Add an Internet Access Rule
The Cisco Secure Access policy is a collection of an organization's internet and private access rules. To start protecting user devices that connect to the Internet, add internet rules to the organization's Access policy.
This guide describes the steps to add an internet access rule and configure security controls and profiles.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- At a minimum, to add an internet access rule, configure the source and destination components and rule settings.
- For more information, see Components for Internet Access Rules.
- For more information, see Default Settings for Internet Access Rules.
- For other factors involved in creating and enforcing internet access rules, see Manage Internet Access Rules.
- In general, decryption is required to properly process HTTPS traffic, including traffic that will be blocked. For more information, see Security Profile.
Note: Prerequisites for internet access rules are similar to but different from prerequisites for private access rules.
Procedure
-
Navigate to Secure > Access Policy.
-
Click Add Rule > Internet Access.
At the top of the rule is a summary section. The Summary describes the security controls that you configure on this rule.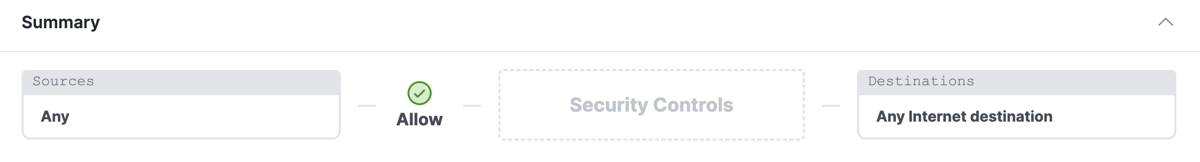
-
Navigate to Specify Access, and then configure the access criteria for the rule. For more information, see Access Options
-
Click Next.
Note: The Next button is not available until you give the rule a name and then click out of the Rule name field. -
Navigate to Configure Security, and then configure the security control settings for the rule. For more information, see Security Control Options.
-
Click Save.
-
(Optional) Enable or disable the rule using the toggle at the top of the page.
-
(Important) Additional rules are required for most traffic. For more information, see Ensure Rule Matching for Encrypted Internet Traffic.
Access Options
- Disable or enable the rule
- Logging settings
- Summary
- Rule name
- Rule order
- Rule action
- Pre-Configured Sources
- Composite Sources
- Pre-Configured Destinations
- Composite Destinations
- App Risk Profiles
- Advanced Application Controls
Disable or Enable the Rule
After you configure the rule and click Save, the rule will take effect only if this toggle shows as Enabled.
Logging settings
Logging options are at the top right corner of the page:
To choose options, click Edit.
For more information, see Manage Logging.
Summary
After you configure the rule, view a summary of the rule's action here.
If you see an Upgrade button, this means your company has an opportunity to upgrade to a licensing package that offers additional functionality. For details, contact your Cisco sales representative.
Rule Name
You must give your rule a name before you can click Next at the bottom of the page (to specify security controls.)
Rule Order
Specify where you want this rule in the overall rule order.
Secure Access applies the first rule in the list on the Access Policy page that matches the traffic.
Order your rules so that more specific rules are above more general rules that might also apply to the traffic.
For important guidelines, see Edit the Order of Rules on the Access Policy Page.
Rule Action
By default, access to internet destinations is allowed unless an access rule blocks or modifies access using the Warn or Isolate options.
The action you choose determines which other options are available in the rule.
Specify the rule action before you specify other settings including source and destination, or those configurations will be reset when you change the action.
- Allow - When the action is Allow, traffic can still be blocked if it does not pass the security controls specified in the rule.
- Block - If you want to display a notification page to end users who attempt to access a blocked destination. For more information, see Manage Notification Pages.
- Warn - When the action is Warn:
- End users must click a link in a warning notification to access the destination.
- The destination can include applications and application categories as well as content categories and content category lists.
- You can configure a custom warning notification that Secure Access will present to users who attempt to access a warned destination. You can also preview the notification page. See Manage Notification Pages.
- Decryption must be enabled in order to present the notification.
- For required certificates for displaying notifications, see Certificates for Internet Decryption.
