Deploy VAs in Google Cloud Platform
Deploy Cisco Secure Access Virtual Appliances (VAs) in Google Cloud Platform.
Note: You must deploy at least two Virtual Appliances (VAs) in a Secure Access Site. It is critical that these VAs are not cloned or copied in any way. Configure and set up each VA manually.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- For information about the network requirements for deploying VAs, see Prerequisites for Virtual Appliances.
- If you are using the VA on Google Cloud Platform (GCP) as a DNS server for your on-premise endpoints, then DNS traffic from these endpoints should not traverse through a Network Address Translation (NAT) device en route to the VA. The VA should receive DNS packets with the source IP as the internal IP of the endpoints. A Google Cloud Interconnect or dedicated MPLS or site-to-site VPN connection from your on-premise environment to GCP meets this requirement.
- A Linux system with the qemu-utils package installed, on which you can run qemu-img and tar commands.
- Only VAs running version 2.6 or above can be deployed in GCP.
Configure Authentication for the Virtual Appliances
Before you can download the Virtual Appliance images in Secure Access, you must configure your Secure Access API keys for the Virtual Appliances in your organization. Secure Access enables the Download Components button only after the API keys for the VAs are configured. For more information, see Configure Authentication for Virtual Appliances.
Procedure
- Step 1 – Prepare the Virtual Appliance Instance Template on GCP. This is a one time task.
- Step 2 - Launch the Virtual Appliance on Google Cloud Platform. Perform this task for each VA after you have performed the one-time task of preparing the VA image.
Step 1 – Prepare the Virtual Appliance Instance Template on GCP
Note: This is a one-time task to create an Instance Template that can be used to launch multiple virtual appliances in GCP.
