Meraki Registration
For Meraki administrators, once you have deployed the Cisco Security Connector (CSC), use the Meraki dashboard to deploy the app to devices using the instructions in the Meraki document Apple Volume Purchase Program (VPP). When your endpoints have registered with Secure Access, they will appear in the dashboard. For support, contact Meraki support.
Anonymization
Secure Access provides you with the option of anonymizing mobile devices for reporting and administration purposes. When you anonymize a mobile device, its label is hidden and replaced by your device's serial number. The label name is anonymized both in the Secure Access dashboard and in the CSC app UI. For information about how to anonymize your device, see Anonymize Devices.
Table of Contents
Prerequisites
- The Cisco Security Connector requirements.
- You must have a Meraki API key. For more information about acquiring a Meraki API key, see Cisco Meraki Dashboard API.
- The Cisco Security Connector app is installed on your iOS device (typically through MDM).
- Configure Meraki as required so that it can push configuration information to both CSC and Secure Access. For information about configuring Meraki, see Meraki documentation.
- If deploying to a supervised device, to ensure that the names in Secure Access match the Meraki portal name, enable device name updates under Restrictions > iOS Restrictions (Supervised) > Allow Modification of Device Name (Enable) > Keep Device Name Up-to-Date with Dashboard (Enable).
Meraki's Hide App Feature Incompatibility
The Cisco Security Connector is not compatible with Meraki's hide app feature.
Procedure
Note: You must log in to your Secure Access dashboard as an administrator.
- Navigate to Connect > End User Connectivity and click Internet Security. Click the iOS tab.
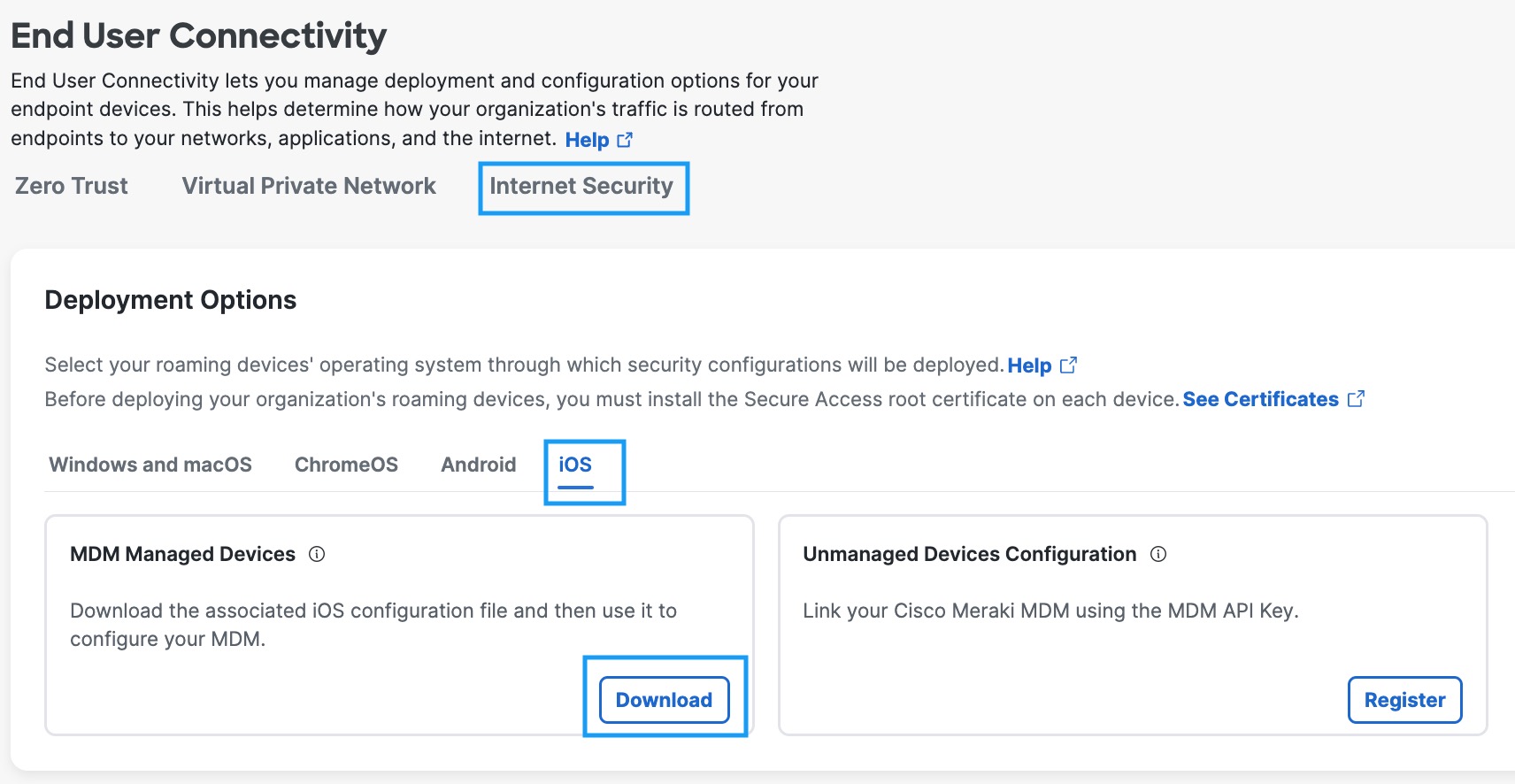
- Under the MDM Managed Devices section, click Download.
