Add a Real Time Rule to the Data Loss Prevention Policy
There is only one data loss prevention policy. Rules are added to the policy to define what traffic to monitor (resources and destinations), the data classifications that require monitoring, and whether content should be blocked or only monitored.
A Real Time rule must have at least one of the following three criteria defined:
- Data Classifications — Include files that match data classification of your own making or a built-in data classification provided by Secure Access.
- File Labels — Include files that have specific file label names configured in the value of the files' document properties.
- File Size — Include files that meet custom size criteria.
Prerequisites
- HTTPS Inspection must be enabled either on the default Access policy, or at least one access policy rule where the same identity is configured in a DLP rule. For example, if the resource "Network A" is configured for a DLP rule, it must also be configured for an access policy rule where HTTPS is enabled. For more information, see Manage Traffic Decryption and Manage Web Profiles.
- If you create a real time rule to protect any destinations that are private resources you must first:
- Define the private resource
- Define the certificate the Data Loss Prevention policy needs to decrypt the traffic going to that destination. See Add a Private Resource for details.
- Enable global decryption.
- Full Admin user role. For more information, see Manage Accounts.
Procedure
- Navigate to Secure > Policy > Data Loss Prevention Policy, click Add Rule, and choose Real Time Rule.
- Under Add New Real Time Rule, give your rule a meaningful name and description.
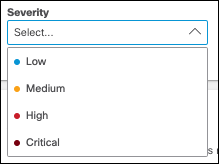
- Choose a severity for your rule based on the risk involved or importance within the ruleset.
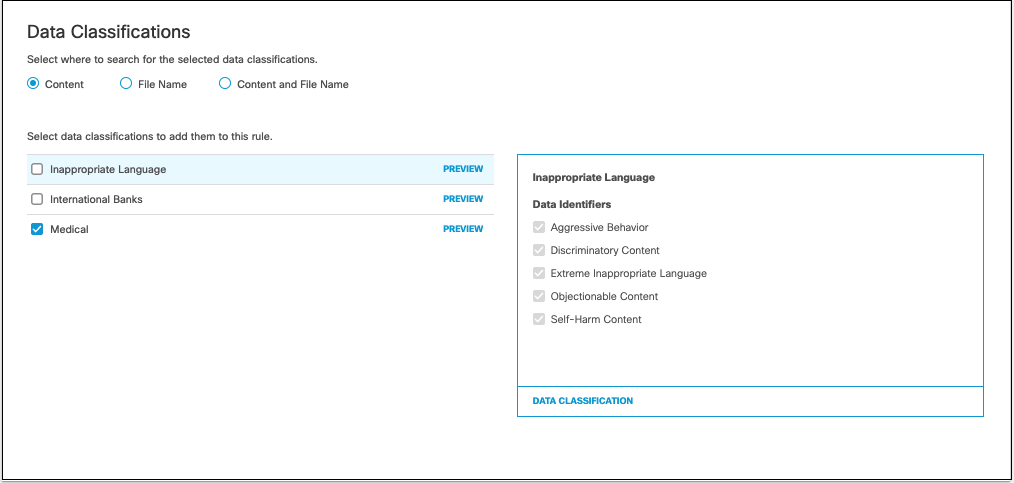
- Choose where you would like this rule to search for data classifications.
- Content—(Default) Searches only the content of files for the selected data classifications.
- File Name—Searches only file names for the selected data classifications.
- Content and File Name—Searches content and file names for the selected data classifications. Both content and file name do not need to match for the rule to apply, only one or the other.
Note: Choosing Content, File Name, or Content and File Name refers to scanning file uploads for the selected data classifications and configured file labels.
- Select classifications to apply this rule. For more information, see Manage Data Classifications.
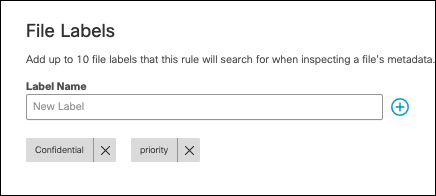
- Add up to 10 case-sensitive file label names to apply to this rule. The rule will search for any of the configured file label names in the value of the files' document properties. This includes Microsoft Office Sensitivity Labels and Adobe PDF Document Properties. For Microsoft Office Document Properties , this includes only the Label Value field in the custom document properties. File uploads to Confluence and Jira are not scanned for file labels.
Note: A DLP rule can be configured with either data classifications or file labels or both. When a DLP rule is configured with both, then a DLP event is raised when any of the selected data classifications and when any of the configured file labels are detected in the inspected file.
Microsoft Sensitivity Labels
Secure Access currently supports detection of Microsoft sensitivity labels in the file properties’ values of the inspected file for Microsoft Word, Excel, PowerPoint, and .pdf files. Ensure you configure the rule with the name of the sensitivity labels, not the Display Names.
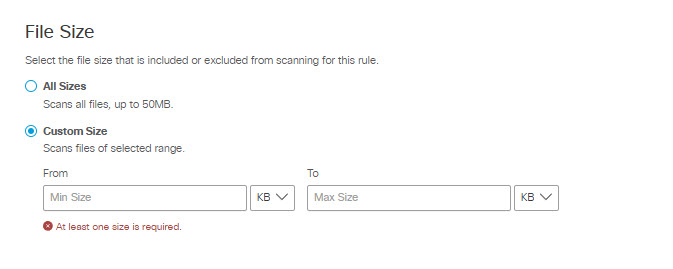
- The File Size area has two use cases:
- In a rule that specifies a custom file size but no other criteria, DLP applies the rule action to files that match the file size criteria, regardless of content. (This may be useful in situations where you want to exclude certain low-risk files below a certain size from inspection, so as not to waste processing time on insignificant events.)
- In a rule that specifies a custom file size along with other criteria such as Data Classification, the DLP applies the rule action to files that match the other criteria within the file size specified up to the first 50 MB of plain text. (Secure Access does not scan file content beyond the first 50 MB regardless of the file size specified here.)
In the File Size area choose from two options:
- All Sizes to scan up to the first 50 MB of plain text of all files that meet other criteria defined by this rule. (A rule that specifies All Sizes must also specify either Data Classifications, File Labels, or both.)
