Configure Integrations with OIDC Identity Providers
Cisco Secure Access enables you to connect securely to the internet, web destinations in private and public clouds, your organization's on-premises private resources, and Software as a Service (SaaS) applications. To create more granular access rules and to authenticate users connecting on networks or network tunnels or with Zero Trust Access (ZTA), you can integrate an OpenID Connect (OIDC) identity provider (IdP) with Secure Access.
Secure Access supports OIDC for single sign-on (SSO) authentication of users through the integration with Okta and Microsoft Entra ID.
Once users in your organization are configured to use SSO through an IdP, the IdP manages all authentication requests. A user authenticates to the SSO authentication IdP, automatically signs in to Secure Access, and is authorized to connect to the requested destination.
Table of Contents
- About Using OpenID Connect with Secure Access
- Use Cases – SSO Authentication
- Configure Identity Providers for OIDC Authentication
About Using OpenID Connect with Secure Access
OpenID Connect (OIDC) is an identity protocol that extends the OAuth 2.0 protocol. The OIDC authentication flow describes the authentication of a request for a destination by the user.
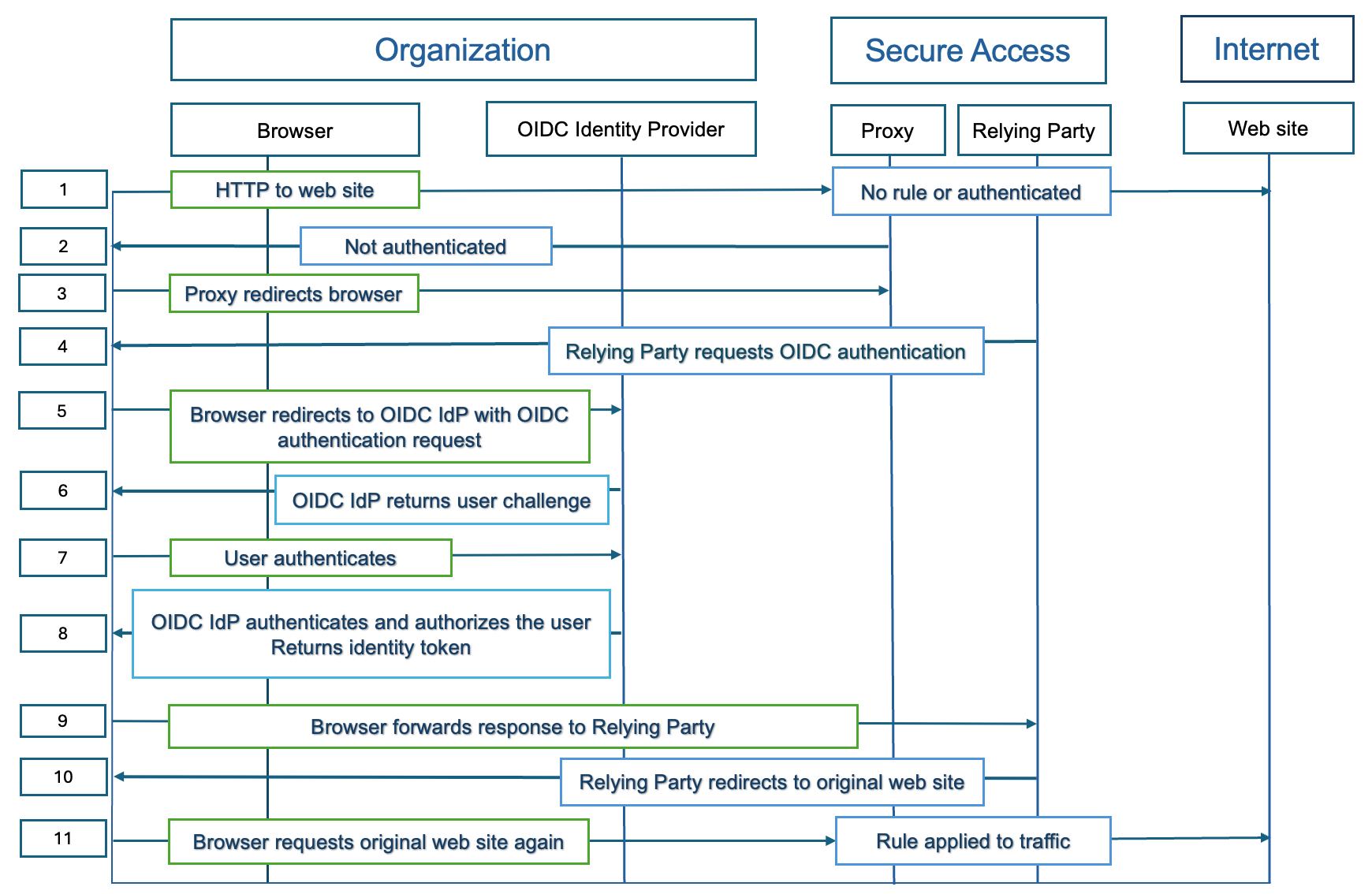
The OIDC authentication flow with Secure Access is described as follows:
-
A user requests a web site. Secure Access (proxy) receives the request and determines if the user is authenticated to get the destination. If the user is not authenticated, the browser redirects the request to the Relying party (Secure Access). The Relying party requests that the OIDC IdP authenticate the user.
-
Then, the OIDC IdP returns a challenge to the user and the user authenticates to the OIDC IdP. If valid, the OIDC IdP returns an identity token to the user. The user's browser forwards the response to the Relying party, and then the Relying party redirects the original request for the web destination to Secure Access.
-
If the rules in the organization's Access policy match the traffic, Secure Access applies the rules and ensures that the connection to the web site is secure.
Use Cases – SSO Authentication
Secure Access supports the OIDC protocol to authenticate users and provide seamless connections to web resources and private resources from user devices.
Secure Internet Access—Networks and Network Tunnels
- Secure web gateway—The Cisco Secure Access Secure Web Gateway (SWG) uses OIDC to authenticate and authorize web requests from user devices sent over networks and network tunnels. Internet traffic is protected by the Secure Access DNS and Web security layers. The Secure Access SWG is not an open proxy. Secure Access must trust the source that forwards web traffic to it, whether the source is a network or network tunnel.
Zero Trust Access with the Cisco Secure Client
- Secure Access Zero Trust Access (ZTA) connections can use OIDC to authenticate and authorize requests to an organization's private resources from a user device where the Cisco Secure Client is deployed.
Zero Trust Access with an Unmanaged Device
- Secure Access Zero Trust Access (ZTA) can use OIDC to authenticate and authorize requests to an organization's private resources from an unmanaged device.
Configure Identity Providers for OIDC Authentication
Follow the procedure in the configuration guides to integrate an SSO authentication IdP for Open ID Connect with Secure Access.
Secure Access Redirect URI
The Secure Access Redirect URI is used when you set up the integration of Secure Access for OIDC in the SSO authentication IdP app.
https://fg.id.sse.cisco.com/gw/auth/oidc/callback
Delete SSO Authentication Profile < Configure Integrations with OIDC Identity Providers > Configure Okta for OpenID Connect
Updated 6 months ago
