Configure Okta for SAML
Secure Access uses the Security Assertion Markup Language (SAML) to authenticate web requests from user devices on networks and network tunnels with web security enabled. Secure Access also uses SAML to authenticate requests to private resources from user devices with Zero Trust Access (ZTA) enabled.
To support SAML authentication, you must configure the integration of an SAML identity provider (IdP) in Secure Access. In Okta, add the Secure Access service provider metadata. Then, add the Okta SAML IdP metadata in the Secure Access SSO authentication profile.
For information about provisioning users from Okta to Secure Access, see Provision Users and Groups from Okta.
Table of Contents
- Prerequisites
- Procedure
- Test the Identity Provider Integration
- View the SAML Certificates in Secure Access
Prerequisites
For information on the prerequisites to integrate an SAML IdP with Secure Access, see Prerequisites for SAML Authentication.
Procedure
- Step 1 – Add SSO Authentication Profile in Secure Access
- Step 2 – Select Okta SAML Identity Provider in Secure Access
- Step 3 – Download the Secure Access SP Metadata and Certificates
- Step 4 – Configure the Okta Integration App
- Step 5 – Add Okta Metadata in Secure Access
Step 1 – Add SSO Authentication Profile in Secure Access
To get started, add the SSO authentication profile for the Okta SAML IdP. For more information, see Add SSO Authentication Profiles.
Step 2 – Select Okta SAML Identity Provider in Secure Access
In the SSO authentication profile, select the Okta SAML IdP, copy the metadata URL for the Secure Access service provider, and choose the time interval when end users will authenticate with Secure Access.
- For Identity Provider, choose Okta.
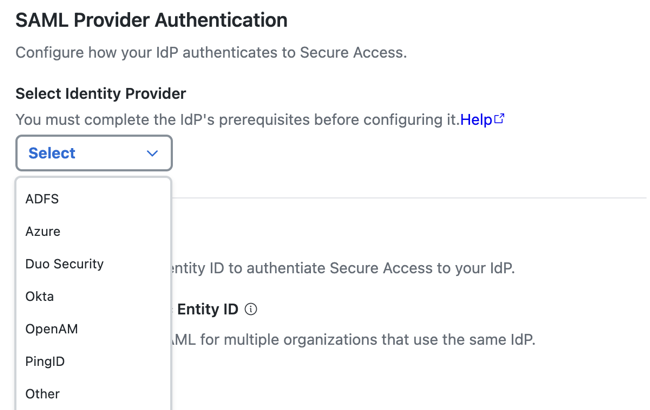
- (Optional) Enable an organization-specific entity ID.
- Organization-specific Entity ID—Choose this option when you have multiple Secure Access organizations and need to configure SAML authentication for Secure Access Internet Security and Zero Trust Network Access (ZTNA) for these organizations against the same IdP. The Secure Access SAML default common
EntityIDis saml.fg.id.sse.cisco.com. Secure Access allows you to override the default Secure Access SAML EntityID for each organization.
- Organization-specific Entity ID—Choose this option when you have multiple Secure Access organizations and need to configure SAML authentication for Secure Access Internet Security and Zero Trust Network Access (ZTNA) for these organizations against the same IdP. The Secure Access SAML default common
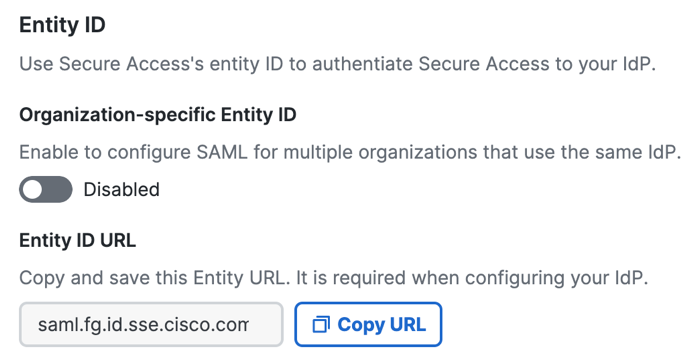
- For Entity ID URL, click Copy URL.
Save the Secure Access metadata URL in your local environment. The Secure Access SAML default commonEntityIDis saml.fg.id.sse.cisco.com.
Note: Use the Secure Access SP metadata URL to configure the Okta SAML IdP app integration. For more information, see Configure Okta with the Secure Access SAML Metadata.
- Choose a time interval when a user must authenticate with Secure Access, or select Never.
The time intervals are: Daily, Weekly, or Monthly.