- Custom Size to specify the minimum and maximum size limits the system will scan for files that meet other inclusion criteria defined by this rule, if there are any. If the file size exceeds the first 50 MB of the file, Secure Access scans only up to the first 50 MB of plain text in the file. (I.e., if you specify a minimum file size greater than 50 MB, Secure Access will not scan for other criteria specified in the rule.)
You can choose to apply the rule action only to files that are greater than a minimum size you specify, or to files that are within a range of sizes you specify. (If you specify a maximum size without specifying a minimum size, the minimum size defaults to 0.) You can specify file sizes in KB or MB.
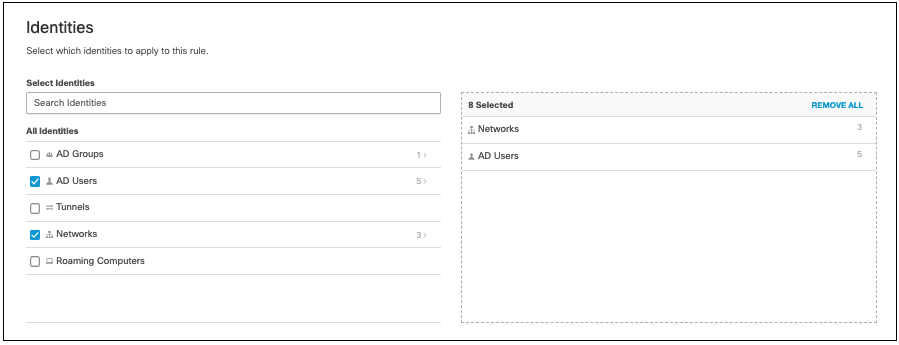
- Select identities to apply to this rule.
- Under Destinations, select All Destinations or Select Destination Lists and Applications for Inclusion.
- All Destinations—Monitors all outbound web requests or blocks all file uploads that originate from the selected identities for this rule.
When All Destinations is selected, you can select the type of data Secure Access monitors:- Choose File uploads and form data to monitor all uploaded files and forms data for all web destinations users visit.
Use care when choosing All Destinations File uploads and form data because it significantly widens the scope of the data the rule scans and can result in excessive false positives, blocking users' access to many sites inappropriately. We recommend that rules applied to all destinations not include built-in identifiers with lenient tolerances or custom identifiers with regexes that define a broad scope. Design regexes to narrowly identify the data you seek, and include threshold and proximity criteria.
- Choose File uploads and form data of vetted applications only to monitor all uploaded files and forms data associated only with DLP Supported Applications.
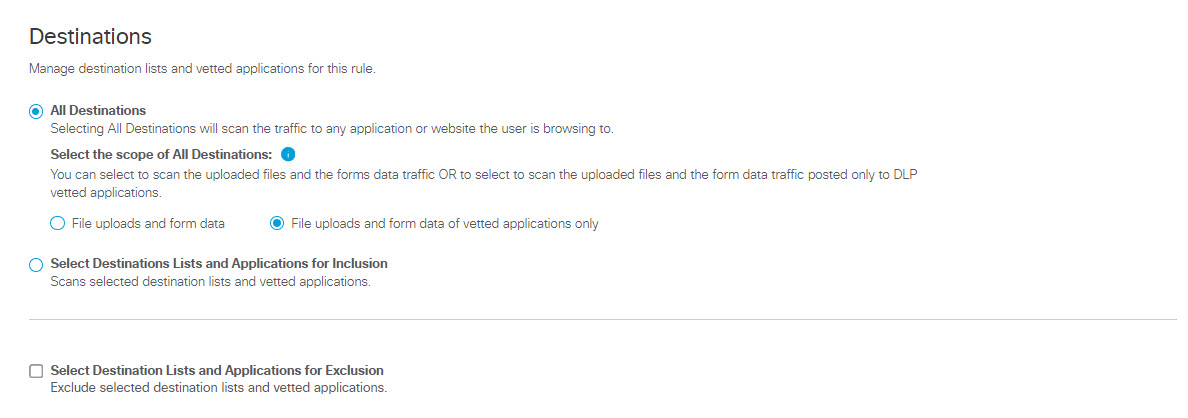
- Choose File uploads and form data to monitor all uploaded files and forms data for all web destinations users visit.
- Select Destination Lists and Applications for Inclusion—Monitors all web requests and blocks all file uploads matching the identities selected on the rule, the selected destination lists, and supported applications.
