View and Customize the Activity Search Report
This topic explains the functions of the Activity Search report and where to find the report in Secure Access.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
View the Activity Search Report
- Navigate to Monitor > Reports > Activity Search. This takes you to the default view of the Activity Search report, which lists all of your identities and the internet requests or traffic events for your organization, tracked over time.
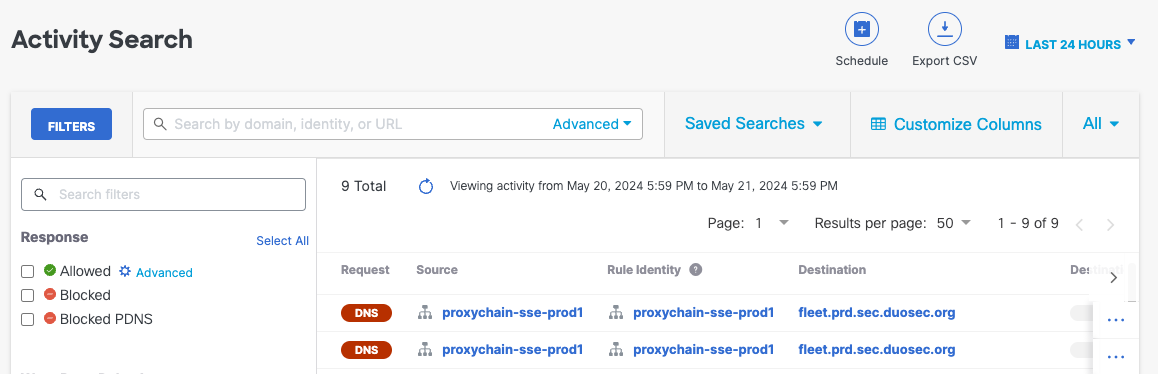
- Hover over individual column values to apply it as a search filter or to exclude it from the search.
- To learn more about individual results, click the blue ellipsis View Actions icon to the right of each search result. For more information, see View Activity Search Report Actions.
Customize the Activity Search Report
- Choose a time frame to view the report. The default is Last 24 Hours. The maximum is Last 30 Days.
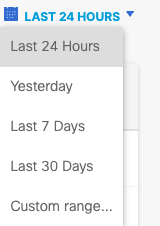
- Customize Columns to select columns to display, drag and drop to reorder column position, then click Apply.
| Column name | Column description |
|---|---|
| Request | When All Requests is selected, this column displays the type of request for each event. Event request types are DNS, Web, Firewall, IPS, ZTNA Clientless, ZTNA Client-based, and Decryption. |
| Source | The name of the source of the request. Applicable to all request types. |
| Rule Identity | The identity of the source that Secure Access used to determine which rule applied to the request. Applicable to DNS, Web, Firewall, and ZTNA requests. A request can have multiple identities. Click the row to view Event Details including all identities associated with a request. For more information, see View Activity Search Report Actions. |
| Destination | The destination of the request. Applicable to DNS, Web, Firewall, IPS, and ZTNA requests. |
| Destination IP | The IPv4 or IPv6 address of the destination. Supports both compressed and long-form IPv6 address formats. Applicable to Web, Firewall, and Decryption requests. |
| Destination Port | The UDP/TCP port of the destination request. Applicable to client-based ZTA requests. For more information, see Comparison of Client-Based and Browser-Based Zero Trust Access Connections. |
| Destination Country | The two-character country identifier. Applicable to DNS, Web, and Firewall requests. |
| File Name | The name of the file involved with the activity, where applicable. Applicable to Web and Firewall requests. Note: File Name will only populate for traffic matching rules with File Type Control or File Inspection enabled (you can enable File Type Control without blocking any file types by clicking enable and saving the rule.) If none of the rules have File Type Control enabled, the file name and extension fields remain blank. |
| Internal IP | The internal IPv4 or IPv6 address of the request. Supports both compressed and long-form IPv6 address formats. Applicable to DNS and Web requests. |
| External IP | The external IPv4 or IPv6 address of the request. Supports both compressed and long-form IPv6 address formats. Applicable to DNS and Web requests. |
| DNS Type | The DNS record type. Applicable to DNS requests. |
