Add an App Risk Profile
Configure an app risk profile to define acceptable risk factors for end-user devices connecting to controllable internet applications.
Prerequisites
- Valid credentials for the Secure Access dashboard.
- Full Admin role in Secure Access. For more information, see Manage Accounts.
Procedure
- Navigate to Secure > Profiles > App Risk Profiles and click Add profile.
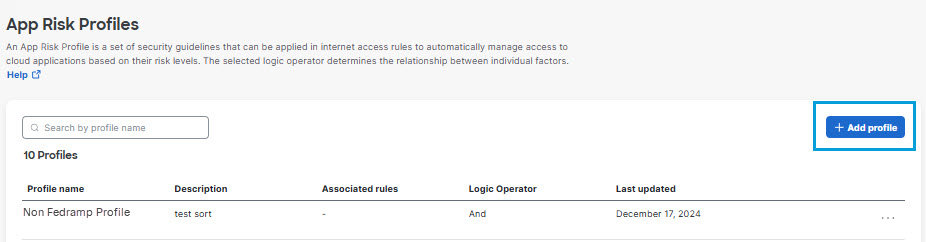
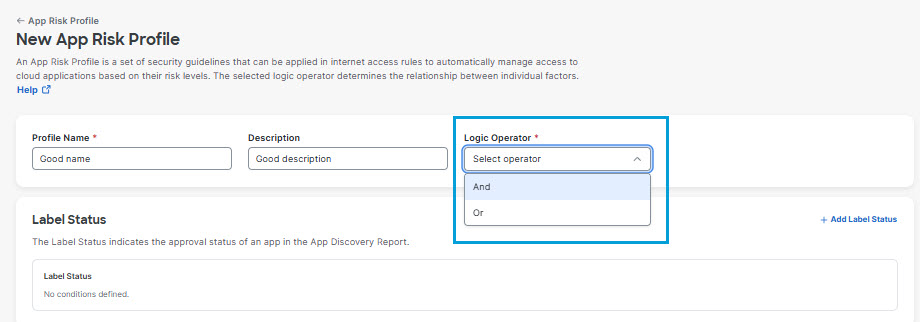
- Give your profile a unique mnemonic Name and a Description.
- For the Logic Operator option, choose And or Or to indicate how the system will evaluate multiple attributes in the profile.
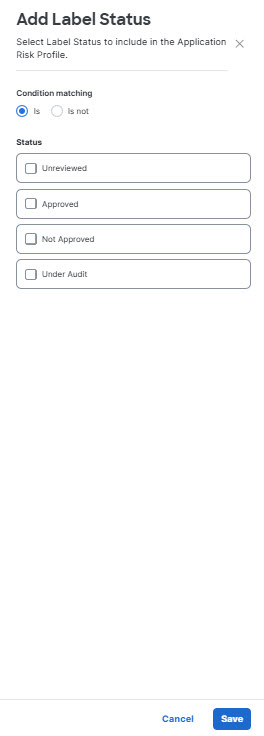
- For Label Status, click Add Label Status and choose the matching conditions for an app's approval status from the App Discovery Report. Click Save when done.
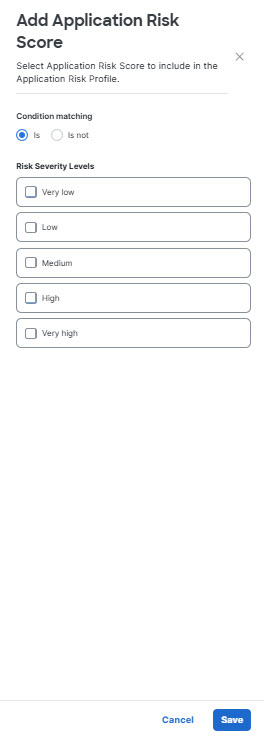
- For Application Risk Score, click Add Application Risk Score and choose application risk scores to include or exclude from the profile. The application risk score could be calculated by Umbrella (based on Business risk, Usage risk, Vendor compliance, and Community risk (if available)) or assigned by you. The possible values are Very Low, Low, Medium, High, and Very High. Click Save when done.
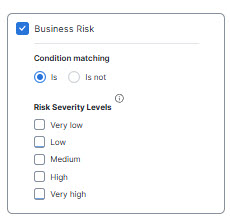
- For Business Risk Factors, click Add Business Risk Factors and choose business risks from the following categories to include or exclude from the profile. Click Save when done.
