Traffic Steering for Zero Trust Access Client-Based Connections
In Cisco Secure Access, Zero Trust traffic steering rules apply only for Client-based Zero Trust Access (ZTA) connections to internal destinations that are configured as private resources.
When you configure a Private Resource, Secure Access automatically adds an entry for each configured resource address for Client-based ZTA to the Zero Trust Traffic Steering page, in order to direct end-user traffic to the resource.
You can view the traffic steering rules, but in most cases you should not edit the rules on the End User Connectivity > Zero Trust page. For more information, see Best Practices.
Important
If you edit entries that were automatically added to this page when you configured a Private Resource, the traffic steering rules for the resource are not updated when you make future edits to the Private Resource configuration page.
If you change the destination address on the Zero Trust Traffic Steering page, the original Private Resource will not have a traffic steering rule and Client-based ZTA connections to that resource will not occur even if configured in the resource.
Table of Contents
Best Practices
In general, you should not add destinations directly to the Zero Trust traffic steering page. Instead, add a Private Resource. For more information, see Add a Private Resource.
-
The private resource address to edit must be configured as a wildcard fully-qualified domain name (FQDN).
-
You should not edit entries on the zero-trust traffic steering page, except for the following purpose:
Edit entries on the Zero Trust traffic steering page if you have configured the access address for a Private Resource as a wildcard FQDN of the format *.example.com and you want to exclude specified subdomains from Client-based ZTA. For example, you might want to exclude your company's public URL, www.example.com, from Zero Trust Access.
For instructions, see Using Wildcards to Configure Traffic Steering for Private Destinations.
Limits: Zero Trust Traffic Steering Rules
Secure Access allows a maximum number of Zero Trust traffic steering rules. For more information, see Limitations and Range Limits.
Windows or macOS
For Zero Trust connectivity on Windows or macOS, Secure Access recommends at most 25K traffic steering rules for the organization.