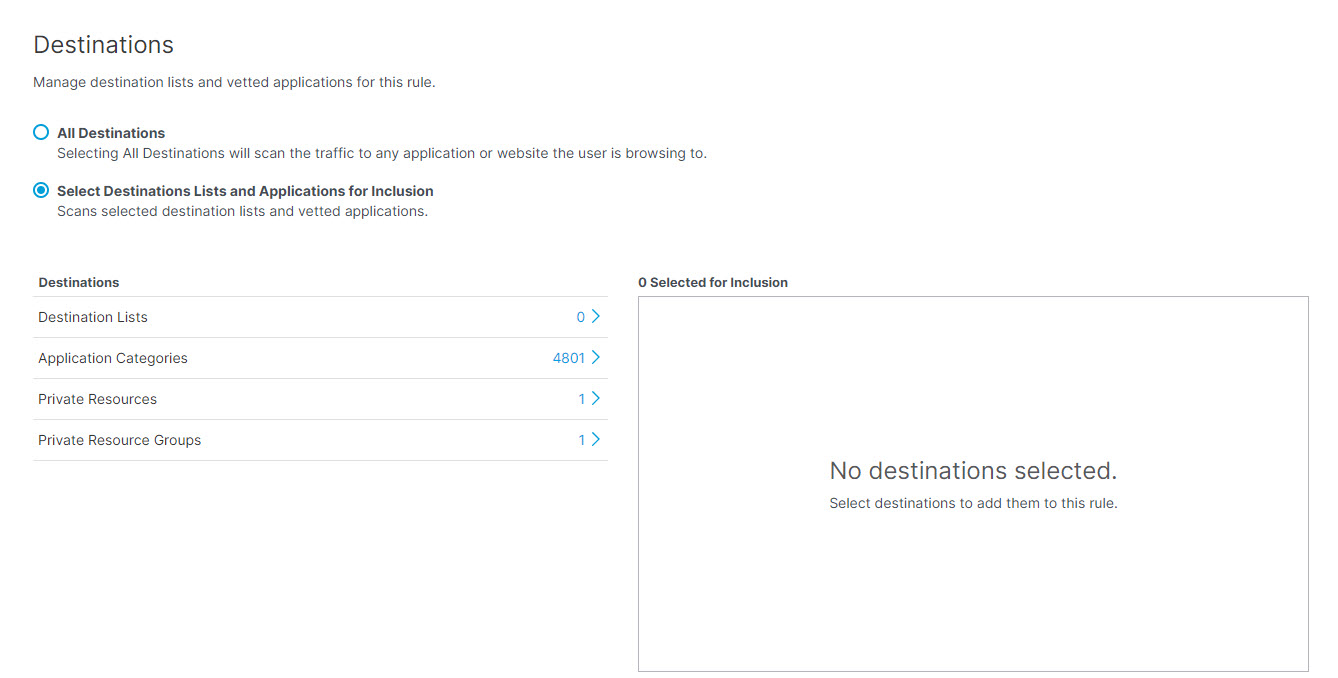
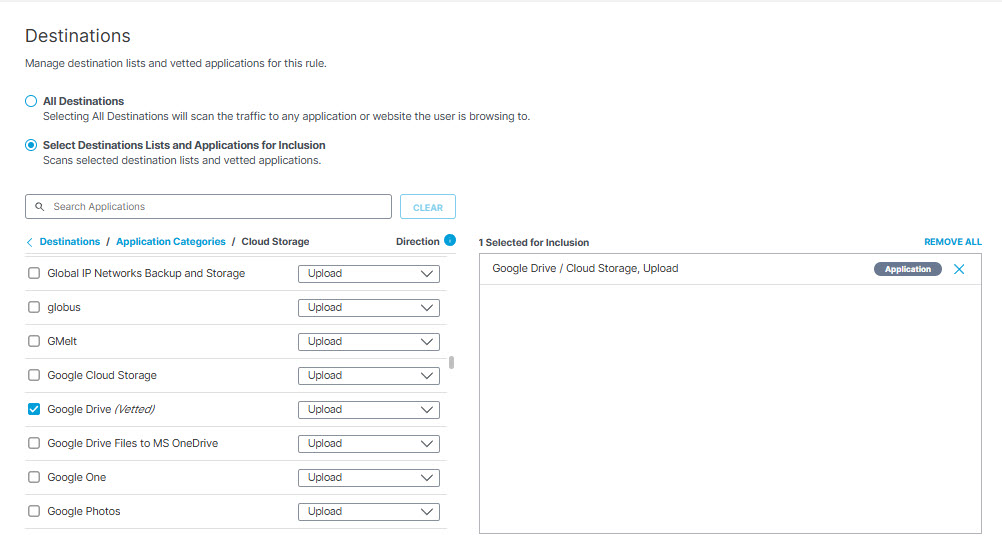
- To add applications for inclusion, under Destinations expand Application Categories. (See Application Categories) for a list of available categories.) Expand categories and check the boxes for the applications you want to add to the rule. You can search for an application by entering at least three consecutive letters from the application name in the search box.
Note: It is not possible to search for an application with fewer than three letters in its name—for example, "QQ" or "YY." These applications must be manually selected from the hierarchy under their respective categories, or wildcarded in search—for example, "QQ*". This behavior is by design.
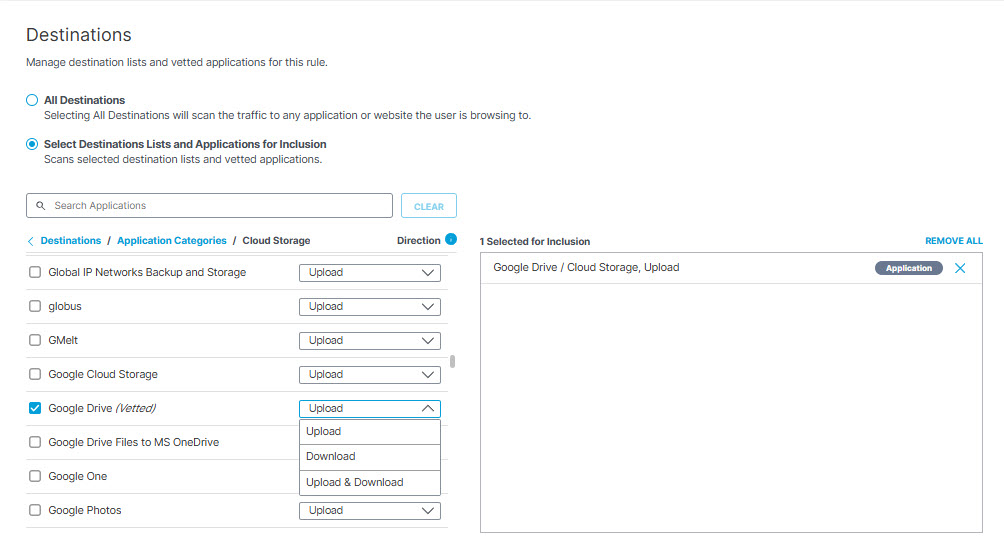
You can scan one of three traffic direction options for application and categories: Upload (from your system to the application), Download (from the application to your system), or Upload and Download. When you select a traffic direction for an application category, that selection applies to all applications within that category.
Note: Not all applications support scanning of all three traffic direction options. The system does not display a traffic direction option for an application unless that option is supported.
- To add private resources for inclusion, under Private Resources select the resource you want to scan. You can also select the direction of traffic associated with the resources that you want scanned: Upload, Download, or Upload & Download. You can search for a resource by entering at least three consecutive letters from the resource name in the search box.
Note: See Prerequisites before including a private resource.
Note: It is not possible to search for a private resource with fewer than three letters in its name—for example, "QQ" or "YY." These resources must be manually selected, or wildcarded in search—for example, "QQ*". This behavior is by design.
