Manage Global Settings for Access Rules
In Cisco Secure Access, the Access policy has a Global Settings configuration that affects all rules of the applicable type: internet access rules or private access rules.
Some global settings are intended only for troubleshooting purposes. Change these settings only if you have good reason to do so. For more information, Edit Rule Defaults and Global Settings.
Secure Access Packages and Feature Availability
Not all of the features described here are available to all Secure Access packages. Information about your current package is listed on the Admin > Licensing page. For more information, see Determine Your Current Package. If you encounter a feature here that you do not have access to, contact your sales representative for more information about your current package. See also, Cisco Secure Access Packages
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
Procedure
Change the global settings on the Access policy for the organization.
- Navigate to Secure > Access Policy.
- Click Rule Defaults and Global Settings.
- Click Global Settings.
- Manage the global settings on the Access policy.
- Scroll to the bottom of the page, and then click Save.
Display User Input Field on Warn Pages
This setting applies only for destinations on internet access rules in the Access policy that have enabled the Warn action.
-
Click to enable the display of the user input field on all Warn pages for internet access rules.
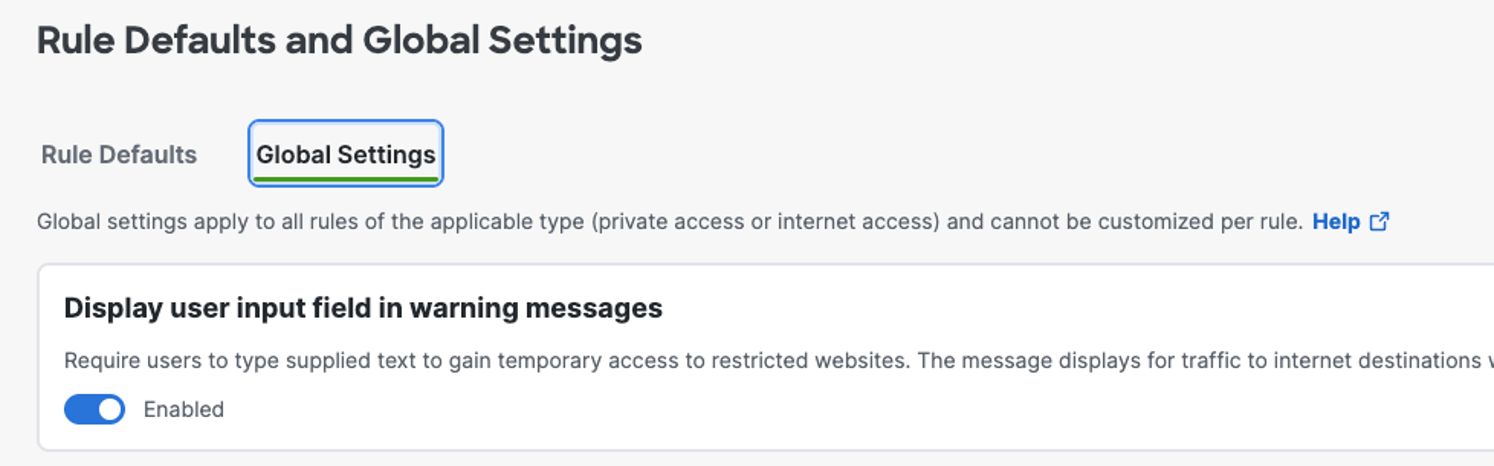
Once enabled, all Warn pages that are displayed by Secure Access have the user input field instead of the link to continue to the warning message.
Note: The Display user input field in warning messages option does not affect the use of the organization's custom Warn pages.
About the Warn Page User Input Field
When Secure Access displays a Warn page with the user input field, the end-user must enter the word Continue to reach the destination. If the user's language is not supported, then use Continue.
The value of the user input field is a case-insensitive string.
Once the user enters Continue, Secure Access enables the Continue button on the Warn page. The user then clicks the Continue button to reach the destination. For more information, see Manage Notification Pages.
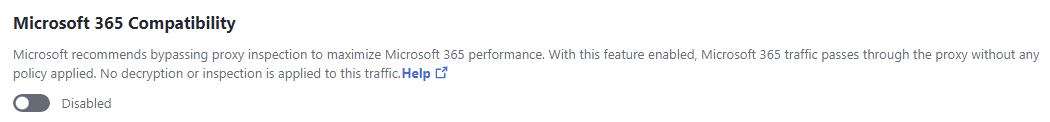
Microsoft 365 Compatibility
This setting applies only to web security features, not to IPS.
The Microsoft 365 Compatibility feature exempts Microsoft 365-related domains, marked as Optimize and Allow in Microsoft's endpoint categories, to bypass inspection and policy enforcement by web security features, allowing traffic to those domains to pass through unaltered. The domains are excluded from HTTPS decryption and content filtering. The Microsoft 365 traffic appears in the Secure Access reports, however, since HTTPS inspection is disabled, traffic is logged only at the host/domain level and does not show the full URL.
Tenant Controls
If you use tenant controls for Microsoft 365, see additional information at Use Tenant Controls in Access Rules.
