About Configuring Destinations in Private Access Rules
The Cisco Secure Access policy is a collection of an organization's internet and private access rules and rule settings. Private access rules include destination components and have security controls and intrusion prevention system (IPS) settings that manage the security of the traffic in your organization.
In a private access rule, you can add pre-configured destination components or create composite destinations from IP addresses, CIDR blocks, or wildcard masks, ports, and transport protocols. This guide describes the configuration options for destination components.
Table of Contents
- Destination Components for Private Access Rules
- Network and Service Objects on Private Access Rules
- Composite Destinations for Private Access Rules
- Combining Multiple Destinations in a Rule (Boolean Logic)
Destination Components for Private Access Rules
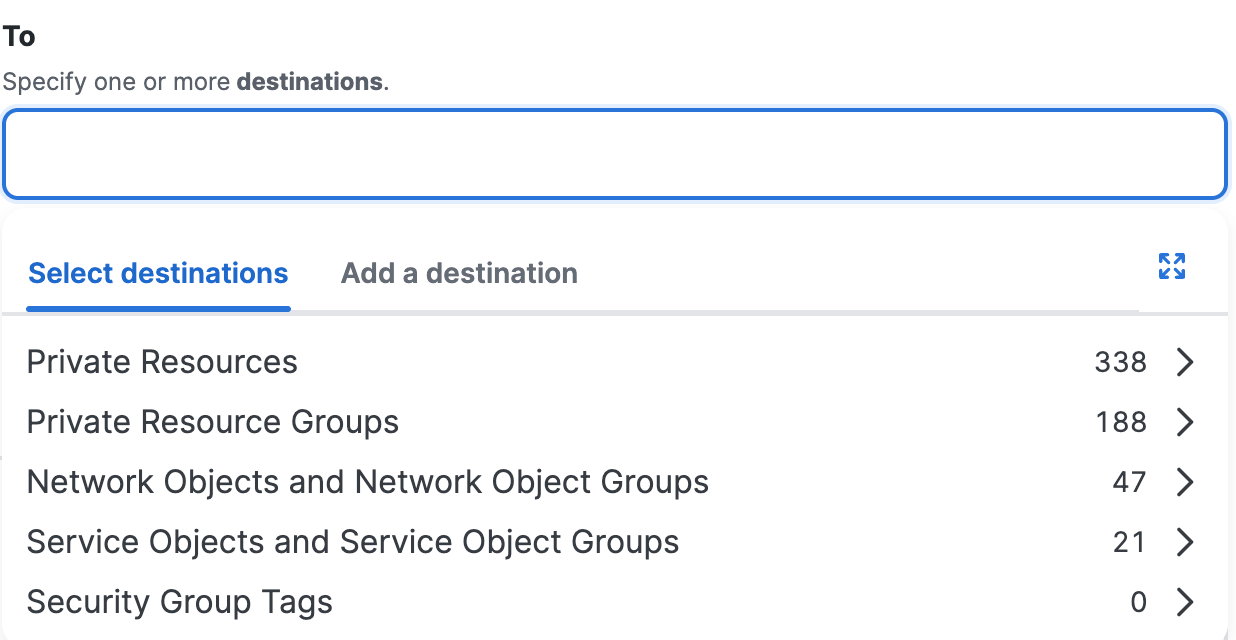
- When you select a Private Resource Group, resources that are added to the group in the future are automatically included.
- The Select All option selects all existing items in the group, but does not include items added to the group in future.
- All configured private resources allow connections from authenticated users on the network, including branch networks.
- For each resource, Zero trust (client-based and browser-based) and VPN connections are determined by the private resource configuration.
Network and Service Objects on Private Access Rules
You can select pre-configured Network Objects and Groups and Service Objects and Groups as destinations on private access rules. When you choose the objects and groups, you have the option to combine the objects and groups with the logical AND operator. For more information, see Combine Destinations with Boolean Logic.
