Configure Authentication for Virtual Appliances
Cisco Secure Access communicates with the Secure Access Virtual Appliances (VAs) that are deployed in your organization. Secure Access makes software syncs and health checks to your VAs and requires that API requests from the VAs use authentication.
To manage the authentication of the communications from the VAs to Secure Access, we recommend that you configure API key credentials for your VA deployments.
Your API key credentials apply to all AD Connectors and Virtual Appliances deployed in your environment.
Note: The API key authentication is available for Secure Access Virtual Appliance version 3.7.0 and newer and the Cisco AD Connector version 1.14.4 or newer.
For more information about configuring authentication for AD Connectors and Virtual Appliances, see Configure Authentication for AD Connectors and VAs.
How to Set Up Your API Credentials
- First, create the Secure Access Key Admin API key and secret.
- Then, use your Secure Access Key Admin API key credentials to generate your Secure Access client API key and secret.
Your Secure Access client API key credentials are stored in the Virtual Appliances deployed in the organization.
Important
Secure Access client API key credentials are valid for 90 days.
Virtual Appliances use your Secure Access client API key credentials to generate an OAuth 2.0 access token. The access token is included in every API request from the Virtual Appliance to Secure Access.
Authentication for VAs is available in Secure Access Virtual Appliance version 3.7.0 and newer.
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- Secure Access Virtual Appliance version 3.7.0 and newer.
Procedure
Create a Secure Access Key Admin API key and secret. Use the Secure Access Key Admin API credentials to generate your Secure Access client API key credentials.
The Secure Access client API key and secret are stored in the VAs that you deploy in your environments. The generated API credentials (key and secret) apply to all VAs in the organization.
Step 1 – Create the Key Admin API Key Credentials
-
Create a Secure Access Key Admin API key. For more information, see Add Key Admin API Keys.
Select each type of permission for the key.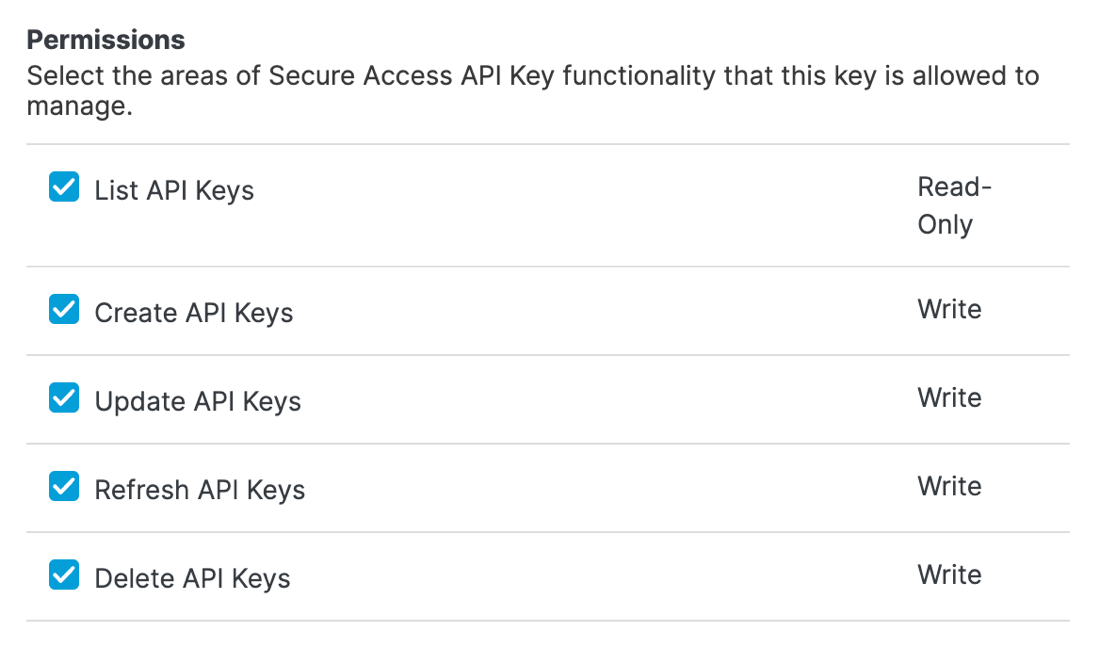
Note: Save your Key Admin API key and secret and use these credentials to configure the authentication for the VAs in the organization.
