Third-Party Apps Report
The Third-Party Apps report lists third-party cloud applications that have been authorized to access sanctioned tenant applications. This report provides visibility to the risks to which your system is exposed by third-party app authorizations. From this report admin users can also block or allow access to third-party applications, overriding all existing authorizations and preventing users from authorizing the app in the future.
Currently the report presents information only about third-party applications authorized through Microsoft 365 tenants and Google Drive tenants.
- For Microsoft 365 tenants, you must authorize the tenant application for third-party access detection. For more information, see Enable Cloud Access Security Broker Protection for Microsoft 365 Tenants. Third-Party Apps discovery for Microsoft 365 tenants is aggregated and processed on an hourly basis.
- For Google Drive tenants, you must authorize the tenant application for third-party access detection. For more information, see Enable Cloud Access Security Broker Features for Google Drive. In the case where the Secure Access administrator has blocked access from third-party applications, Secure Access prevents users from authorizing third-party apps by scanning for access granted to third-party applications every 7 minutes. This is necessary because Google Drive does not allow third-party access to be permanently blocked using an API; the frequent scans enable Secure Access to detect and revoke new third-party authorizations. A Google Drive administrator can override an application's authorization manually through the Google Drive interface and permanently block access to any third-party application.
Table of Contents
- Prerequisites
- View the Third-Party Apps Report
- Search the Third-Party Apps Report
- Export the Third-Party Apps Report
Prerequisites
- Viewing the report requires a minimum user role of Read-Only. To use the block/unblock override feature, you must have the Admin user role. For more information, see Manage Accounts.
View the Third-Party Apps Report
- Navigate to Monitor > Reports > Third-Party Apps.
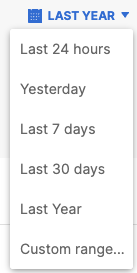
- Choose a time frame of application detection events. You can view the results for the last 24 hours, Yesterday, Last 7 Days, Last 30 Days, the Last Year (default), or a Custom range.
- View the following columns for information on third-party application access events.
- Applications: The names of third-party applications that users have authorized through the tenant application listed under the Source column. For applications whose names appear as links, Secure Access can provide additional information; click the link for an app name to view app details and traffic data for the last 90 days. See View App Details for more information.
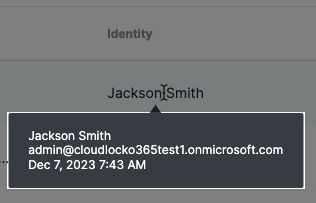
- Identity: The names of users that have accessed the third-party applications. Hover over a name to see the email address for the user and the date and time of the access event.
- Tenant Name: The name of the tenant from which authorization originated. (See Manage Cloud Malware Protection for information about authenticating tenant applications.)
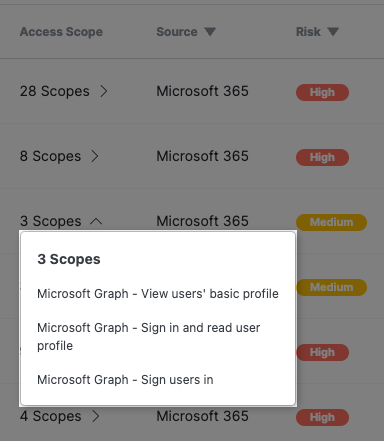
- Access Scope: The number of access permission scopes granted to the third-party application. Click on a value in the Access Scope column to see the scopes listed by name.
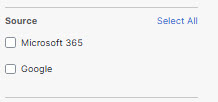
- Source: The tenant application from which authorization originated. The report presents information about third-party applications authorized through Microsoft 365 or Google tenants. For more information, see Enable Cloud Access Security Broker Protection for Microsoft 365 Tenants or Enable Cloud Malware Protection for Google Drive. You can filter the report results by values in this column using the filter selections on the left side of the screen.