| Action | The request is either Blocked or Allowed. Applicable to DNS, Web, Firewall, IPS, and ZTNA requests. Blocked – Certificate Error indicates certificate and TLS error events when the request is processed by a ruleset with HTTPS inspection and File Analysis enabled. Blocked – AI Supply Chain indicates end user attempts to download AI model files that are associated with prohibited suppliers, rely on a copyleft license, or can execute arbitrary code when the request is processed by an internet access rule with a security profile for internet access with AI Supply Chain Blocking enabled. For more information, see AI Supply Chain Report. |
| Categories | Content and Security categories flagged with the activity. Applicable to DNS, Web, and Firewall requests. Click Dispute Categorization in the Event Details navigation drawer to suggest a different category for a Source. |
| Resource/Application | The resource or application involved with the activity, when applicable. Populates for traffic matching rules with Application Controls enabled. If no rules have Application Controls enabled, then the field will remain blank. Applicable to DNS, Web, Firewall, and ZTNA requests. For more information, see Advanced Application Controls. |
| Signature List Name | The Secure Access Intrusion Prevention System (IPS) signature list applied to the request. Applicable to IPS requests. For more information, see Manage IPS Profiles. |
| IPS Signature | The signature of the known threat that was blocked or logged by Secure Access IPS. Applicable to IPS requests. For more information, see Manage IPS Profiles. |
| Protocol | Displays whether the Web request protocol is HTTP or HTTPS, and whether the Firewall, IPS, or Decryption request protocol is TCP or UDP. Decryption request protocol includes the cryptographic protocol, such as TLS. |
| Rule Name | The name of the access rule applied to the request. Applicable to DNS, Web, Firewall, IPS, and ZTNA requests. Click the rule name to view your Access Policy where the rule is configured. For more information, see Manage the Access Policy. Click the row to view Event Details including details of the rule (such as destination list or schedule applied). For more information, see View Activity Search Report Actions. |
| Application Category | If an application is involved with the activity, this column contains the categories associated with the application. Applicable to DNS, Web, and Firewall requests. For the full list of application categories, see Application Categories. |
| Application Protocol | If an application is involved with the activity, this column contains the protocol for the application (HTTP, SSL, RTP, DNS, or none). Applicable to Firewall requests. |
| Request Method | The HTTP method used by the request. Applicable to Web requests. |
| Referer | The URI from which the request originated. Applicable to Web requests. |
| Status Code | Standard HTTP status codes. Applicable to Web requests. |
| Content Type | The HTTP content type. Applicable to Web requests. |
| File Extension | The extension of the file involved in the activity, where applicable. Applicable to Web and Firewall requests. |
| OS | The operating system of the client's device. Applicable to ZTNA requests. |
| Browser | The client's browser. Applicable to ZTNA requests. |
| Location | The two-character country identifier. Applicable to ZTNA requests. |
| Location IP | The IPv4 or IPv6 address of the client. Supports both compressed and long-form IPv6 address formats. Applicable to ZTNA requests. |
| Date and Time | The date and time stamp of the request. Applicable to all request types. |
- Filter Request by selecting an option from the dropdown menu at the top right. Filters and columns update to those that are relevant to the selected Request type. The default Request type is All.
