Configure a Site-to-Site VPN tunnel with Amazon Web Services
Deploy a site-to-site (S2S) VPN tunnel from Amazon Web Services (AWS) to Cisco Secure Access. An AWS S2S VPN in Secure Access will support the following:
- Tunnel redundancy with high availability for branch site connections to your Amazon Virtual Private Cloud (Amazon VPC). For more information, see Throughput and Multiple Tunnels and Failover for Branch Connections in Secure Access Data Centers.
- Connection over IPsec (Internet Protocol Security) with authentication negotiated and traffic encrypted by IKEv2 (Internet Key Exchange, version 2). For more information, see Supported IPsec Parameters.
- Dynamic (BGP) routing. For more information, see Routing Options and Guidelines.
Table of Contents
Prerequisites
- A valid Cisco Secure Access account.
- An AWS account with an active subscription and an Amazon VPC.
Configure S2S Tunnels with Dynamic Routing with BGP
Follow these steps to create an S2S tunnel connection on IPsec/IKEv2 between your Amazon VPC and Secure Access.
- Step 1: Create a VPC in AWS
- Step 2: Create a Transit Gateway in AWS
- Step 3: Create two placeholder Customer Gateways in AWS
- Step 4: Create a Site-to-Site VPN connection for each customer gateway
- Step 5: Create a network tunnel group in Secure Access
- Step 6: Replace the placeholder customer gateways in AWS
- Step 7: Verify tunnel status in AWS and Secure Access
- Step 8: Modify subnet routing tables to send traffic to the AWS Transit Gateway
The S2S VPN topology depends on components configured in the following order. Components in the diagram are numbered by order of configuration.
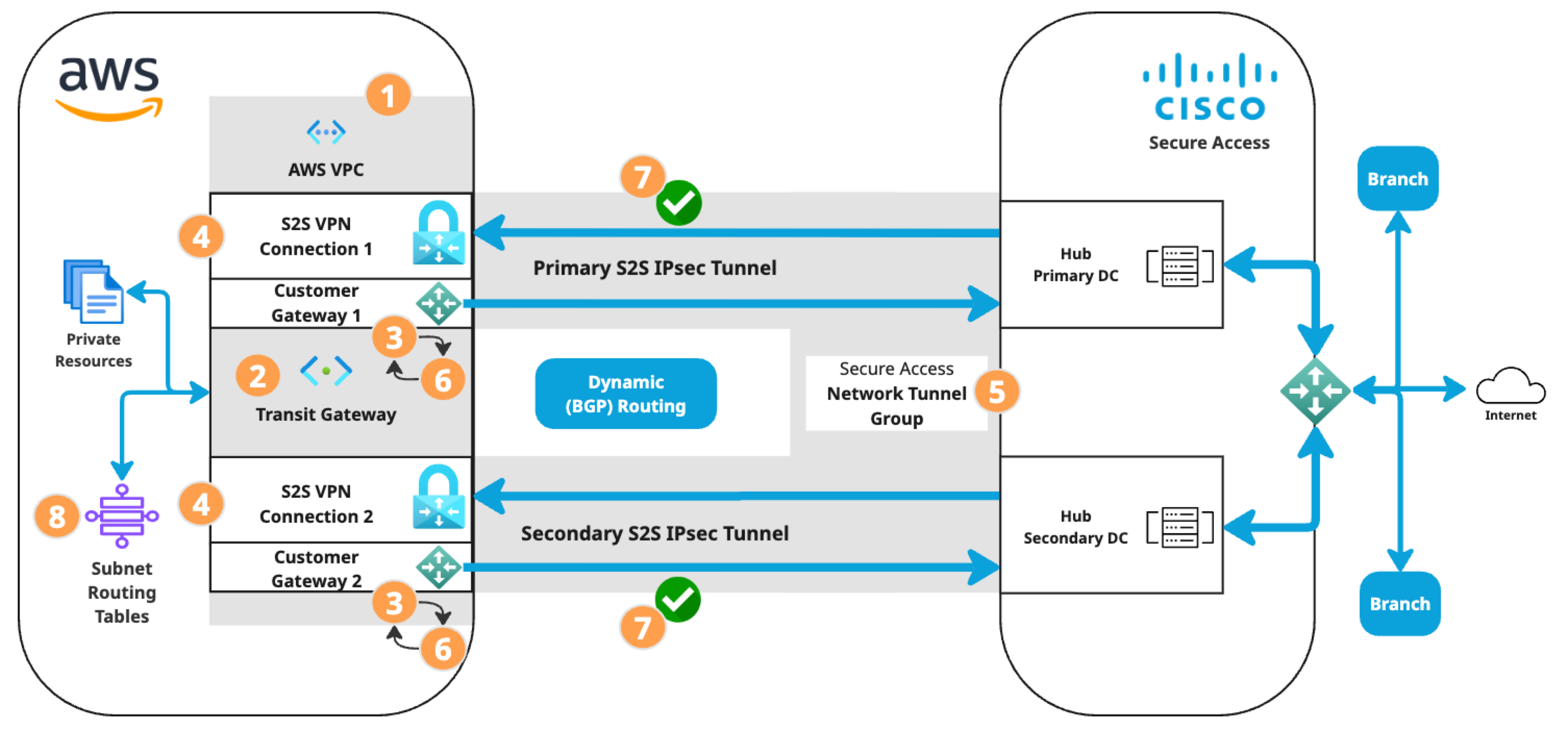
For more detailed instructions, refer to Amazon Virtual Private Cloud Documentation. Please note that AWS may update their documentation without notice.
Step 1: Create a VPC in AWS
In your AWS dashboard, create a VPC with two subnets. Skip this step if you already have a VPC. For more information, see Create a VPC.
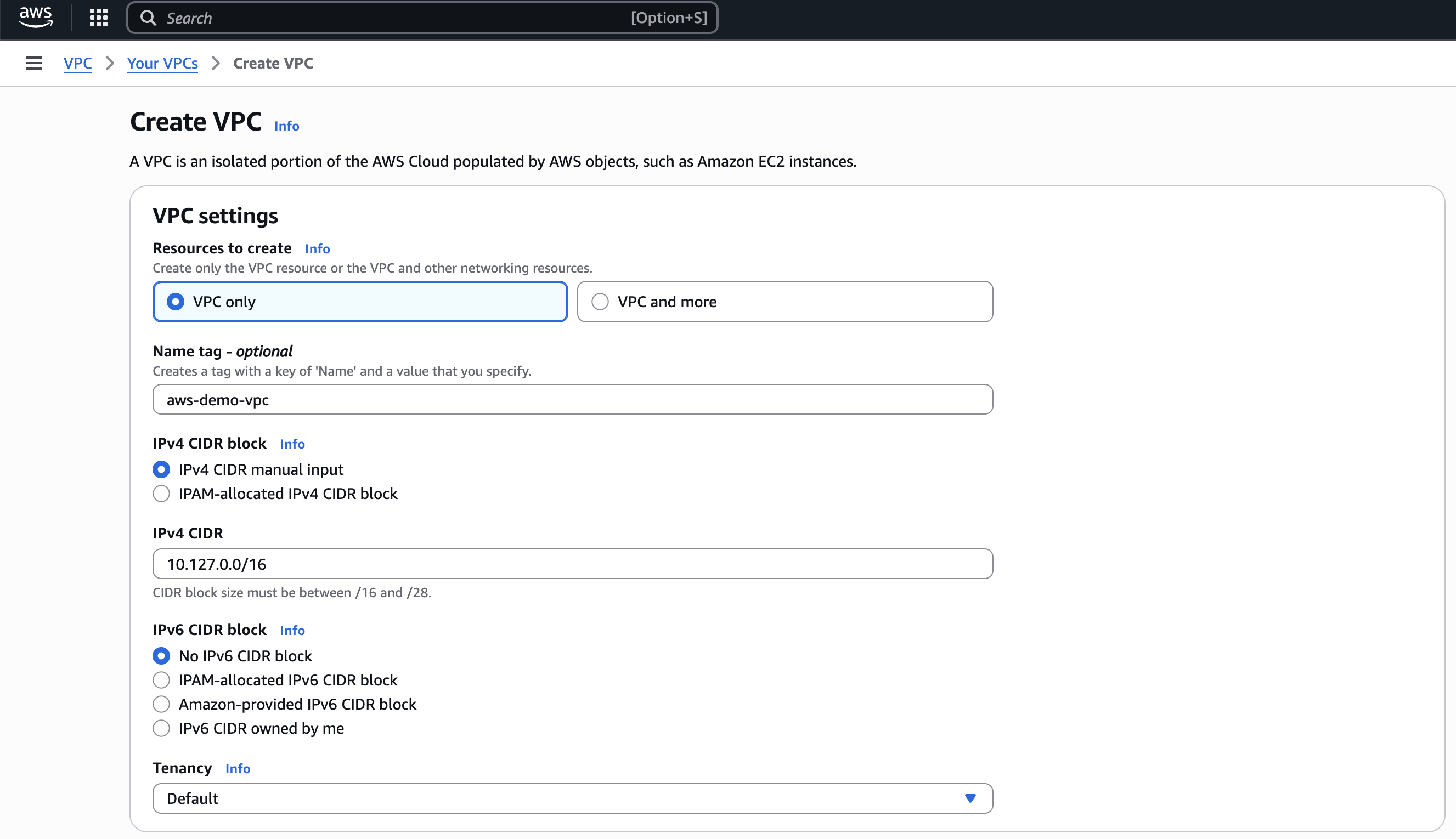
- Navigate to VPC dashboard > Create VPC.