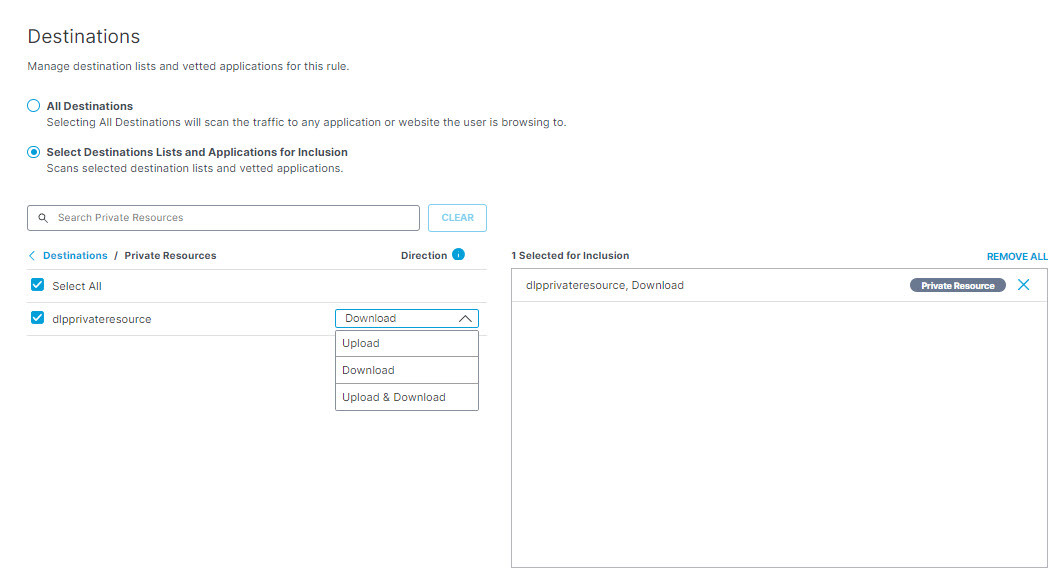
Secure Access DLP supports scanning private resources in HTTP/s traffic in both upload and download directions for all supported file types, but does not support scanning forms data.
- To add private resource groups for inclusion, under Private Resource Groups select the resource group you want to scan. You can also select the direction of traffic associated with the resource groups that you want scanned: Upload, Download, or Upload & Download. You can search for a resource group by entering at least three consecutive letters from the resource group name in the search box.
Note: See Prerequisites before including a private resource group.
Note: It is not possible to search for a private resource group with fewer than three letters in its name—for example, "QQ" or "YY." These resource groups must be manually selected, or wildcarded in search—for example, "QQ*". This behavior is by design.
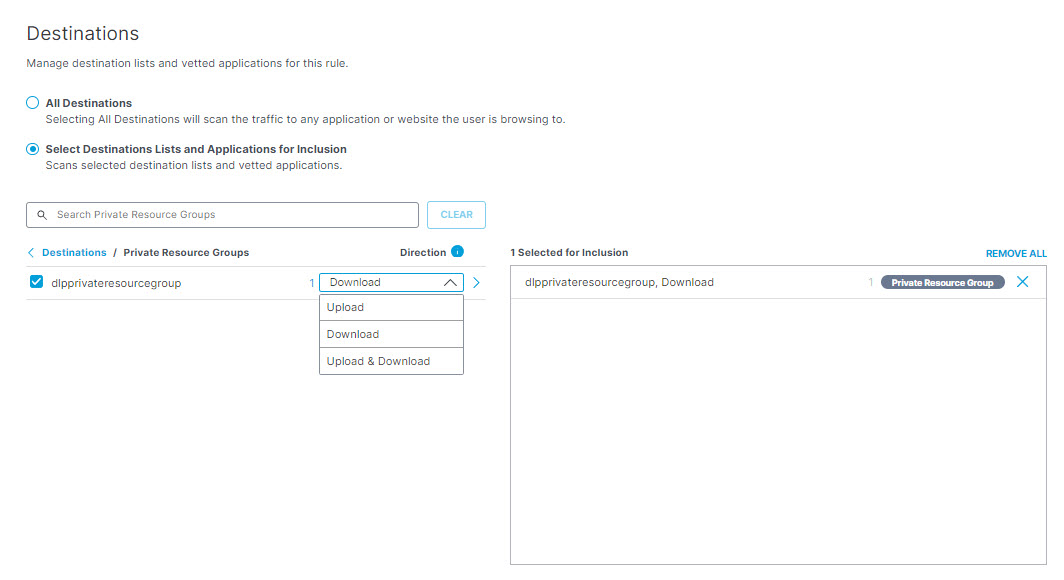
Secure Access DLP supports scanning private resources in HTTP/s traffic in both upload and download directions for all supported file types, but does not support scanning forms data.
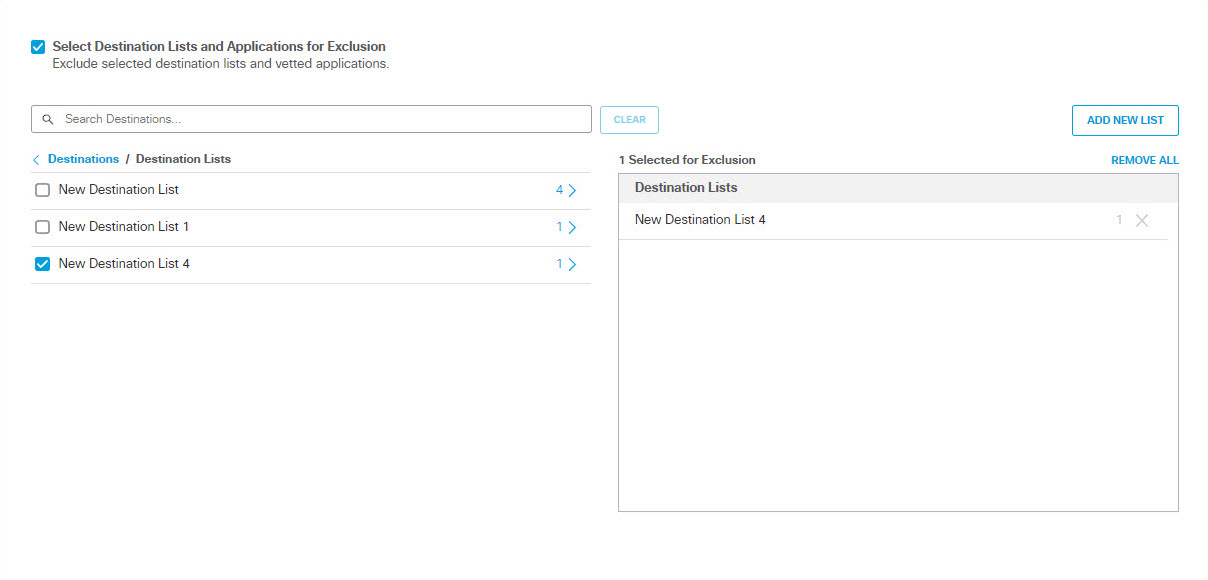
- To add destination lists for inclusion, under Destinations expand Destination Lists and check the boxes for the destination lists you want to add to the rule.
