Enable File Inspection
To inspect files for threats, enable the file inspection features in security profiles for internet and private access, then assign the security profiles to internet and private access rules.
File Inspection uses multiple features to evaluate for malicious files. For details, see Manage File Inspection and Analysis.
Once inspections are complete, a file is either delivered to the end user or the connection is terminated and the user is shown a block page.
Once you have enabled File Inspection, to monitor and review Umbrella's inspection activities, use the Security Activity and Activity Search reports.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- Determine which options you want to enable. For details, see Manage File Inspection.
If you will enable file analysis: Before you enable that feature, see important caveats in Enable File Analysis by Secure Malware Analytics.
By default, File Inspection is enabled and file analysis is not.
You must first enable File Inspection before you can enable file analysis. - Decryption must be enabled. See Manage Traffic Decryption.
- Certificates are required to decrypt traffic and detect files, and to display block notifications for files blocked in internet traffic.
- For internet traffic, see Certificates for Internet Decryption.
- For traffic to private resources, configure certificates in each private resource or see Manage Certificates for Private Resource Decryption.
Procedure
- Navigate to Secure > Security Profiles.
- Click +Add Profile or expand an existing profile.
- In the Security and Acceptable Use Controls section, for File Inspection, click Edit.
- Enable File Inspection if it is not already enabled:
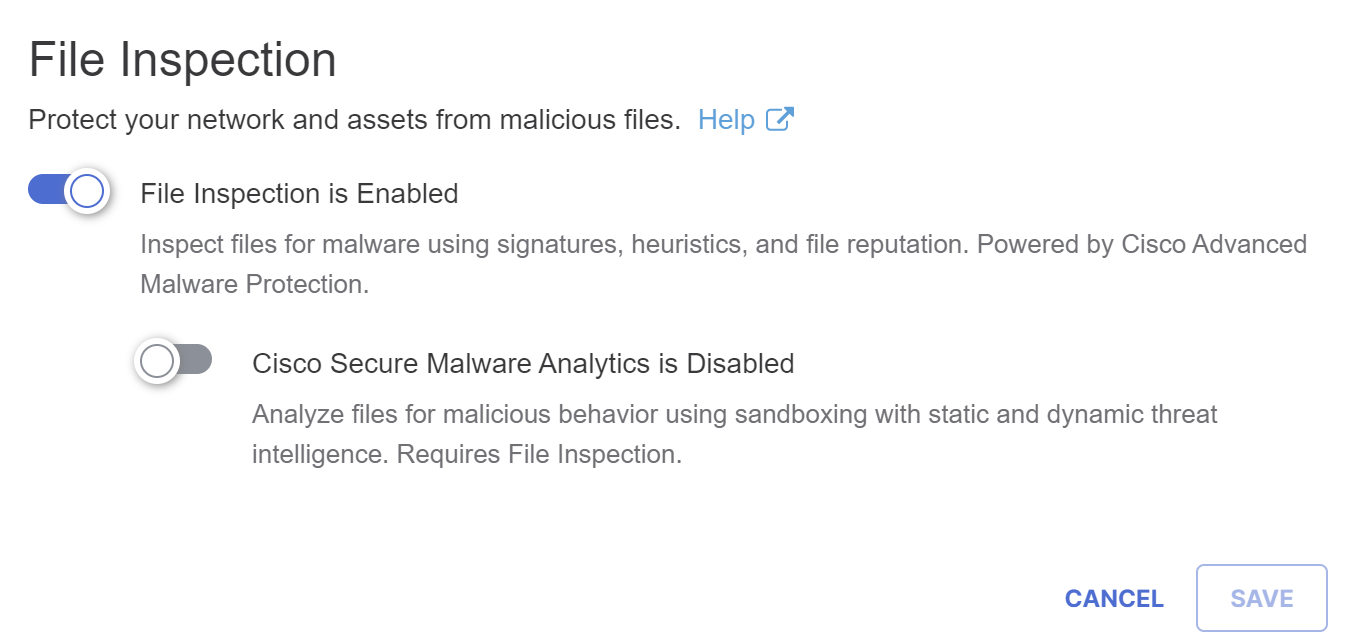
- Click Save.
- If you will enable file analysis using Cisco Secure Malware Analytics, see important information and follow the procedure in Enable File Analysis by Cisco Secure Malware Analytics.
- For security profiles for internet access: In the same profile, ensure that Decryption is enabled.
- For security profiles for private access: Ensure that destinations configured in the rule are configured as Private Resources with decryption enabled.
- Choose a security profile that has file inspection enabled when you configure access rules.
Manage File Inspection < Enable File Inspection > Enable File Analysis by Cisco Secure Malware Analytics
Updated 11 months ago