- Resources to create: VPC only
- IPv4 CIDR block: Choose IPv4 CIDR manual input and enter an IPv4 address range for your VPC.
- Click Create VPC.
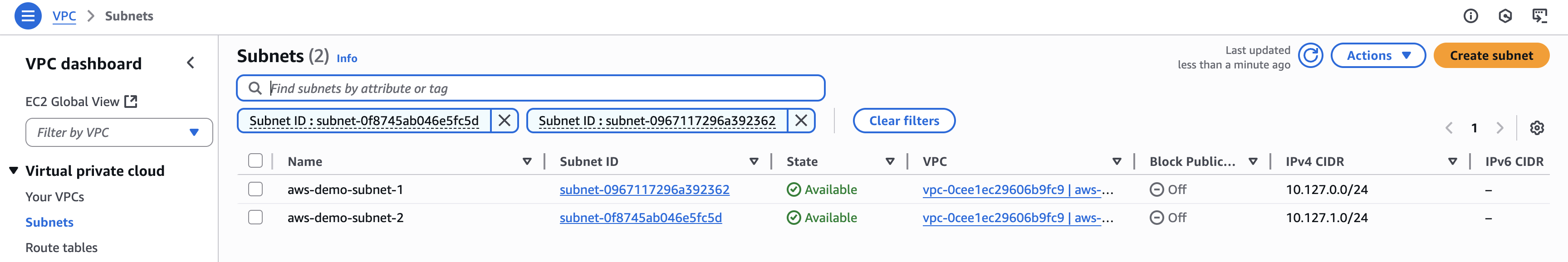
Create two subnets. For more information, see Create a subnet.
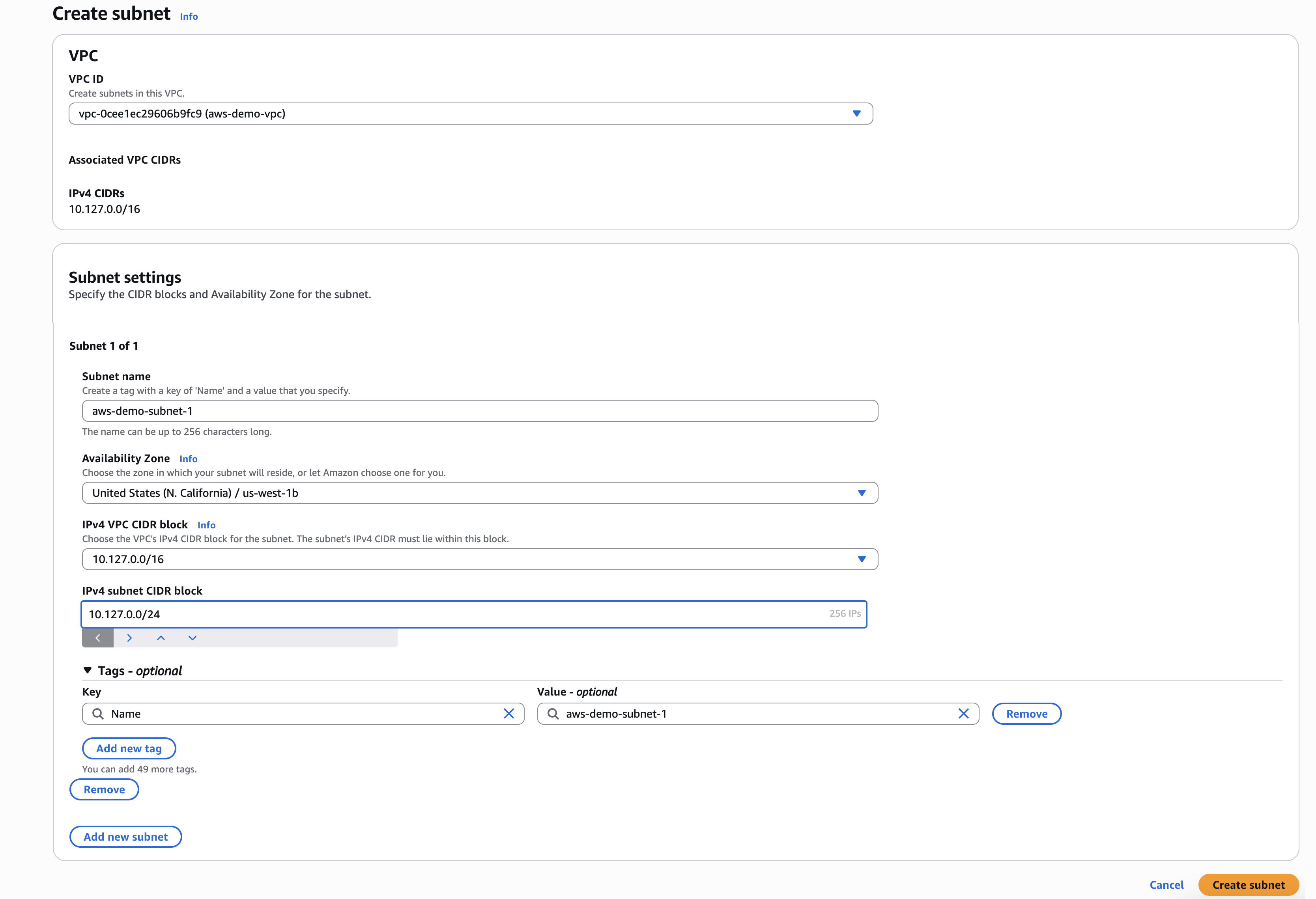
- Navigate to VPC dashboard > Virtual private cloud > Subnets.
- Click Create subnet.
- VPC ID: Choose your VPC by ID or IP address.
- Configure subnet 1 of 2.
- Subnet name: Enter a name that indicates the VPC and whether this is the first or second subnet.
- Availability Zone: Choose a zone.
- IPv4 subnet CIDR block: Enter an IPv4 CIDR block that is within the VPC CDIR range and does not overlap with the IPv4 range of other subnets in the VPC.
- Click Add a subnet. Repeat the above steps to configure subnet 2 of 2 with a different availability zone for high availability.
- Click Create subnet.
Step 2: Create a Transit Gateway in AWS
Create a transit gateway in AWS with an attachment to your Amazon VPC. For more information, see Connect your VPC to other VPCs and networks using a transit gateway, Create a transit gateway using Amazon VPC Transit Gateways, and Create a VPC attachment using Amazon VPC Transit Gateways.
- Click Transit gateways in the left navigation menu of the AWS VPC dashboard.
