Dynamic Routing with BGP
Border Gateway Protocol (BGP) automates the exchange of routing information between autonomous systems (AS) to determine optimal paths for data traffic and failover routing without the need to configure and maintain static routes.
You add network tunnel groups to Secure Access to enable secure network connections to the internet and private resources. When setting up a network tunnel group, choose dynamic routing when you have a BGP peer for your on-premise router.
Dynamic routing using BGP enables the advertisement of customer-specific routes, ensuring the Secure Access tunnels can route return traffic. Without these routes, the Secure Access tunnels cannot properly route return traffic to the customer networks.
For more information about BGP, see Cisco Support documentation topics Select BGP Best Path Algorithm and Examine Border Gateway Protocol Case Studies
Table of Contents
- BGP Guidelines and Best Practices for Secure Access
- Secure Access BGP Configuration
- Multi-region backhaul across Secure Access regions
- Key Considerations for Dynamic Routing
- Tunnel Redundancy and High Availability
- View BGP Routes
- Important Restrictions
BGP Guidelines and Best Practices for Secure Access
Follow these guidelines when configuring dynamic routing for Secure Access network tunnel groups.
Secure Access BGP Configuration
BGP Peer IPs
- SSE Side: Use an IP address within the 169.254.0.0/24 range; for example, 169.254.0.5 for the primary data center and 169.254.0.9 for the secondary data center.
- Customer Side: Match these IPs within the 169.254.0.0/24 range whenever possible; for example with 169.254.0.6 (for 169.254.0.5) and 169.254.0.10 (for 169.254.0.9). We recommend this for ease of configuration. However, this is not mandatory and the customer-side IP range can be different and/or outside the 169.254.0.0/24 range.
BGP Identifier (Router ID)
- Do not use 169.254.0.1 as the BGP identifier.
- Use the local router gateway address (typically in the RFC1918 space, e.g., 192.168.x.x) as the customer-side BGP identifier. Avoid using addresses in the 169.254.0.0/24 range.
Note: Some devices refer to the BGP identifier as the Router ID.
Multi-region backhaul across Secure Access regions
Secure Access network tunnel groups can support a customer backhaul network that spans multiple Secure Access regions when the following conditions are met:
- The customer backhaul network is connected to two or more Secure Access network tunnel groups with Multi-region backhaul enabled.
- The customer backhaul network uses BGP to advertise subnet prefixes and preferences to Secure Access.
Upon creation of a network tunnel group with multi-region backhaul enabled, Secure Access will advertise a BGP community string to the customer backhaul in the format 32644:X, where 32644 is the Cisco Secure Access public ASN and X encodes regional priority. The customer backhaul network policy can transform this BGP community string to a priority in routes propagated internally. If the backhaul uses iBGP, it can transform the string to a local preference. If the backhaul uses EIGRP, it can transform the string to an EIGRP metric. The result is the preservation of routing symmetry with Secure Access.
On the Secure Access side, each region will distribute routes to all regions. Secure Access will also advertise subnet prefixes, preferences, and AS path length to optimize routing between regions and the customer backhaul, or between remote access VPN (RAVPN) users and the customer backhaul.
Multi-region backhaul supports the following:
- When a primary tunnel fails, the network tunnel group will failover to the secondary tunnel within the region.
- When a region fails, Secure Access will failover to another region connected to the customer backhaul. Note: Multi-region backhaul must be enabled on all network tunnel groups to support regional failover.
- When an RAVPN user connects to a region that is not connected to the customer backhaul and the requested private resource, Secure Access will forward the RAVPN user traffic to the appropriate region to complete the request.
- Secure Access advertisement of RAVPN user route prefixes and preferences to the customer backhaul to support optimal routing of return traffic and avoidance of asymmetric routing by customer routers.
This diagram shows a private resource in a customer backhaul network spanning Secure Access Regions A and B. Region C is not connected to the backhaul. All three regions share routing information.