- In the Configure Managed iOS Clients window, click Link MDM.
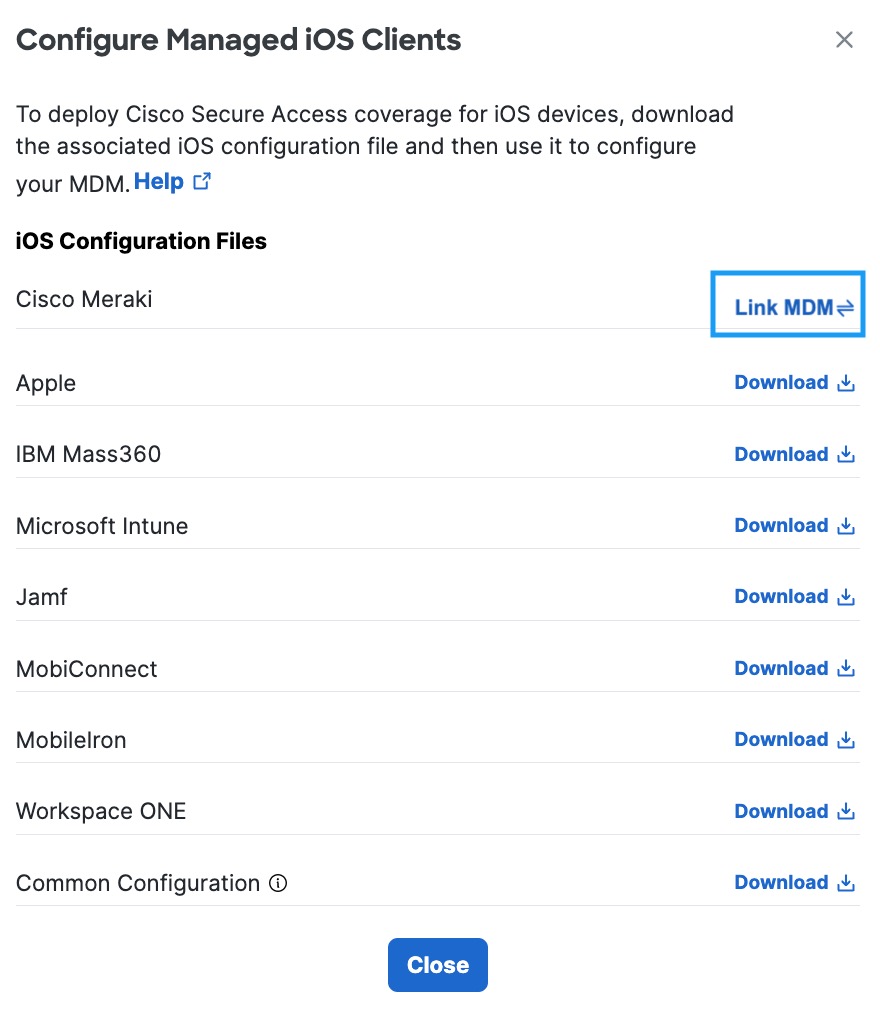
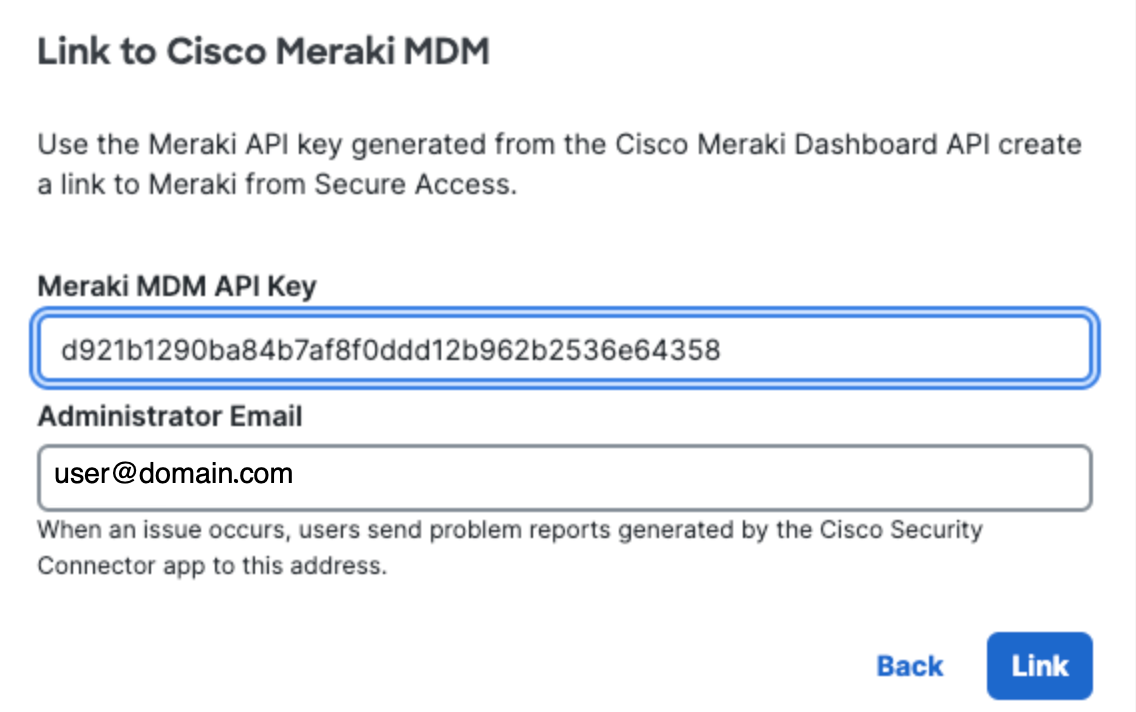
- Add your Meraki MDM API Key, optionally add an Administrator Email, and click Link.
This email address is where diagnostic reports are sent when a user clicks the I icon from within the iOS device. Once set, this email address is automatically added when managing an MDM.
Note: You acquire a Meraki MDM API key from the Meraki dashboard. For more information, see Cisco Meraki Dashboard API.
- In the Provision through Meraki MDM modal, select your MDM Profiles.
Note: While you can deploy more than one profile to an iOS device, if you try to deploy more than one profile with Secure Access applied, an error will occur and the second profile will not be applied. You can safely deploy a second profile with only Secure Access applied to a device that has an existing profile that only has Clarity applied.
