View the Remote Access Log Report
The Remote Access Log report lists users' connection events that are related to remote access, tracked over distinct time periods.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
View the Remote Access Log Report
- Navigate to Monitor > Reports > Remote Access Logs.
- Choose a time frame of remote access events.
- Use the search bar to find remote access events by identity or endpoint device OS version. Identity includes the columns User and Device Name.
Note: If you have configured rules to traffic originating from IP addresses in network segments that include Security Group Tags, then you can search for connection events by SGT. When present, SGTs will be appended to the User column value. For more information, see Integrate ISE with Secure Access and Integrate Catalyst SD-WAN with Secure Access. - Refine your search using the following filters to help identify security issues that require attention.
- AAA
- Addr Assignment Fail
- Access Allowed
- Administrator Reset
- Authentication Check
- Authorization Check
- Cert Auth Check
- Certificate Expired
- Client Type Not Supported
- Connection Lost
- Connection Preempted
- DDNS Update Failed
- Geocompliance Check
- Geocompliance Service Unavailable
- IKE Delete
- IKEV2 Check
- IPSec Error
- Max Time Exceeded
- Port Error
- Posture Check
- Posture Check Failed
- SA Expired
- Static IP Addr Assignment Fail
- TLS Check
- Unknown Disconnection Reason
- Unknown Failed Reason
- User Requested
- Identities lets you filter by connection events with Security Group Tags (SGT) you have configured rules to traffic originating from IP addresses in network segments that include SGTs. When present, SGTs will be appended to the User column value. For more information, see Integrate ISE with Secure Access and Integrate Catalyst SD-WAN with Secure Access.
Note: Each filter is dynamic, except for Identities, and will only display filter option values that are present in the connection data. If no option values are present in the data for a filter, that filter remains hidden.
- The table includes the following categories:
- User—The name of the user in Secure Access.
- Device Name—The name of the device in Secure Access.
- Connection Event—The identity used to determine which policy applied to this activity
- Event Details— The category of activity or action committed.
- Public IPv4 Address— The public-facing IPv4 address configured in the VPN profile.
- Internal IPv4 Address— The internal IPv4 address configured in the VPN profile.
- Internal IPv6 Address—The internal IPv6 address configured for the VPN profile.
- VPN Profile— The name of the VPN profile associated with the event.
- Session Type— The type of network security protocols detected in the event.
- OS Type and Versions— The OS type and software version of the machine associated with the event.
- Secure Client Version— The version of the Secure Client version.
- Session Duration— Duration of the session, if terminated.
- Region— The region configured in the VPN profile that is associated with the event.
- Event Time— The day, year, and timestamp of the event.
View Event Details
There are two options to view details of an event.
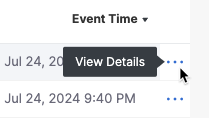
- Option 1: Click the View Details icon (the blue ellipsis at the right end of each row).
- Option 2: Hover over an Event Details field in any row, then click Read More below the ASA syslog message ID.
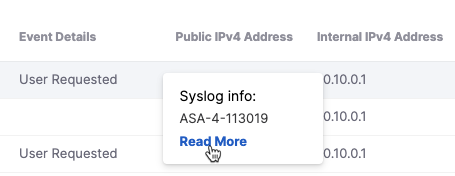
Result: The Event Details drawer displays detailed information about an individual event.
Extra information is available in the Event Details window:
- Last Connected— The timestamp when this users was last connected to the machine.
- Posture profile information— The posture profile associated with the event.
At the bottom of the Event Details window click View More Details to view VPN specific event details. The following categories is displayed:
-
Duration— The duration of the event.
-
Machine ID— The unique identifier assigned to the client machine.
-
Redirect ACL— The redirect access control l (ACL) that originates from the user or device.
-
Redirect URL—The URL where a user is automatically sent after attempting to access a different URL.
-
Security group Tag— The unique identifier assigned to a device or user, representing their security role or access level within the network.
-
Audit Session ID— The unique identifier generated and associated with a user's process when they successfully log in or connect.
-
Tunnels— How many tunnels are contained within the VPN profile and tunnel information.
From your search results, you can click an identity or destination and go to their respective detailed report.
Remote Access Log Report < View the Remote Access Log Report > Activity Search Report
Updated 4 days ago
