View Endpoint Device Details
After an administrator provisions endpoint devices in Cisco Secure Access, you can view details about the devices including information about the access rules that apply to the endpoint devices.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
- An Active Directory integration with Cisco AD Connector version 1.14.4 or newer.
For more information, see Manage Active Directory Integration, Connect Active Directory to Secure Access, and Configure Updates on AD Connectors.
Procedure
View provisioned endpoint devices in Secure Access.
View Details for Endpoint Devices
-
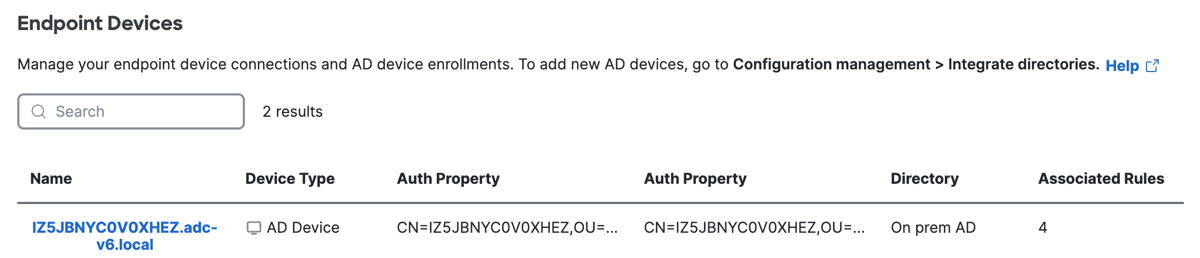
Navigate to Connect > Users, Groups, and Endpoint Devices, and then click Endpoint Devices.
Secure Access lists the devices provisioned in the organization.- Name—The AD display name of the device.
- Device Type—The type of identity provider (IdP) integration that provisioned the device.
Secure Access supports the AD Device type only. - Auth Property—The value of the property used to authenticate the device in Secure Access.
- Directory—The name of the Active Directory IdP.
- Associated Rules—The number of access rules that apply to the device.
-
Navigate to an endpoint device.
View a Configured AD Device
Click a device name to view the details about the device.
- Navigate to Connect > Users, Groups, and Endpoint Devices, and then click Endpoint Devices.
- Navigate to an endpoint device, and then click the name of the device.
General
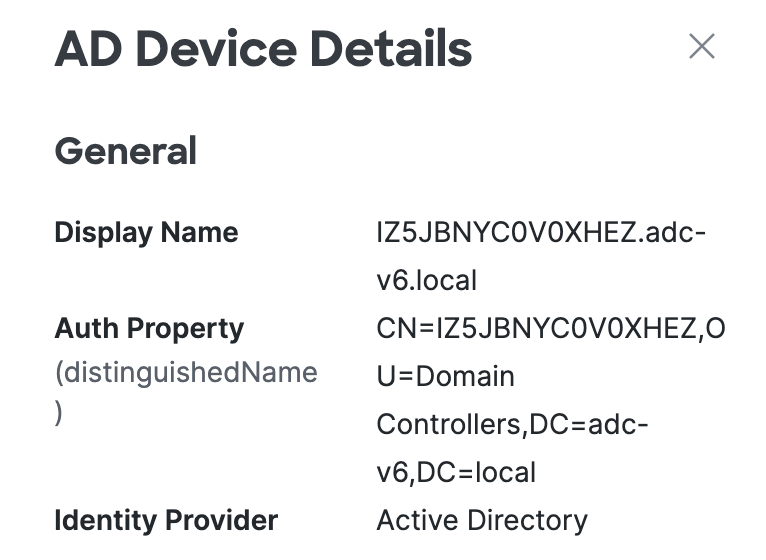
View the general properties for the endpoint device.
-
Display Name—The AD display name of the device.
-
Auth Property—The name and value of the property that Secure Access uses to authenticate the device.
-
Identity Provider—The name of the identity provider that manages the user device.
Associated Rules
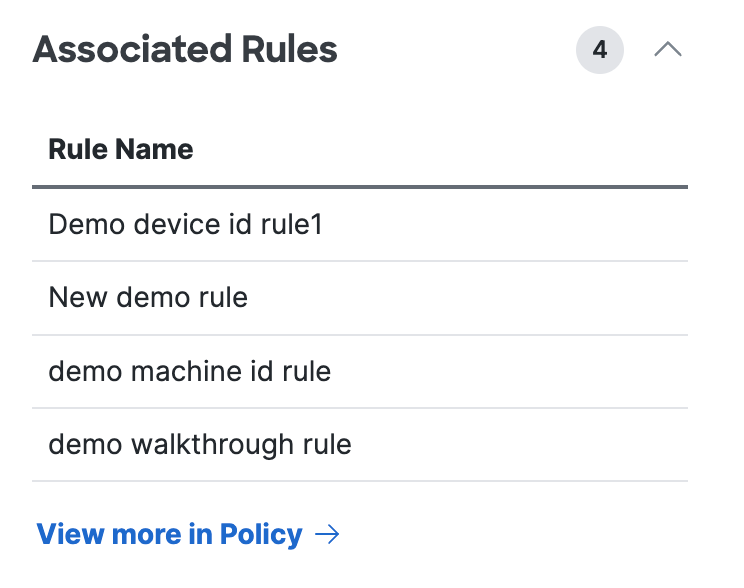
View the information about the access rules that apply to the endpoint device.
-
The number of access rules that apply to the endpoint device.
-
Rule Name—The name of the access rules that apply to the endpoint device.
- Click View more in Policy to navigate to the Access Policy in Secure Access.
View Group and Organizational Unit Details < View Endpoint Device Details > Unenroll Devices for Client-Based Zero Trust
Updated 3 months ago