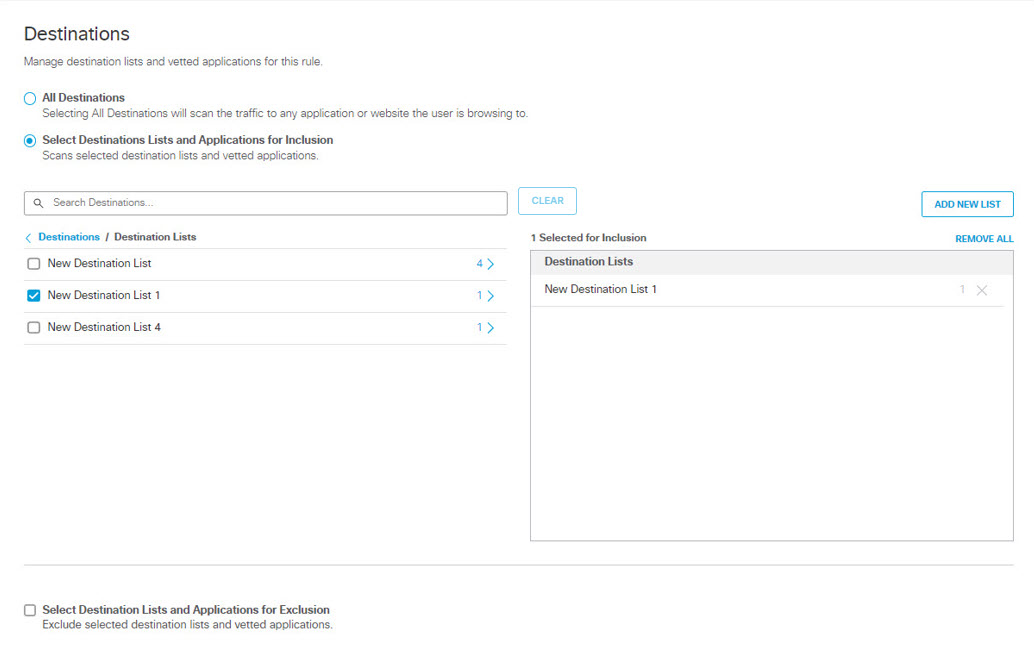
- To create a new destination list and add it for inclusion, under Destinations expand Destination Lists and click ADD NEW LIST. Under List Name enter a unique name for the list. For each URL/Domain to be in the list, enter a domain name, URL, IPV4 address or CIDR, and click Add. Click Save when done.
Note: Adding a new destination list to the rule here automatically adds it for inclusion.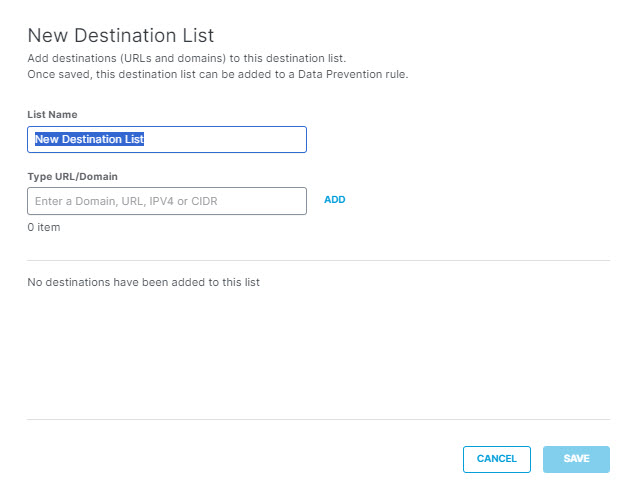
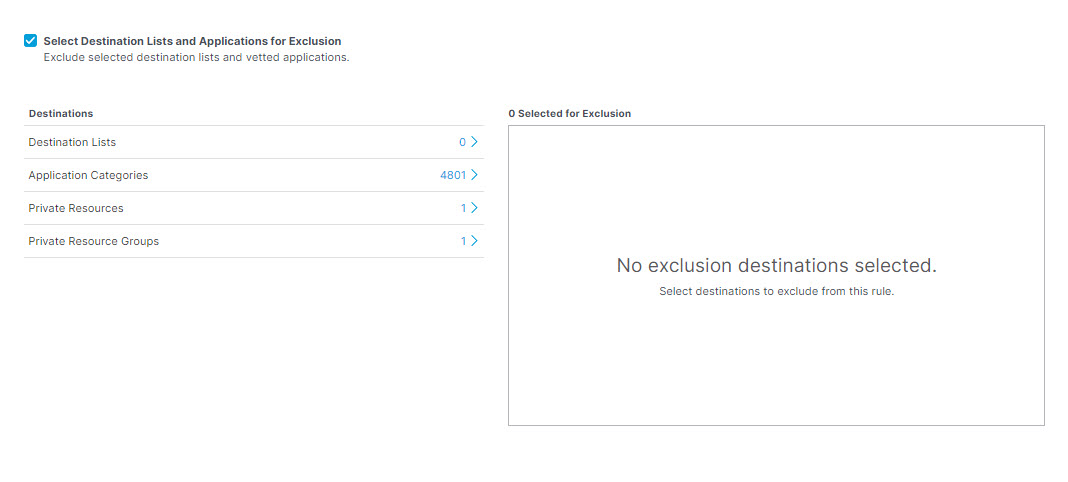
- Check the checkbox Select Destination Lists and Applications for Exclusion to select destinations and applications to exclude from this rule.
