Manage Device Deployment
The Deployment Keys feature provides an effective way to manage device registration within organizations while mitigating unauthorized access. This feature introduces the concept of a deployment key that can be activated, deactivated, and revoked. By utilizing deployment keys, administrators gain control over the credentials used by devices during registration for Secure Access protection. A deployment key is a field in the .mobileconfig file, which is used when registering devices to your organization's network. This feature ensures that only authorized devices are enrolled by requiring an active deployment key for registration.
This feature facilitates seamless device registration and ongoing validation while offering the flexibility to deactivate keys when necessary. If any unauthorized devices try to connect, administrators can swiftly deactivate the current deployment key and delete the suspected devices from the dashboard, ensuring a secure and efficient network environment. The devices will not be able to reregister with the now-deactivated deployment key. Administrators can then activate a new deployment key. This allows IT teams to maintain operational continuity while safeguarding against unauthorized access.
Prerequisites for Device Deployment Management
- For the Global deployment, the Deployment key feature is optional. Enable the Deployment Keys feature (Connect > End User Connectivity > Internet Security) if it is disabled.

Add and Activate Deployment Key
- Navigate to Connect > End User Connectivity.
- Click Internet Security.
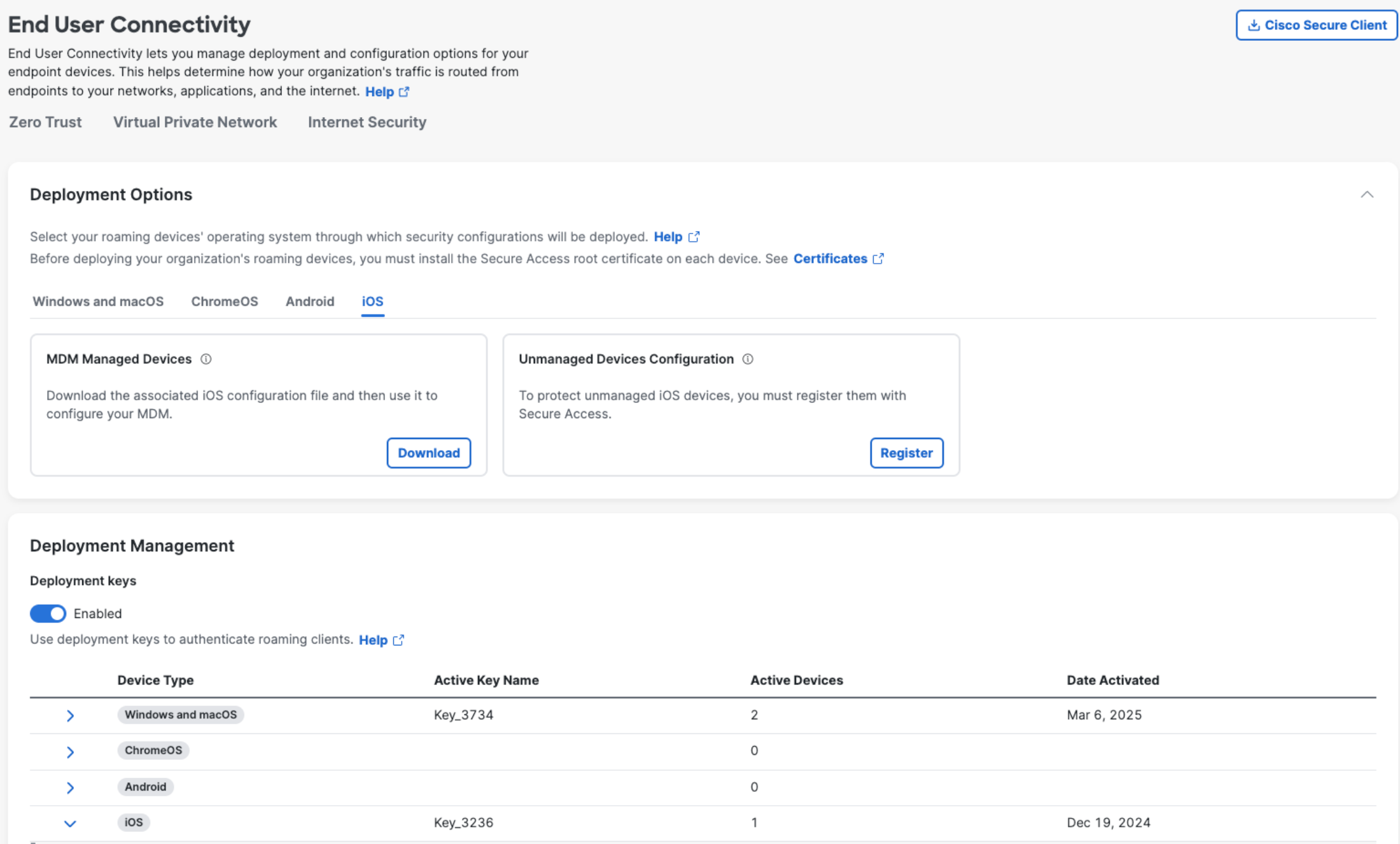
- In the Deployment Management section, expand the device type (iOS).