- Isolate - If your license includes the Remote Browser Isolation feature, Secure Access creates a virtual browser that hosts applicable destination access requests. This action is available only for certain destinations.
For information about the Isolate action, see Understand Isolated Destinations.
If you see an Upgrade button, click it for information about enhanced functionality for this feature.
Pre-Configured Sources
We recommend that you create reusable components rather than adding source IP addresses directly to a rule. For more information, see Components for Internet Access Rules.
Note: The arrows out icon opens a window to configure the sources in your rule.
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.
-
Navigate to Specify Access and then click on the search bar under From.
-
For Select sources, click in the white space beside the default value ("Any") and choose the configured source components in your organization.
For descriptions of the different types of sources, including links to how to create reusable sources, see Components for Internet Access Rules.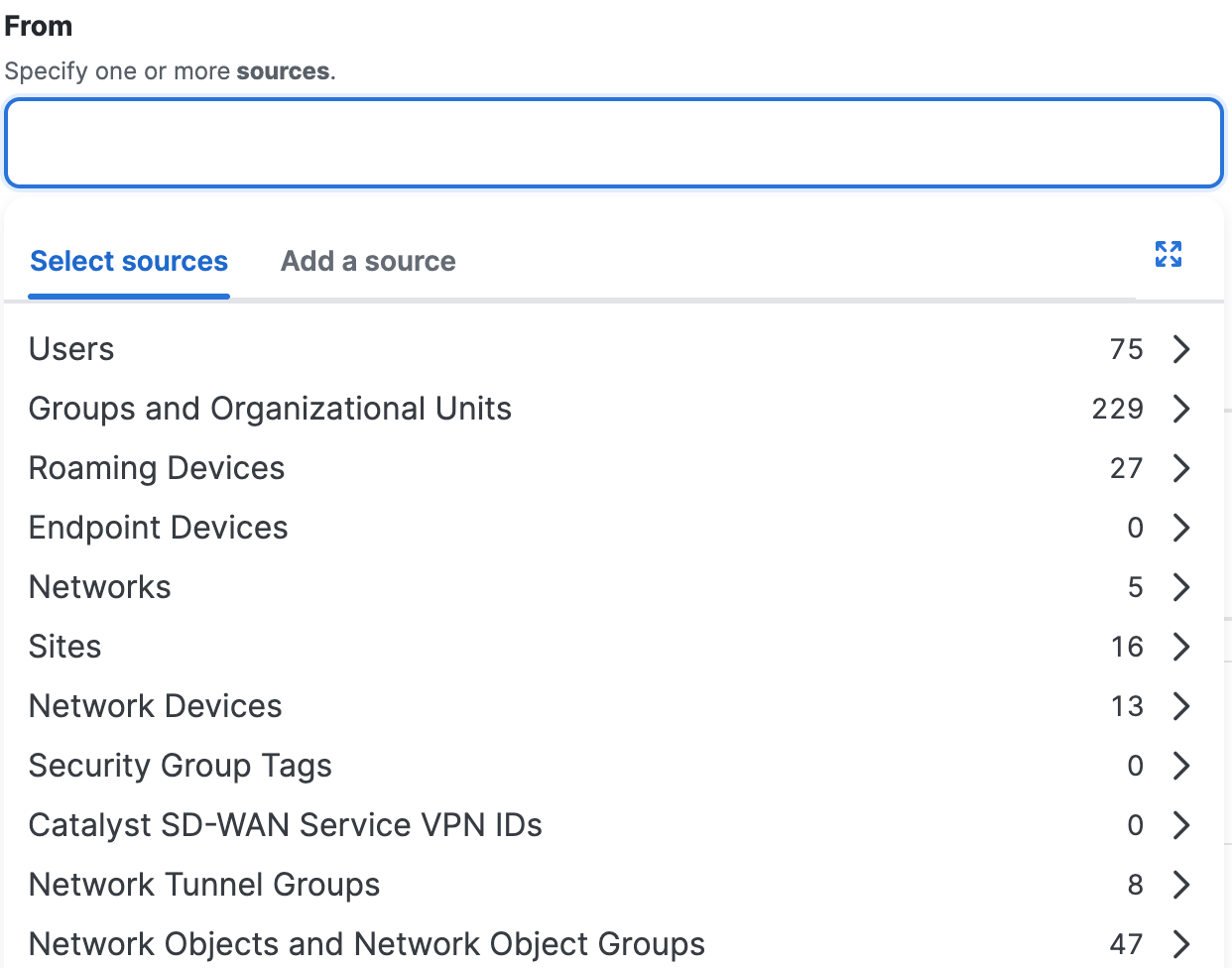
-
After you add a source component, click +More to view the list of sources that you added to the rule.