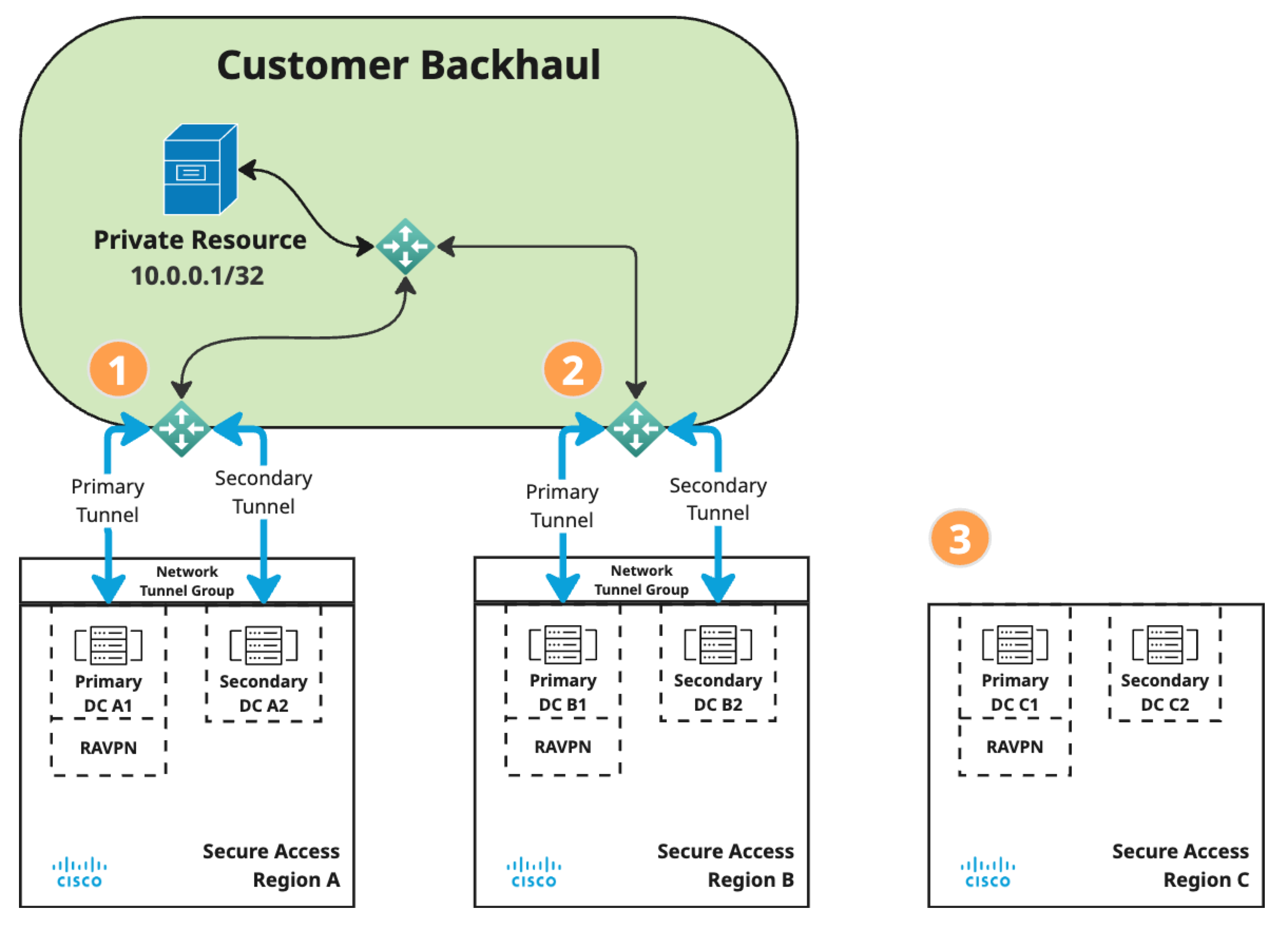
The customer IPSec router is connected to a network tunnel group in Secure Access Region A. As advertised by BGP in this example, this is the customer's preferred route to the subnet prefix 10.0.0.1/32.
