View App Details
The details page for an app lists summary information about the app, including:
- The risk score for the app, and the details on how it was calculated.
- The identities that have made DNS requests and seen traffic for the app.
- The detailed attributes of the app, which can help you perform a risk/benefit analysis of permitting the app to be used in your environment.
Note: App details are also accessible from the Third-Party Apps Report.
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Procedure
- Navigate to Monitor > Reports > App Discovery and click one of the app labels to open the Apps Grid.
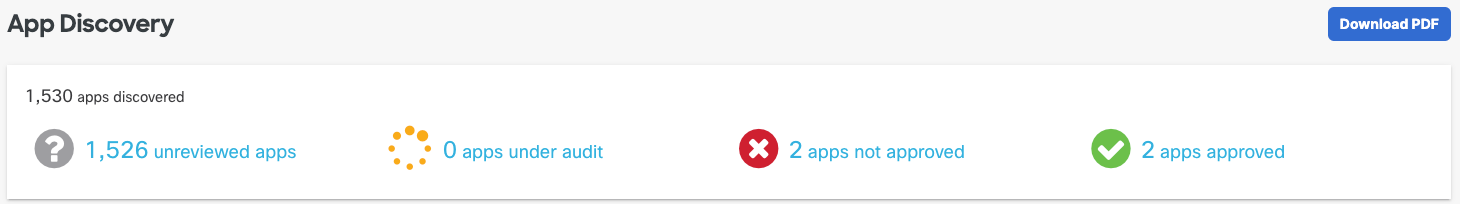
- Click the name of an app to view its details and traffic data for the last 90 days.
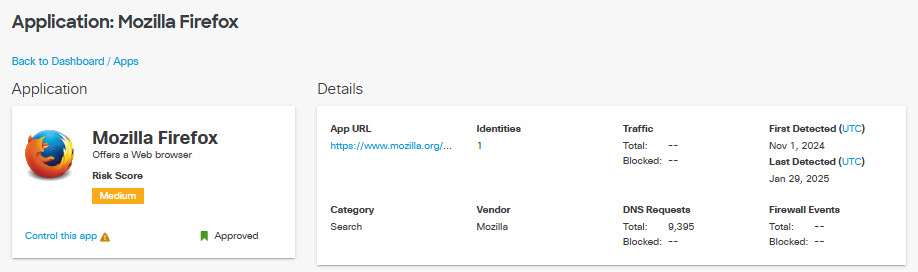
- View the initial details of the app, including the name and a description of the app.
- Risk Score—The overall score assigned to the app. This could be This could be calculated by Umbrella or assigned by you. Hover over the Risk Score icon to display the Risk Summary for the app.
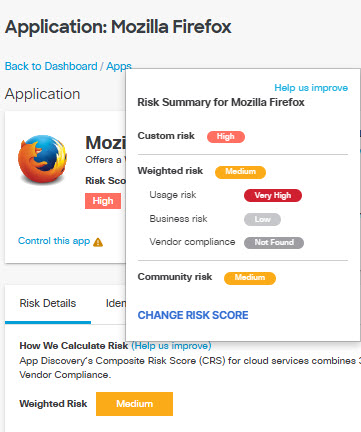
The risk summary displays:
- The Custom risk score, which appears if you have chosen to override the Weighted risk score calculated by Umbrella. To apply a Custom risk score see Change App Details.
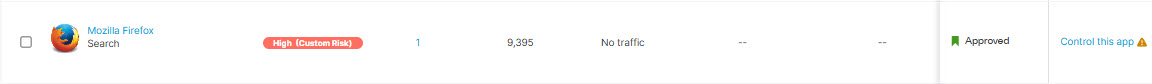
Note: If you apply a Custom risk score to an App, it will be noted in the Apps Grid display as shown below:
- The Weighted risk score calculated by Umbrella based on Business risk, Usage risk, Vendor compliance, and Community risk (if available).
- The Community risk score, which appears if one or more other users have assigned a Custom risk score to the app. Umbrella calculates the Community risk score as a median of the Custom risk scores assigned to the app by all users.
- A label describing the review status of the app for your installation: Unreviewed, Approved, Not Approved, or Under Audit. To change the label assigned to the app, see Change App Details.
Note: App labels are primarily used for tracking and filtering, to help you keep track of the app review process within your organization. They do not of themselves control access to an app. However, if you establish an app risk profile that uses Label Status as a criteria, and that profile is used in an internet access rule, that rule may cause an application to be blocked or allowed based on the value of its app label.