Click on the X to remove a previously-added source. Click Donewhen the list of sources is complete.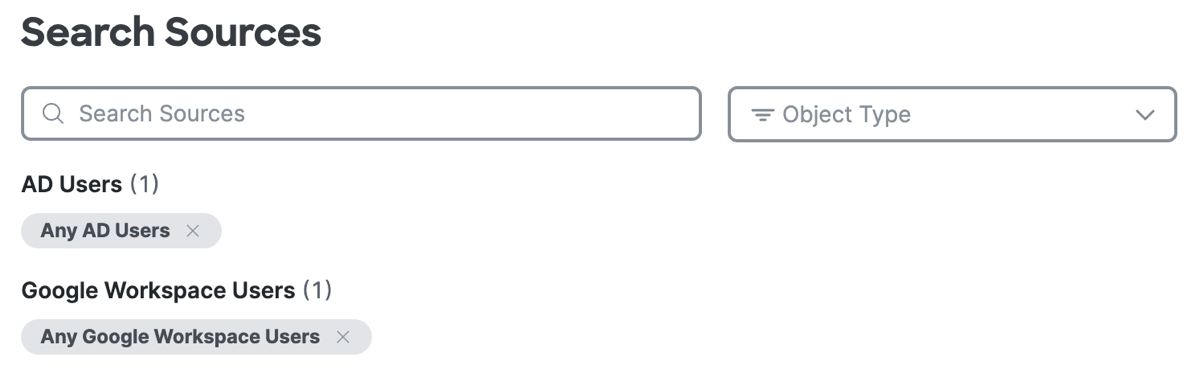
Composite Sources
You can add Sources directly on an internet rule. This option is useful if you need to quickly address a specific issue that arises, for example to immediately block a particular user's access to an internet destination. For more information about configuring sources, see About Configuring Sources for Internet Access Rules.
Important: Secure Access does not support a comma-separated list of wildcard masks.
- Navigate to Secure > Access Policy > Add Rule > Internet Access.
- Navigate to Specify Access and then click on the search bar under From.
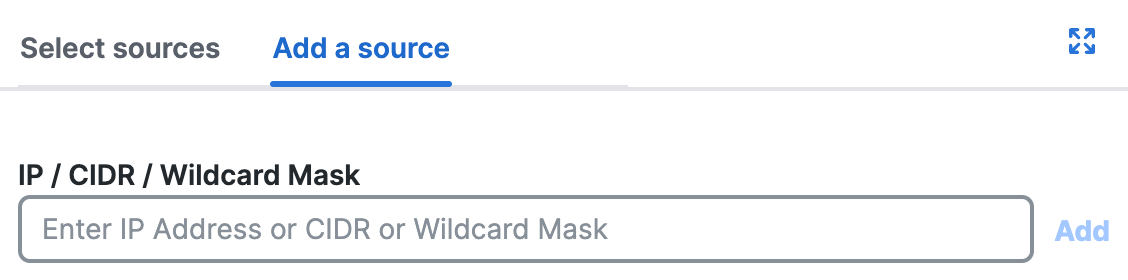
- For Add a source, enter an IPv4 address, CIDR block, or IPv4 address with a wildcard mask.