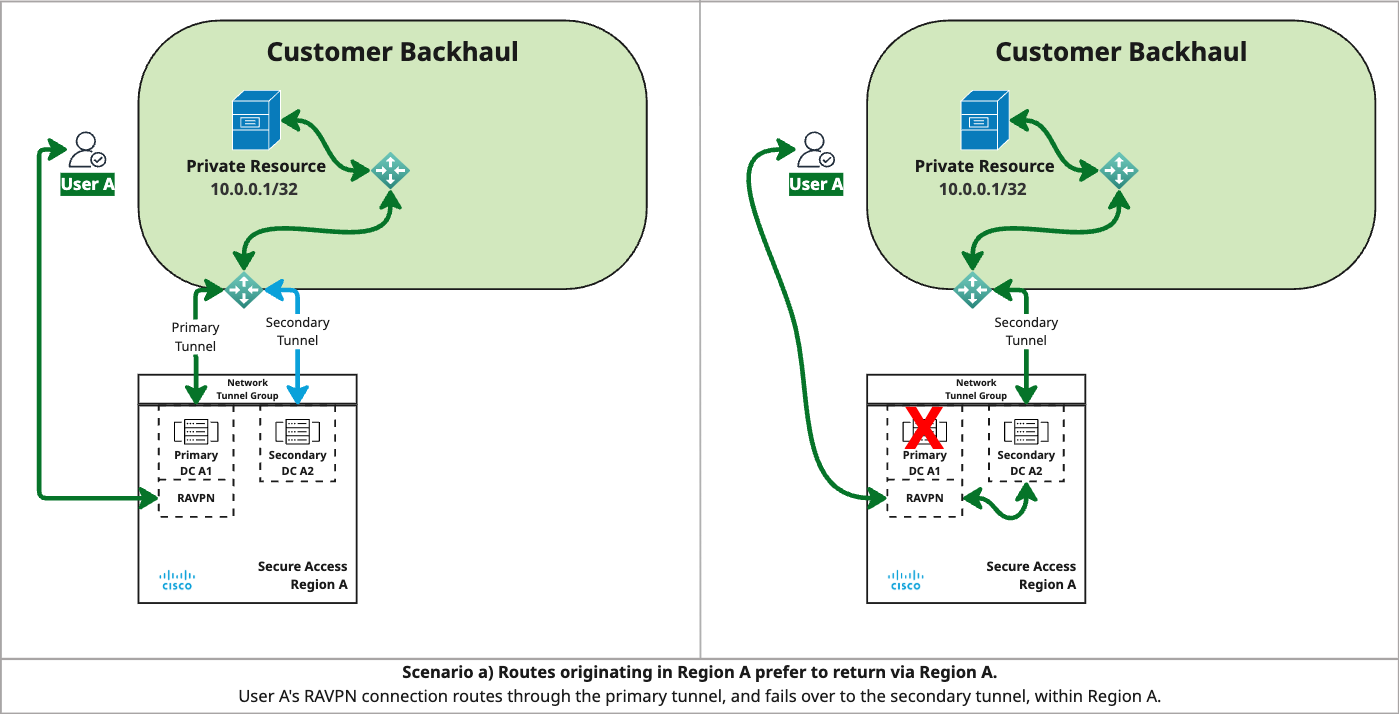
In the diagram for scenario a:
- Region A learns routes advertised for both Region A and Region B, but prefers local routes.
- RAVPN User A accesses the private resource via the primary tunnel in Region A.
- If the primary tunnel goes down, the tunnel group fails over to the secondary tunnel within Region A.
In the diagram for scenario b:
- Region B learns routes advertised for both Region A and Region B, and prefers local routes.
- User B connects to RAVPN via DC B1 in Region B and accesses the private resource via the primary tunnel in Region B.