a. Navigate to Deployments > Configuration > Sites and Active Directory and click Download Components.
b. Click Download for VA for Hyper-V.
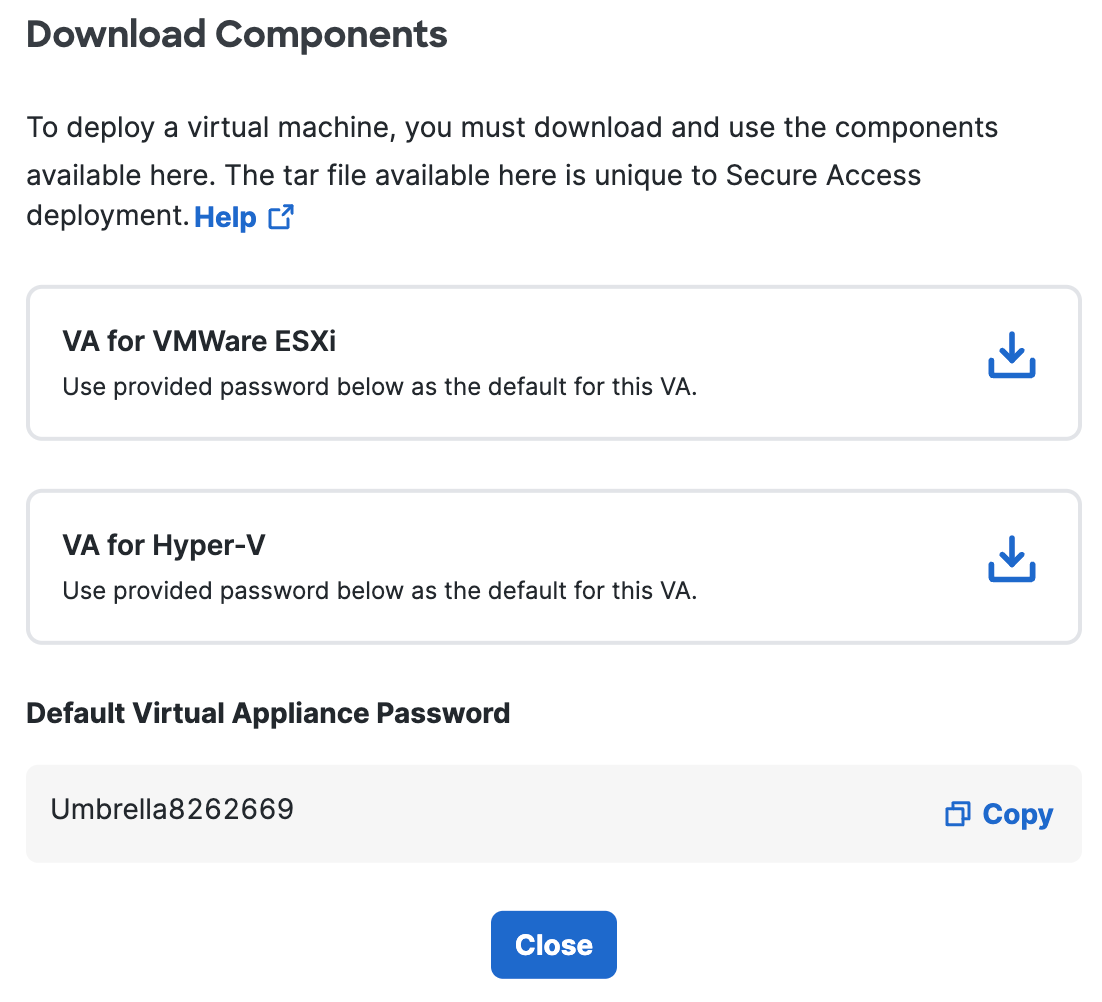
Secure Access generates and downloads a .tar file unique to your deployment.
This .tar file includes:
- .zip file containing the virtual hard disks that need to be deployed on Google Cloud Platform
- Signature file
- Cisco public certificate to validate the signature
- README file
c. Extract the contents of the tar file using the command tar –xvf <.
To verify the integrity of the downloaded file, validate the signature by following the instructions provided in the readme file. When successful, you should see a message saying “Verified OK."
d. Extract the .zip file. The .zip file contains two folders—Virtual Hard Disks and Virtual Machines—and a config file.
e. Use the qemu-img convert commands to convert each of the VHD files to RAW format and resize them to a multiple of 1 GB.
qemu-img convert -f vpc -O raw forwarder-va.vhd forwarder-va.raw
qemu-img resize forwarder-va.raw -f raw 7G
qemu-img convert -f raw -O raw dynamic.vhd dynamic.raw
qemu-img resize dynamic.raw -f raw 1G
f. Tar each raw file.
Note: GCP requires that each file be renamed as disk.raw before you tar it. GCP also requires tar to use the oldgnu format.
mv forwarder-va.raw disk.raw
tar --format=oldgnu -Sczf forwarder-va.tar.gz disk.raw
mv disk.raw forwarder-va.raw
mv dynamic.raw disk.raw
tar --format=oldgnu -Sczf dynamic.tar.gz disk.raw
mv disk.raw dynamic.raw
g. Create a bucket in GCP Storage Engine or use an existing bucket and then upload both the forwarder-va.tar.gz and dynamic.tar.gz files to this bucket.
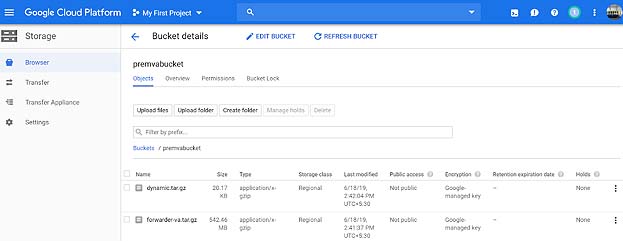
h. Create two images in Google Compute Engine: one with source as the forwarder-va.tar.gz file and the other with source as the dynamic.tar.gz file.
Each image is created with roughly the same size as its respective .tar.gz file (7 GB or 1 GB).
