Allow SSH and RDP Access to Private Resources
Secure Access Packages and Feature Availability
Not all of the features described here are available to all Secure Access packages. Information about your current package is listed on the Admin > Licensing page. For more information, see Determine Your Current Package. If you encounter a feature here that you do not have access to, contact your sales representative for more information about your current package. See also, Cisco Secure Access Packages
You can allow Zero Trust Access to private resources using SSH and Microsoft's Remote Desktop Protocol (RDP).
Table of Contents
Browser-Based Zero Trust Access
Configuration overview: Browser-based zero trust access using SSH or RDP
To allow clientless browser-based Zero Trust Access to private resources using SSH or RDP:
- If you are using older SSH servers, see Details: Supported options for SSH.
- Configure your private resource:
- Allow access using the applicable protocol for the internally reachable address. See Add a Private Resource.
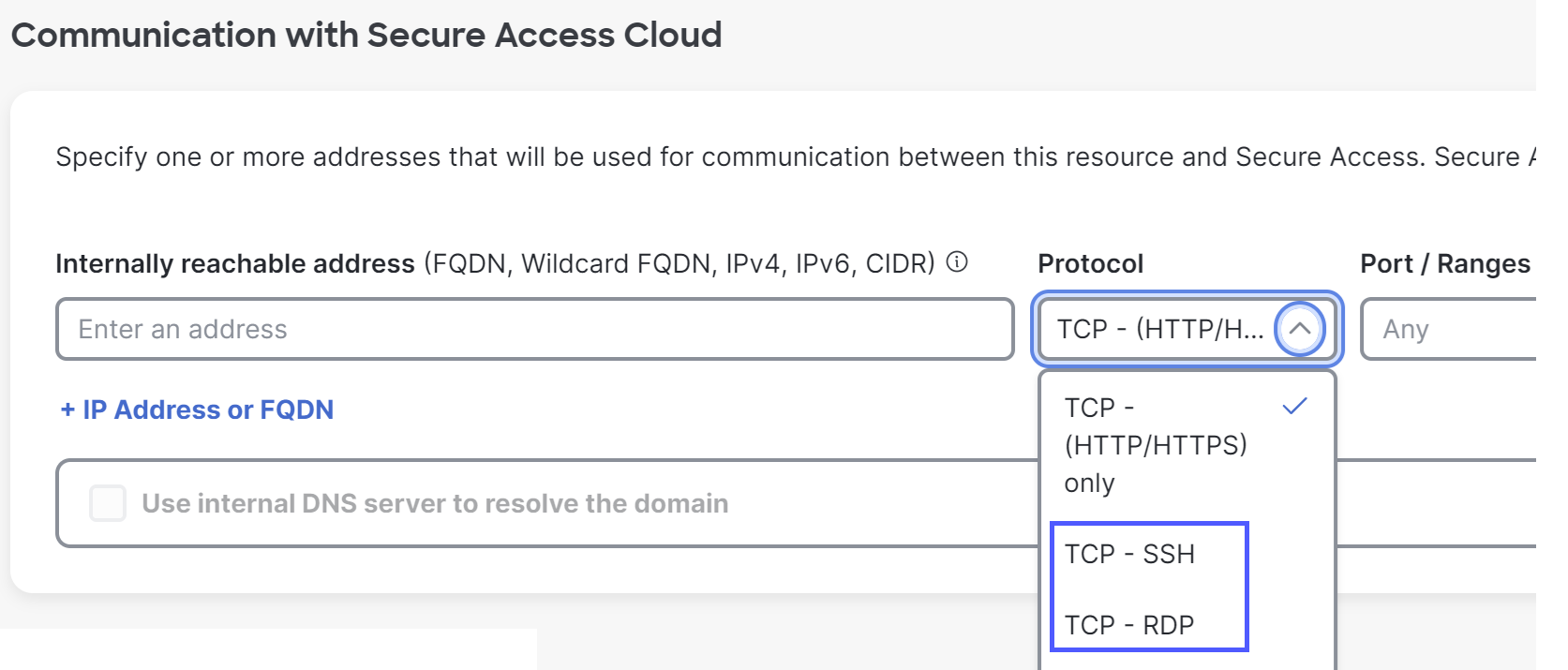
Note: The resource name will appear at the top of your users' SSH or RDP window.
- In the Private Resource, enable Zero-trust connections, then enable and configure browser-based connections.
- Follow the instructions for granting access to private destinations in Get Started With Private Access Rules.
- If your environment has a web proxy or firewall between end user browsers and the Secure Access cloud, you must allow websocket access on port 443 from your users' browsers to Secure Access.