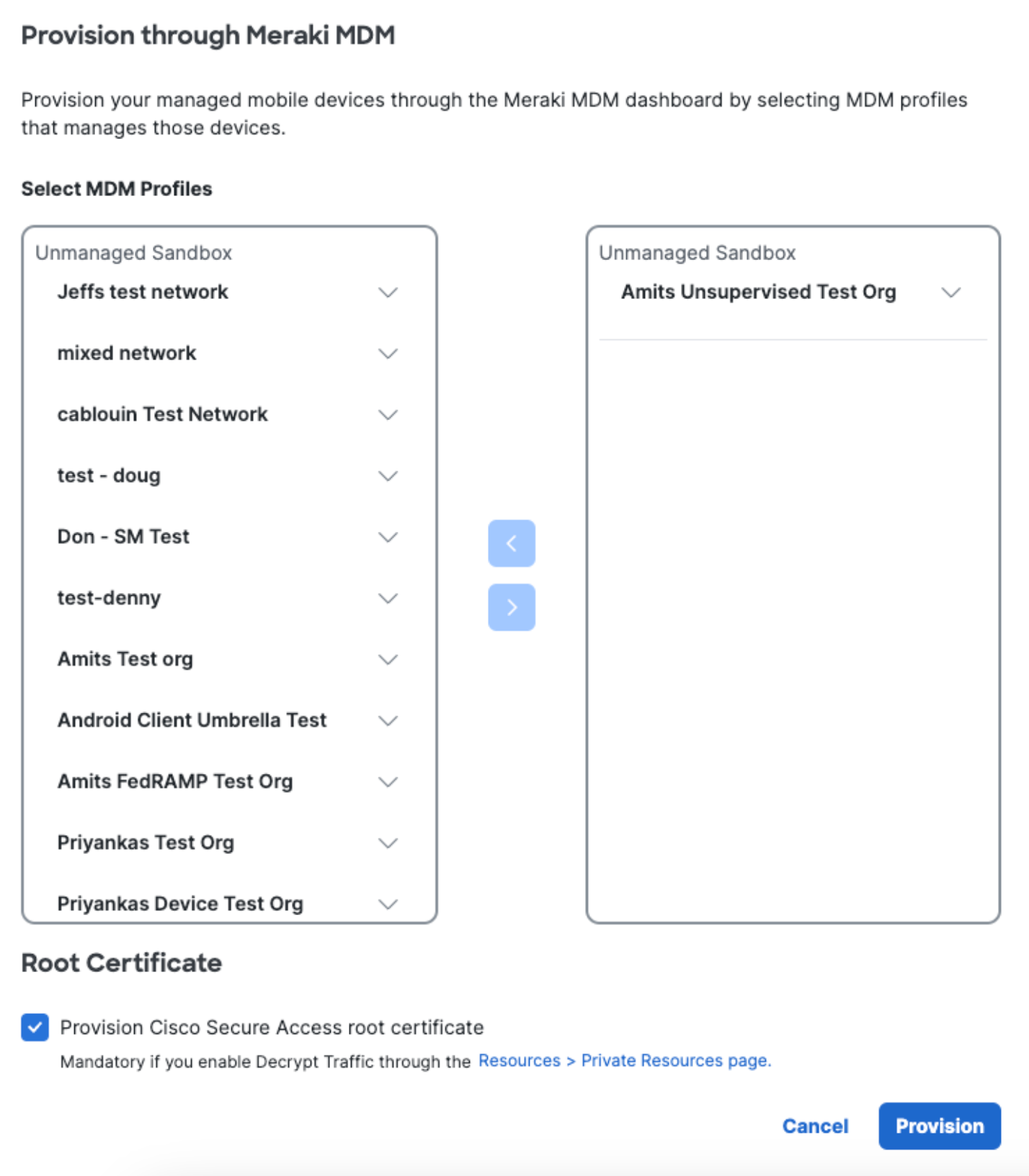
- Check Provision Cisco Secure Access Root Certificate.
The root certificate is required to perform SSL decryption for the intelligent proxy and also helps avoid error messages when visiting blocked pages. - Click Save.