For example:- IPv4 address—1.2.3.4
- CIDR block—1.2.3.4/24
- Wildcard mask—1.2.3.4/255.255.255.255
For Wildcard Mask, use this format:<IP address>/<Wildcard Mask>. For information about wildcard masks, see Using Wildcard Masks on Internet Rules.
-
Click Add.
-
After you add a composite source, click +More to view the list of sources that you added to the rule.
Click on the X to remove a previously-added source. Click Done when the list of sources is complete.
Pre-Configured Destinations
We recommend that you create reusable components rather than adding destinations directly in a rule. For more information, see Components for Internet Access Rules.
The rule action sets the the destination options that are available on the rule. Usually you will select destinations that you or others have previously configured.
Note: The arrows out icon opens a window to configure the destinations in your rule.
-
Navigate to Secure > Access Policy > Add Rule > Internet Access.
-
Navigate to Specify Access and then click on the search bar under To.
-
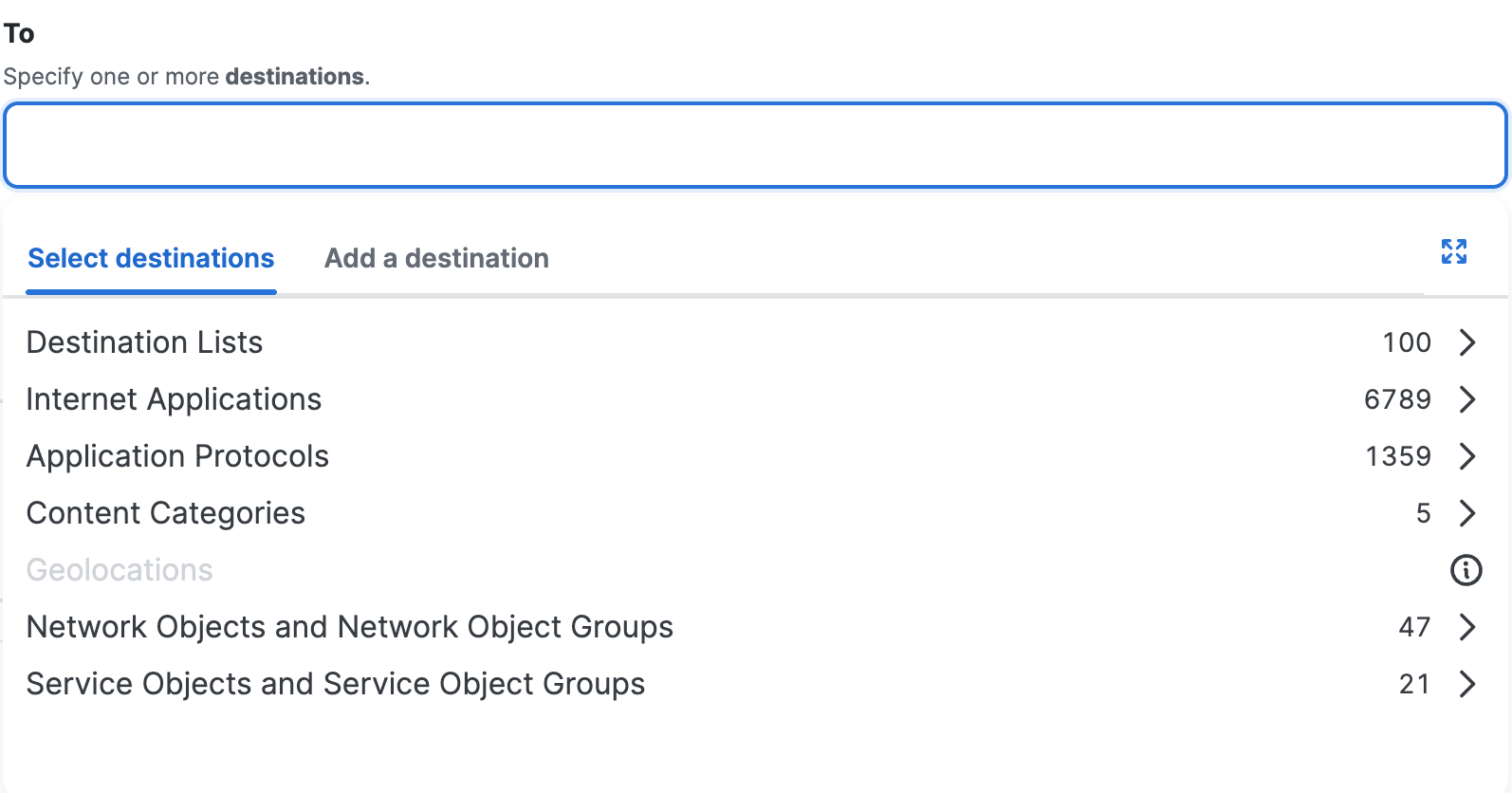
Click Select destinations, click in the white space beside the default value ("Any") and choose the configured destinations in your organization.