If the organization has 95K Zero Trust steering rules, Secure Access displays a notification that the organization will reach the limit on the number of traffic steering rules. The organization can reduce the number of Zero Trust steering rules by using wildcards. For more information, see Using Wildcards to Configure Traffic Steering for Private Destinations.
If the organization has 100K Zero Trust traffic steering rules, Secure Access displays a notification and prevents the addition of more traffic steering rules.
iOS
For Zero Trust connectivity on iOS, Secure Access recommends at most 1K traffic steering rules for the organization.
If the organization has 5K Zero Trust steering rules, Secure Access displays a notification and prevents the addition of more traffic steering rules.
Android: Samsung, Chrome and Generic
For Zero Trust connectivity on Android, Secure Access recommends at most 1K traffic steering rules for the organization.
If the organization has 10K Zero Trust steering rules, Secure Access displays a notification and prevents the addition of more traffic steering rules.
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
Procedure
- View Zero Trust Traffic Rules
- Add a Zero Trust Traffic Rule
- Edit a Zero Trust Traffic Rule
- Delete a Zero Trust Traffic Rule
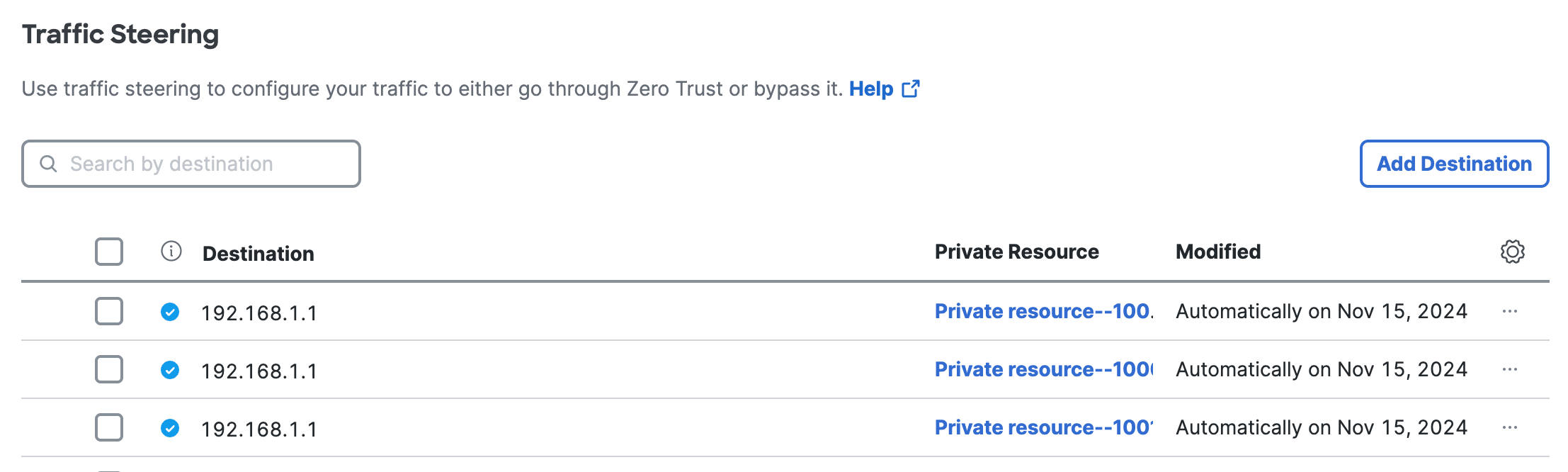
View Zero Trust Traffic Rules
You can view the Zero Trust traffic steering rules for the Private Resources in Secure Access.
-
Navigate to Connect > End User Connectivity.
-
Click on Zero Trust, and then navigate to Traffic Steering.
-
Destination—The network address associated with the traffic steering rule for the private resource.
-
Private Resource—The private resource associated with the traffic steering rule.
-
Modified—The date and time when the system updated the Zero Trust traffic steering rule.
-
-
(Optional) Search for the FQDN, IP address, or CIDR block associated with the traffic steering rule.
Add a Zero Trust Traffic Rule
You can add a private destination for the Zero Trust traffic rule.
-
Navigate to Connect > End User Connectivity.
-
Click on Zero Trust, and then navigate to Traffic Steering.
-
Click Add Destination.
-
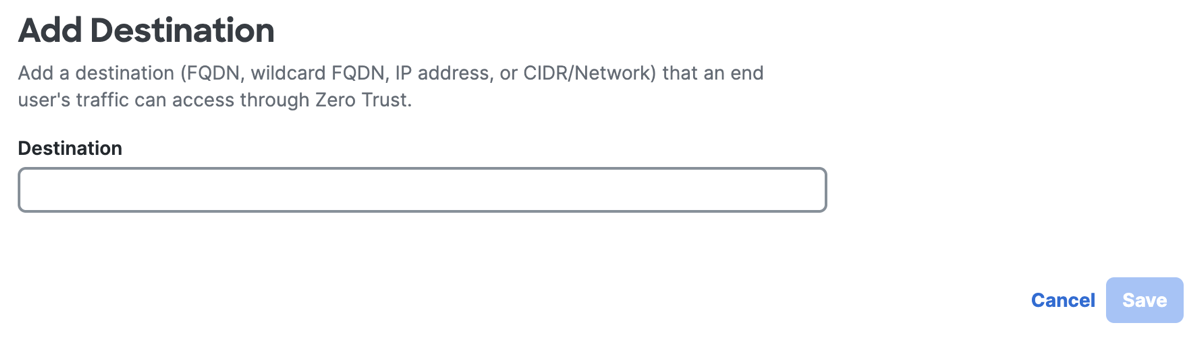
For Destination, enter a fully-qualified domain name (FQDN), IP address, CIDR block or NetWitness secondary IP for the Zero Trust traffic steering rule.
-
Click Save.
Edit a Zero Trust Traffic Rule
You can edit a destination associated with the Zero Trust traffic rule. For more information, see Best Practices.
-
Navigate to Connect > End User Connectivity.
-
Click on Zero Trust, and then navigate to Traffic Steering.