If successful, your mobile device registers with Secure Access and is listed at Resources > Roaming Devices > Mobile Operating Systems. CSC on your mobile device updates to connect to Secure Access so that your iOS device is protected by Secure Access.
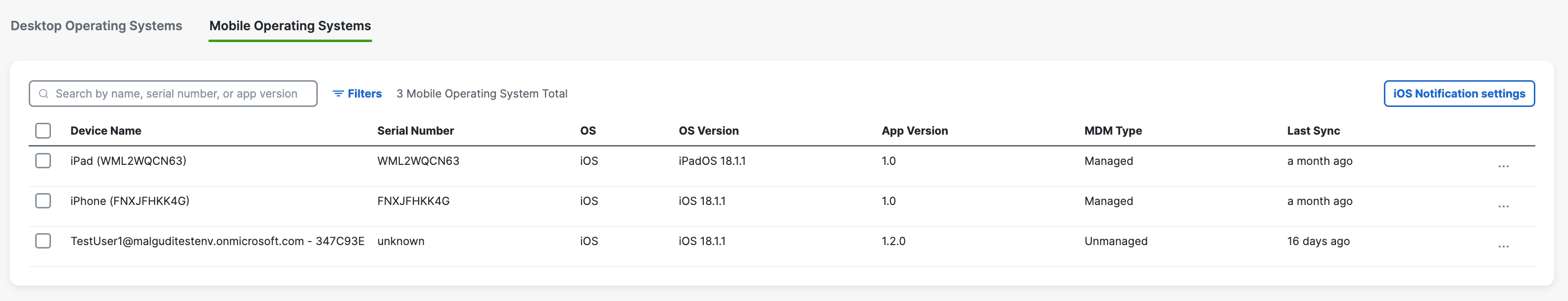
Verify Push of Profile Config
Once you have provisioned Secure Access, verify the push of the Secure Access Profile Config on your Meraki dashboard.
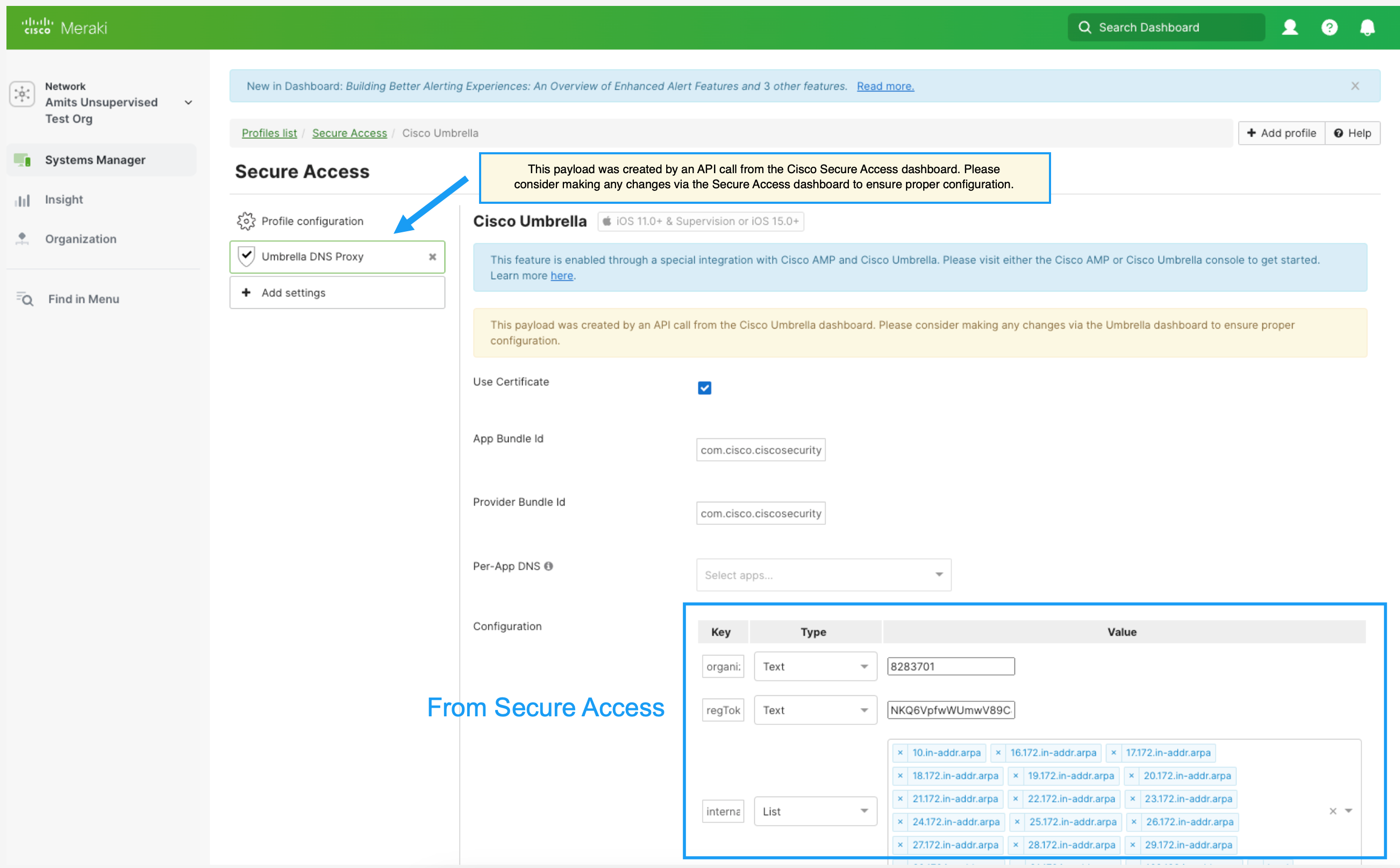
- In Meraki, navigate to Systems Manager > Settings.