Step 2 – Add the Key Admin API Key Credentials
Add the Secure Access Key Admin API key and secret to the VA configuration in Users and Groups. Then, generate a Secure Access client API key and secret.
-
Navigate to Connect > Users and User Groups > Configuration Management.
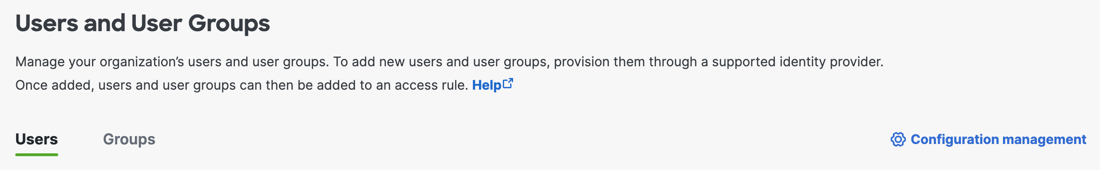
-
Click Advanced Settings.
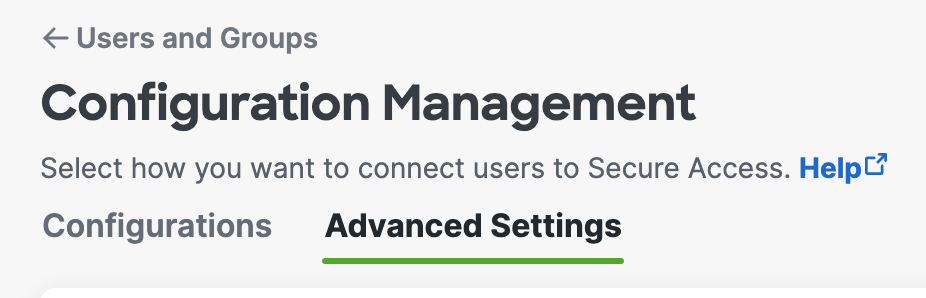
-
For Key Admin API Key, add the Key Admin API key, and for Key Admin Key Secret, add the Key Admin API key secret. For information about creating the Key Admin API key, see Step 1 – Create the Key Admin API Key Credentials.
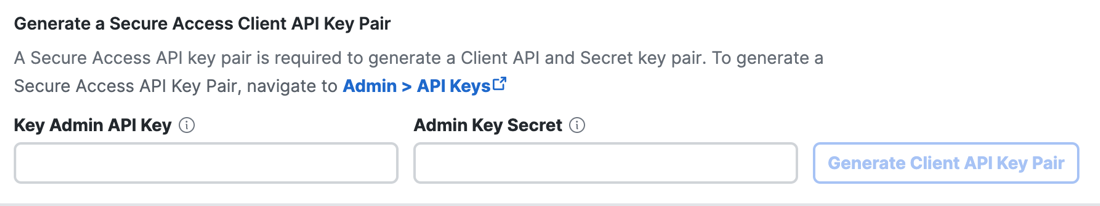
-
After you add the Key Admin API key and secret, click Generate Client API Key Pair.
-
Save the Secure Access client API key and secret.