- To exclude applications, under Destinations expand Application Categories. (See Application Categories) for a list of available categories.) Expand categories and check the boxes for the applications you want to exclude from the rule. You can search for an application by entering at least three consecutive letters from the application name in the search box.
Note: It is not possible to search for an application with fewer than three letters in its name—for example, "QQ" or "YY." These applications must be manually selected from the hierarchy under their respective categories, or wildcarded in search—for example, "QQ*". This behavior is by design.
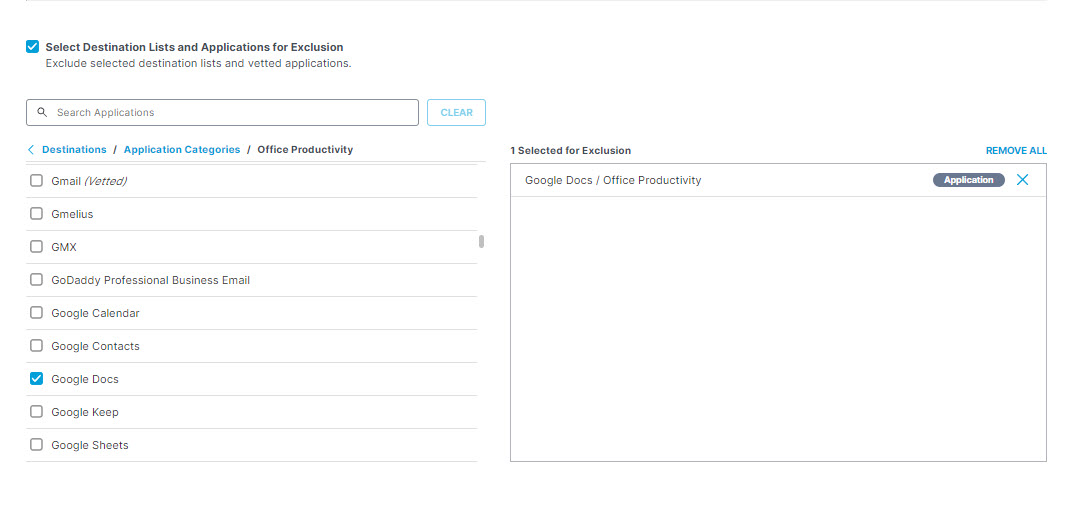
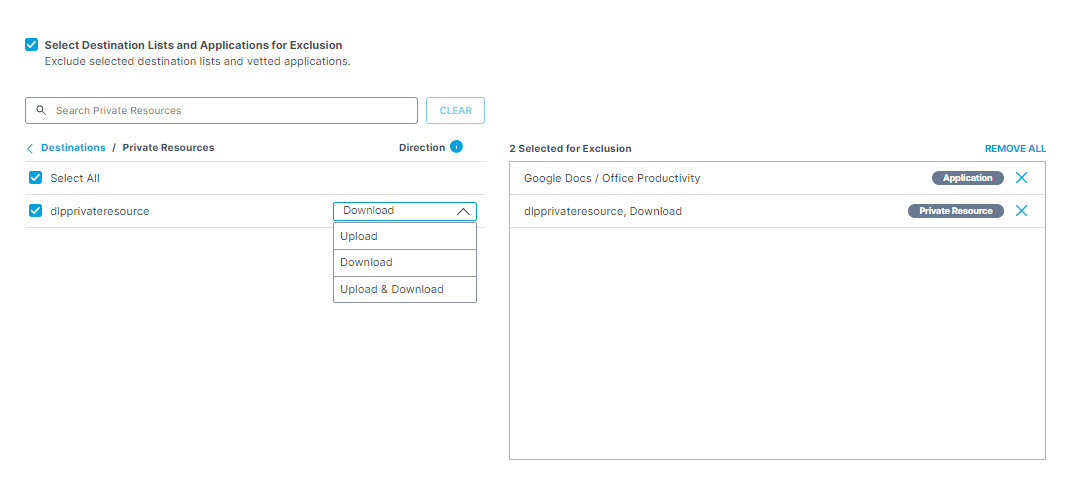
- To exclude private resources, under Private Resources select the resource you want to exclude from the rule. You can search for a resource by entering at least three consecutive letters from the resource name in the search box.
Note: It is not possible to search for a private resource with fewer than three letters in its name—for example, "QQ" or "YY." These resources must be manually selected, or wildcarded in search—for example, "QQ*". This behavior is by design.
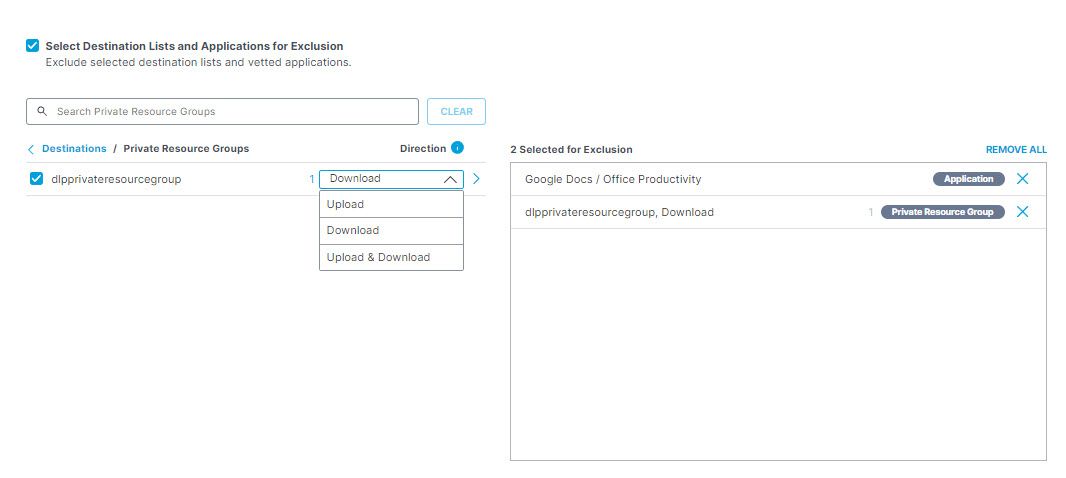
- To exclude private resource groups, under Private Resource Groups select the resource group you want to exclude from the rule. You can search for a resource group by entering at least three consecutive letters from the resource group name in the search box.