You'll see an Secure Access DNS Proxy profile with configuration settings populated from Secure Access.
Anonymize Your Device
Secure Access provides you with the option of anonymizing mobile devices for reporting and administration purposes. When you anonymize a mobile device, its label is hidden and replaced by your device's serial number.
- In Meraki, navigate to Systems Manager > Settings and then select your profile.
- Under Value for anonymizationLevel, type 1.
Note: If anonymizationLevel is not listed, click Add Setting and add a Key with the value anonymizationLevel and Number with the value of 1.
A value of 0 turns anonymization off.
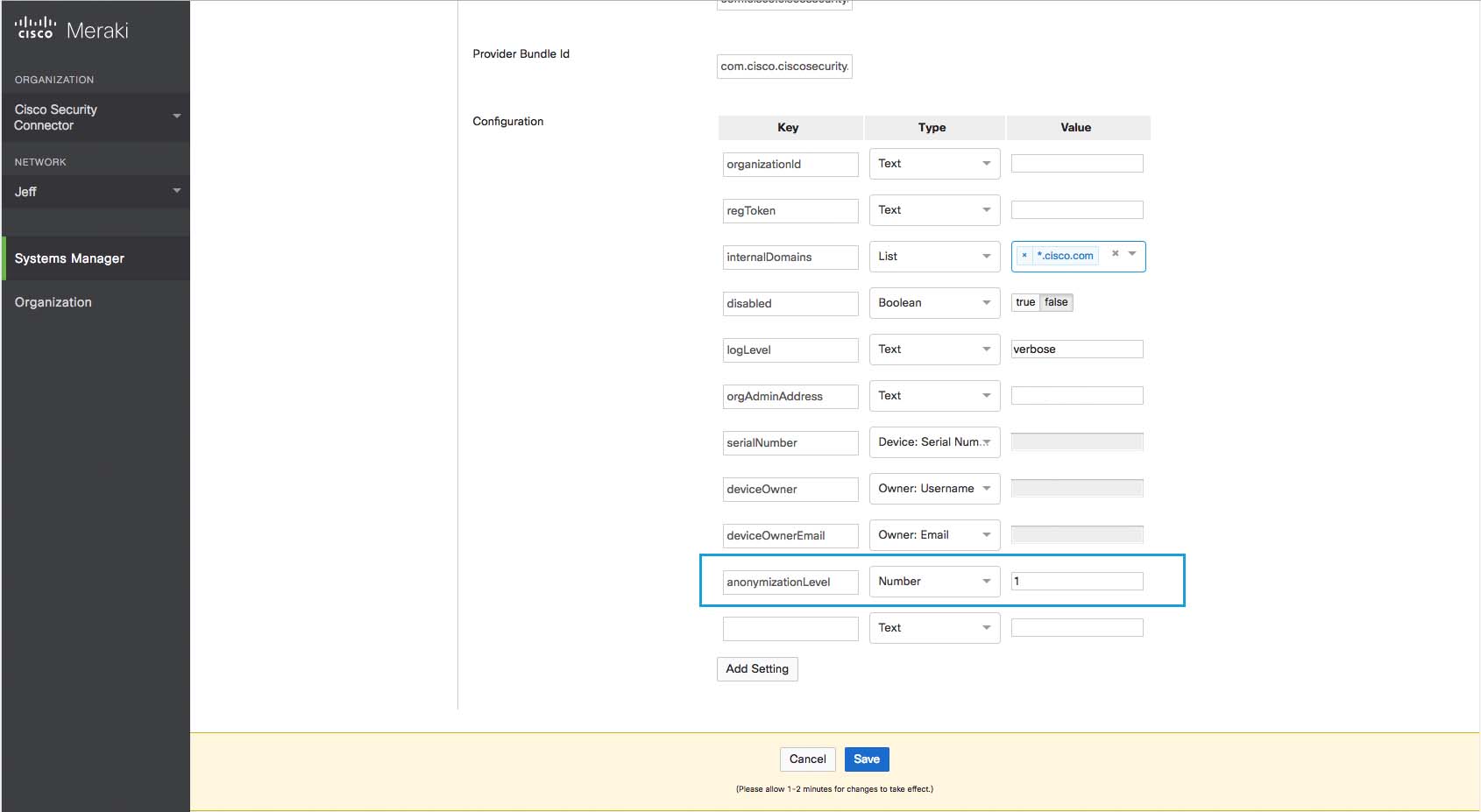
- Click Save.
Meraki pushes settings to Secure Access, and Secure Access hides the device's true label name by replacing it with the device's serial number. Existing active devices anonymize with 24 hours. New devices anonymize immediately.
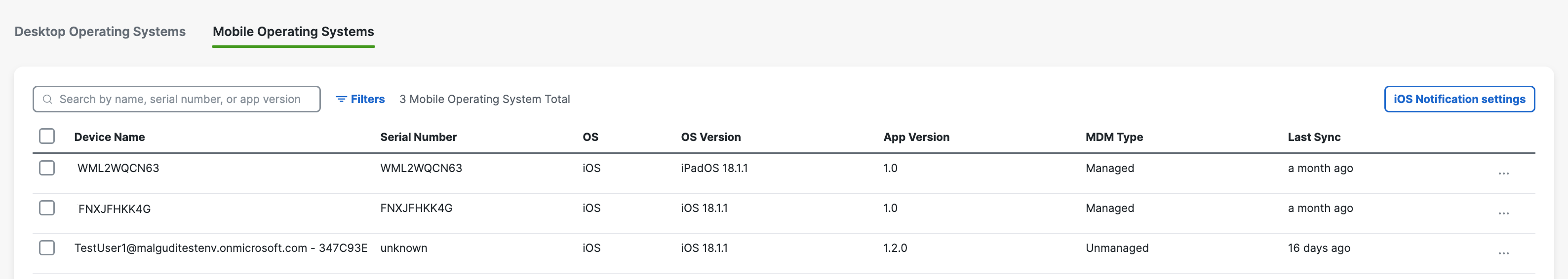
Verify Secure Access on Your Device
On your iOS device, verify that Secure Access is operational.