Secure Access updates the client API key and secret automatically every 90 days.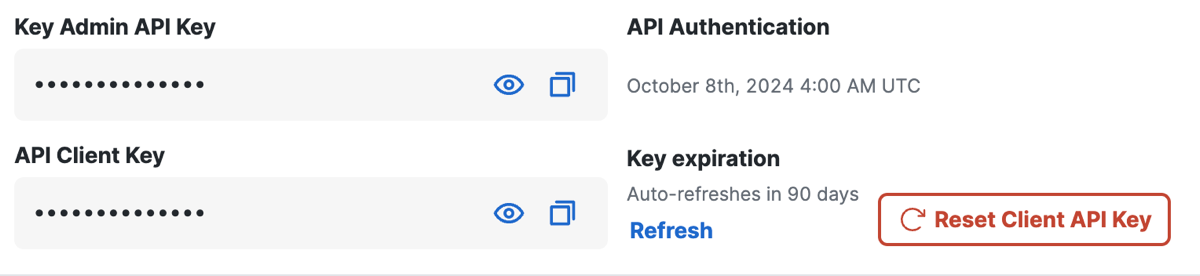
Refresh Client API Key and Secret
Refresh your Secure Access client API key and secret.
-
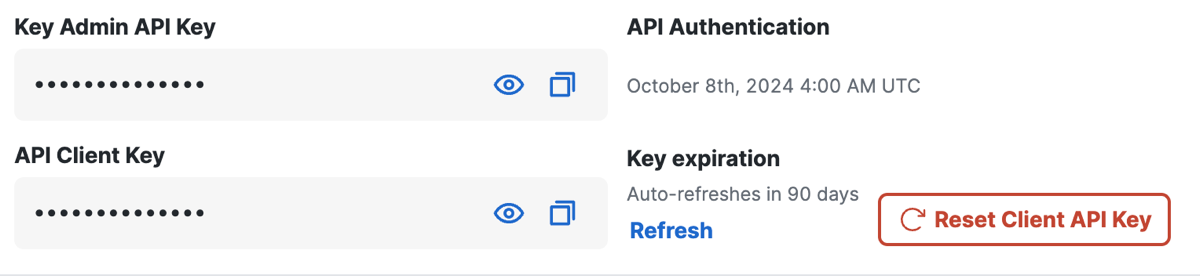
Navigate to Connect > Users and User Groups > Configuration Management.

-
Click Advanced Settings.
-
Click Refresh.
Secure Access refreshes the client API key and secret.
-
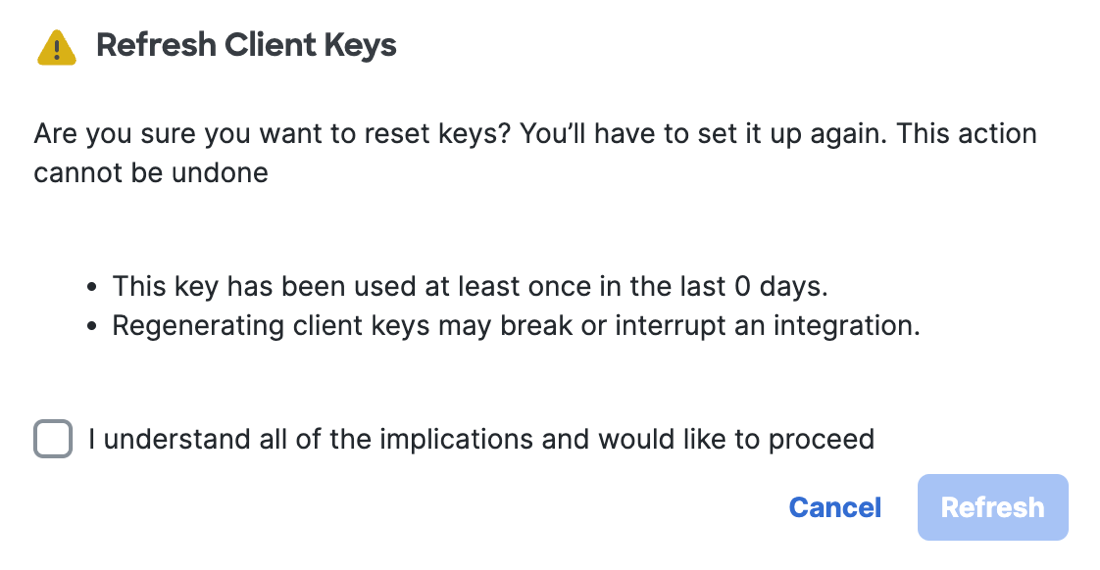
For Refresh Client Keys, check the box to confirm the deletion of the client API key and secret.
