Authenticate Device Identity with Active Directory
Cisco Secure Access supports the integration of users, groups, and endpoint devices through various identity providers (IdPs). Once integrated with Secure Access, you can protect and monitor the connections for the users and devices to internet and private destinations by configuring Access rules in the organization's policy.
Important
We recommend you use certificate-based authentication to register device identities with Active Directory as described in this topic. The method to associate machine tunnel and user identity via the manual upload of a CSV file is scheduled to be phased out.
In a future upgrade, Secure Access will introduce an API to upload the machine tunnel identity to automate identity provisioning.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- Endpoint device integration requires devices provisioned by an on-premise Active Directory domain controller (DC) and Cisco AD Connector version 1.14.4 or newer. For more information, see Connect Active Directory to Secure Access and Configure Updates on AD Connectors .
- A configured machine tunnel applied to a VPN profile. For more information, see Manage Machine Tunnels.
- Important: Make a note of the primary attribute for Active Directory certificate-based authentication. For more information, see Authentication for Machine Certificate.
Procedure
The following guidelines explain how to manage your endpoint device connections and AD device enrollments.
Step 1: Configure Active Directory Endpoint Device Management
The Active Directory integration in Secure Access includes the option to provision endpoint devices from an on-premise Active Directory domain controller (DC).
- Navigate to Connect > Users, Groups, and Endpoint Devices, and click Configuration management.
- On the Configurations tab, navigate to Directories, and then expand Active Directory.
Download the Active Directory Components
- For Active Directory Connector, click Download.
- For Windows Configuration Script for Domain Controller, click Download.
Edit the Active Directory Connector Auto-Upgrades
- For more information, see Configure Updates on AD Connectors.
View Active Directory Components
- For more information, see View AD Components in Secure Access.
Manage Sites for AD Components
- For more information, see Manage Sites for AD Components.
Delete Active Directory Integration
- For more information, see Delete AD Components.
Step 2: Authenticate Active Directory Devices
Configure your Active Directory integration to provision your endpoint device enrollments into Secure Access. The integration will save your configuration changes immediately. For more information, see AD Connector Communication Flow and Troubleshooting and View AD Components in Secure Access.
- Check the box at the bottom of your Active Directory integration menu to Use a specified property to Authenticate Active Directory Devices.
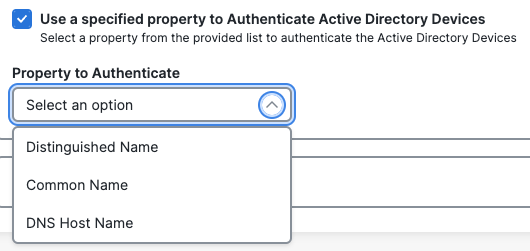
- Select a Property to Authenticate from the list of Active Directory machine attributes for certificate-based authentication. Secure Access supports the Distinguished Name, Common Name, and DNS Host Name attributes. For more information see, Manage Machine Tunnels.
When selecting the Property to Authenticate option, we recommend:- For the computer names in the FQDN format, choose DNS Host Name.
- For the computer name in the short-format, choose Common Name.
- After making changes to the AD integration, restart the AD Connector to trigger a full synchronization of AD Users, Groups, and Endpoint Devices. For more information, see Restart the Active Directory Connector.
Step 3: Use Active Directory Devices as Sources in Access Rules
Secure Access has a single Access policy, which consists of policy rules and settings. Your private access and internet policy rules and the default policy rules control the access and security of your resources and protect the traffic in your organization.
Secure Access supports configuring security controls for sources and destinations (resources) on private and internet access rules. Once authenticated in Active Directory, user devices are available as sources in private access and internet access rules. You can select all endpoint devices in the organization, all existing and future AD devices, or individual AD devices.
View Endpoint Device Details in Secure Access
After an administrator provisions endpoint devices in Cisco Secure Access, you can view details about the devices and identify the access rules that are applied to these identities.
- Navigate to Connect > Users, Groups, and Endpoint Devices and click Endpoint Devices.
Secure Access lists the devices provisioned in the organization. - See View Endpoint Device Details for complete information.
Machine Tunnel - What to do Next<Authenticate Device Identity with Active Directory> Manage Application-Based Remote Access VPN (Per App VPN)
Updated 3 months ago