Limitations
- Microsoft 365 traffic is still sent to Secure Access's web proxy service in all deployment methods (Tunnel, AnyConnect, PAC). To stop this traffic from hitting Secure Access entirely, add manual 'External Domain' entries or route the traffic direct to the internet from your connecting devices.
- File Inspection will no longer apply to this traffic.
- This will not prevent the Microsoft 365 traffic egressing from a Secure Access IP address
- This does not apply to all Microsoft/Microsoft 365 domains. Only those categorized as important for performance by Microsoft.
- This setting allows a number of important Microsoft 365 domains so web security and filtering do not apply to them, and prevents these domains from triggering Secure Access SAML authentication.
Note: MS Intune sync requires "manage.microsoft.com" to be added to the Do Not Decrypt List(s) used in the relevant rules even when Microsoft365 Compatibility is enabled.
For more information, see the official Microsoft documentation.
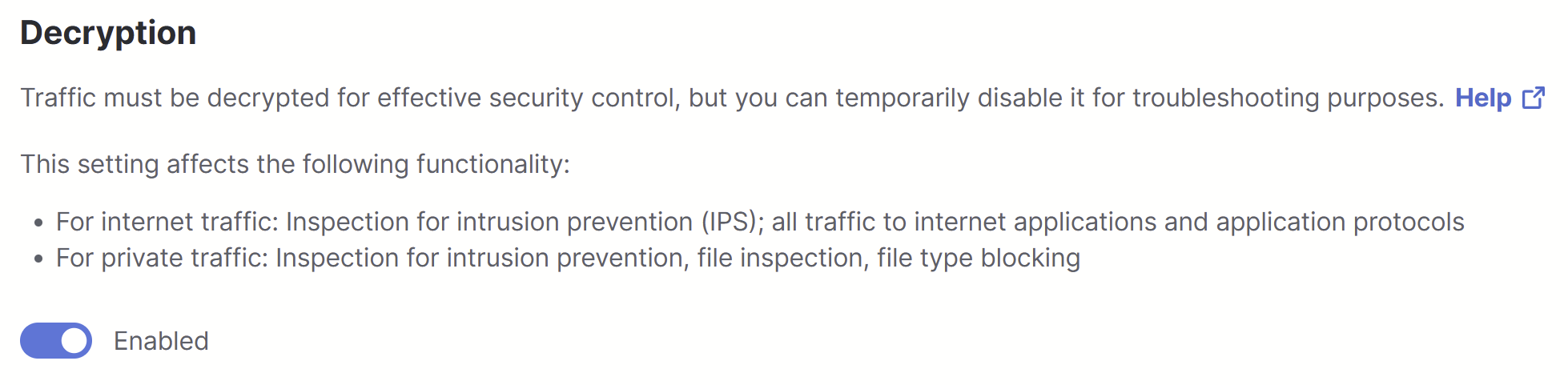
Decryption
Traffic must be decrypted for effective security control, but you can temporarily disable decryption for troubleshooting purposes.
This setting applies to the following functionality:
- For internet destinations: Intrusion prevention (IPS) and all traffic to internet application and application protocol destinations.
- For private resources: Intrusion prevention (IPS), file inspection, and file type blocking
Disabling decryption does not disable affected features, but decreases their effectiveness for encrypted traffic. Traffic that is not encrypted is not affected.
For information about other decryption settings, see Manage Traffic Decryption.
Disable Decryption for Specific Sources
To enable traffic from sources on which you cannot install certificates, such as Internet of Things (IOT) devices, disable decryption for traffic from these sources. This feature applies only to sources in internet access rules.
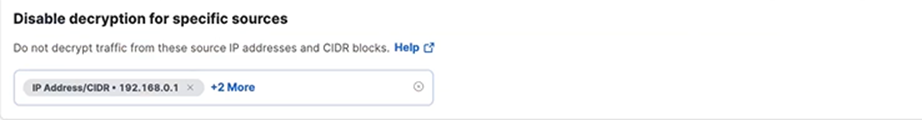
For information about other decryption settings, see Manage Traffic Decryption.
Decryption Logging
You can enable or disable decryption logging globally in Global Settings, for traffic to private resources or internet destinations or both.
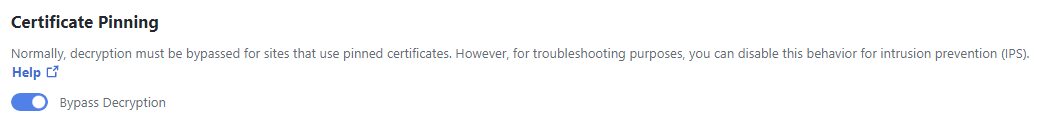
Certificate Pinning
Certificate pinning is an Internet security mechanism which allows applications to resist impersonation against HTTPS servers using mis-issued or otherwise fraudulent digital certificates. However, if this security feature causes problems when users attempt to access destinations that are both essential and trusted, you may bypass this security feature for destinations that use certificate pinning.
Note: Normally, decryption must be bypassed for sites that use pinned certificates. However, for troubleshooting purposes, you can disable this behavior for intrusion prevention (IPS).
Rule Defaults: Default Settings for Access Rules < Manage Global Settings for Access Rules > Edit Rule Defaults and Global Settings
Updated about 1 month ago