- Click Next.
Step 3 – Download the Secure Access SP Metadata and Certificates
Download the Secure Access metadata files and use the service provider file to configure your instance of Okta.
The Secure Access service provider metadata includes the service provider Issuer ID, the assertion consumer endpoint URL, and the SAML request signing certificate from Secure Access. The Secure Access metadata is required when configuring your IdP.
Note: Encrypted SAML assertions are a compliance standard in many industries and mitigate the risk of intercepted SAML assertions. For more information, see Prerequisites for SAML Authentication.
-
Check Manual Configuration.
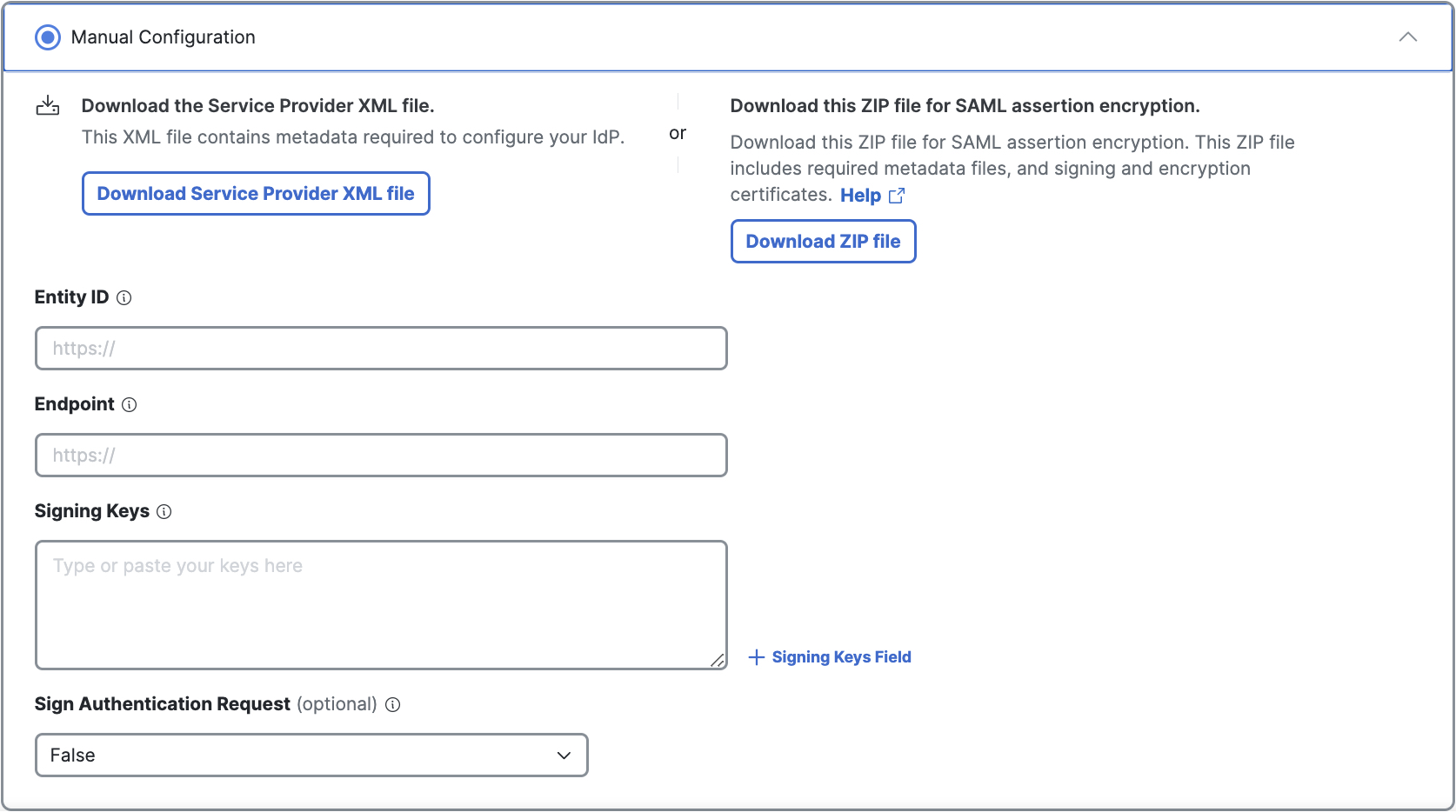
-
Download the service provider files.
a. Click Download Service Provider XML file for the metadata XML file.
b. (Optional) To enable Secure Access to sign or encrypt the SAML communications, click Download Zip file. -
Open the Cisco_SSE_SP_Metadata XML file.
a. The value of theentityIDfield issaml.fg.id.sse.cisco.com, which is the same value that you copied in Step 2 – Select Okta SAML Identity Provider in Secure Access.
b. Copy the value ofLocation,https://fg.id.sse.cisco.com/gw/auth/acs/response.
c. If you require a signing certificate, copy the value ofX509Certifcate. -
Copy the certificates from the Cisco_SSE_SP_Metadata XML file to a new file and save. Use the certificate file in the next step when you create the app integration in Okta.