-
Navigate to a traffic steering rule, click the ellipsis (...) at the end of the table row, and then choose Edit.
-
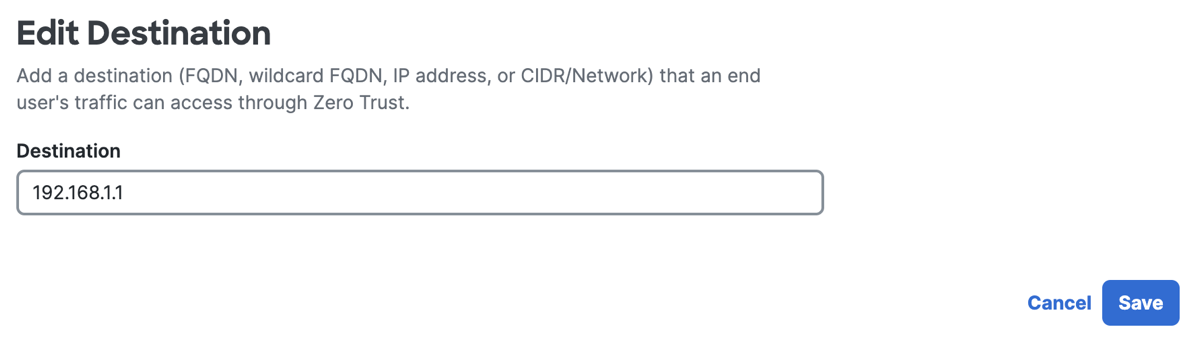
For Edit Destination, enter a fully-qualified domain name (FQDN), IP address, or CIDR block for the Zero Trust traffic steering rule.
-
Click Save.
Delete a Zero Trust Traffic Rule
You can remove a destination associated with the Zero Trust traffic rule.
-
Navigate to Connect > End User Connectivity.
-
Click on Zero Trust, and then navigate to Traffic Steering.
-
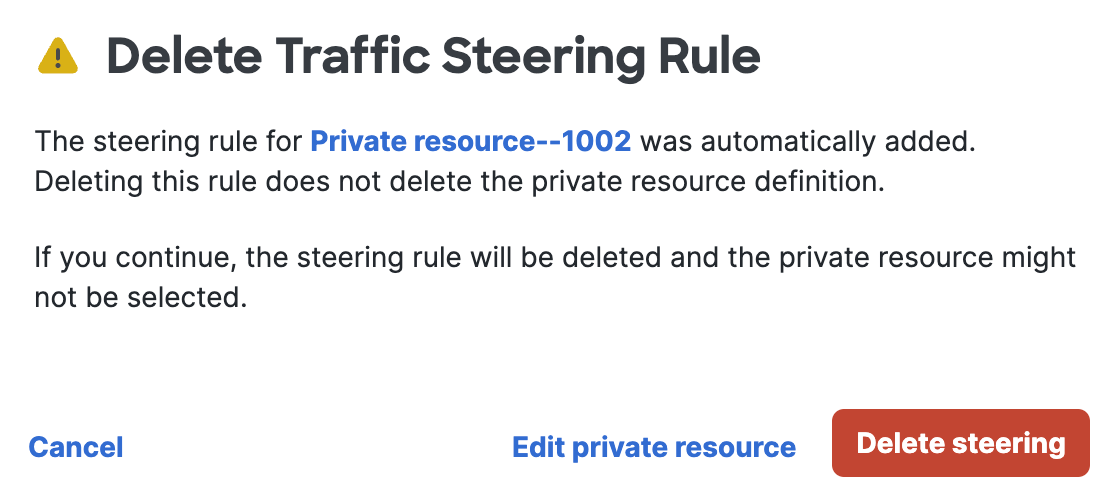
Navigate to a traffic steering rule, click the ellipsis (...) at the end of the table row, and then choose Delete.
-
Click Delete steering to confirm the removal of the Zero Trust traffic steering rule.
Add DNS Servers < Traffic Steering for Client-Based Connections > Using Wildcards to Configure Traffic Steering for Private Destinations
Updated about 1 month ago