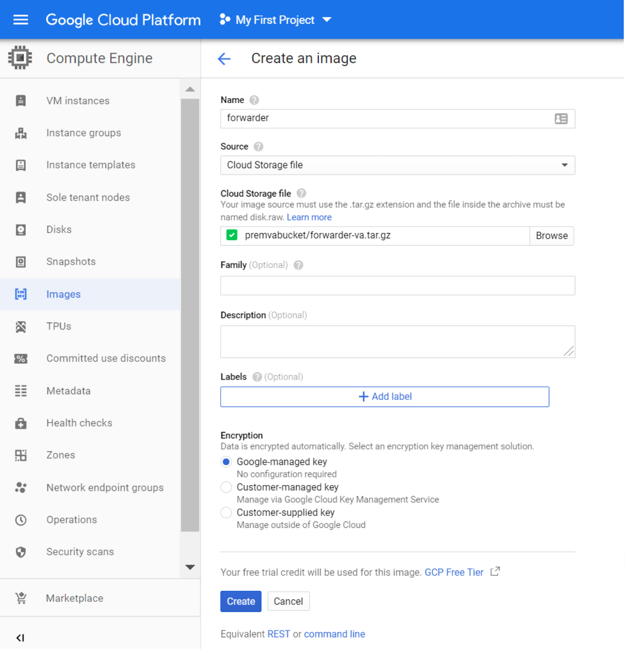
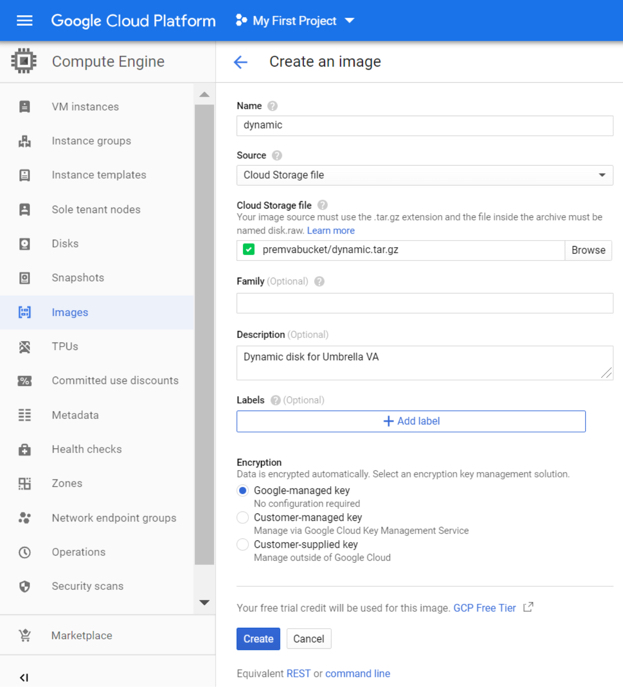
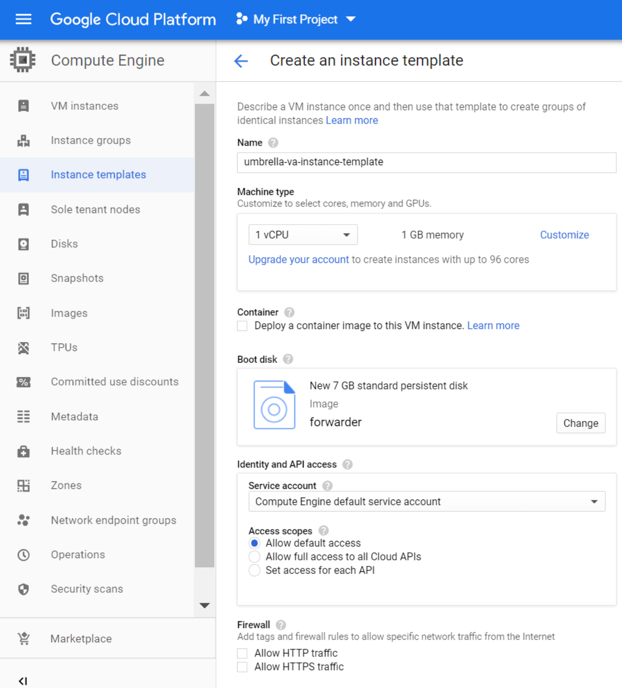
i. Create an Instance Template in the Google Compute Engine using the forwarder image as the boot image and the dynamic image attached as a data disk.