- Create a transit gateway with an Amazon-side Autonomous System Number (ASN).
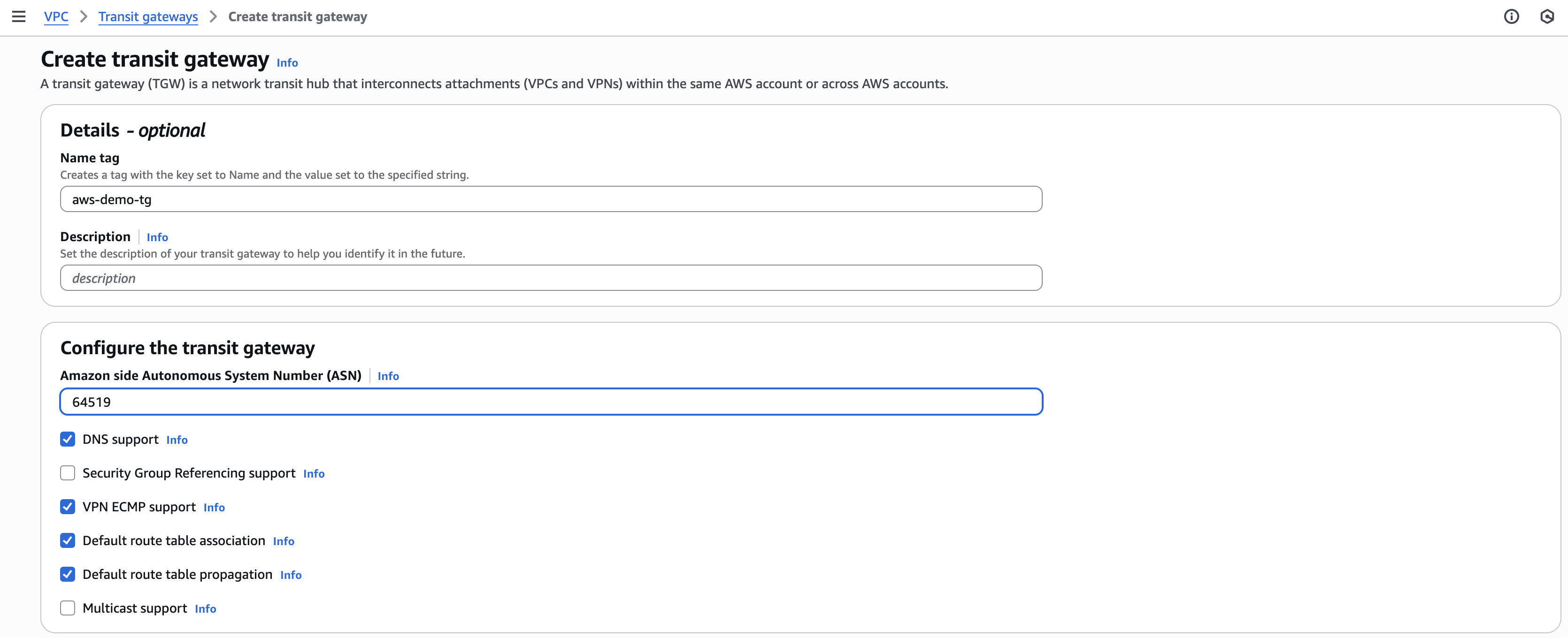
Note: The Amazon side ASN is required for dynamic routing supported by Border Gateway Protocol (BGP) sessions. This example uses 64519. The range is from 64512 to 65534 for 16-bit ASNs. We recommend entering an ASN that is not already in use by other transit gateways in your Amazon VPC. Do not use 64512, which is reserved for Secure Access BGP peers.
- Click Create transit gateway.
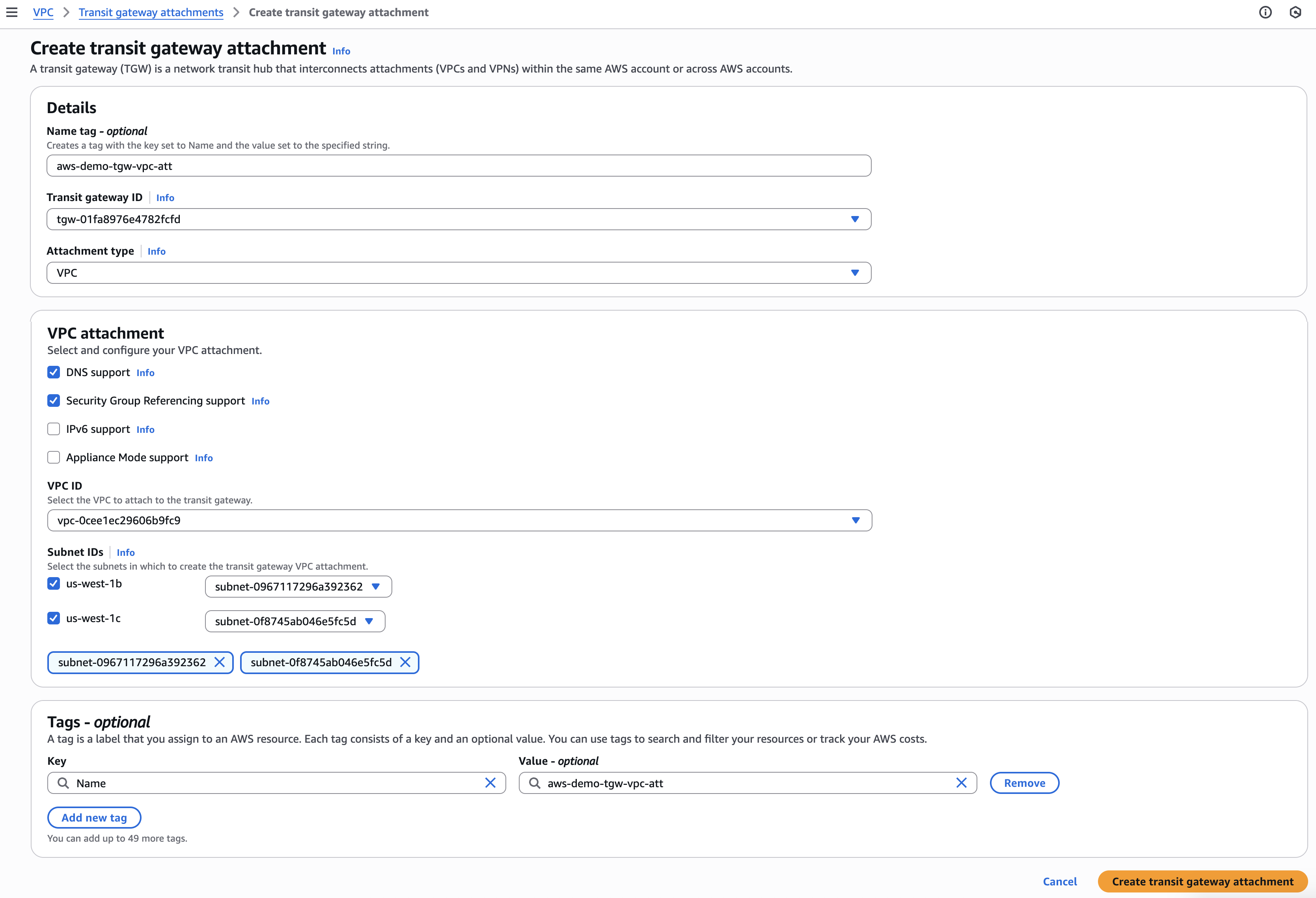
- When the gateway Status is Available, create a Transit gateway attachment between the transit gateway and the VPC.
- Click Transit gateway attachments in the left navigation menu of the AWS VPC dashboard.
- Click Create transit gateway attachment.
- Transit gateway ID: Select the ID of the gateway you just created.
- VPC ID: Select the ID of the VPC you created in Step 1.
- Click Create transit gateway attachment.
Step 3: Create two placeholder Customer Gateways in AWS
Create two customer gateways with S2S connections. For more information, see Get started with AWS Site-to-Site VPN, Step 1: Create a customer gateway and Step 5: Create a VPN connection.
