Manage Identities
To enable identity and be searchable in Secure Access, configure your Mobile Device Manager to share identity information.
Identity can be any of the following based on what you choose to share with Secure Access:
- User email address
- Username
- Device serial number
- Any other unique device identifier
After you push the identities to Secure Access, they are listed in the Secure Access dashboard.
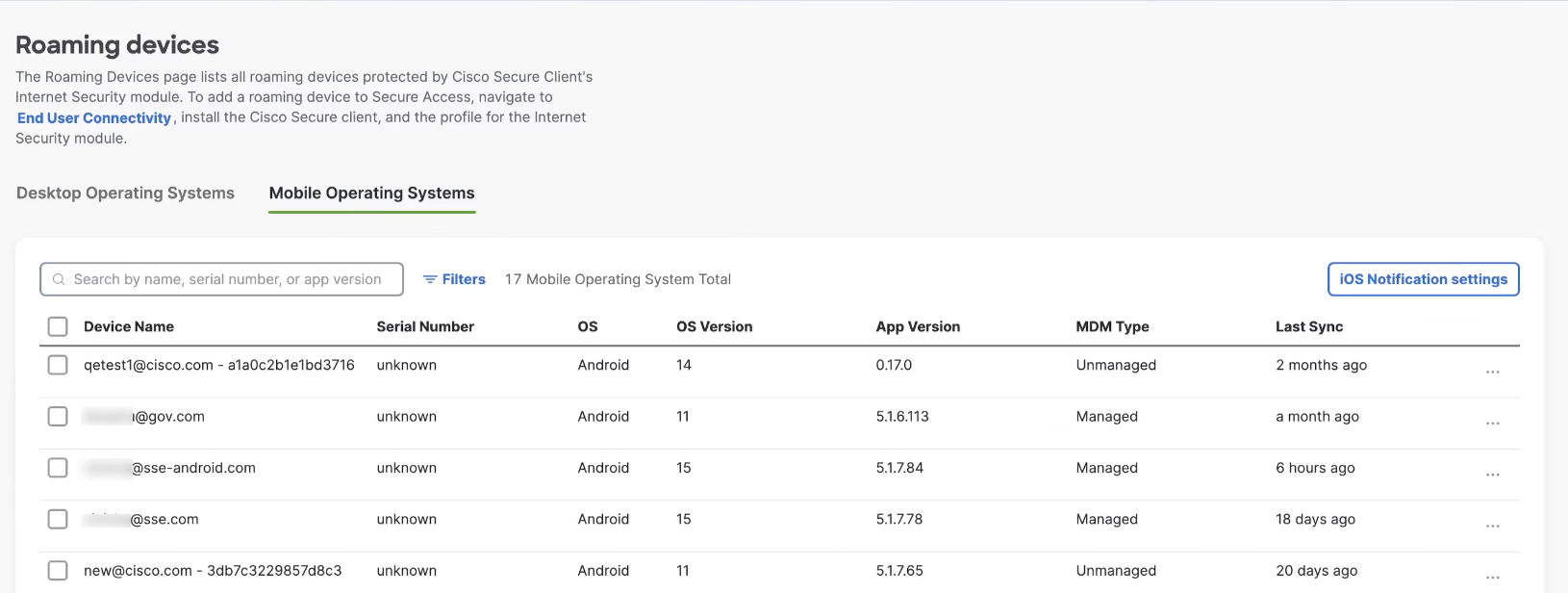
You can select user devices or use the user ID to search for them. To enable User Identities for Android clients, follow these steps.
Table of Contents
- Cisco Meraki Systems Manager
- Microsoft Intune
- Samsung Knox
- VMWare WorkspaceOne
- Access User Identities on the Secure Access Dashboard
Cisco Meraki Systems Manager
The key for User Identity in Meraki is umbrella_user_identity.