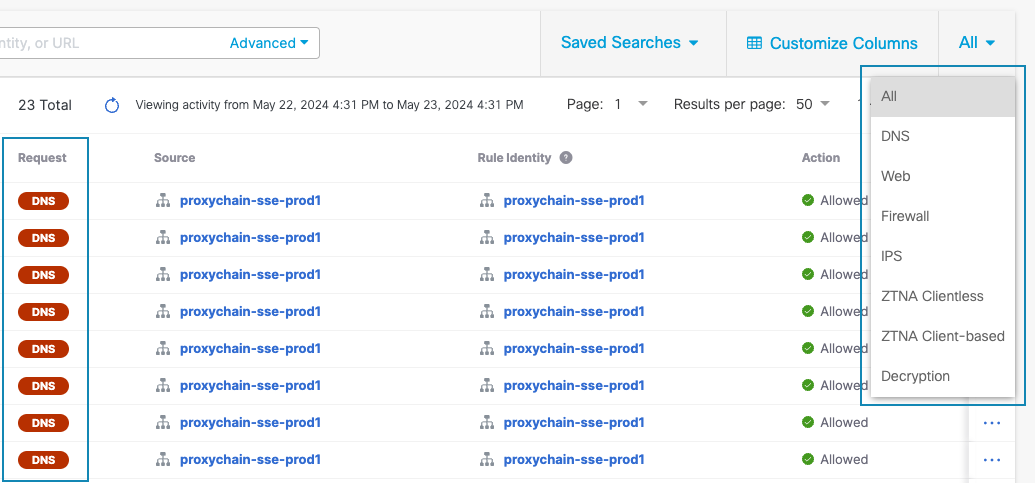
- Search and select additional Filters to the left of the report results. For the complete list of filters and options, see the table below.
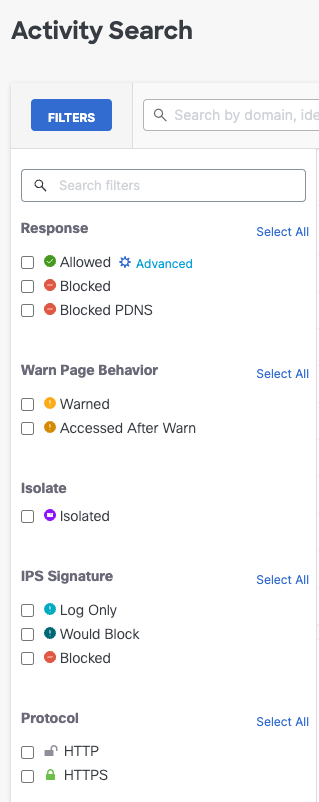
Choose from the following filters and options. Filter options available in this menu are determined by the Request selected in the previous step.
Note: Filters apply a logical OR relationship between options, except in the case Event Type. Selecting more than one Event Type option will not return results because the Event Type filter applies a logical AND relationship between options.
For example, if you filter for both the Public Application and Destination List event types, the Activity Search report will not return any results because an event can have only one event type.
For all other filters, selecting some or all options can return results. For example, if you filter for both the HTTP and HTTPS protocols, the Activity Search report will return all web events because they will have used either the HTTP OR HTTPS protocol.
Filter Filter options Response Allowed
Blocked
Blocked PDNS
The Response filter applies a logical OR relationship when you select more than one option.
Optionally, you may apply one or both advanced options to the Allowed event filter:
Allow: All events that were allowed by passing through your security policies. For Web Policies, this will include the Allow-Security enforced action.
Security Overridden: Identities will be permitted to access destination even if we detect a security issue. This action will only appear on activity associated with Web Policies.Warn Page Behavior Warned
Accessed After Warn
The Warn Page Behavior filter applies a logical OR relationship when you select more than one option.Isolate Isolated events are browser-based security threats that were redirected to a Secure Access cloud-based host. For more information, see About Isolated Destinations. IPS Signature Log Only
Would Block
Block
The IPS Signature filter applies a logical OR relationship when you select more than one option.Protocol HTTP
HTTPS
The Protocol filter applies a logical OR relationship when you select more than one option.Event Type Public Application
Destination List
Any Security Category
Any Content Category
Cisco AMP Disposition is Malicious
Antivirus Disposition is Malicious
Integration
Tenant Controls
Certificate and TLS Errors
Data Loss Prevention
Geolocations
The Event Type filter applies a logical AND relationship when you select more than one option and will return only one type of event.Identity Type The type of source in the Rule Identity column. Identity Type options vary by event and by organization.