Note: These gateways will act as temporary placeholders that provide outside IP addresses required by the Secure Access network tunnel group configuration in the next step. The network tunnel group will provide the Secure Access BGP ASN and public IP addresses for the Secure Access Peer IP address DCs that you will use to create two new customer gateways in AWS.
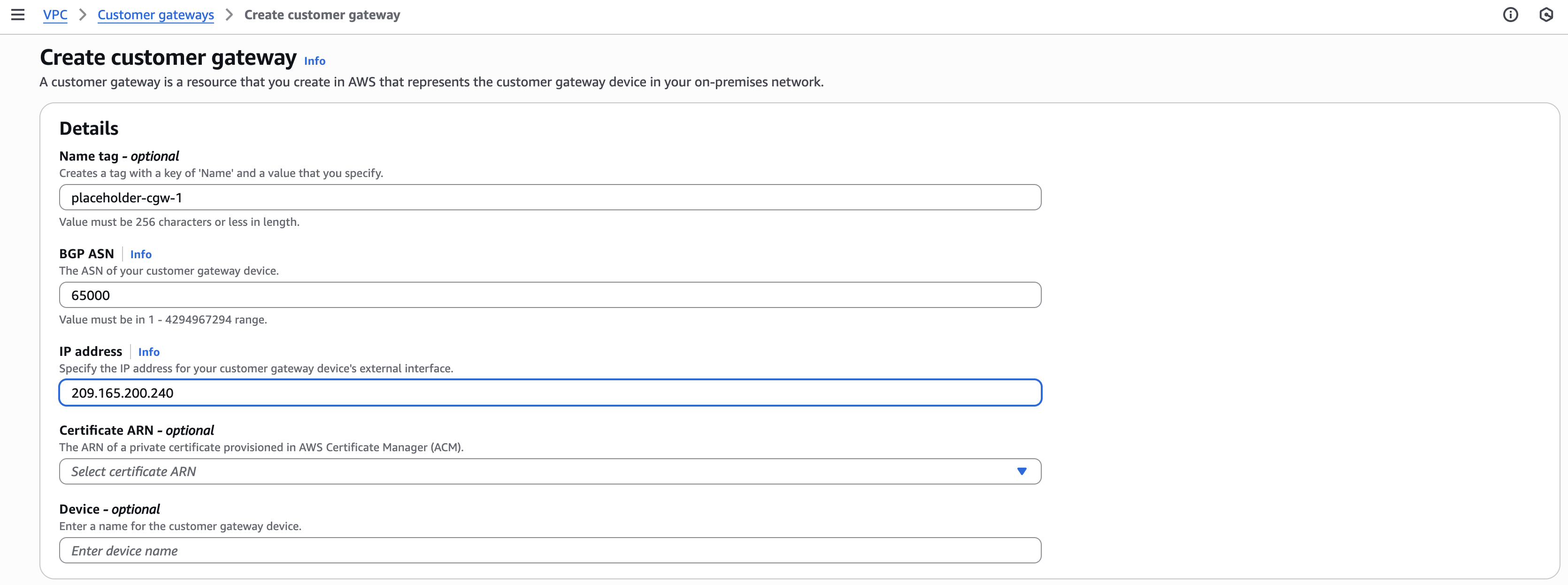
- In the left navigation menu of the AWS VPC dashboard, navigate to Virtual private network (VPN) and click Customer gateways.
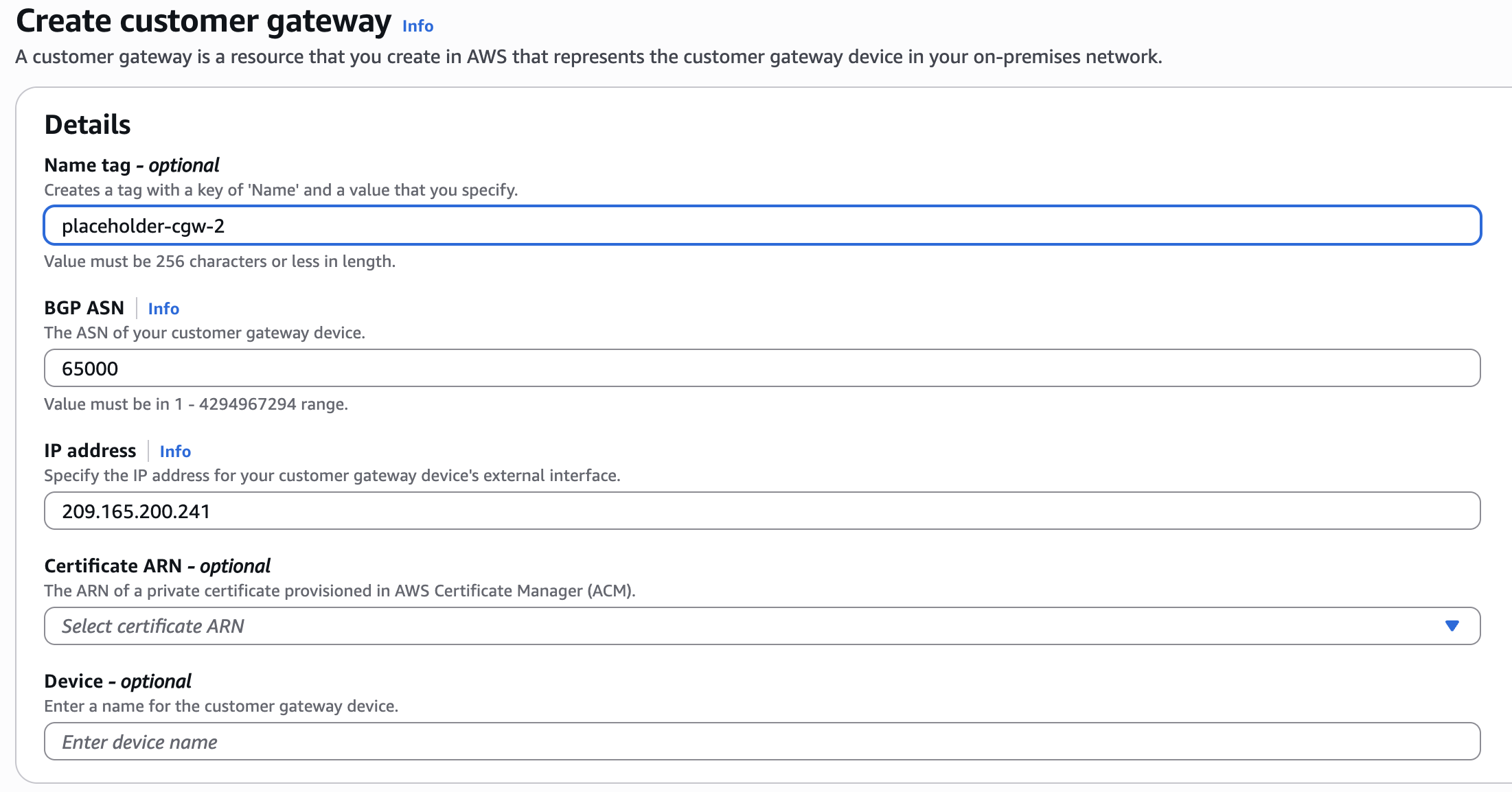
- Click Create customer gateway.
- IP address: Enter a placeholder public IP address. This example uses 209.165.200.240.
- Click Create customer gateway.
- Repeat these steps to create a second customer gateway with a different placeholder IP address (for example, 209.165.200.241).
Step 4: Create a Site-to-Site VPN connection for each customer gateway
- In the left navigation menu of the AWS VPC dashboard, navigate to Virtual private network (VPN) and click Site-to-Site VPN connections.
- Click Create VPN connection.
- Target gateway type: Transit gateway
- Select the virtual private gateway that you created earlier.
- Customer gateway: Existing
- Select the first customer gateway that you created earlier.