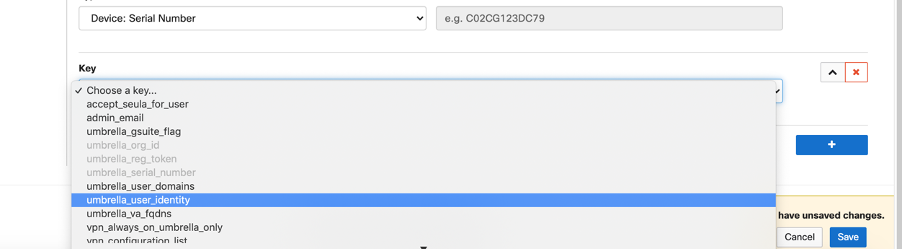
By default, the Type is a text field. Instead of choosing text, you can opt for the variables provided by Meraki SM.
For setting up a user identity value, choose a type.
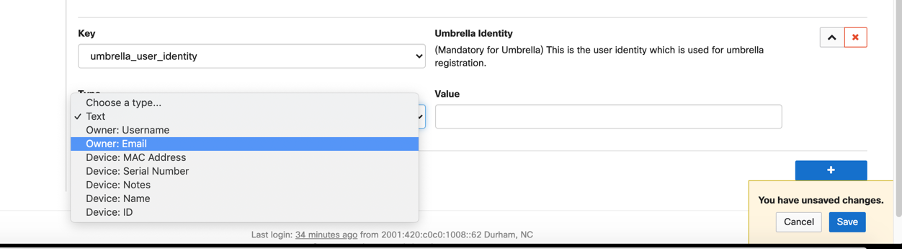
If a user identity is selected, the field looks as shown below:
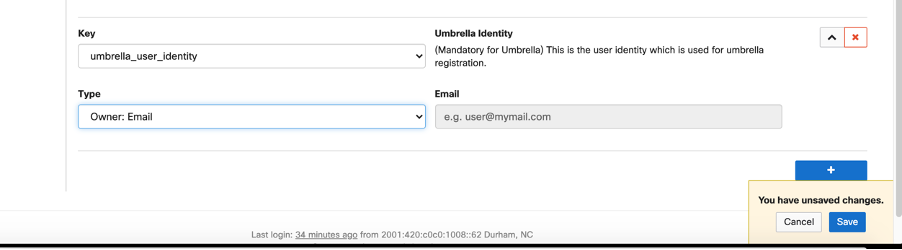
Once the configuration is pushed to the device, Meraki SM replaces the variable with the corresponding value.
Microsoft Intune
You can choose the key for user identity.
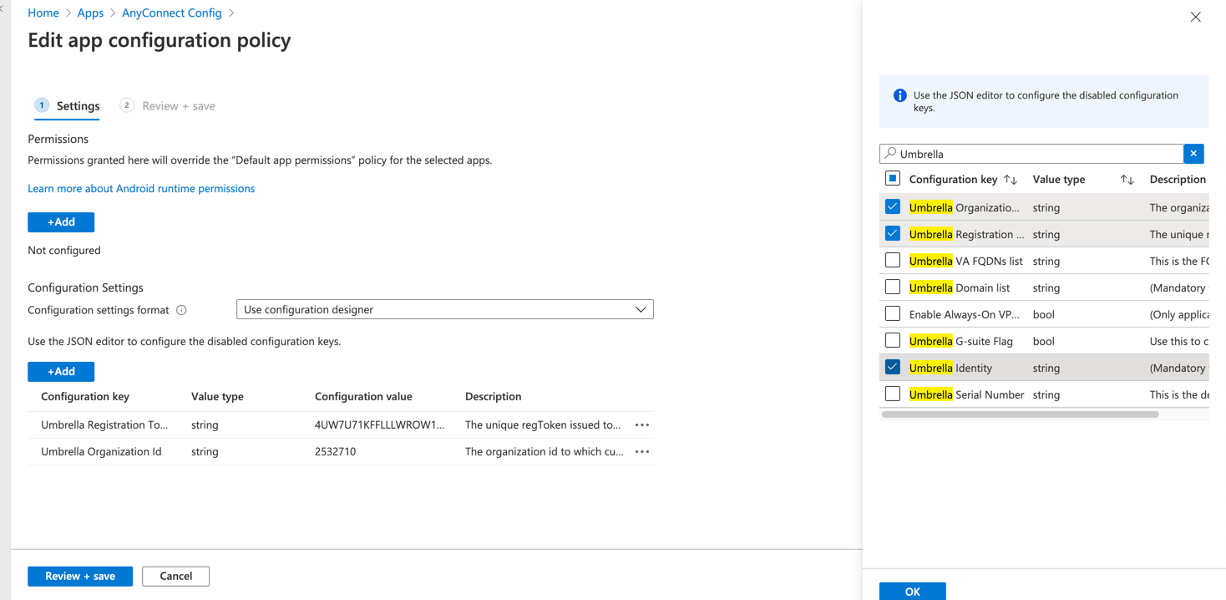
The Value type can either be a string or a variable.