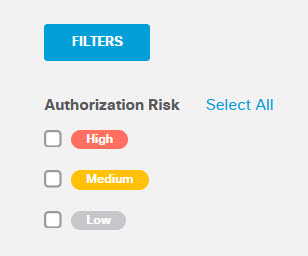
- Authorization Risk: The risk scope Umbrella has calculated for the third-party application, based on the access scopes granted by the user that authorized the application to access an application tenant. The possible values are Low, Medium, and High. You can filter the report results by values in this column using the filter selections on the left side of the screen.
- App Risk: The overall weighted risk score assigned to the app. This could be calculated by Secure Access (based on Business risk, Usage risk, Vendor compliance, and Community risk (if available)) or assigned by you. The possible values are Very Low, Low, Medium, High, and Very High.
- Detected: The time and date when Secure Access detected the access event.
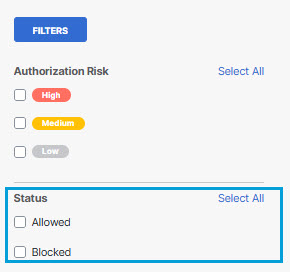
- Status
Block/Allow status for the third-party application:
- Blocked - The system has blocked users from granting access to the application via sanctioned tenant. (Overriding the access granted by a tenant application.)
- Failed to Block - The system has attempted to block users from granting access to the application via sanctioned tenant, but the block attempt failed. Retry the block action; if it fails again, check that your tenant authentication is active. (You may need to re-authenticate.) If you are still unable to block the application, contact Support.
- Allowed - The system allows users to grant access to the application via sanctioned tenant.
- In progress - A block or unblock action is in progress. (The action in progress will appear dimmed in the Permissions column.)
You can filter the report results by the values Allowed and Blocked in this column using the filter selections on the left side of the screen.
- Permissions: This column offers administrators the ability to override the tenant access granted to third-party apps by another user. The possible actions are:
- Block - Block the third-party applications from accessing the application via a sanctioned tenant, overriding access granted by other users.
- Unblock - Allow the third-party application to access the application via a sanctioned tenant.
The options in this column will appear dimmed if they are not available for any of the following reasons:
- The user does not have admin privilege.
- A block or unblock action is in progress.
- A block action has failed
- Sort columns by Tenant Name, Applications, Source, Risk, or Detected.
- Click the Refresh button at the top of the report to update results.
Search the Third-Party Apps Report
- Use the search bar above the report results to search by a specific application, identity, or permission scope.

Select a search result to apply it as a filter to the report columns Application, Identity, or Access Scope.
- Click Advanced to perform a targeted search.
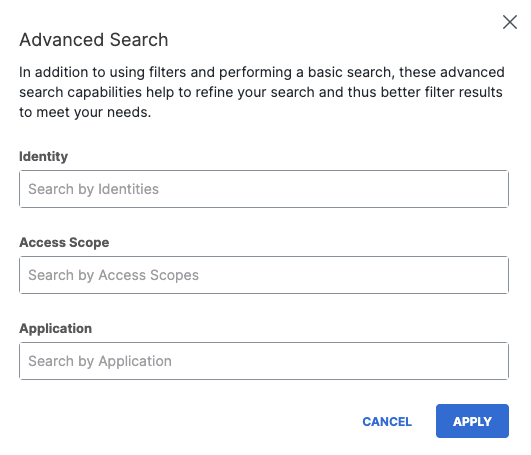
Note:
- There is a three-character minimum for search terms.
- The search feature does not support wildcards.
- The system does not search detail information from the Identity column.
- Search results reflect matches found for all third-party applications that users have authorized. Results are not restricted by the time frame or filters applied to the report.
Export the Third-Party Apps Report
Click Download CSV at the top right of the report to export results in CSV format.
- The export will include results of the time frame and filters applied to the report.
- The file name format will be Third_Party_Apps_YYYY-MM-DDThh_mm_ss.sssZ.csv
Where:
- YYYY-MM-DD represents the date of the download.
- hh_mm_ss.sss represents the time of the download.
Category Details < Third-Party Apps Report > View App Details
Updated 6 months ago
