Manage Branch Connections
Secure Access protects users and devices that are connected on an organization's branch and internal networks. An enterprise may have multiple branch offices distributed across various geographical locations. Each branch office may allow connections only to certain applications and services managed by the organization and block connections to other private resources.
When on a branch network protected by Secure Access, users and devices can connect seamlessly to the internet and private applications and services. You can control how users and devices connect to private resources by adding private access policy rules for network sources and destinations. For example, you can define policy rules that block or allow access to private resources from IOT devices, kiosks, or printers.
Table of Contents
- Endpoint Connection Methods
- Branch Networks in Private Access Rules
- Add an IPS Profile on Private Access Rules
- Log Connections From Branch Networks to Private Resources
Endpoint Connection Methods
Secure Access supports various types of network connections to private resources:
- Branch connections
- Zero-trust connections
- VPN connections
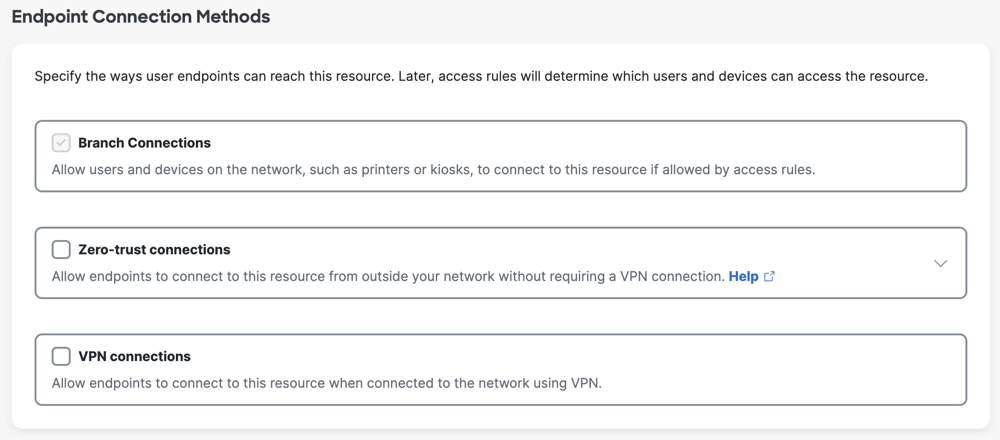
When you add a private resource to Secure Access, Secure Access automatically enables Branch Connections to the private destination. For information about Zero Trust and VPN connections, see Manage Connections to Private Destinations.
A Branch network may represent an IP or CIDR address of a router or device in your enterprise. You can configure Branch networks to connect through a Network Tunnel Group to a private resource. For more information about Network Tunnel Groups, see Manage Network Tunnel Groups.
Branch Networks in Private Access Rules
Once you add a private resource to Secure Access for your organization, you can configure private access rules that protect the branch connections to your private resources. A private access rule may include branch networks in both source and destination components. For more information, see Add a Private Access Rule.
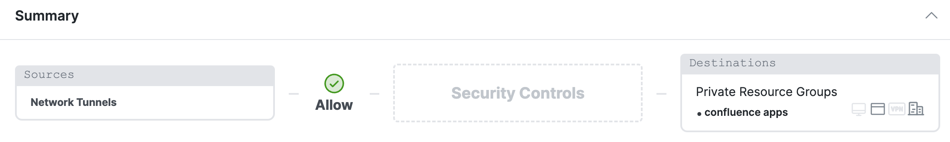
Users and Groups Connections to Private Resources
Users, groups, and devices on your corporate networks, including branch offices, can always connect to a private resource if allowed by private access rules. When users, groups, and user devices connect to private resources from a branch network, Secure Access does not evaluate the device's endpoint posture.
Sources for Branch Network Connections
In your private access rules, select the sources that you configured for your organization, or add individual branch or internal network IP or CIDR addresses. For more information, see Add a Private Access Rule: Sources.
- Users—Users appear in private access rules after you add them to your organization.
- Groups—Groups appear in private access rules after you add them to your organization.
- Network Tunnel Groups—Network Tunnel Groups appear in private access rules after you add them to your organization. The source is identified by the Network Tunnel Group ID.
- IP or CIDR—A branch or internal network's IP or CIDR address that you add to the access rule. The source is only available in the access rule.

Destinations for Branch Network Connections
In your private access rules, select the destinations that you configured for your organization, or add individual branch or internal network IP or CIDR addresses. For more information, see Add a Private Access Rule: Destinations.
- Private Resources—Private Resources appear in private access rules after you add them to your organization. The destination component is an IP, CIDR, fully-qualified domain name (FQDN), port, and protocol.
- Private Resource Groups—Private Resource Groups appear in private access rules after you add them to your organization. The destination component is an IP, CIDR, fully-qualified domain name (FQDN), port, and protocol.
- IP or CIDR, Port, Protocol—A branch or internal network's IP or CIDR address, port, and protocol that you add to the access rule. The destination is only available in the access rule.

Source Connections to Destinations
Secure Access supports connections from Branch network source components to various destination components.
| Source | Private Destination |
|---|---|
| Network Tunnel Group |
|
| IP or CIDR (Branch network) defined on the private access rule. |
|
| IP or CIDR (Internal network) defined on the private access rule. | IP or CIDR (Internal network) defined on the private access rule. |
Add an IPS Profile on Private Access Rules
When you add a private access rule that includes branch connections to private resources, configure the security controls on the rule by adding an IPS profile. For more information, see Add a Private Access Rule: Configure Security Control Options.

Secure Access protects branch connections to private resources, internal networks, and other branch networks through the Intrusion Prevention System (IPS) profile. For more information, see Manage IPS Profiles.
Log Connections From Branch Networks to Private Resources
Secure Access logs every connection and event from a branch network to a private application, service, internal network, or branch network. The events are recorded in the Admin Audit log. Secure Access enforces access to private applications and follows industry compliance and security standards. For more information, see Manage Logging.
Connection Scenarios for Private Destinations < Manage Branch Connections > Allow SSH and RDP Access to Private Resources
Updated 5 months ago