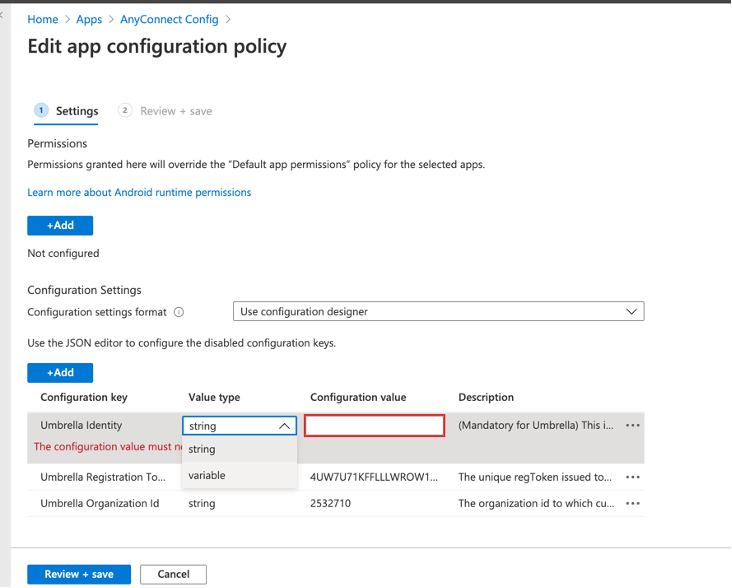
Choose the value type as a variable so that configuration values can be selected from the options provided.
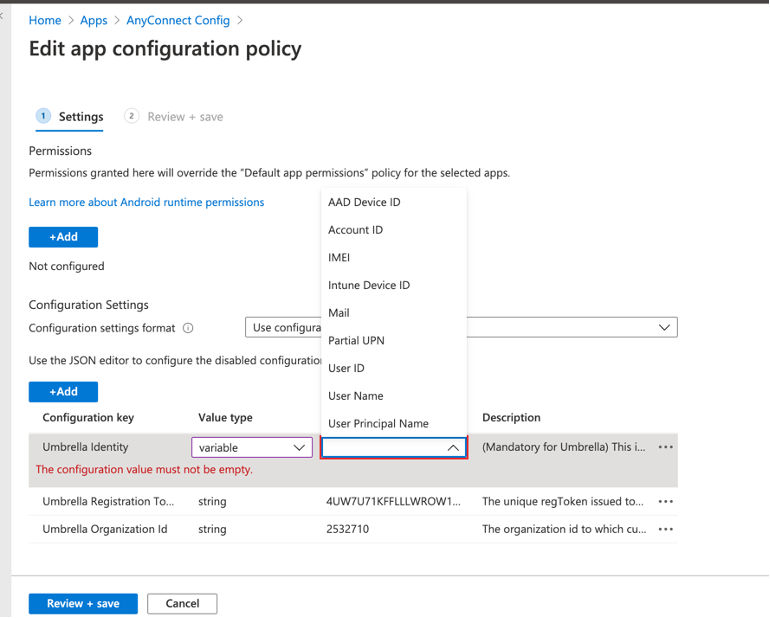
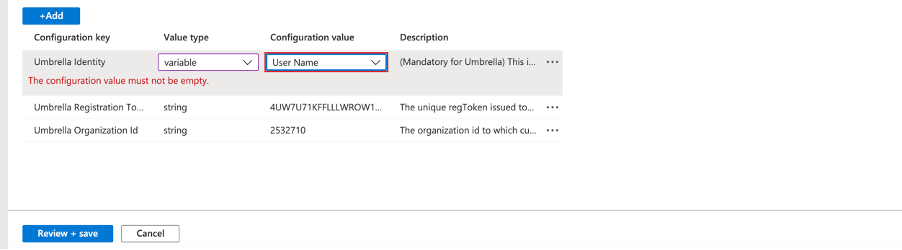
Choose any of the options from the list. Once the configuration is pushed to the device, MS Intune replaces the variable with the corresponding value.