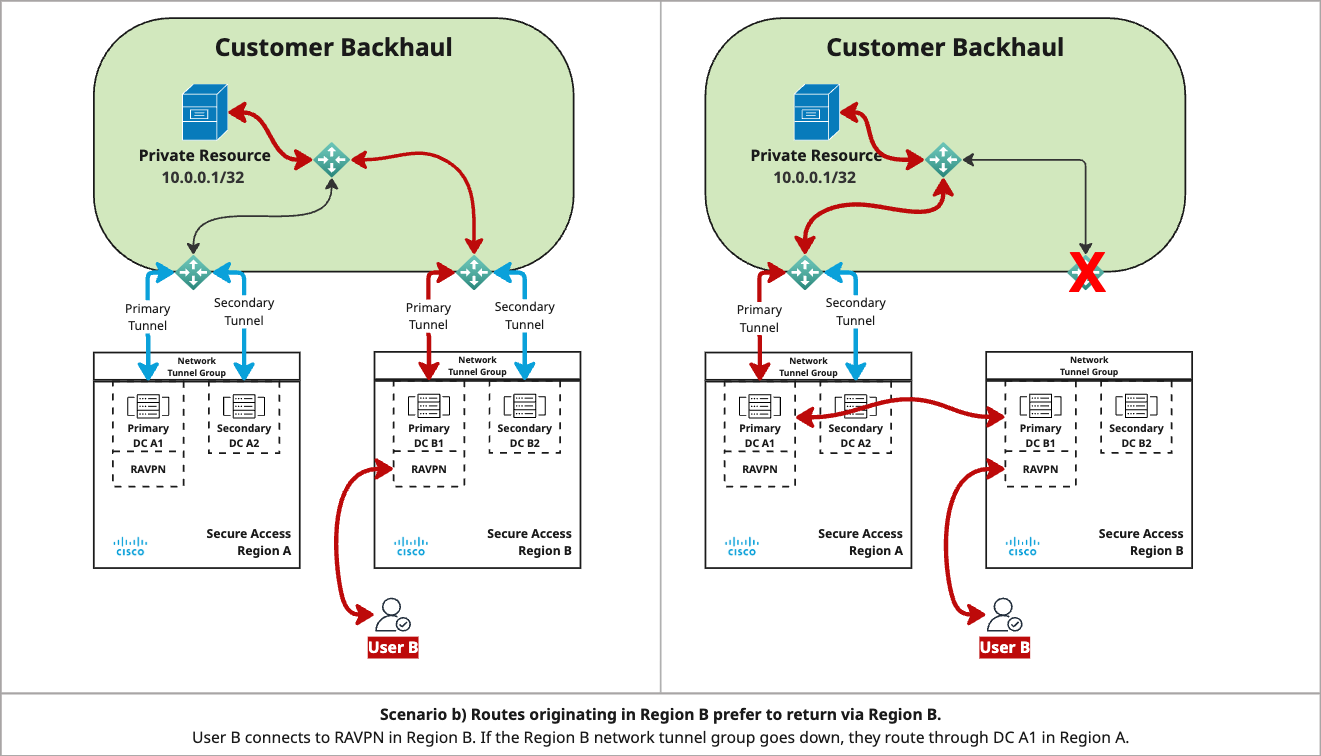
- If the network tunnel group between Region B and the customer backhaul goes down, User B fails over to the primary tunnel in Region A.
Note: In this scenario, both network tunnel groups in Secure Access must have Multi-region backhaul enabled to support regional failover.