Step 4 – Configure the Okta App Integration
In Okta, configure the Okta SAML IdP integration with the Secure Access metadata and certificates. For more information, see Configure Okta with the Secure Access SAML Metadata
Step 5 – Add Okta Metadata in Secure Access
First, get the Okta SAML IdP's metadata in Okta. For more information, see Get Metadata from Okta App Integration.
Then, in Secure Access, enter the Okta SAML IdP metadata from the Okta app integration.
- Entity ID—The Entity ID for the Okta SAML IdP.
- Endpoint—The metadata URL used to communicate with your Okta SAML IdP.
- Signing Keys—The Okta SAML IdP's x.509 certificate that is used to sign the authentication request.
- Signed Authentication Request—Choose whether to sign the authentication request for the Okta SAML IdP.

-
For Entity ID , enter the Okta app integration's value of Metadata URL.
-
For Endpoint, enter the Okta app integration's value of Sign on URL.
-
For Signing Keys, enter the Okta app integration's value of Signing Certificate.
-
(Optional) For Signed Authentication Request, choose whether to sign the authentication request.
-
Click Done.
Configure Okta with the Secure Access SAML Metadata
Important: Your instance of the Okta SAML IdP must send the Cisco Secure Access User principal name in the NameID attribute in the SAML assertion.
Add the Secure Access service provider metadata to your instance of Okta. You must configure Secure Access as a generic SAML 2.0 application within Okta. Okta does not provide a method to upload Secure Access metadata for automatic configuration. Extract the EntityID and AssertionConsumerService values from the Secure Access metadata file and add these values in Okta.
Note: If you have general questions about the Okta SAML IdP, we recommend that you contact Okta.
- Sign in to your instance of Okta, then navigate to Applications > Create a new app integration.
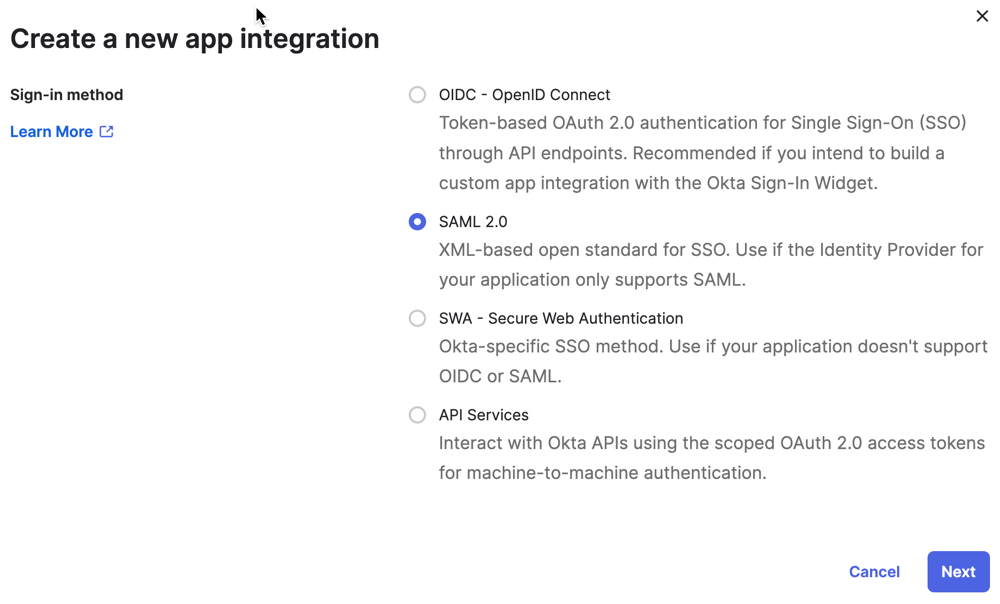
-
Click SAML 2.0, and then click Next.
-
For General Settings, add a name for the app integration, and then click Next.
