Rule Defaults: Default Settings for Access Rules
When you create a new access rule, Secure Access configures the rule with the default rule settings unless you select other options in the rule. The rule defaults are a collection of controls for endpoint security posture and security profiles, and the zero trust authentication interval property.
You can modify the default rule settings. For more information, see Edit Rule Defaults and Global Settings.
Important Information About Changing Rule Defaults
If you modify a rule default, all existing rules that are configured to use a particular rule default will change to use the new default.
For example, if you change the default IPS Profile from Balanced Security and Connectivity to Maximum Security, the IPS profile in all existing rules that are configured to use the default IPS Profile will now use the Maximum Security settings for IPS.
Existing rules that are configured to use custom settings are not affected by changing the rule default. To determine whether a rule uses default or custom settings, see About the Access Policy.
Table of Contents
- Zero Trust Access: Endpoint Posture Profiles
- Zero Trust Access: User Authentication Interval
- Intrusion Prevention (IPS)
- Security Profile
- Tenant Control Profile
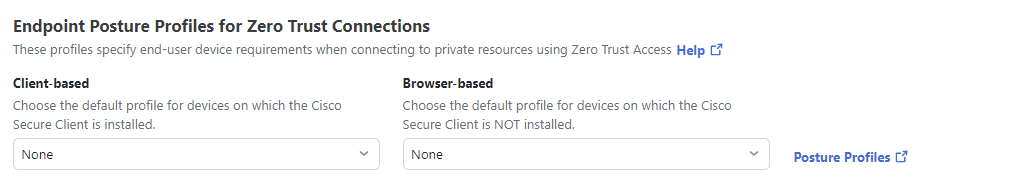
Zero Trust Access: Endpoint Posture Profiles
Client-based and browser-based Zero Trust Access (ZTA) profiles specify end-user device requirements when connecting to private resources using ZTA.
Choose from these types of posture profiles:
- Client-based—Select as the default profile for devices where the Cisco Secure Client is installed.
- Browser-based—Select as the default profile for devices where the Cisco Secure Client is not installed.
For more information about Zero Trust posture profiles, see Manage Zero Trust Access Posture Profiles.
Zero Trust Access: User Authentication Interval
The Zero Trust Access User Authentication Interval is sometimes known as step-up authentication.
For the ZTA user authentication interval, specify the default frequency with which end users must verify their identity, in order to connect to any private resource using client-based zero trust access. When disabled, users are not prompted to re-authenticate to the network.
Note: iOS clients do not support the User Authentication Interval option. The User Authentication Interval must be disabled in access rules that apply to iOS devices.
User Authentication Default Interval Settings
- The default interval is 3 days.
- The minimum value is 1 minute.
For more information, see Network Authentication for Zero Trust Access.
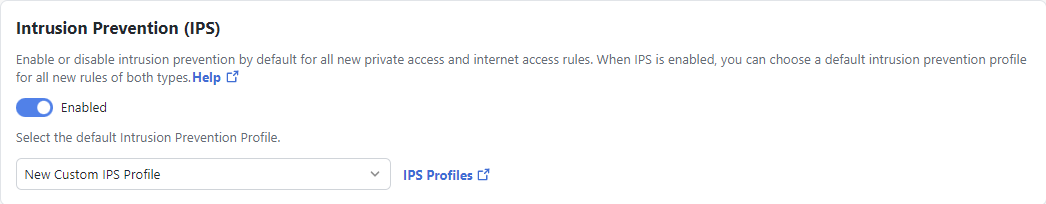
Intrusion Prevention (IPS)
Enable or disable intrusion prevention by default for all new private access and internet access rules. When IPS is enabled, you can choose a default intrusion prevention profile for all new rules of both types. For more information about IPS profiles, see Manage IPS Profiles.
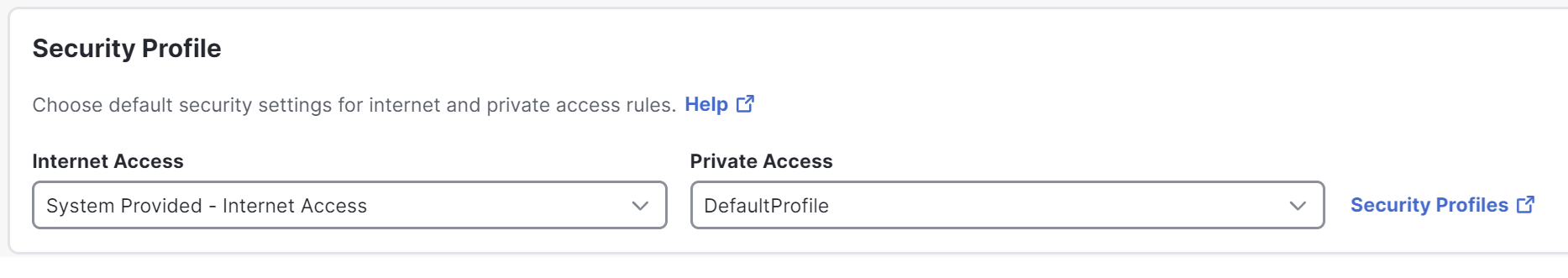
Security Profile
A security profile lets you configure settings that you can use in a rule as a set. Choose a profile to apply to all new access rules of each type (internet and private access). For more information about Security profiles, see Manage Security Profiles.
Tenant Control Profile
Limit access to your organization’s tenant for certain SaaS applications. This setting applies only to internet access rules. For more information about Zero Trust posture profiles, see Manage Tenant Controls.

Edit the Order of the Rules on the Access Policy Page < Rule Defaults: Default Settings for Access Rules > Global Settings for Access Rules
Updated about 1 month ago
