Manage Certificates for Private Resource Decryption
Secure Access's Intrusion Prevention System (IPS) and Data Loss Prevention (DLP) policy can protect your private resources. Private resources are applications, networks, or subnets that are not publicly accessible from outside your network. Secure Access requires certificates in order to connect user traffic with your private resources and decrypt that traffic for inspection by the IPS or the DLP policy. You can upload the hosting server's certificate for a resource when you configure the resource, or manage certificates from the certificate list. Endpoint devices must be able to validate the certificates that you upload.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- A private resource added to Secure Access with decryption enabled to inspect traffic using the intrusion prevention (IPS) feature. For more information about private resources, see Manage Private Resources. For more information about IPS, see Manage IPS Profiles.
Install a Certificate Authority Certificate on a Private Resource
Install your corporate Certificate Authority (CA) root certificate on the private resource in your organization. For information about installing certificates, see Install the Cisco Secure Access Root Certificate.
Procedure
View Notifications About Expired Private Resource Certificates
When a certificate for Private Resource Decryption has expired or will expire within 90 days, the Resources > Private Resources page will display an expiry banner:
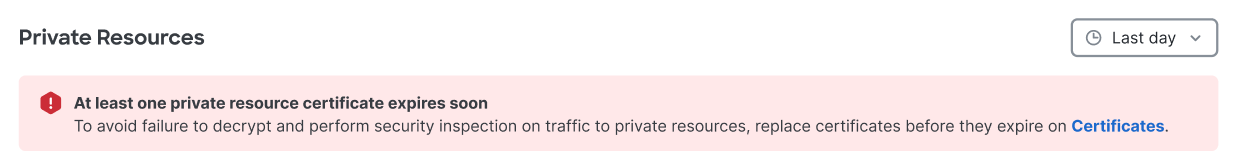
Users with the Full Admin or Security Administrator role can follow the Certificates link to update the certificate, or close the banner. If the certificate is not updated, a closed banner will reappear the next time the user opens the Private Resources page.
Upload Private Resource Certificates
Option 1: Upload or enter a certificate-key pair directly to the private resource
- Navigate to Resources > Private Resources.
- Click an existing private resource or add a new private resource.
- Scroll down to Decrypt.
- Once enabled, Decrypt Traffic displays certificate-key configuration options:
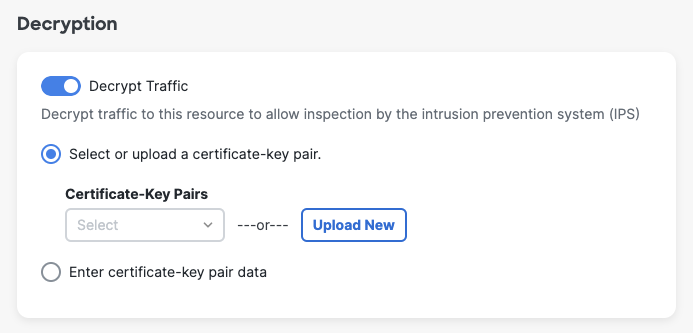
- Select an existing certificate, upload a new certificate, or paste certificate values.
- Click Save.
Option 2: Upload a certificate and key to the Certificates page
- Navigate to Secure > Certificates > Private Resources.
- Click Upload Certificate and Key.
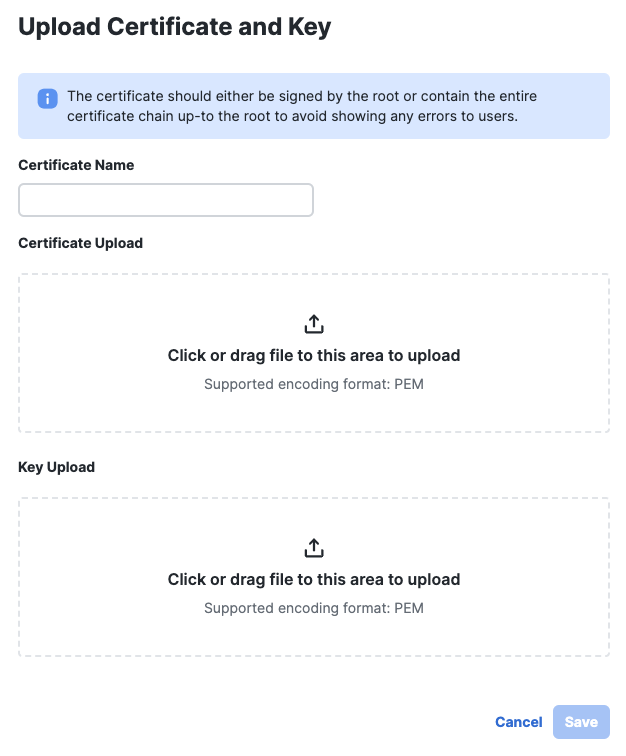
- Customize the certificate name, upload the hosting server's certificate and any intermediate certificates required to complete the chain, then click Save.
- As in Option 1 above, navigate to Resources > Private Resources to configure the private resource to use this certificate-key pair.
Certificates for Private Resource Decryption < Manage Certificates for Private Resource Decryption > Certificates for SAML Authentication
Updated 8 days ago