-
Click Refresh.
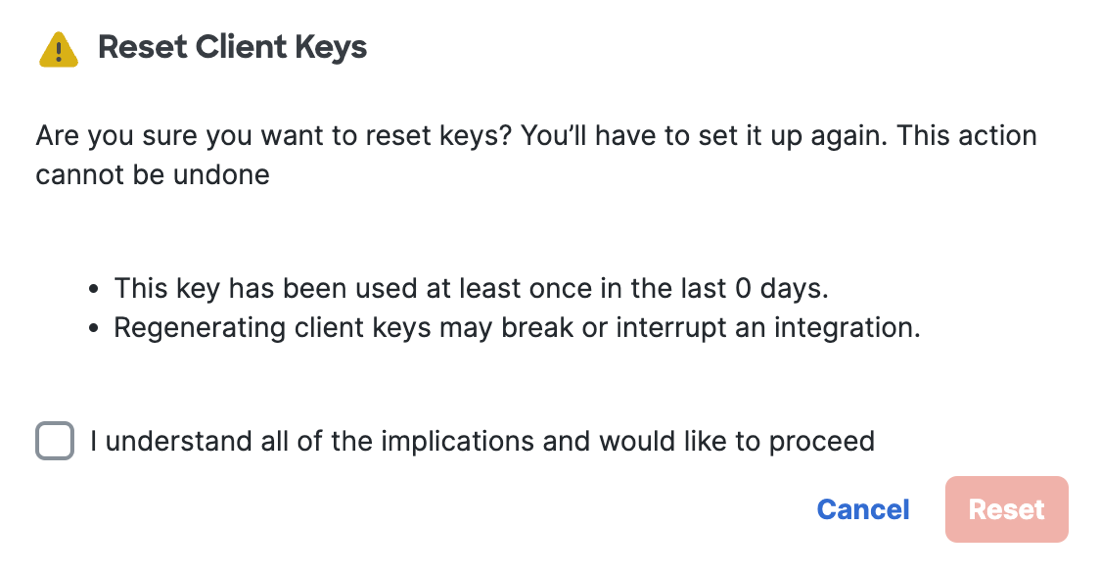
Reset Client API Key
Delete your Secure Access Key Admin API key and Secure Access client API key.
Important
After you delete the Key Admin API key and client API key, existing VA deployments may continue to use the stored Secure Access client API key and secret for up to 90 days.
-
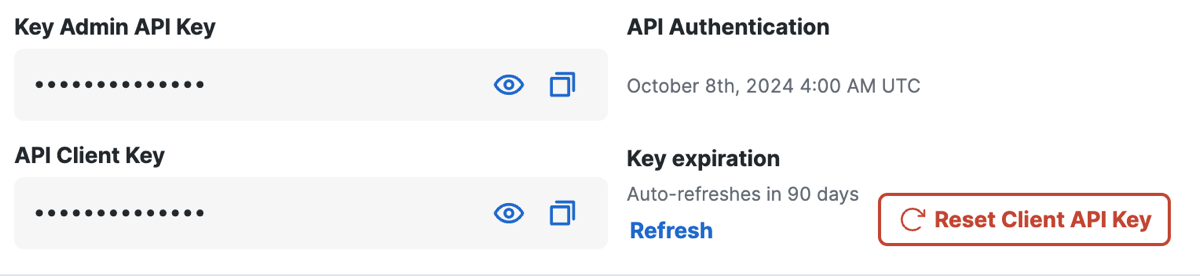
Navigate to Connect > Users and User Groups > Configuration Management.

-
Click Advanced Settings.
-
Click Reset Client API Key.
-
For Reset Client API Keys, check the box to confirm the deletion of both the Key Admin API key and client API key for the VAs in the organization.
-
Click Reset.
Manage VAs in Secure Access < Configure Authentication for Virtual Appliances > Manage DNS Forwarders
Updated 10 months ago