Choose a machine type with at least 1 vCPU and 1 GB memory.
To select the ‘forwarder’ image as the boot disk, choose Change on the boot disk, and then choose the forwarder image from the Custom Images category.
Note: Do not click Create.
j. Click Disks, Add new disk to attach the dynamic disk to the instance template.
You must create a new disk with the source as the ‘dynamic’ image you created earlier. Failure to do so results in your VA not registering with Umbrella.
Note: Google Cloud does not allow you to create a disk of size less than 10 GB from the dynamic image.
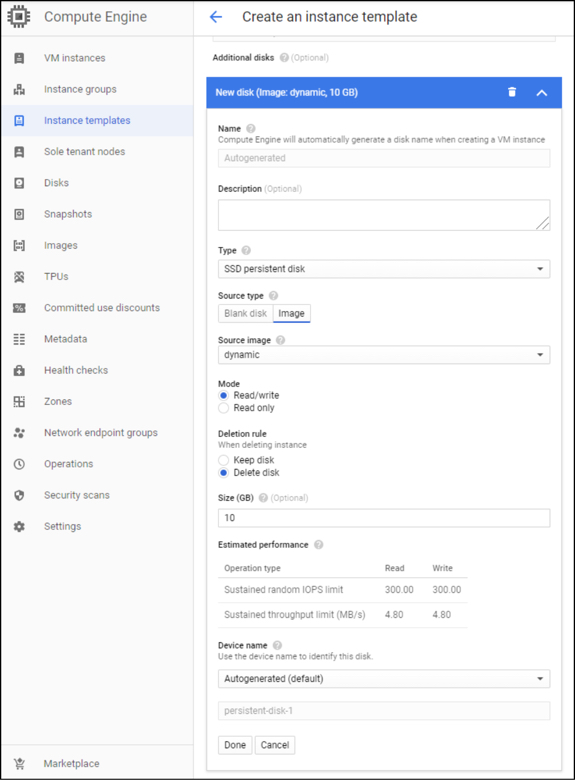
k. After you have added the new disk created from the dynamic image, you can click on Create to create the VA Instance template.
l. Once the VA Instance template is created, use this image to launch multiple VAs. For more information, see Step 2. Launch the Virtual Appliance on Google Cloud Platform.
Step 2 – Launch the Virtual Appliance on Google Cloud Platform
Note: Before performing this task, you must complete the one-time task of preparing the virtual appliance instance template.
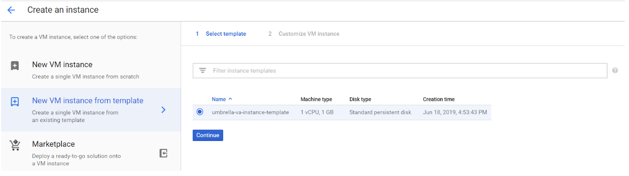
a. Create VA instances based on the template.
The VA will automatically pull a DHCP IP and register to Secure Access with this IP address.
Note: Specifying a public IP address for the VA is a security risk and is not a supported configuration.
b. In Secure Access, navigate to Connectors > DNS Forwarders.
You should see the VA listed here with the dynamic IP address as its name. You can now configure the VA. For information about configuring VAs, see Configure Virtual Appliances.
Deploy VAs in Amazon Web Services < Deploy VAs in Google Cloud Platform > Deploy VAs in KVM
Updated 2 months ago