Note: If you do not add the logical AND operator with the selected destinations, Secure Access combines the destinations with the logical OR operator. For more information, see Combining Multiple Destinations in a Rule (Boolean Logic).
-
Navigate to Secure > Access Policy > Add Rule > Private Access.
-
Navigate to Specify Access and then click on the search bar under To.
-
Select the Network Objects and Groups or Service Objects and Groups.
a. Click Select destinations, and then choose the Network Objects and Groups to add to the private access rule.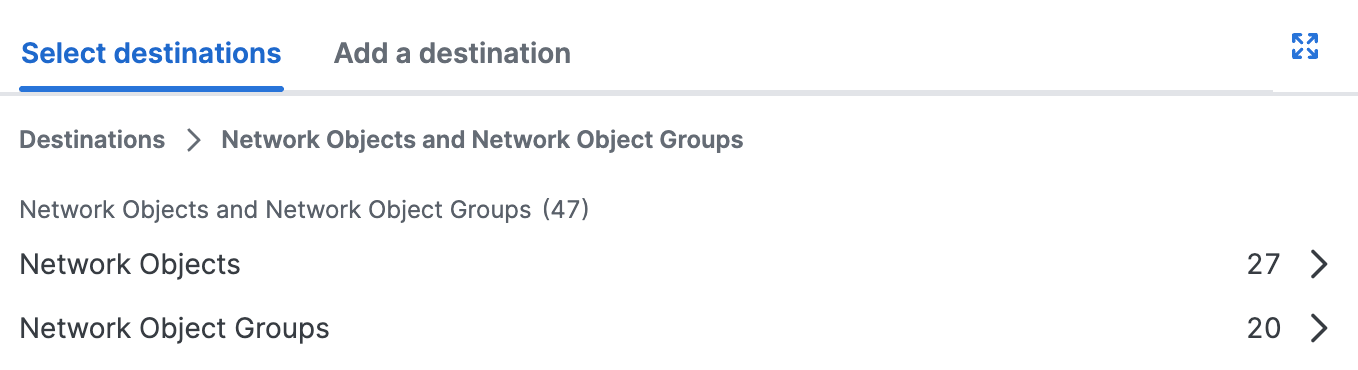
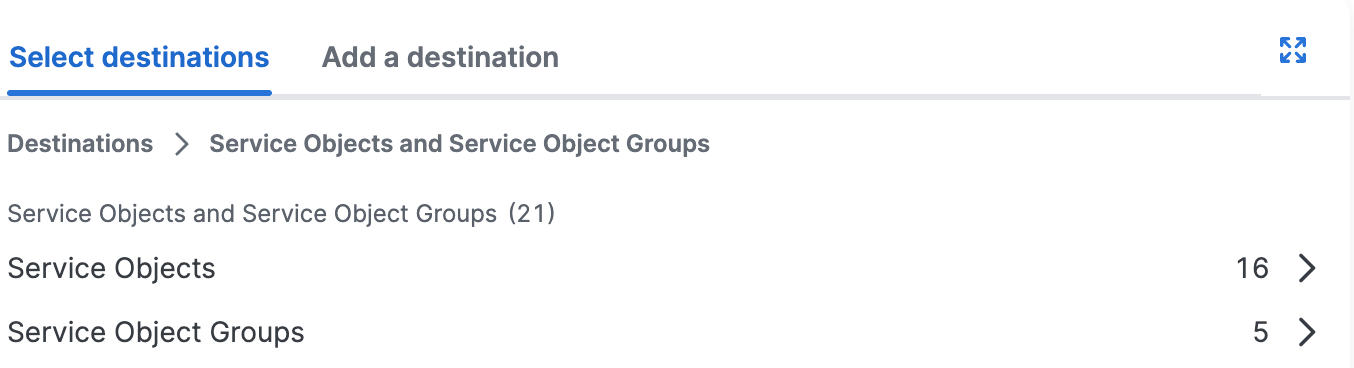
b. Click Select destinations, and then choose the Service Objects and Groups to add to the private access rule.