Samsung Knox
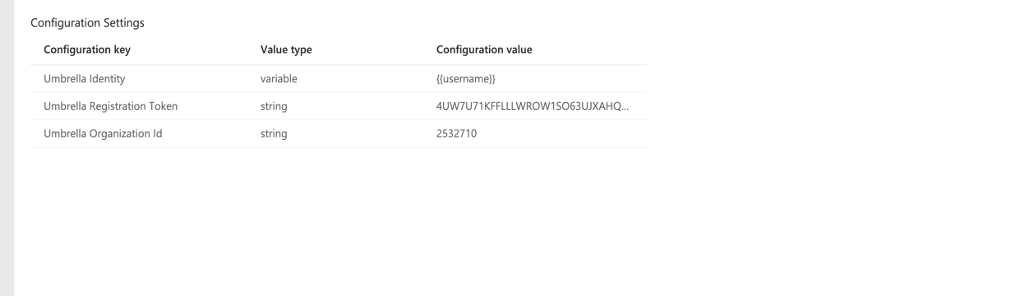
The key for user identity in Knox MDM is ‘Umbrella Identity’.
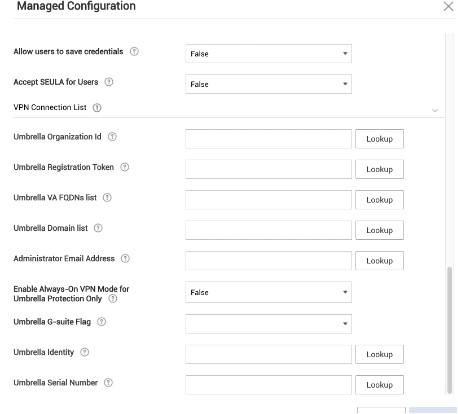
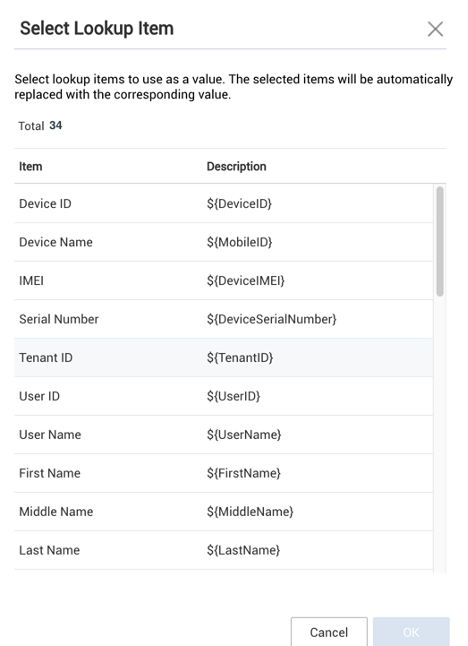
Click LookUp for the Select Lookup Item and choose the appropriate variable for the identity.
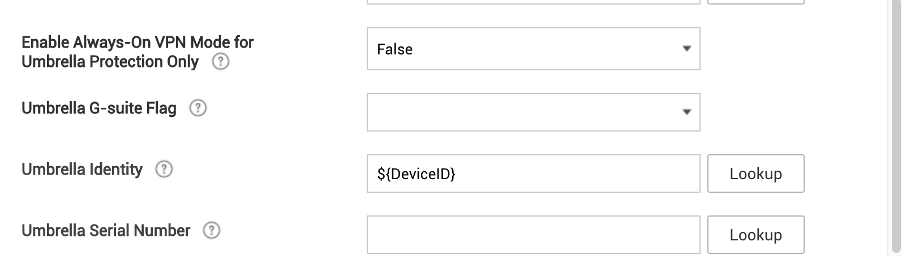
After you select the appropriate variable for the identity, the page appears.