- Routing options: Dynamic
- Tunnel 1 options:
- Inside IPv4 CIDR for tunnel 1: Enter a size /30 IPv4 block from the 169.254.0.0/24 range.
Note: AWS allows inside CIDR addresses in the 169.254.0.0/16 range in which the network address is the first 16 bits, with 65,536 IP addresses in the range 169.254.0.0 to 169.254.255.255. Secure Access utilizes the 169.254.0.0/24 subnet range for BGP peer addresses, see Secure Access BGP Configuration.
- Pre-shared key for tunnel 1: Enter a passphrase. You will enter this in the Secure Access network tunnel group in the next step.
- Advanced options for tunnel 1: Edit tunnel 1 options.
- DPD timeout action: Restart.
- Startup action: Start.
- Repeat these steps for Tunnel 2 options with a different size /30 IPv4 block from the 169.254.0.0/24 range. See the note above about the difference in CIDR range requirements between AWS and Secure Access.
- Click Create VPN connection.
- Repeat these steps to create a second VPN connection.
- Select the second customer gateway that you created earlier.
- Inside IPv4 CIDR for tunnels 1 and 2 should match the inside IP addresses you entered for tunnels 1 and 2 in the first S2S connection.
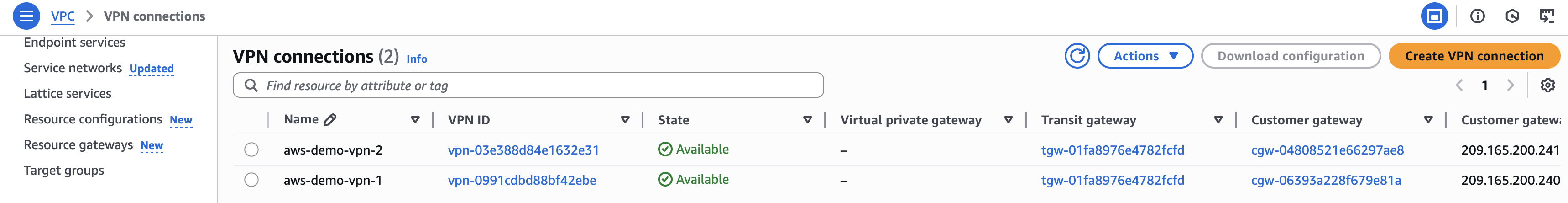
- Confirm that both S2S VPN connections have an available State.
Step 5: Create a network tunnel group in Secure Access
Configure a network tunnel group in Secure Access. For a more detailed procedure, see Add a Network Tunnel Group.
- Step 1 - General Settings: Set Device Type to AWS.
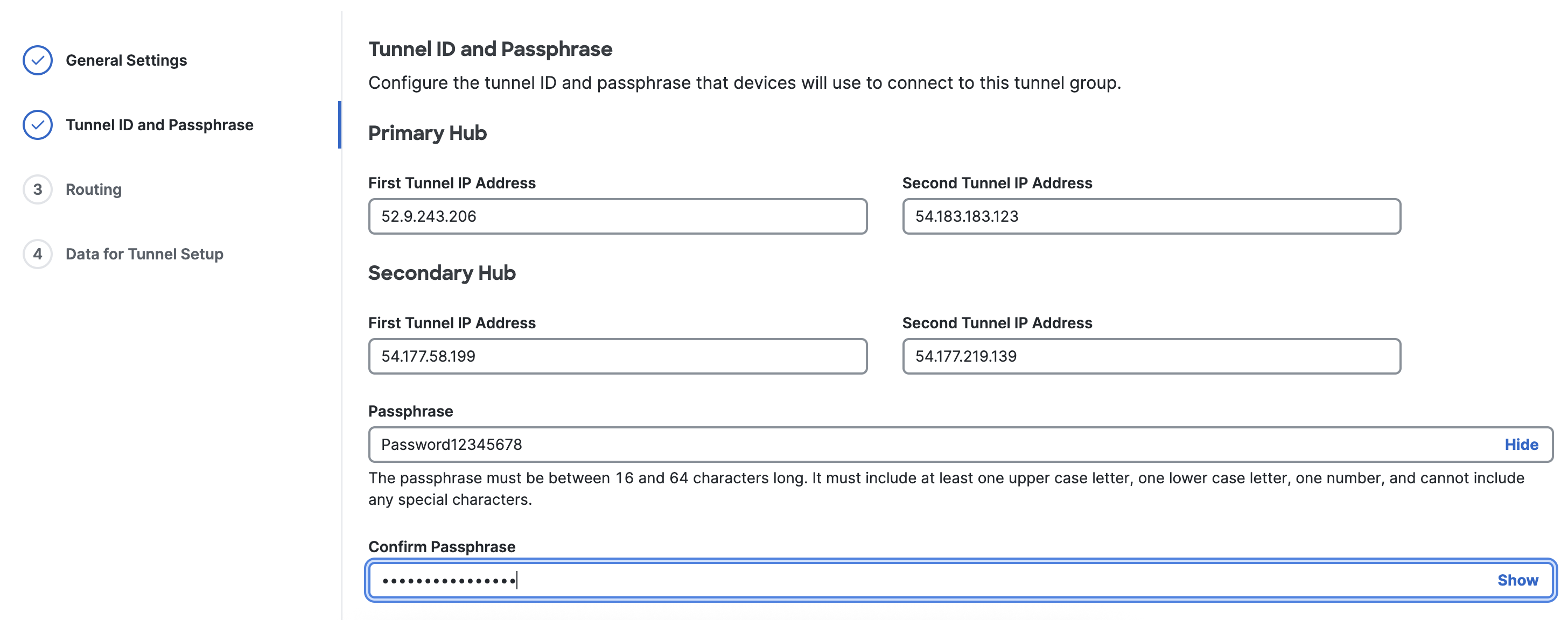
- Step 2 - Tunnel ID and Passphrase: Each AWS customer gateway that you created in the previous step will have two tunnels, and each tunnel will have an outside IP address.
- Primary Hub, First Tunnel IP Address: Enter the outside IP address of tunnel 1 for AWS S2S VPN connection 1.
- To find this IP address in AWS, navigate to VPC > VPN connections, click the VPN ID of VPN connection 1, then navigate to Tunnel state > Tunnel 1 > Outside IP address.
- Primary Hub, Second Tunnel IP Address: Enter the outside IP address of tunnel 2 for AWS S2S VPN connection 1.
- Secondary Hub, First Tunnel IP Address: Enter the outside IP address of tunnel 1 for AWS S2S VPN connection 2.
- Secondary Hub, Second Tunnel IP Address: Enter the outside IP address of tunnel 2 for AWS S2S VPN connection 2.
- Passphrase: Enter the pre-shared key that you created for the tunnels in AWS.
- Primary Hub, First Tunnel IP Address: Enter the outside IP address of tunnel 1 for AWS S2S VPN connection 1.
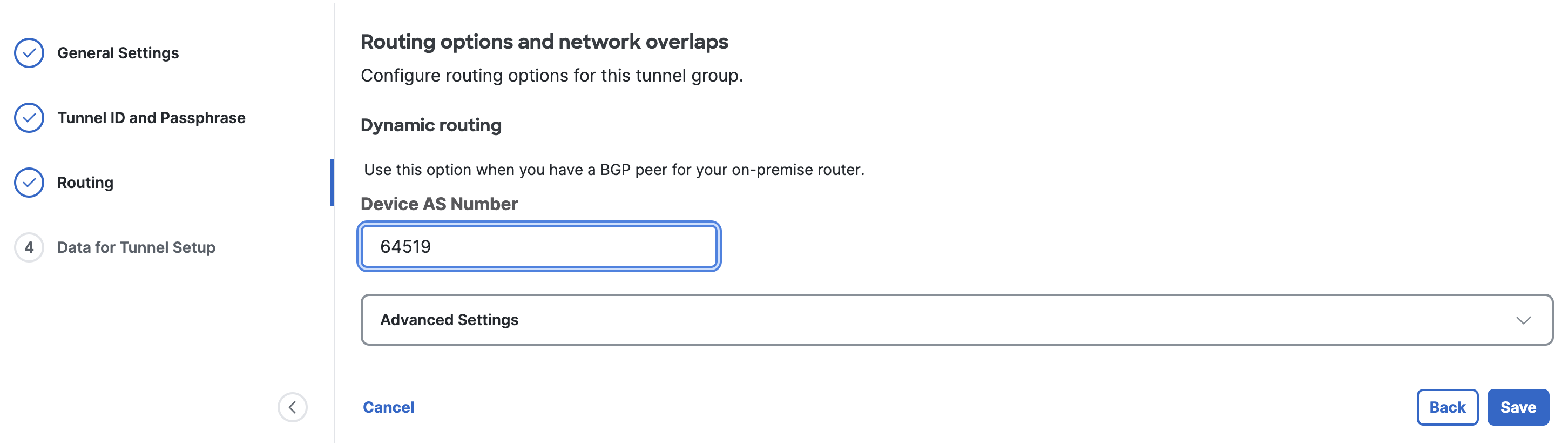
- Step 3 - Routing, Dynamic routing: Enter the Amazon-side Autonomous System Number (ASN) configured for the Transit Gateway in AWS.