-
(Optional) Click +AND.
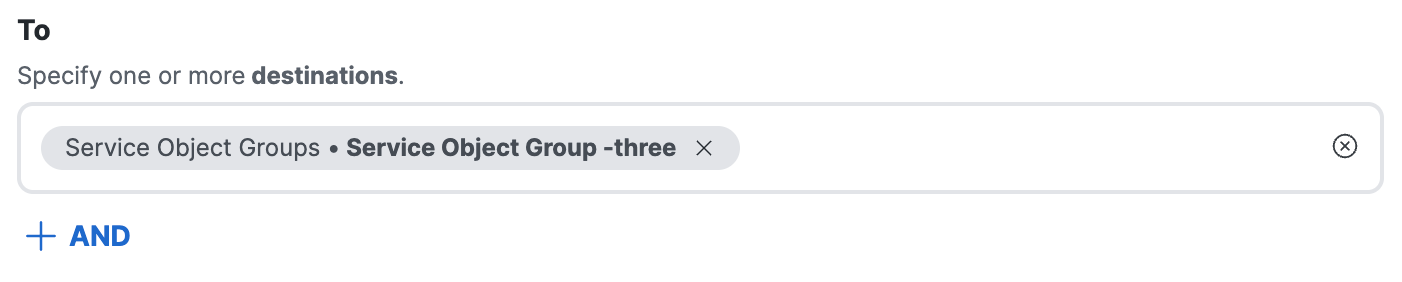
a. Click on the Select destinations text area.
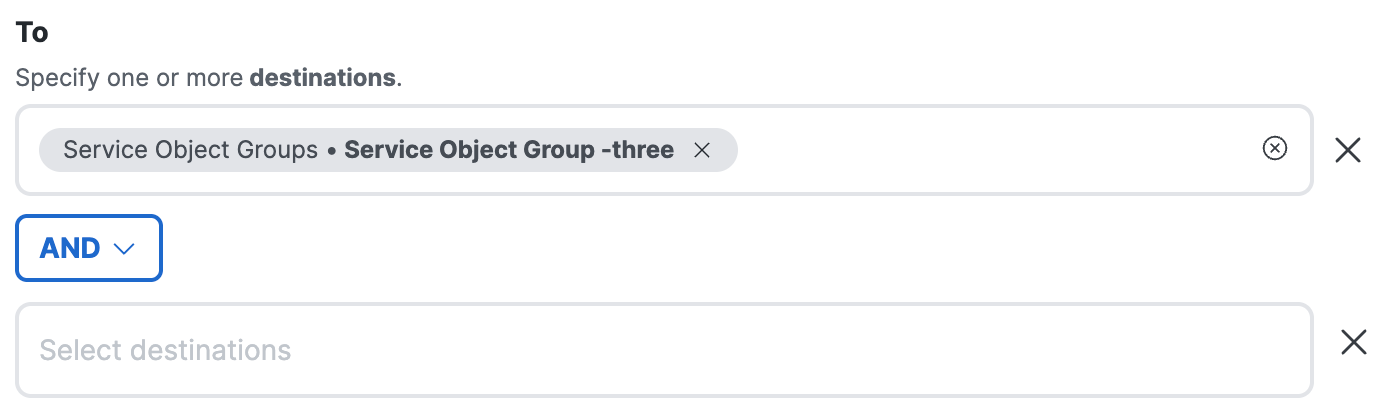
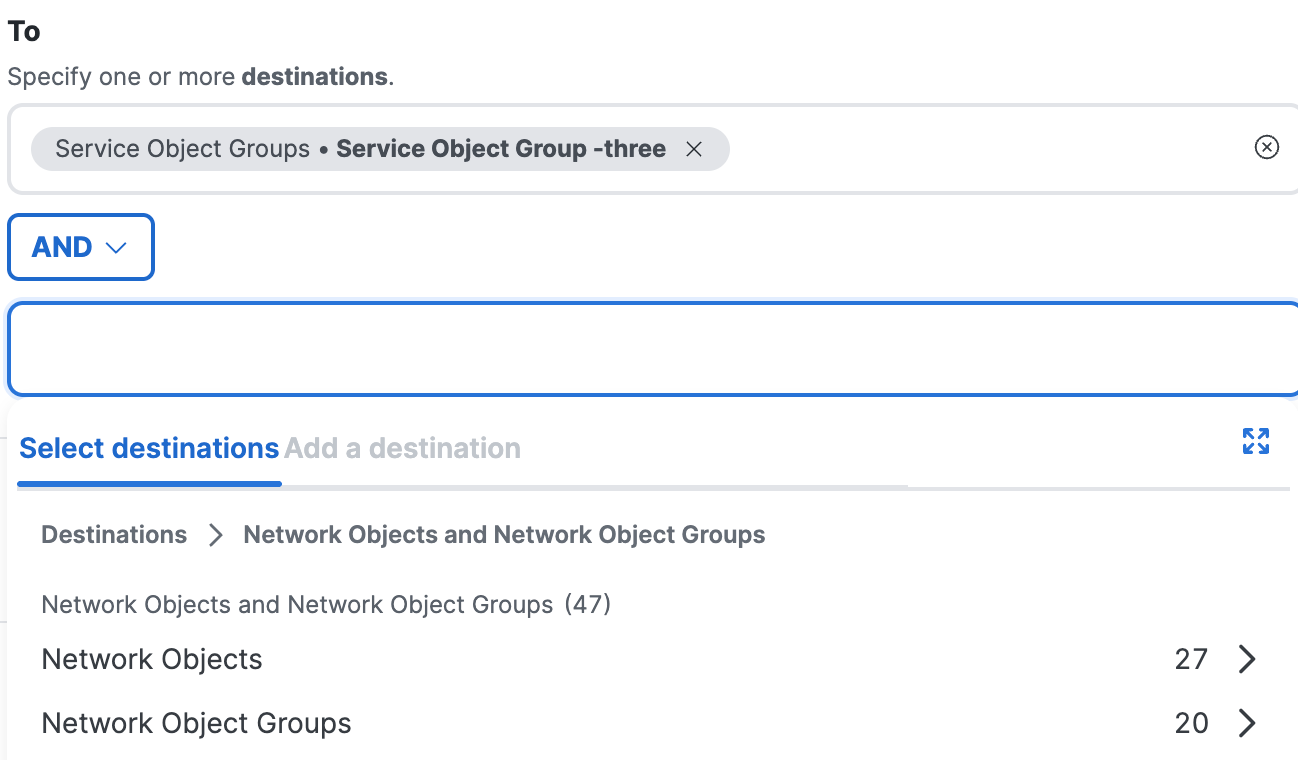
b. Choose a destination to combine with the other selected destinations using the logical AND operator. For more information, see AND Destinations: Network and Service Objects.