-
After you add a destination component, click +More to view the list of destinations that you added to the rule.
Click on the X to remove a previously-added destination. Click Done when the list of destinations is complete.
Composite Destinations
You can add destinations directly on an internet rule. For more information, see About Configuring Destinations for Internet Access Rules.
- Navigate to Secure > Access Policy > Add Rule > Internet Access.
- Navigate to Specify Access and then click on the search bar under To.
- Click Add a destination.
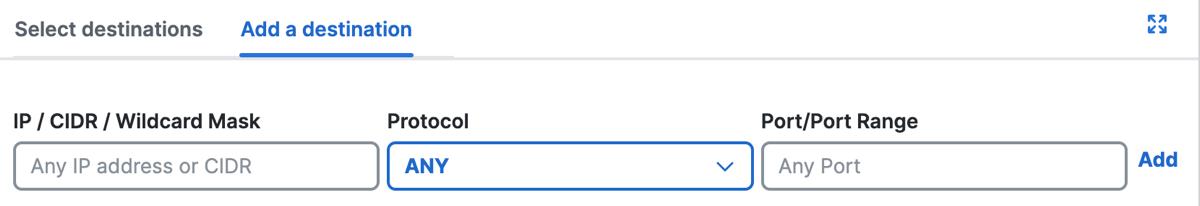
a. For IP, CIDR, or Wildcard Mask, enter an IPv4 address or CIDR block, or IPv4 address with wildcard mask.
For example:- IPv4 address—1.2.3.4
- CIDR block—1.2.3.4/24
- Wildcard mask—1.2.3.4/255.255.255.255
For Wildcard Mask, use the syntax:<IP address>/<Wildcard Mask>. For information about wildcard masks, see Using Wildcard Masks on Internet Rules.
b. For Protocol, choose from one of the supported protocols: ANY, TCP, UDP, or ICMP.
c. For Port/Port Range, enter a port or range of ports separated by a hyphen (-).
d. When you finish adding the composite destination, click Add.
-
After you add a destination component, click +More to view the list of destinations that you added to the rule.
Click on the X to remove a previously-added destination. Click Done when the list of destinations is complete.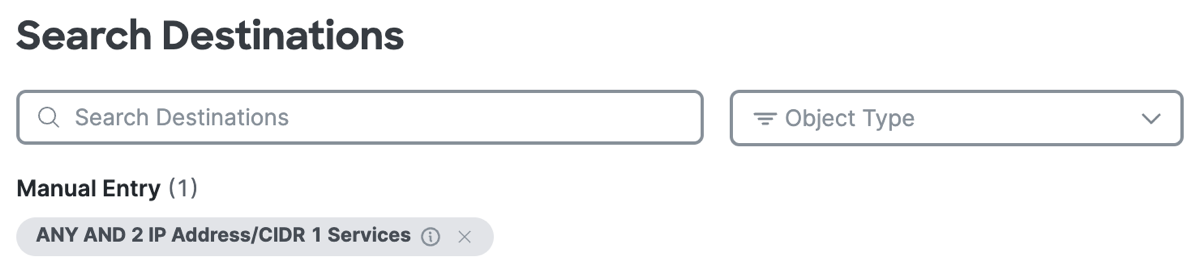
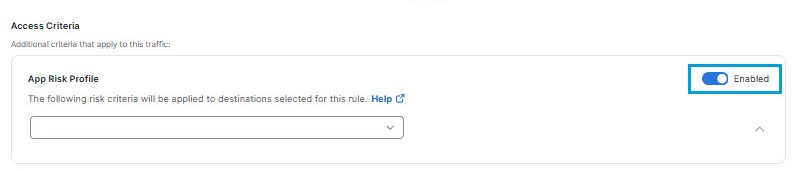
App Risk Profiles
If for Destination you have selected Any Internet Destination or a destination that includes an internet application, you will see the App Risk Profile section. For more information, see App Risk Profile.