VMWare WorkspaceOne
The key for user identity in VMWare WorkspaceOne is Umbrella Identity.
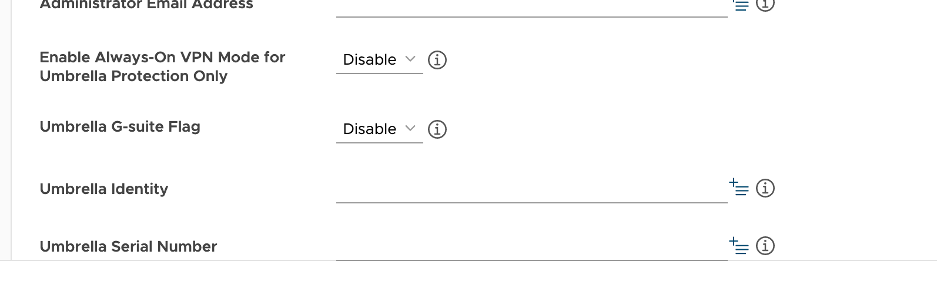
The Value can either be typed into the text box or you can be chosen from the Select Lookup Item tab.
Click LookUp for the Select Lookup Item, and then choose the appropriate variable for the identity.
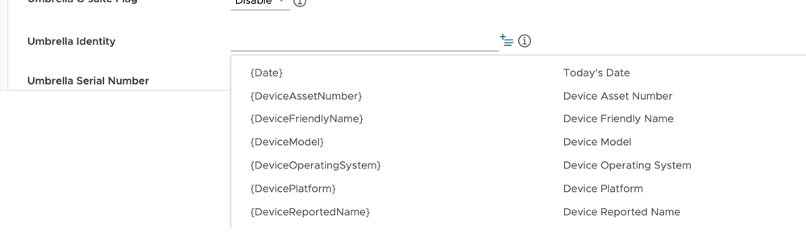
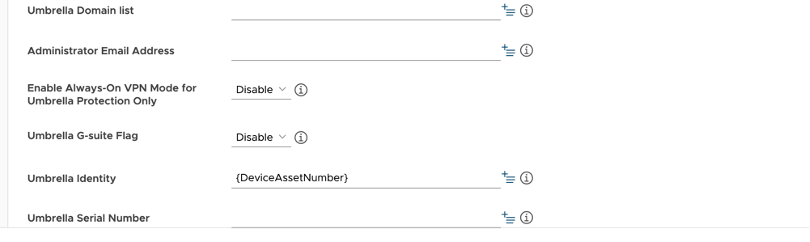
After you select the appropriate variable for the identity, the below screen appears.
Access User Identities on the Secure Access Dashboard
Configure Policy Based on User Identity
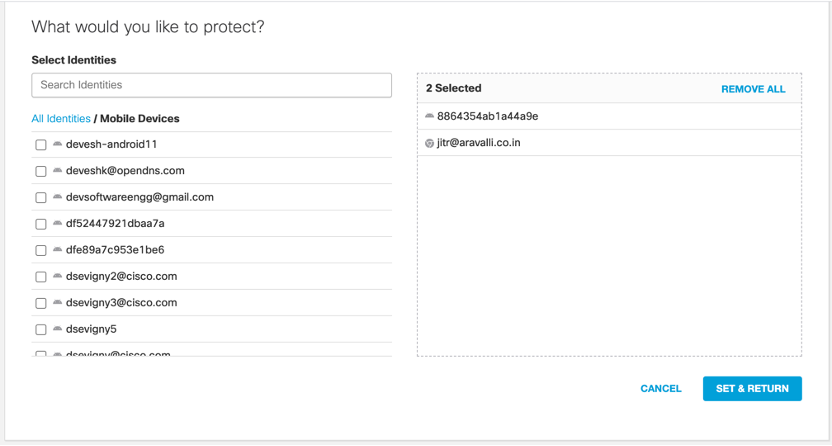
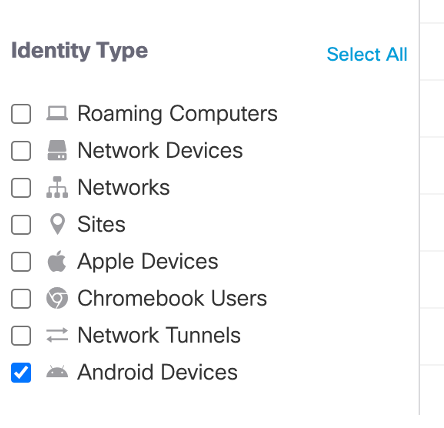
After the user identity is shared with the Secure Access dashboard, you can select these identities in the policy configuration flow. On the identity page, you can choose either a single identity or all the mobile devices.