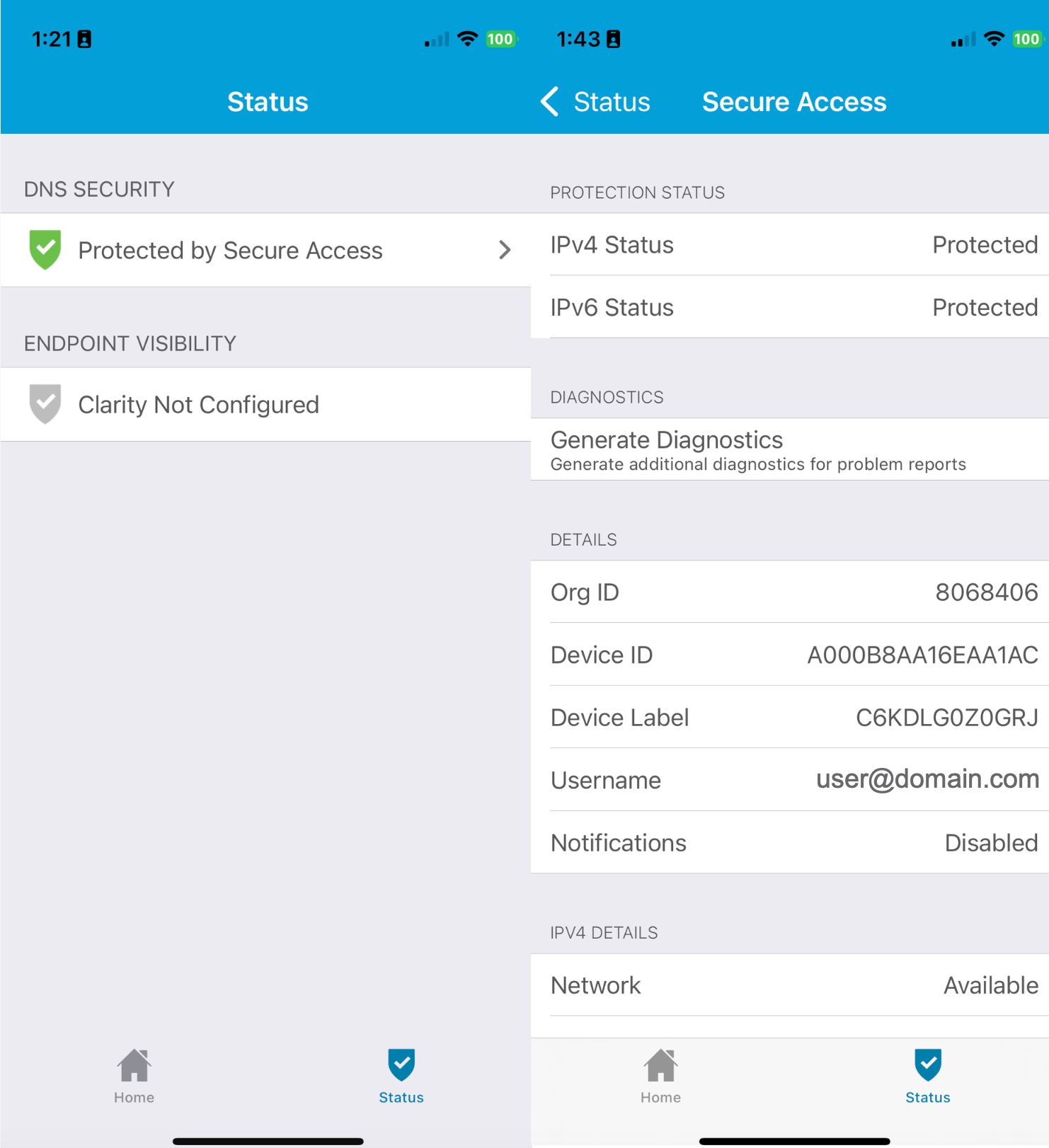
- In the CSC app, click the Status icon and confirm that it shows Protected by Secure Access.
- For protection details, tap Protected by Secure Access.
Manage Device Deployment< Meraki Registration > Verify Secure Access with Meraki
Updated about 1 month ago