- Step 4 - Data for Tunnel Setup: Copy or download the primary and secondary tunnel IDs, data center (DC) IP addresses, and passphrase (pre-shared key). Note: This is the only time your passphrase will be displayed.
Step 6: Replace the placeholder customer gateways in AWS
Configure two more customer gateways in AWS to connect to the Secure Access DC IPs. These will replace the placeholder customer gateways that you created in Step 3: Create two placeholder Customer Gateways with S2S connections in AWS.
Note: It is not possible to update the placeholder customer gateways. You must create new customer gateways with the DC IPs from Secure Access, then modify the VPN connection in AWS to target the new customer gateways.
Before you begin, you will need this information from Secure Access:
- The DC IP addresses for the primary and secondary tunnel from Step 4 - Data for Tunnel Setup. You can also find this information in Secure Access by navigating to Connect > Network Connections > Network Tunnel Groups and clicking the network tunnel group name to see details.
- The Peer (Secure Access) BGP AS number for the network tunnel group. Find this information in Secure Access by navigating to Connect > Network Connections > Network Tunnel Groups and clicking the network tunnel group name to see details.
Create two customer gateways using the same procedure that you followed in Step 3:
- In the left navigation menu of the AWS VPC dashboard, navigate to Virtual private network (VPN) and click Customer gateways.
- Click Create customer gateway.
- BGP ASN: Enter the Peer (Secure Access) BGP AS from the Secure Access network tunnel group.
- IP address: Enter the DC IP address for the Secure Access primary tunnel.
- Click Create customer gateway.
- Repeat these steps to create a secondary customer gateway with the DC IP address for the Secure Access secondary tunnel.
Modify the VPN connection in AWS. For more information, see Modify AWS Site-to-Site VPN connection options.
- In the left navigation menu of the AWS VPC dashboard, navigate to Virtual private network (VPN) and click Site-to-Site VPN connections.
- Click the VPN ID of the first connection.
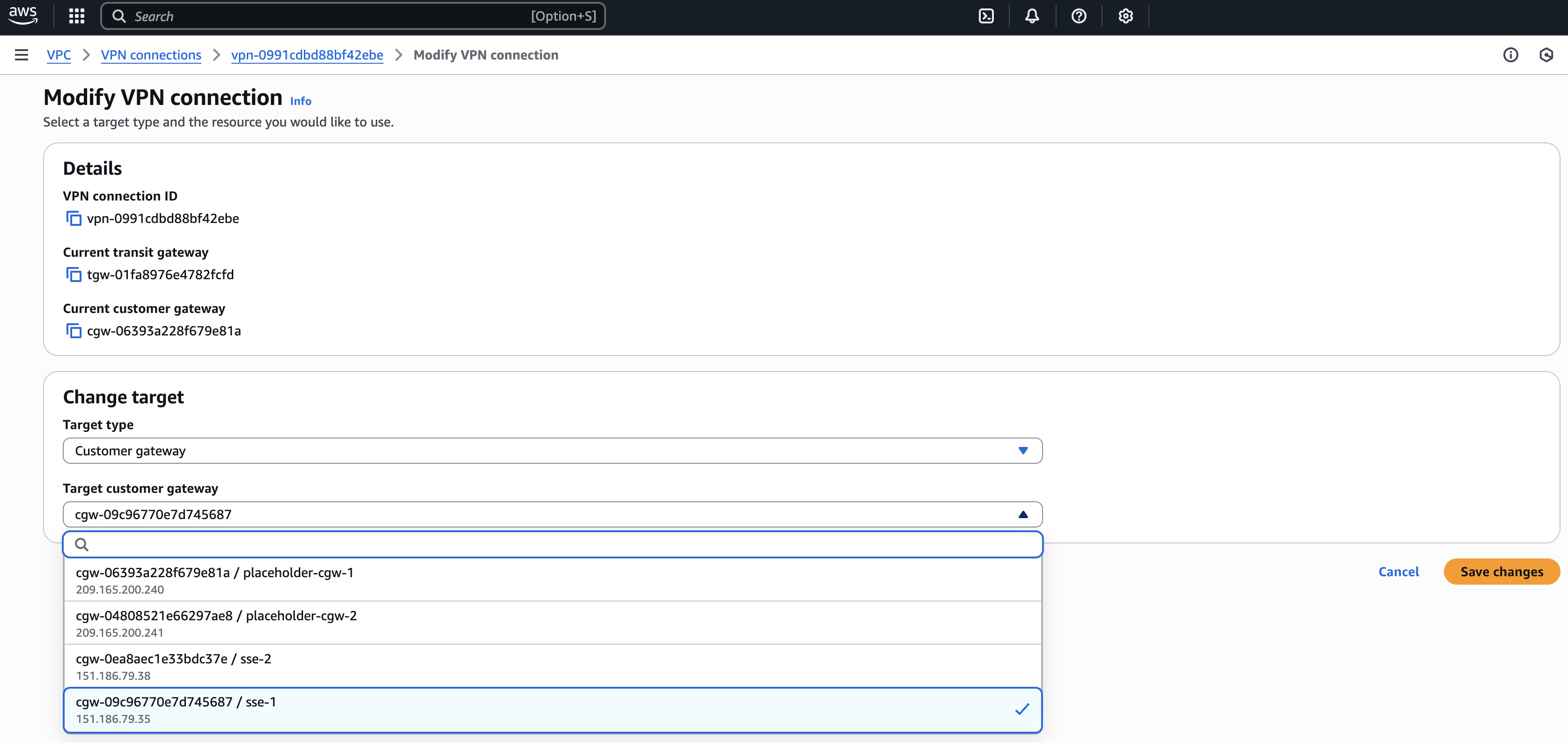
- Navigate to Actions > Modify VPN connection.
- Change Target customer gateway to the primary tunnel customer gateway created to replace the placeholder gateway.
- Click Save changes.
- Repeat these steps for the second VPN connection and the secondary tunnel customer gateway.
- Delete the placeholder Customer gateway.