- When you give users the applicable SSH or RDP credentials or private key for the resource, also provide the public URL for browser-based Zero Trust Access that you configured on the Private Resource page. Neither Secure Access nor the browser stores the credentials or private key.
Notes for browser-based SSH and RDP access
- For limits on the number of user sessions, see the Service Connections section in Limitations and Range Limits.
- The user experience will look like this:
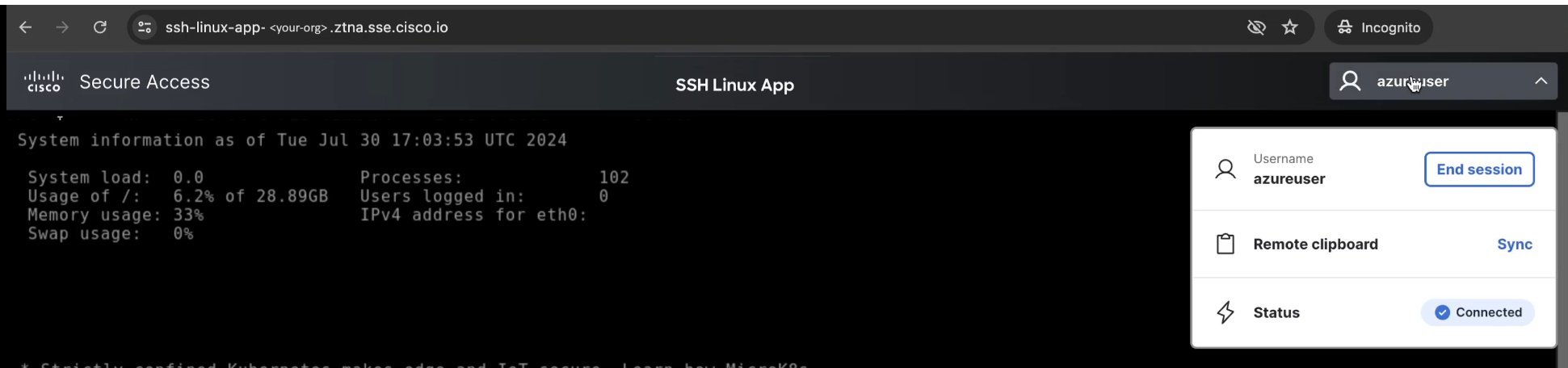
- SSH and RDP users can paste text copied from their local machine by using the remote clipboard feature, shown in the image above. Follow these steps in order for each text string that needs to be copied and pasted:
- Copy text on your local machine.
- Click Sync to the right of the Remote clipboard menu item in the browser-based SSH or RDP session.
- Paste into the remote session.
Note: The Sync button is not necessary when copying from the remote session to your local machine.
- RDP users will not be able to upload files or images.
Supported options for SSH access
Most SSH connections will be successful. If you are using older SSH servers, the following options are supported.
| Key Exchange (KEX) | Symmetric Cipher | Message Authentication Code (MAC) | Server Host Key Algorithm | Compression Schemes | Authentication |
|---|---|---|---|---|---|
| diffie-hellman-group-exchange-sha256 | [email protected] | hmac-sha2-512 | ssh-ed25519 | zlib | password |
| diffie-hellman-group1-sha1 | [email protected] | hmac-sha2-512- [email protected] | ssh-ed25519- cert-v01 @openssh.com | [email protected] | public key |
| diffie-hellman-group14-sha1 | hmac-sha2-256 | hmac-sha2-256 | ecdsa-sha2- nistp521 | none | n/a |
| diffie-hellman-group-exchange-sha1 | [email protected] | [email protected] | ecdsa-sha2-nistp384 | n/a | n/a |
| n/a | hmac-sha1 | hmac-sha1 | ecdsa-sha2-nistp256 | n/a | n/a |
| n/a | hmac-sha1-96 | hmac-sha1-96 | ssh-rsa | n/a | n/a |
| n/a | hmac-md5 | hmac-md5 | ssh-dss | n/a | n/a |
| n/a | hmac-md5-96 | hmac-md5-96 | n/a | n/a | n/a |
| n/a | hmac-ripemd160 ([email protected] ) | hmac-ripemd160 ([email protected] ) | n/a | n/a | n/a |
Client-Based Zero Trust Access
Client-based SSH and RDP access does not require special configurations. No user experience specific to Secure Access is required.
Manage Branch Connections < Allow SSH and RDP Access to Private Resources > Application Portal for Zero Trust Access Browser-Based User Access
Updated 3 months ago