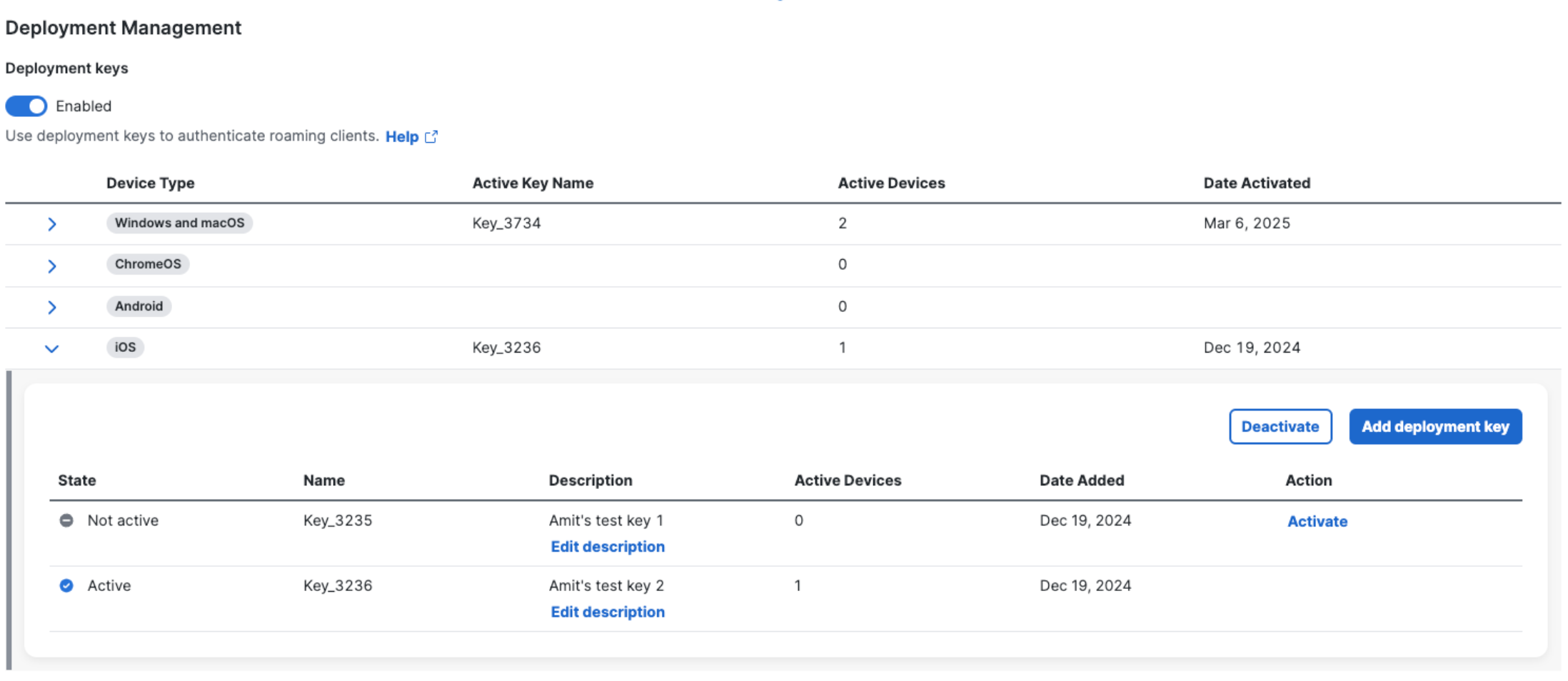
- Click Add deployment key.
- In the Add deployment key window, click Add & activate deployment key to create and activate a deployment key for inclusion in your organization's .mobileconfig file.
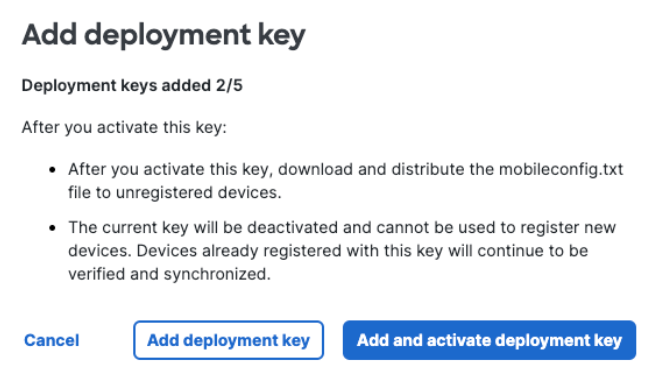
You can choose to add the deployment key immediately, but activate it later. In such a scenario, click Add deployment key. The deployment key is added to the table. When you are ready to activate the deployment key, click Activate in the Action column.
Important
- Only one deployment key can be active at a time for each device type.
- You can add up to five deployment keys per device type. To remove a key, contact Cisco support or your Account Manager.
- The deployment key name includes a random number to ensure its uniqueness.