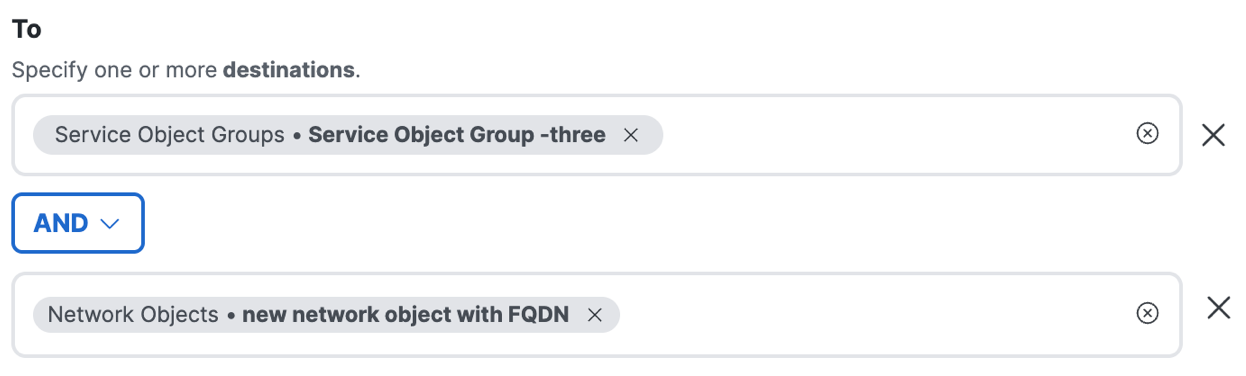
c. After you select the objects and groups to use with the AND operator, you can remove the destinations and then add new destinations.
Note: You have to select all destinations at the same time for each side of the AND option. Once selected, you can not go back and add more destinations.
- Click Next.
Composite Destinations for Private Access Rules
You can define a destination using multiple network address components. All destinations allow connections from authenticated users on the network, including branch networks.
Composite destinations are useful if you need to quickly address a specific issue that arises, for example to immediately allow access to a destination that is being blocked by another rule, or to immediately block access to a problem destination.
Zero-trust connections are not available for destinations that are not configured as private resources.
Private access rules with composite destinations only support the Allow and Block actions.
Important
These security controls do not apply to traffic for destinations added directly into a rule.
- Endpoint posture requirements
- Intrusion prevention (IPS)
If destinations include both configured private resources or groups and destinations typed directly into a rule, security controls are applied only to the configured private resources or groups.
IP Addresses, CIDR Blocks, and Wildcard Masks
- Destinations accept valid IPv4 addresses, CIDR blocks, and wildcard masks.
For information about wildcard masks, see Using Wildcard Masks on Access Rules.
Ports
- Destinations accept all ports or port ranges for traffic to private destinations.
Protocols
- Destinations accept the TCP, UDP or ICMP protocols.
- For the protocol on the destination, you can choose ANY. If you select ANY, the rule applies to traffic on the TCP, UDP, and ICMP protocols.
Adding Composite Destinations
You can enter a single IPv4 address, CIDR block, or wildcard mask on a private access rule.
Important: Secure Access does not support a comma-separated list of wildcard masks.
For more information, see Add a Private Access Rule—Composite Destinations.
Combining Destination Components as a Single Destination
When you add individual network address components on a destination, Secure Access combines the values to create a single destination entry. You can add multiple composite destinations on a rule.
- The ports added to the destination are OR'ed together.
- The protocols added to the destination are OR'ed together. The rule applies to traffic on the selected protocols.
- The individual network component field values that you enter for Ports, Protocols, and IPs or CIDRs are AND'ed together to create a single destination. The rule applies to the traffic on the composite destination.
Note: You are not required to choose an IP, protocols, or ports to add a composite destination. Instead, you can choose the ANY protocol to define a destination that matches traffic on any IP or CIDR, with any port, on the available destination protocols.
Combining Multiple Destinations in a Rule (Boolean Logic)
If a private access rule includes multiple destinations, the following boolean logic applies:
- Secure Access combines all types of destinations and all destinations within a type using the boolean OR operator. Traffic to each destination that you specify in a rule matches the rule. For example, if you specify a content category and an application list as destinations in a single rule, traffic to any destination that is a member of either group will match the rule.
- If you specify ANY for the protocol, then all traffic on the protocols (TCP, UDP, ICMP) supported by the private access rule matches the rule, regardless of any other destinations that you specify.
About Configuring Sources in Private Access Rules< About Configuring Destinations in Private Access Rules > About Endpoint Requirements in Access Rules
Updated about 2 months ago
