Test Virtual Appliance Deployments
After you deploy the Cisco Secure Access Virtual Appliances (VAs) in your environment and set up internal domains in Secure Access, we recommend that you test your Virtual Appliances.
To begin enforcing your DNS-layer security settings, DNS traffic from the endpoints on your network must exclusively use the VAs as a DNS forwarder.
Table of Contents
- Prerequisites
- Resolve Public and Local DNS Queries
- Test with Endpoints
- Transition Production Traffic
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Resolve Public and Local DNS Queries
Before configuring endpoints to utilize the VAs for DNS traffic, ensure that the VAs are capable of resolving public and local DNS queries. The simplest test is to open a command prompt from a local endpoint and run the nslookup command:
nslookup opendns.com
nslookup opendns.com. 192.168.10.1
Server: 192.168.10.1
Address: 192.168.10.1#53
Non-authoritative answer:
Name: opendns.com
Address: 67.215.92.218
- If the lookup times out, confirm that you have met firewall requirements. For more information, see Prerequisites for Virtual Appliances.
- If the test succeeds, perform the same test again, but this time with a local resource, such as a domain controller or mail server.
nslookup dc01.localdomain.corp.
nslookup dc01.localdomain.corp.
Server: 192.168.10.1
Address: 192.168.10.1#53
Non-authoritative answer:
Name: dc01.localdomain.corp
Address: 192.168.10.47
If the result is something other than expected, ensure the domain was added as an internal domain in Secure Access.
When deploying the VA, we recommend the following for DNS configuration on any internal DNS servers:
- On the DNS server adapter settings, use the loopback address (127.0.0.1) so that the server will use itself for DNS resolution. The second entry should be another internal DNS server.
- On the forwarder settings of the DNS server, we recommend using the Secure Access Anycast IPs (208.67.222.222/208.67.220.220) rather than the virtual appliance IPs. This limits the ability to see the source IP when viewing reports but avoids any problems with DNS loops if there is a misconfiguration on either the VA or internal DNS server.
- If the server also acts as a mail server, the best option is to point to your ISP's DNS servers or other recursive resolvers such as those provided by your ISP.
Test with Endpoints
Before sending most or all of your network's DNS traffic to the VAs, testing with several endpoints is highly recommended. First, change an endpoint's DNS settings to the IPs of the VAs, and then verify the following:
- Local and Remote DNS is functioning—Ensure that local resources, internet resources, and applications are working as expected; this includes cloud-based applications, local websites, and commonly-used resources on the internet in general.
- Verify in the Secure Access Reports—Within a few minutes of changing DNS on an endpoint, you should start seeing traffic containing the Internal IP address in the Secure Access reports.
Secure Access recommends testing for between two and five days with several computers, preferably from different areas of your organization, before switching all production traffic to the VAs.
If DNS fails to resolve after modifying your DNS settings, confirm that you have met the network requirements. For more information, see Prerequisites for Virtual Appliances.
Transition Production Traffic
After successful testing, begin utilizing the VAs for production DNS traffic.
Important
The Secure Access VAs must be the only servers listed as DNS servers. Using a mixture of the VAs and other types of DNS servers is not supported.
In most network environments using Windows Server, local IP addressing is handled through the DHCP Manager. To update your endpoints’ DNS settings to point to the VAs, change the DNS Servers in your DHCP scope options.
- Open DHCP Manager and navigate to Start > Administrative Tools > DHCP.
- Select IPv4 or specific scope, if applicable.
- Right-click Server Options or Scope Options.
- Select 006 DNS Servers, remove ALL the existing local DNS servers, and add the IP addresses of the VAs.
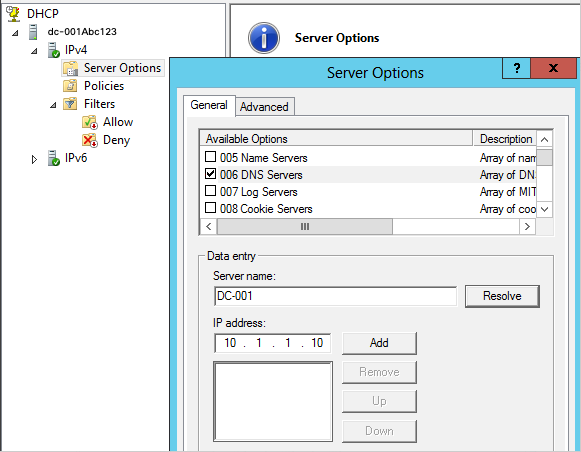
The VAs must be the only DNS servers in this list. It is not possible to use a mixture of VAs and other DNS servers.