Once you create an App Risk profile, you may choose the profile to add the criteria it defines to your rule.
To incorporate an app risk profile in this rule:
- Click the toggle to the right of App Risk Profile to enable the feature.
- From the Select profile drop-down list, click on the name of an app risk profile to apply it to this rule.
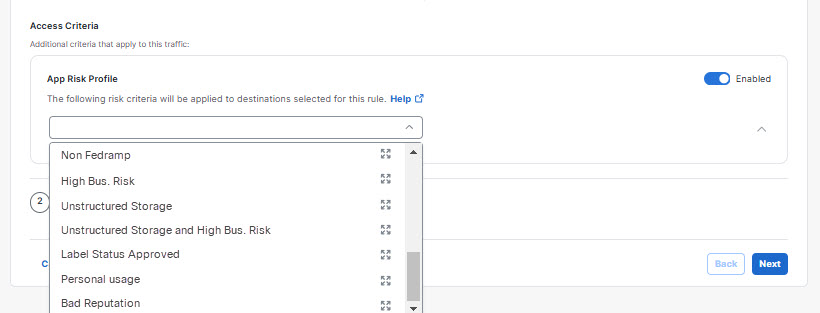
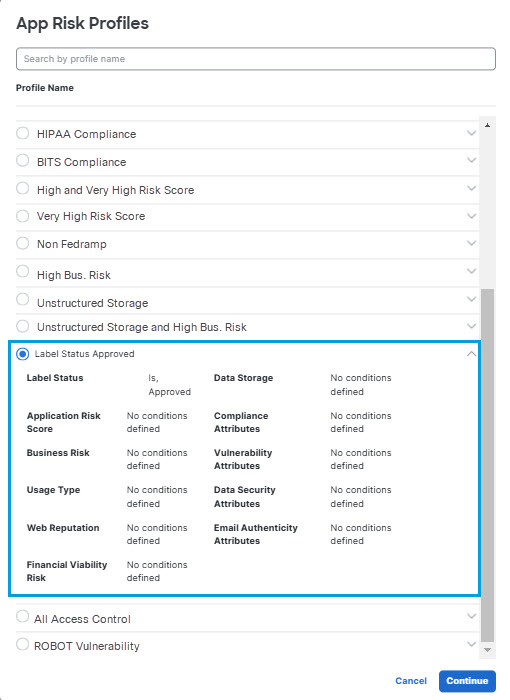
Tip: Alternatively, you may click the expand icon to the right of an app risk profile name to display a dialog showing the risk criteria it defines. Then click Cancel to dismiss the dialog, or click Continue to select the profile.
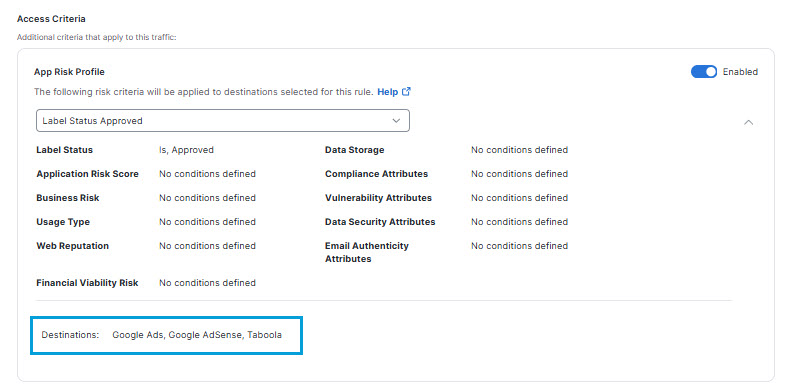
Once you select an app risk profile, a summary of the risk criteria the profile applies to your rule appears. Below it, a list of Destinations that match the profile appears. This list reflects the restriction the app risk profile places on the list of destinations you selected for the rule.