Step 7: Verify tunnel status in AWS and Secure Access
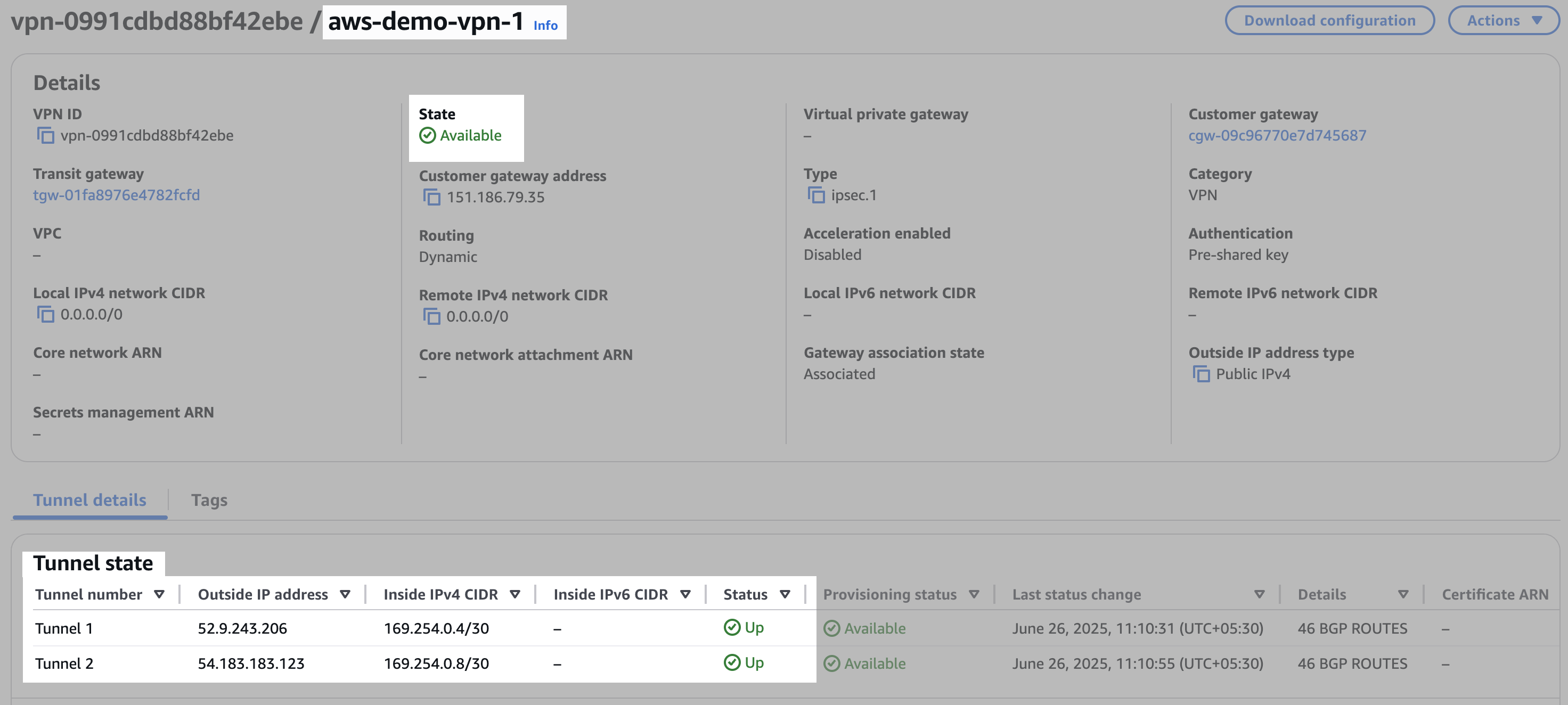
In the left navigation menu of the AWS VPC dashboard, navigate to Virtual private network (VPN) and click Site-to-Site VPN connections. Click the VPN ID of each VPN connection to confirm that the State is Available and that the Status of both tunnels is Up.
This example shows VPN connection 1 is Available and both tunnels are Up:
VPN connection 2 is also Available and both tunnels are Up.
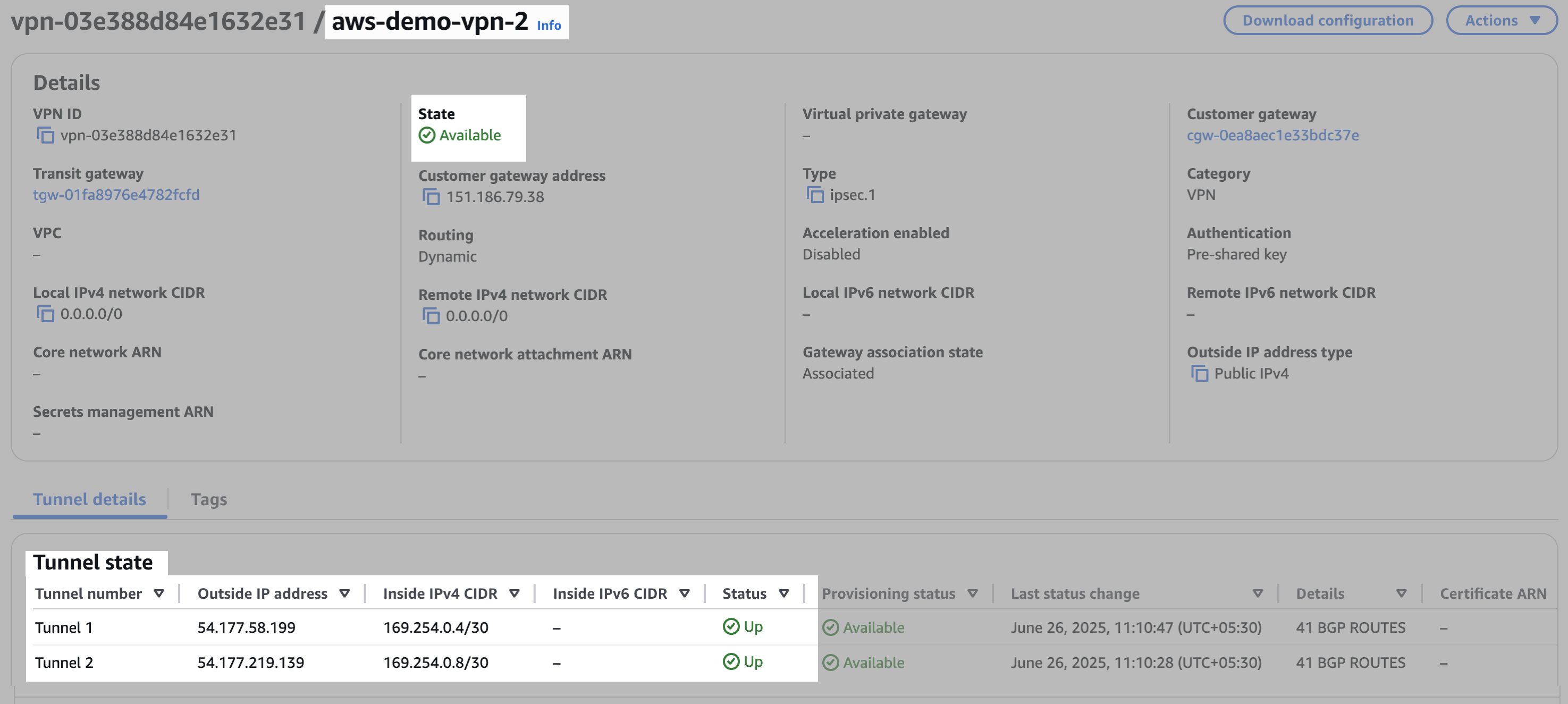
Note that each tunnel has a unique Outside IP Address. Tunnel 1 has the same Inside IPv4 CIDR range for each VPN connection, and Tunnel 2 has the same Inside IPv4 CIDR range for each VPN connection.
In Secure Access, navigate to Connect > Network Connections > Network Tunnel Groups and click the name of the network tunnel group to review the connection status with AWS.
