of the file, if available and the event matched rules with File Type Control or File Inspection enabled. |
| File Transfer Direction | DOWNLOAD, UPLOAD, or UNKNOWN, if the event matched rules with File Type Control or File Inspection enabled. |
| Identified Threat | The name of the detected malware. |
| Malware Analysis Detected | If the event matched rules with File Inspection enabled, this field shows one of the following values as a result of file analysis by Cisco Secure Malware Analytics. For more information, see Enable File Analysis by Cisco Secure Malware Analytics. - UNKNOWN - NOT ANALYZED - ANALYSIS COMPLETE NO VIRUS - ANALYSIS FAILED - ANALYSIS COMPLETE MALWARE DETECTED |
| Threat Severity Score | The threat score most recently associated with this file. This is a value from 0 to 100. |
| File Type Identifiers | The type of file. For example, PDF or MSEXE. |
| File Size (bytes) | The size of the file in bytes, if the event matched rules with File Type Control or File Inspection enabled. |
| Archive File Name | The name of the archive file involved with the activity, if the event matched rules with File Type Control or File Inspection enabled. |
| Archive Extraction Depth | The level (if any) at which the file was nested in an archive file. |
| Archive SHA-256 Hash | The checksum of the archive file, if the event matched rules with File Type Control or File Inspection enabled. |
View and Customize the Activity Search Report < View Firewall Events in Activity Search Report > View Web Events in Activity Search Report
Updated 5 months ago