Advanced Application Controls
If configured destinations include Application Lists, Application Categories, or individual applications selected from Application Categories that support the ability to control uploads, downloads, posting, or sharing without entirely blocking access to the application, you will see the Advanced Application Controls section.
For more information, see Advanced Application Controls.
Security Control Options
- Intrusion Prevention (IPS)
- Security Profile
- Tenant Control Profile
- Schedule Enablement Time and Date
- Advanced Security Controls
Intrusion Prevention (IPS)
Choose the IPS profile that includes the threat detection settings that you want applied to traffic that matches this rule. You can also disable intrusion prevention for this rule.
For more information, see Manage IPS Profiles.
Security Profile
- Choose the security profile that includes the web-related settings that you want applied to traffic that matches this rule.
- For all rules, including Block, Warn, and Isolate rules, unless you have good reason not to, choose a security profile that is configured to decrypt the traffic that will hit the rule. Decryption is required to accurately process traffic to most internet destinations.
- Best practice: If decryption is disabled in a security profile, or if decryption is enabled only to show notifications, use that profile only in rules that include only trusted destinations.
- For important information about decryption, see Security Profiles for Internet Access and Manage Traffic Decryption.
- If the rule will block traffic or warn users, you can choose a security profile that specifies the notifications to display to end users.
For more information, see Security Profiles for Internet Access.
Tenant Control Profile
Tenant controls affect access to Microsoft 365, Google G Suite, Slack, and Dropbox.
- For more information, see Manage Tenant Control Profiles.
- For additional requirements, see Use Tenant Controls in Access Rules.
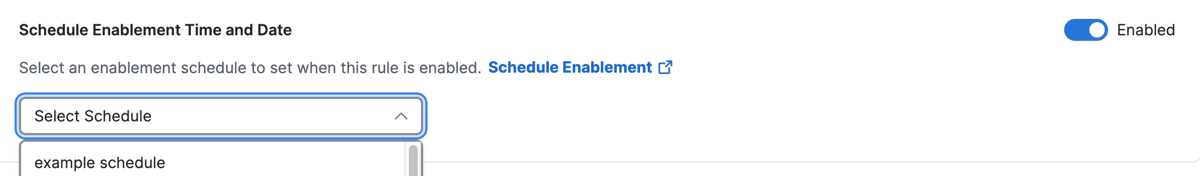
Schedule Enablement Time and Date
Configure the Schedule Enablement Time and Date setting and add a Schedule on the access rule. For more information about Schedules, see Manage Schedules.
-
Navigate to Configure Security, and then navigate to Schedule Enablement Time and Date.

-
Click Enabled to activate a Schedule on the internet access rule.
a. (Optional) To disable a Schedule on the internet access rule, toggle off the Schedule Enablement Time and Date setting. -
Choose the Schedule to enable on the internet access rule.
-
Click Save.
Advanced Security Controls
This section includes options to skip enforcement of certain security features, which you may want to do permanently for trusted destinations or temporarily to troubleshoot an issue.
This section includes the ability to access files without decrypting them (sometimes known as "protected file bypass") and the ability to not enforce certain web security features for this rule.
In general, you should allow access to encrypted files only for trusted destinations, because encrypted files cannot be effectively assessed for threats. By default, access to encrypted files is not enabled.
Disable security features only when you have a specific reason to do so.
Next Steps
Return to Get Started with Internet Access Rules and review additional steps you should take after configuring a rule.
Default Settings for Internet Access Rules< Add an Internet Access Rule > About Configuring Sources in Internet Access Rules
Updated about 1 month ago