Note: It is not possible to search for a private resource group with fewer than three letters in its name—for example, "QQ" or "YY." These resource groups must be manually selected, or wildcarded in search—for example, "QQ*". This behavior is by design.
- To exclude destination lists, under Destinations expand Destination Lists and check the boxes for the destination lists you want to exclude from the rule.
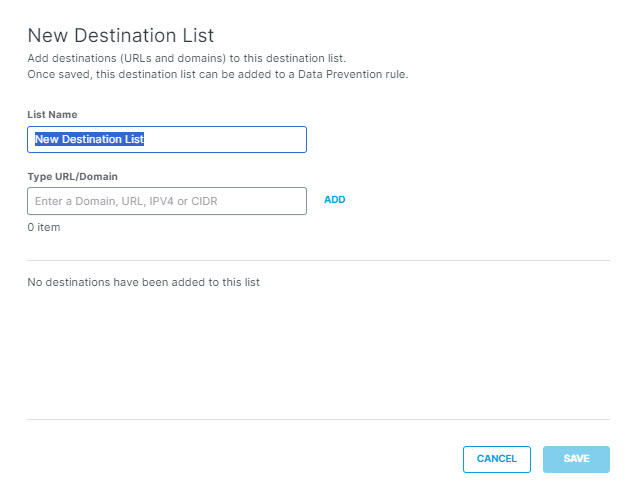
- To create a new destination list and exclude it, under Destinations expand Destination Lists and click ADD NEW LIST. Under List Name enter a unique name for the list. For each URL/Domain to be in the list, enter a domain name, URL, IPV4 address or CIDR, and click Add. Click Save when done.
Note: Adding a new destination list to the rule here automatically adds it for exclusion.
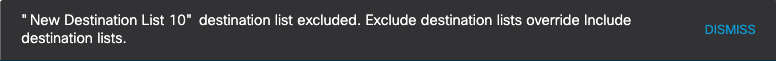
Note: When a destination list is selected for both inclusion and exclusion in a rule, it will automatically be excluded. Exclusion destination lists always override inclusion destination lists. Similarly, if a domain is included on an inclusion destination list and an exclusion destination list, the domain will be excluded.
- Under Action, from the drop-down list, choose Monitor or Block.
- Monitor—Monitor file uploads and data submitted in web forms.
The rule will search for content that matches supported workflows (See Supported Applications) and policy-configured destinations and identities. - Block—Block file uploads.
The rule will search for content that matches supported workflows (See Supported Applications) and the policy-configured destinations and identities. When content matches these workflows, the rule blocks the content.

Limited Availability
Secure Access can optionally block all password-protected files directed to destinations configured in the DLP rules. If enabled, this feature impacts all file types and all users and cannot be configured for finer granularity. This feature is not generally available; contact Secure Access Support to have it enabled in your account.
- If you have established a connection with an ICAP server, by default the payload of all active Realtime DLP rule violations will be sent to an on-premises DLP over ICAP. Disabling Secure ICAP for this rule will prevent payload transmission for DLP violations triggered by this rule.
- Under User Notifications you can enable and configure an email notification to be sent to a user who performs an action that triggers a violation of the rule. You can use a default email template provided by the system, or create your own custom template.
i. Enable user notifications.
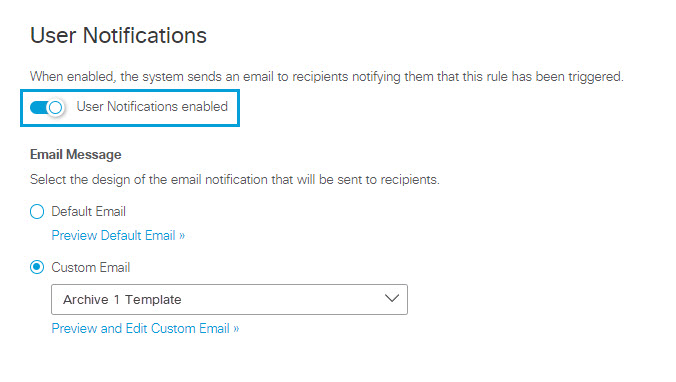
ii. Choose the email template:
To Use the Default Email Template:
a. Click Default Email.
b. To preview the content of the email that will be send to users, click on Preview Default Email. You can review the email subject line and text, but you cannot change it.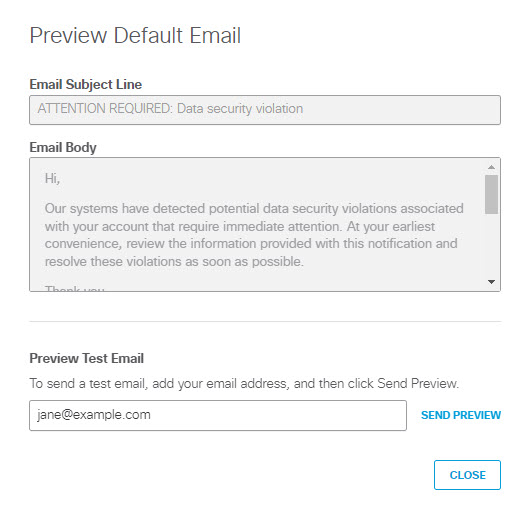
iii. (Optional) To send a test copy of the email to an address of your choosing, enter an address in Preview Test Email and click SEND PREVIEW to send the message. (By default the system uses the email address of the logged in user.)
iv. Click CLOSE to return to the Data Loss Prevention Policy page.To Use a Custom Email Template:
a. Click Custom Email.