Monitor User Activity
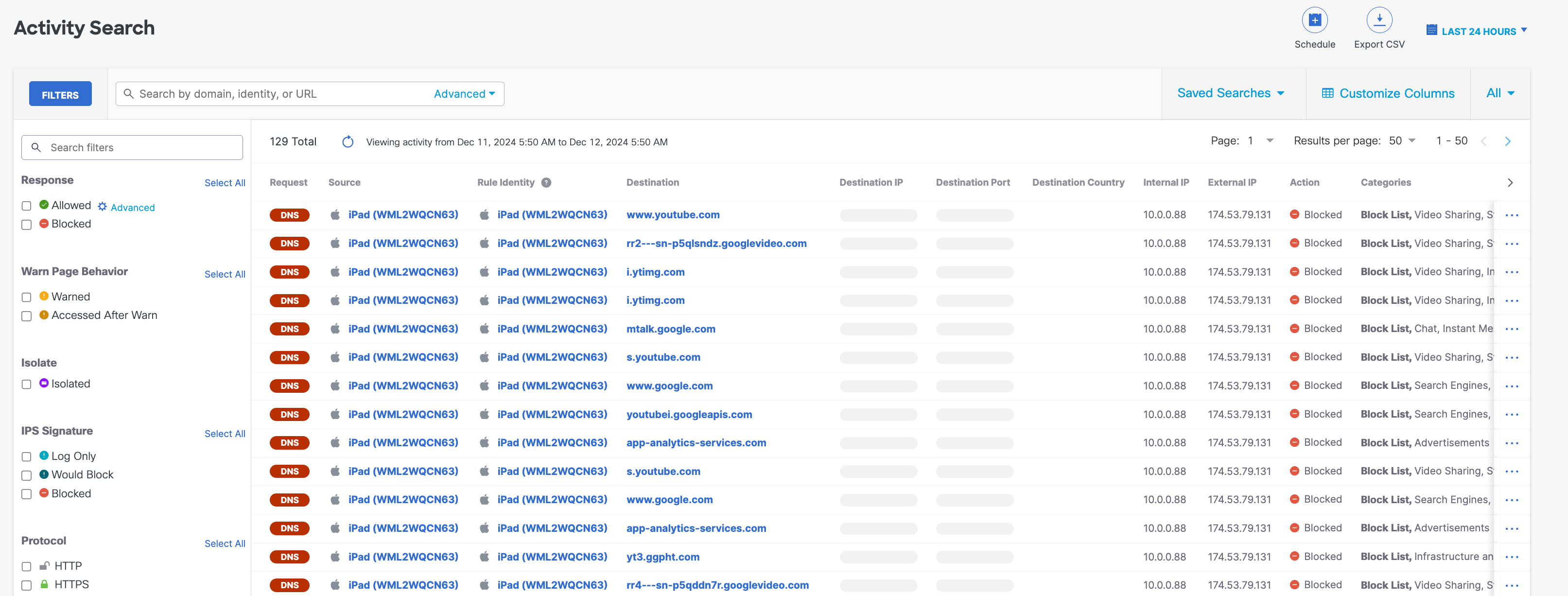
As users start using the mobile device, you can monitor user activity through the Activity Search report.
You can filter logs for the Android devices by selecting Android Devices.
You can see the user activity for the Allowed and Blocked.
Push the Cisco Root Certificate to Devices < Manage Identities > Export Device Data to CSV
Updated about 1 month ago