- Business Risk
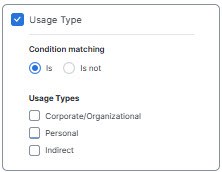
- Usage Type
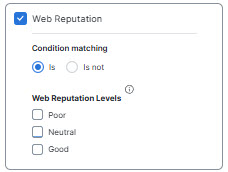
- Web Reputation
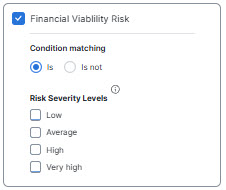
- Financial Viability Risk
Data Storage
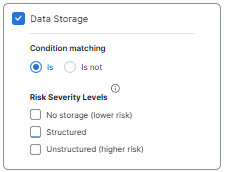
- For Attribute Categories, you can choose to add characteristics and properties from the following categories to add to your profile:
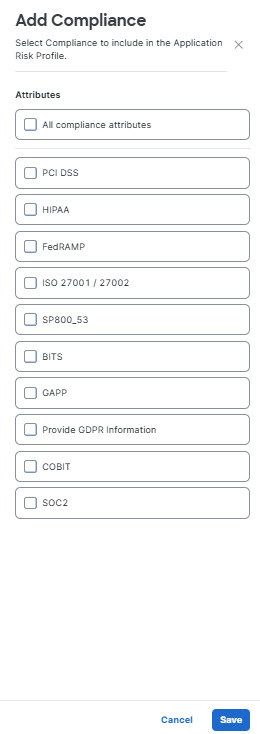
- Click Add Compliance to select from a list of security standards with which an application must comply or standards with which an application need not comply. You may select a specific security standard (such as FEDRAMP or COBIT), or all standards presented in the list.
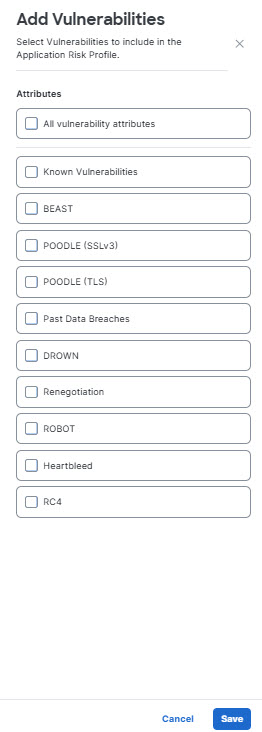
- Click Add Vulnerabilities to select from list of vulnerabilities to which an application must be resistant or need not be resistant. You may select a specific known vulnerabililty (such as DROWN or BEAST), or all known vulnerabilities.
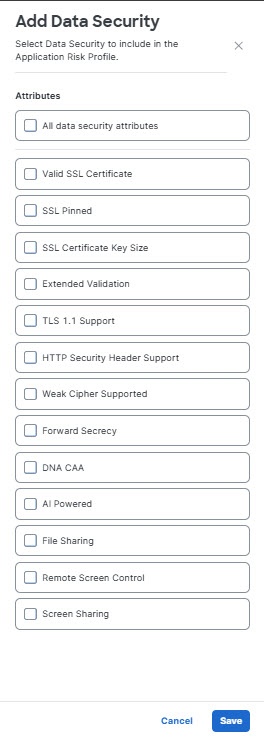
- Click Add Data Security to select from a list of data security attributes an application must provide (such as HTTP Security Header Support) or exclude (such as weak ciphers) . You may select specific attributes or all attributes offered.
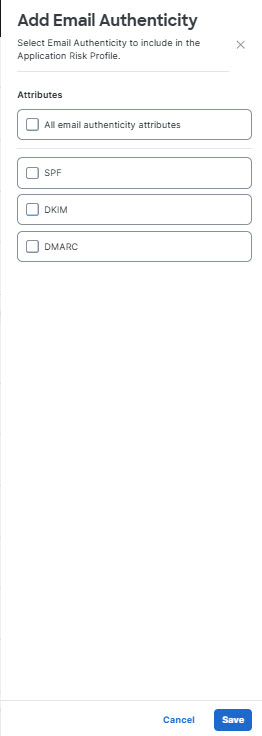
- Click Add Email Authenticity to select from a list of email security attributes an application must support or exclude. (Such as DPF or DKIM.) You may select specific attributes or all attributes offered.
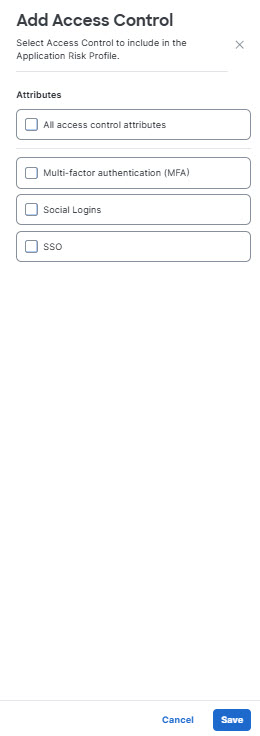
- Click Add Access Control to select from a list of access methods an application must support or exclude. (Such as MFA or SSO.) You may select specific methods or all methods offered.
- Click Add Auditability to select from a list of auditing features an application must support or exclude.

- Click Save to save the app risk profile and make it available for use in Internet Access Rules.
Manage VPN Connection Posture Profiles < Add a VPN Connection Posture Profile > Manage Threat Categories
Updated 5 months ago