b. From the drop down menu, select an existing custom template, or choose CREATE CUSTOM TEMPLATE. If you select an existing custom template, you can click Preview and Edit Custom Email to review and change the template.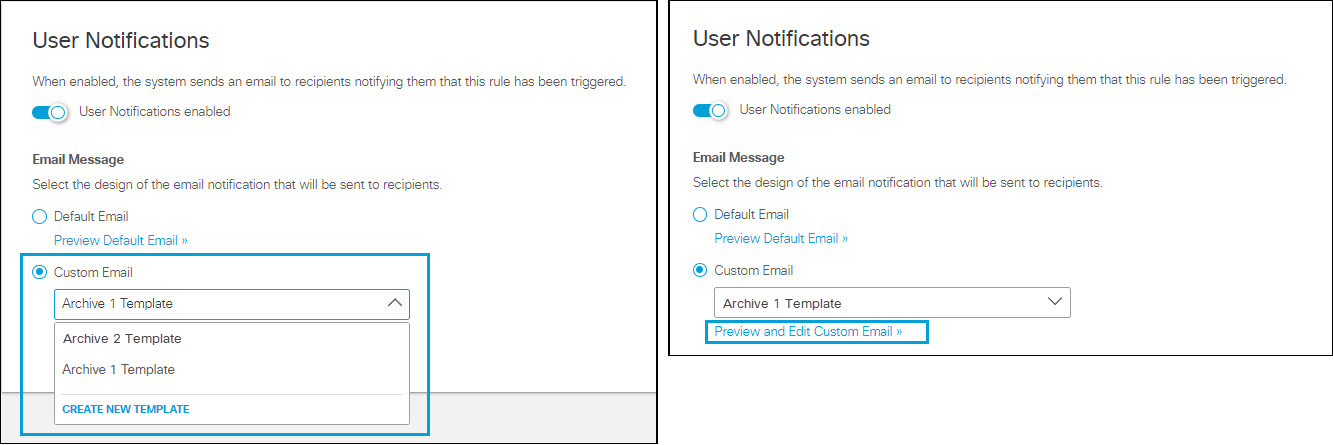
c. When you choose to create or edit a custom template for email notifications of policy violations you will see one of these two dialogs, which are almost identical:
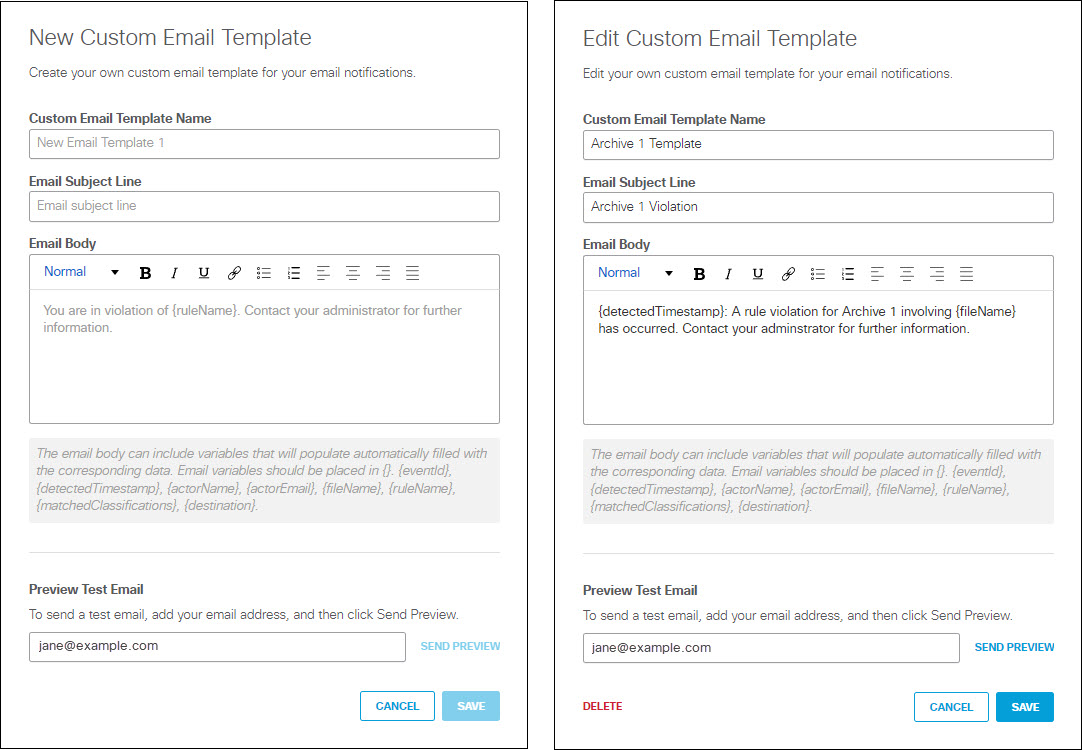
The Edit Custom Email Template includes a DELETE link which you can use to delete a custom template that is no longer needed. You may not delete a template that is in use by any rule.
To create a new template or change an existing template:
A. Enter a unique Custom Email Template Name.
B. Enter an Email Subject Line.
C. Enter the text of the email in the Email Body text box.
The email text can include the following variables, which you must enclose in braces ( {} ):
- {eventId} - The unique identifier the system generates for the policy violation event.
- (detectedTimestamp} - The date and time the violation was detected, formatted as shown in this example: "Oct 1, 2023 at 14:04 UTC"
- (actorName} - Name of the user whose action triggered the violation. (Secure Access gets this information from the authenticated Active Directory.)
- {actorEmail} - Email address of the user whose action triggered the violation. (Secure Access gets this information from the authenticated Active Directory.)
- {fileName} - Name of the data file that triggered the violation.
- {ruleName} - Name of the rule that was triggered.
- {matchedClassifications} - The data classifications associated with the violation. (See Manage Data Classifications.)
- {destination} - URL or IP address of the intended destination for the monitored request.
Note: The system replaces a variable with blank text if there is no value assigned to the variable or if an invalid variable name appears within the braces.
D. (Optional) To send a test copy of the email to an address of your choosing, enter an address in Preview Test Email and click SEND PREVIEW to send the message. (By default the system uses the email address of the logged in user.)
E. Click SAVE to return to return to the Data Loss Prevention Policy page.
- Click Save.
Note: All fields must have options selected to save.
Manage the Data Loss Prevention Policy < Add a Real Time Rule to the Data Loss Prevention Policy > Understand Exclusions in a Real Time Rule
Updated 9 days ago