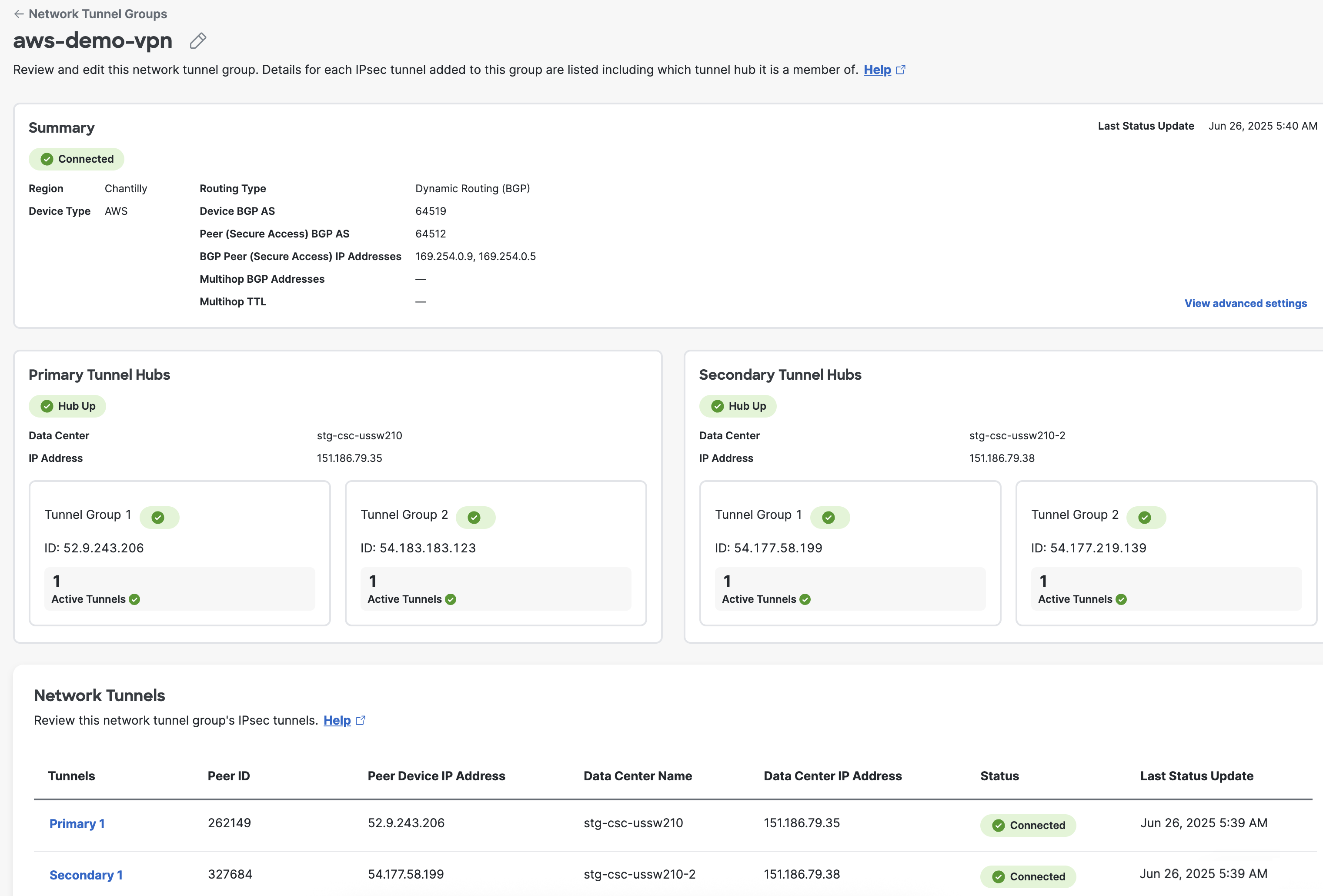
Under Primary Tunnel Hubs, the ID of Tunnel Group 1 should match the Outside IP Address of VPN connection 1, Tunnel 1 in AWS. The ID of Tunnel Group 2 in Secure Access should match VPN connection 1, Tunnel 2 in AWS.
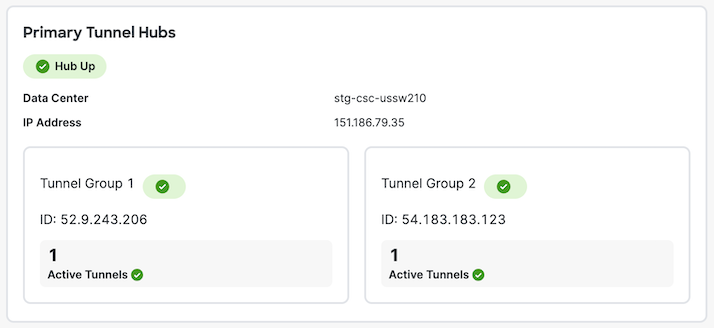
Under Secondary Tunnel Hubs in Secure Access, the tunnel group IDs should match the tunnel addresses of VPN connection 2 in AWS.
This confirms that the tunnel connection has been established between AWS and Secure Access DCs.
Step 8: Modify subnet routing tables to send traffic to the AWS Transit Gateway
To send traffic from the AWS VPC to the AWS transit gateway, modify the routing table of each subnet to target the Transit gateway ID. For more information, see Change a subnet route table.
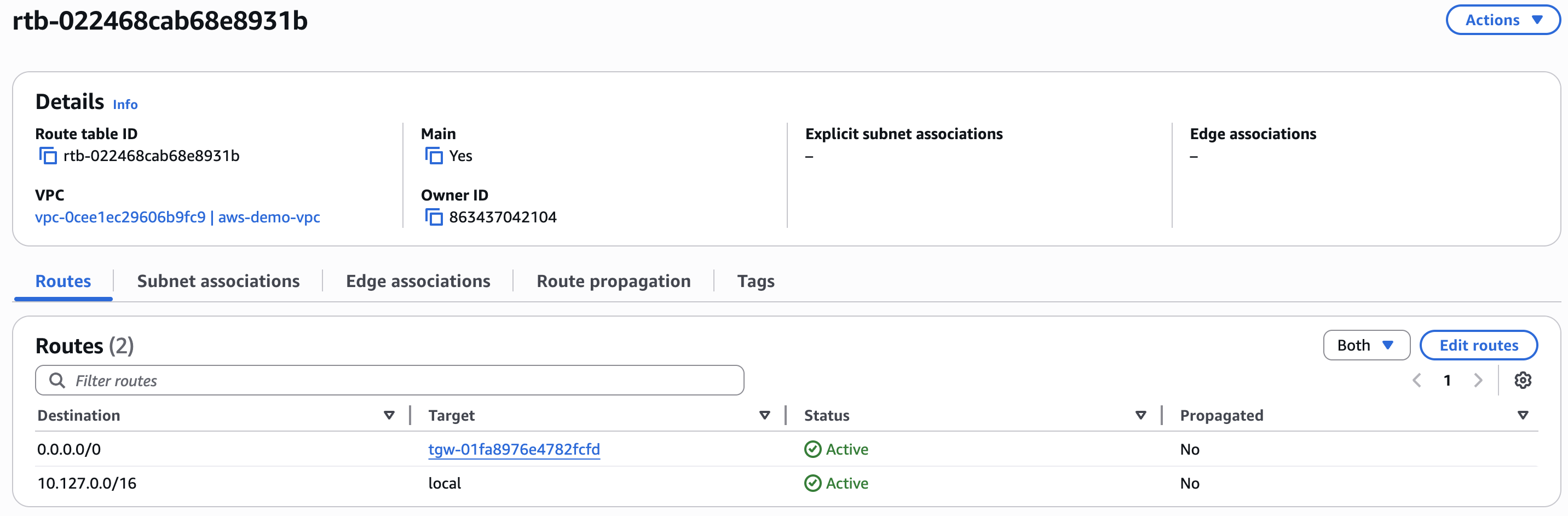
- In AWS, navigate to VPC dashboard > VPC ID > Main route table > Route table ID > Edit routes > Add route.
- Destination: 0.0.0.0/0.
- Target: Transit Gateway, select your Transit Gateway ID.
- Click Save changes.
In Secure Access:
- Navigate to Connect > Network Connections > Network Tunnel Groups.
- Click the name of the network tunnel group, then click a tunnel name to review Routing details.
- Client Routes show routes advertised by Amazon to Secure Access via BGP.
- Cloud Routes show routes advertised by Secure Access to Amazon via BGP.
This confirms that branch access to resources in your AWS VPC is now protected by the site-to-site (S2S) IPsec/IKEv2 VPN tunnel with Cisco Secure Access.
What to do next
For information about managing and monitoring your network tunnel group, see Manage Network Tunnel Groups.
Configure a Site-to-Site VPN tunnel with Microsoft Azure < Configure a Site-to-Site VPN tunnel with Amazon Web Services > Manage Resource Connectors and Groups
Updated 11 days ago