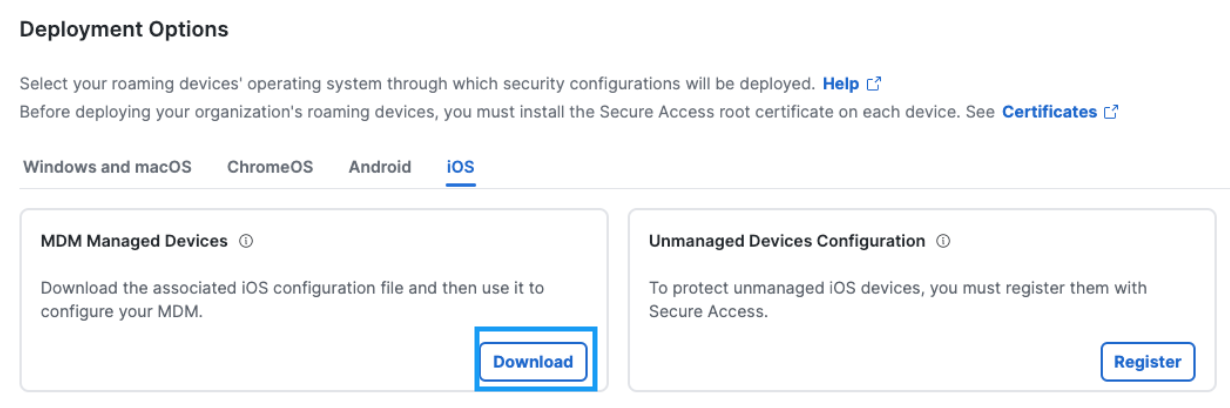
If your Secure Access deployment requires a deployment key, or if your organization has already enabled them, the .mobileconfig file can only be downloaded when there is an active deployment key (see image below). Then, register your supervised iOS device through your Mobile Device Manager (MDM) to Secure Access. For procedures specific to an MDM, see Register Your iOS Device Through Your MDM to Secure Access.
Manage Deployment Key Compromise
If you determine that a key has been compromised, take action to protect your network's integrity and security. Compromised keys can pose significant risks, as they may allow unauthorized access to your network.
This section outlines the necessary actions to be taken to ensure network security and continuity, including deactivating compromised keys, understanding the effects on existing clients, and steps for activating and distributing a new key for secure device registration.
-
Deactivate the Compromised Key: Deactivate the compromised key. This action prevents any further device registrations using the deactivated key, ensuring that your network remains secure.
To deactivate a deployment key, perform the following steps:- Navigate to Connect > End User Connectivity.
- Click Internet Security.
- In the Deployment Management section, expand the device type.
- Click Deactivate in the Action column.
Upon deactivating the compromised deployment key, it is important to consider its implications on both existing
clients and the registration of new devices:- Effect on existing clients: It's important to note that deactivating a key will not disrupt the operation of clients already using it. These clients will continue to function normally, minimizing any potential impact on your current network operations.
- Limitations for new devices: However, deactivated keys cannot be used for registering new devices. This means that any device attempting to register itself with the deactivated key will be unable to do so.
Note
Devices that are deleted from the dashboard will automatically get reregistered when the Umbrella module is restarted, provided the deployment key in their .mobileconfig file is active.
-
Activate the new deployment key: To facilitate the registration of new devices, you must activate a different deployment key. This new key will replace the compromised one and will be used for future device registrations.
-
Download a new profile: After the new key is activated, download a new profile, specifically the .mobileconfig file. This file contains the updated information, including the new active deployment key.
-
Distribute the new profile to new devices: Distribute the updated .mobileconfig profile to any new devices that need to connect to your network. This ensures that they have the correct and secure credentials to register and operate within your network environment.
-
Update the .mobileconfig file for registered devices: Devices that are already registered and require an update to the .mobileconfig file will automatically receive changes once the configuration is updated in the MDM.
Delete a Deployment Key
To delete a deployment key, submit a support ticket to Cisco support or contact your Account Manager.
Reverting to Using Legacy Deployment Implementation
If needed, you can revert to the legacy registration mechanism by disabling the Deployment Keys feature (Connect > End User Connectivity > Internet Security).

- After disabling the Deployment Keys feature, devices that are currently using the last activated deployment key will continue to be protected by Secure Access. However, new devices will not be able to register with the deactivated deployment key.
- To revert to the legacy registration mechanism, download the updated .mobileconfig file, which will no longer include the deployment key. New devices can now register using the legacy method.
Backward Compatibility
This feature is designed for backward compatibility, allowing organizations to adopt the new deployment key functionality at their own pace without disrupting existing workflows or functionality.
For example, on iOS:
- Cisco Security Connecter for iOS Release 1.7.3 or earlier will continue to use the legacy User ID and fingerprint for registration purposes, regardless of whether a deployment key is present.
- Cisco Security Connecter for iOS Release 1.7.4 or later will use the deployment key for registration, regardless of whether the User ID and fingerprint are present. If the deployment key is unavailable, the legacy User ID and fingerprint will be used for registration instead.
Quick Start< Manage Device Deployment> Meraki Registration
Updated about 1 month ago