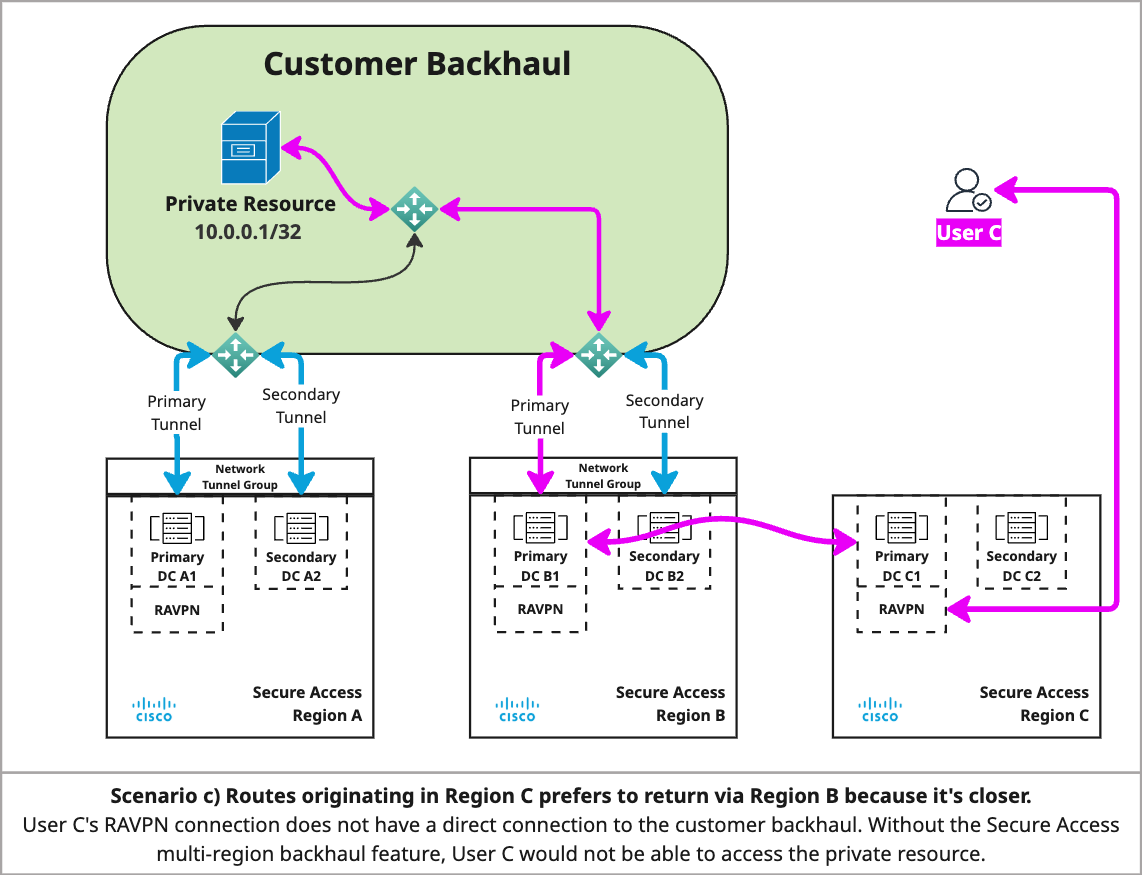
In the diagram for scenario c:
- Region C does not have a direct connection to the customer backhaul, so it cannot use local routes to reach the private resource. Without Multi-region backhaul enabled for Region B, User C would not be able to access the private resource.
- Region C learns routes advertised for both Region A and Region B, but prefers Region B because it is closer to Region C.
For more information, see Add a Network Tunnel Group, View Network Tunnel Group Details, and Secure Access Regions.
Key Considerations for Dynamic Routing
Advantages of Using BGP Dynamic Routing
- Automatic Route Updates: When route changes occur on the customer side, they are automatically communicated to the Secure Access side without requiring manual updates in the dashboard settings.
- Dynamic Failover: If a tunnel on the Secure Access side goes down, the routes sent to the customer dynamically adjust, allowing seamless failover to a secondary tunnel.
Customer AS Number
- Use any private BGP AS number in the range 64513–65534.
- Avoid conflicts: 64512 is the AS number reserved for Secure Access.
Tunnel Redundancy and High Availability
Network Tunnel Group Configuration
- A single network tunnel group can support multiple IPsec tunnels for redundancy and high availability.
- Typically there would be a 1-to-1 correspondence between primary and secondary IPsec tunnels. For example, if you configure six IPsec tunnels to the primary data center for ECMP, you would have six corresponding IPsec tunnels to the secondary data center. This setup requires 12 BGP connections, one per IPsec tunnel.