After updating the DNS Servers in the DHCP options, wait for the DHCP leases on the endpoints to expire and see the new changes. In most cases, DHCP lease durations are seven days or less, but sometimes may be set to higher values. We recommend verifying the DHCP lease duration in the DHCP Manager.
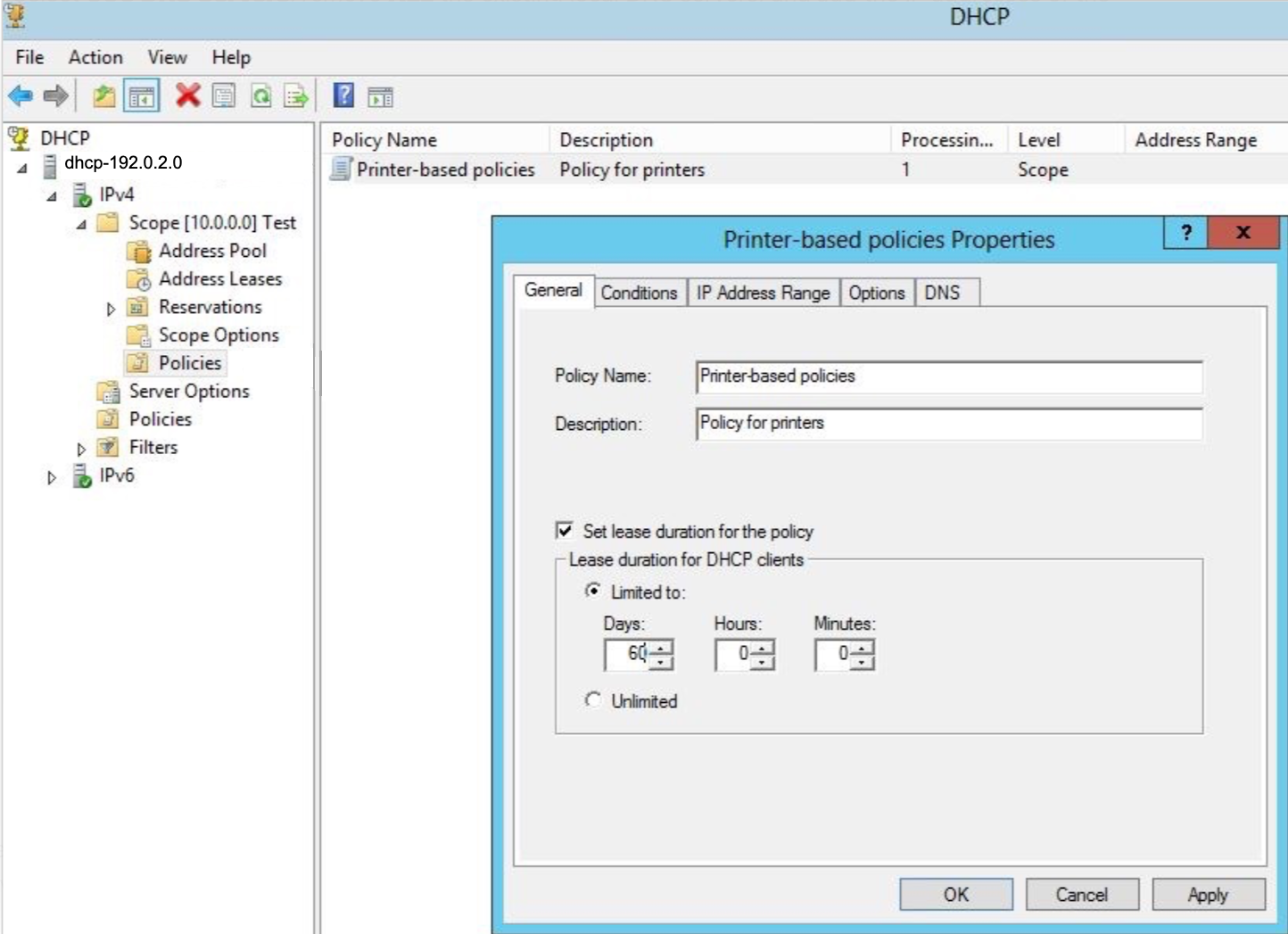
Unfortunately, there is no easy way to force an immediate DHCP lease renewal. One method is to use a Group Policy Object to deploy and execute a batch file with the ipconfig /renew command in it; this would cause the endpoints to recognize the VAs as their DNS servers.
Local DNS Forwarding < Test Virtual Appliance Deployments > SNMP Monitoring for Virtual Appliances
Updated 11 months ago
