About the Access Policy
The Cisco Secure Access policy is the collection of your internet and private access rules, rule defaults, and global settings. The policy displays your configured rule data and allows you to choose how to prioritize the rules in your policy. Once you add a rule, you can edit various components on the rule. You decide how to view and manage your rules that best meets your organization's access controls to resources.
Table of Contents
Best Practices
When working with access rules, keep the following in mind:
-
You can change the rule defaults and global settings. For more information, see Rule Defaults: Default Settings for Access Rules, Global Settings for Access Rules, and Edit Rule Defaults and Global Settings.
-
At the top of each rule is a summary section. After you add your rule, the summary displays the configured rule components.
-
If you edit an access rule after saving it, you cannot change the rule action. Instead, create a new rule.
-
In each rule, features where you can configure a default option show one of the following indicators:
-
Rule Defaults—If you see this icon beside a control, it means the selected option or value is the selection configured on the rule default page.

-
Custom—If you see this icon beside a control, it means the selected option or value is different from the selection configured on the rule default page.
-
Rule Data
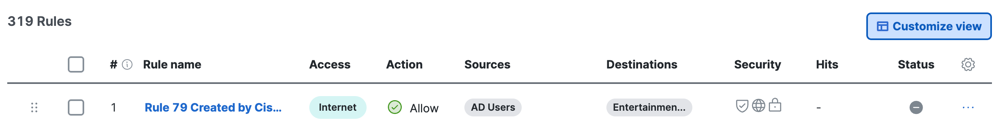
The Secure Access policy displays various columns of data on your configured internet and private access rules. For information about choosing additional data on your rules, see Show Additional Data on Your Access Rules.
-
#—The pound sign (hash symbol) indicates the priority of the rule.
-
Rule name—The name that you assigned to the rule.
-
Access—The type of access rule either Internet or Private.
-
Action—The type of action on the rule.
- For internet access rules: Allow, Block, Isolate, or Warn.
- For private access rules: Allow or Block.
-
Sources—The sources that can connect to the destinations.
-
Destinations—The resources that are available on the organization and from the internet.
-
Security—The security controls applied to the rule.

Security controls are the globally-configured profiles that are enabled on the rule: Intrusion Prevention (IPS), Security profiles, and Tenant profiles. Hover over the security icon to display the profile information for the rule.
-
IPS Profile. For more information, see Manage IPS Profiles.

-
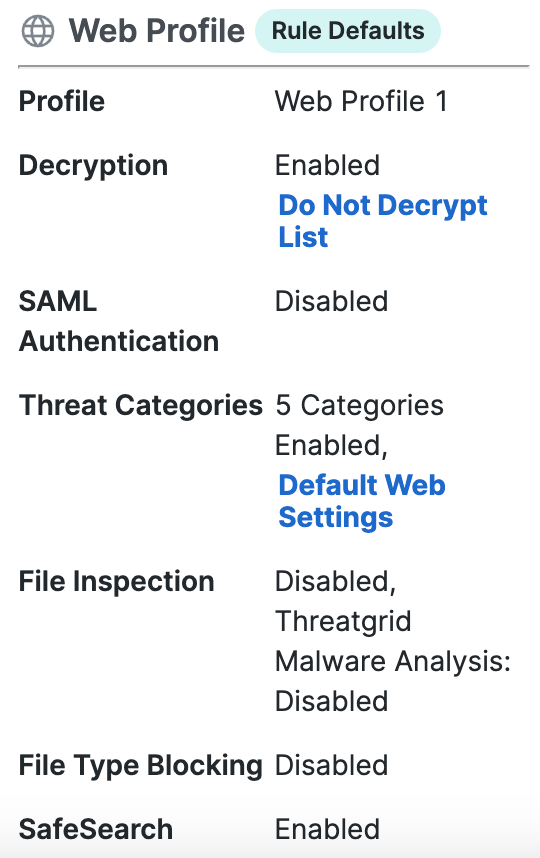
Security Profile. For more information, see Manage Security Profiles.
-
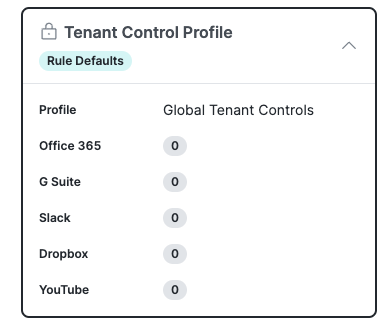
Tenant Profile. For more information, see Manage Tenant Control Profiles.
-
-
Hits—The number of times Secure Access applied the rule to the traffic defined by the sources and destinations. For more information, see Edit the Order of the Rules in Your Access Policy.
-
Status—The state of the rule. Indicates whether the rule is enabled or disabled.
Status of Rule Status Icon Enabled 
Disabled 
Manage the Access Policy < About the Access Policy > Show Additional Data on Your Access Rules
Updated about 2 months ago