ECMP Support
- Secure Access supports Equal-Cost Multi-Path (ECMP) across primary IPsec tunnels in the same network tunnel group. If the primary tunnels are not available, secondary tunnels are used and ECMP will happen across the secondary tunnels.
- To enable ECMP, create multiple IPsec tunnels in the same data center and advertise the same prefix on all BGP connections associated with that network tunnel group.
Tunnel and Device Aggregation
- You can aggregate IPsec tunnels from different devices in the same network tunnel group when those devices are part of an HA pair, either in Active/Active mode or Active/Standby mode.
- Do not aggregate multiple IPsec tunnels from different devices that are not part of an HA pair in the same network tunnel group.
Route Advertisement by Secure Access
- Routes advertised by Secure Access prepend the original AS path to include 1 for primary tunnels and 2 for secondary tunnels, thus preserving the original AS path.
- This allows customers to install all received routes in their Forwarding Information Base (FIB) and switch between primary and secondary routes based on routing decisions.
Connecting Multiple Devices in HA to Secure Access
- Secure Access allows you to connect multiple HA routers from the same branch to Secure Access, either in Active/Active mode or Active/Standby mode.
- The two devices should advertise the same set of routes to Secure Access and use the AS path length to define the device priority; you should prepend the AS path length for Standby devices.
- All IPsec tunnels from all HA routers should belong to the same Network Tunnel Group.
- For example, if you want to connect two devices to Secure Access in Active/Active mode, use the same AS path length for all routes advertised by the two devices.
- If you want the devices to be in Active/Standby mode, advertise routes from your Active device with a shorter AS path length (e.g. length of 1 for routes coming from the Active device and 2 for routes coming from the Standby device).
- You can connect as many HA routers as you want to Secure Access but you are limited to 20 IPsec tunnels overall for a Network Tunnel Group; 10 IPsec tunnels to the primary and 10 IPsec tunnels to the secondary.
View BGP Routes
Monitoring Client Routes
- To view BGP routes received from the customer side, go to the Network Group page in the Secure Access dashboard.
- Click on a network tunnel to open the details pane on the right-hand side of the page. The Client Routes section shows received routes.
- Routes can be seen on the primary tunnels. If there are multiple primary tunnels advertising the same route, the route would be seen on each primary tunnel.
- All other routes for an organization (not coming from the primary tunnel) are shown in the Cloud routes section of the Secure Access dashboard.
Important Restrictions
Default Route Advertising
-
Advertising default routes via BGP from the customer to Secure Access is not supported and can lead to traffic disruptions.
-
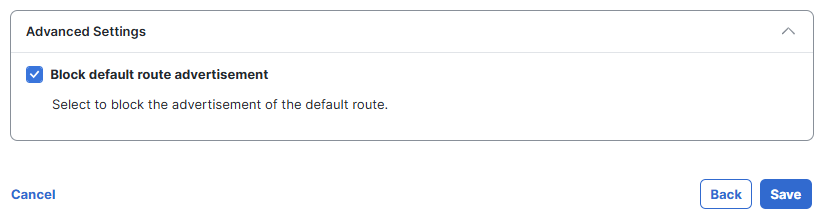
You can block default route advertisements from Secure Access to the customer site. From the Secure Access dashboard, go to Connect > Network Connections > Network Tunnel Groups. In the Advanced Settings of the network tunnel group routing configuration, check Block default route advertisement.
Avoid Router ID and BGP Peer Conflicts
- BGP requires a Router ID to establish BGP sessions between peers. If BGP does not have a Router ID, it cannot establish any peering sessions with BGP peers.
- When configuring Secure Access network tunnel groups, an organization can use the same BGP peer IPs for any or all of its network tunnel groups in the same region.
- However, the BGP Router ID must be unique to the BGP peers in a network. In other words, each router in the network must have a unique Router ID.
Static Routing < Dynamic Routing Using BGP > Configure Tunnels with Cisco Catalyst SD-WAN
Updated 3 days ago