The Identity Type filter applies a logical OR relationship when you select more than one option.Decryption Actions Decrypt Inbound
Decrypt Outbound
Do not Decrypt
Decrypt Error
The Decryption Actions filter applies a logical OR relationship when you select more than one option.Security Categories For the full list of filter options, see Threat Category Descriptions. The Security Categories filter applies a logical OR relationship when you select more than one option. Content Categories For the full list of filter options, see Available Content Categories. The Content Categories filter applies a logical OR relationship when you select more than one option.
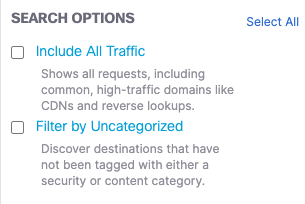
- Select Search Options below the Filters menu in the previous step.
- Include All Traffic— Includes data from all domains including noisy domains that are filtered out by default.
- Filter by Uncategorized— Includes destinations that are not classified under a specific security or content category.
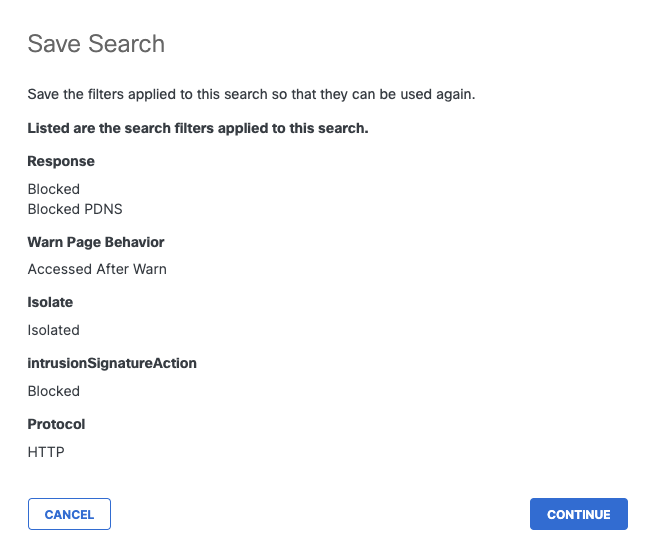
Save Activity Search Report columns and filters for future use
- Once you select a filter on a new search, a Save Search button will appear. Configure filters and customize columns, then click Save Search.
- Review search filters applied to this search, then click Continue.
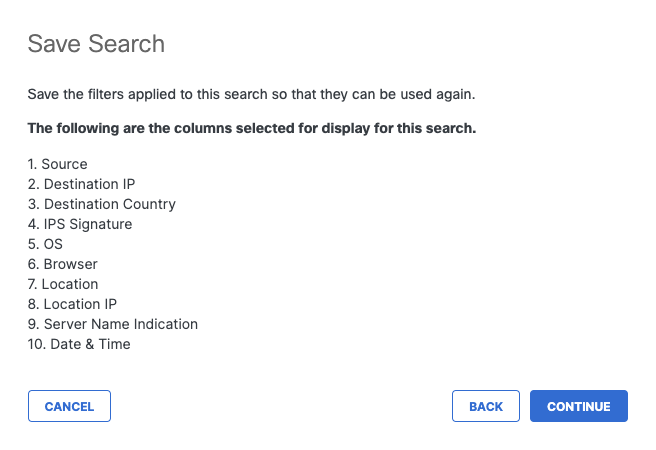
- Review customized columns selected for display for this search, then click Continue.
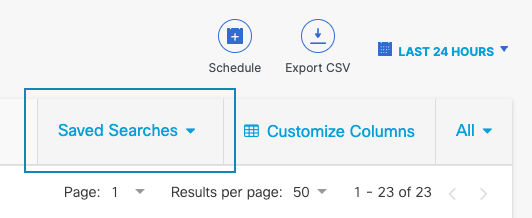
- Search name is required and Description is optional. Once you Save, you will be able to access and update your customized report from the Saved Searches dropdown at the top right of the report.
Activity Search Report < Activity Search Report > View Firewall Events in Activity Search Report
Updated 2 months ago