-
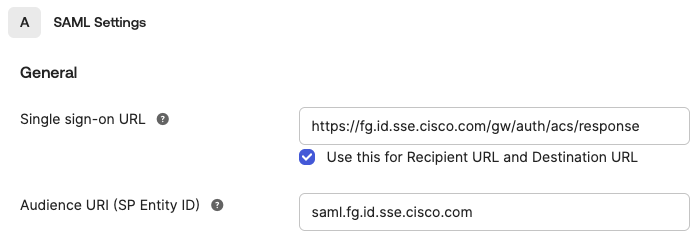
For SAML Settings > General, enter the Secure Access service provider metadata URL and the certificates from the file that you downloaded in Step 3 – Download the Secure Access SP Metadata and Certificates .
-
For Single sign-on URL, add
https://fg.id.sse.cisco.com/gw/auth/acs/response. -
For Audience URI (SP Entity ID), add
saml.fg.id.sse.cisco.com, or the organization-specific entity ID. -
For Name ID format, choose EmailAddress.
-
-
(Optional) Click Show Advanced Settings.
-
(Optional) For Signature Certificate, upload the root certificate that you downloaded from the Cisco_SSE_SP_Metadata XML file. Click Preview the SAML Assertion to show the created metadata file, and then click Next.
-
Click I'm an Okta customer adding an internal app.
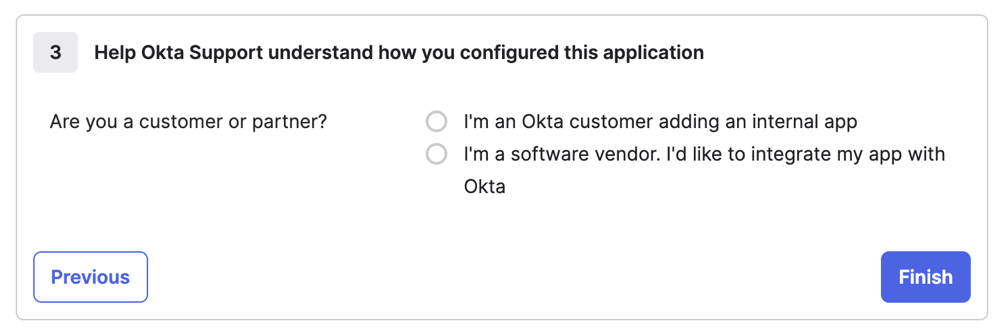
- Click Finish.
Get Metadata from Okta App Integration
Get and save the Okta metadata created in the Okta app integration. You will add the metadata for the Okta SAML IdP in your Secure Access SSO authentication profile for Okta.
-
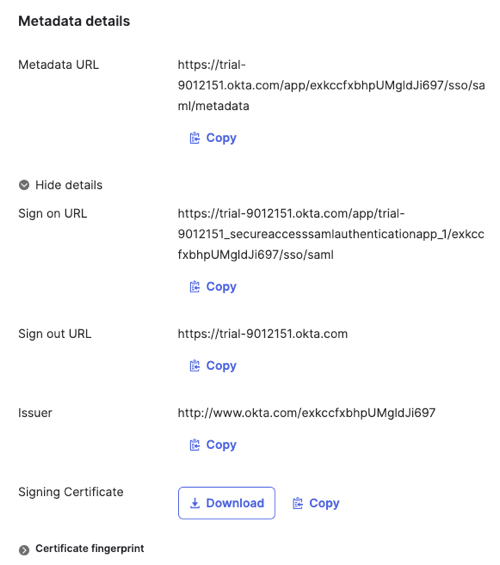
On Okta, navigate to Sign on > Settings > Metadata details.
-
For Metadata URL, copy the Okta SAML IdP metadata URL.
-
Click More Details.
-
For Sign on URL, copy the Okta SAML IdP sign-on URL.
-
For Signing Certificate, copy or download the Okta certificate.
Test the Identity Provider Integration
To complete the integration of the Okta SAML IdP with Secure Access, evaluate the single sign-on authentication through the IdP. For more information, see Test SAML Identity Provider Integration.
View the SAML Certificates in Secure Access
Once you have completed the integration of an Okta SAML IdP in Secure Access, you can manage the root certificates used in SAML authentication for Secure Access (service provider) and the SAML IdP. For more information, see Manage Certificates.
Configure Microsoft Entra ID for SAML < Configure Okta for SAML > Configure AD FS for SAML
Updated about 2 months ago