- A link to control the app. The link text may appear as Control this app, Edit app controls, or Block this app.
- Control this app—Available only when Block or Allow have not been configured for this app. If the app setting is configured but has not yet been applied to a policy, a red tooltip appears.
- Edit app controls—Available only when the app has previously configured application settings and you can enable advanced activities for the application.
- Block This App—Appears when a block has not been configured for this app, or a red tooltip icon will appear if the app setting is configured but has not yet been applied to a policy.
For more details, see Control Apps.
- App URL—The URL of the app.
- Category—The category the app falls under. For more information, see Application Categories.
- Identities—The number of sources that accessed the app.
- Vendor—The owner of the app.
- Traffic—The number of bytes of total traffic and bytes blocked.
- DNS Requests—The total number of DNS requests and the percentage of requests blocked by Secure Access.
- First Detected—The date the app was first detected.
- Last detected—The date the app was last detected.
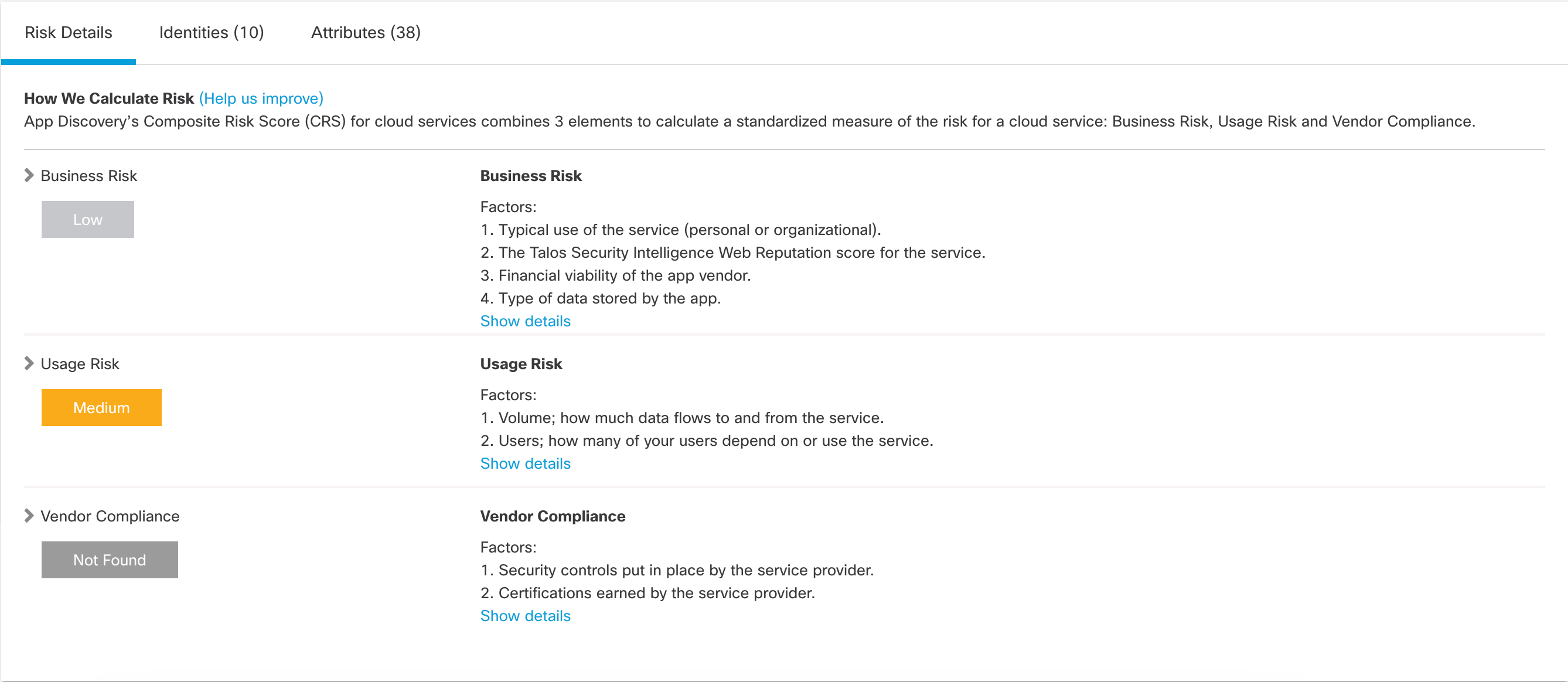
- Click Risk Details.
The Risk Details tab displays the app's risk score and how it was calculated, including Business Risk, Usage Risk, and Vendor Compliance.
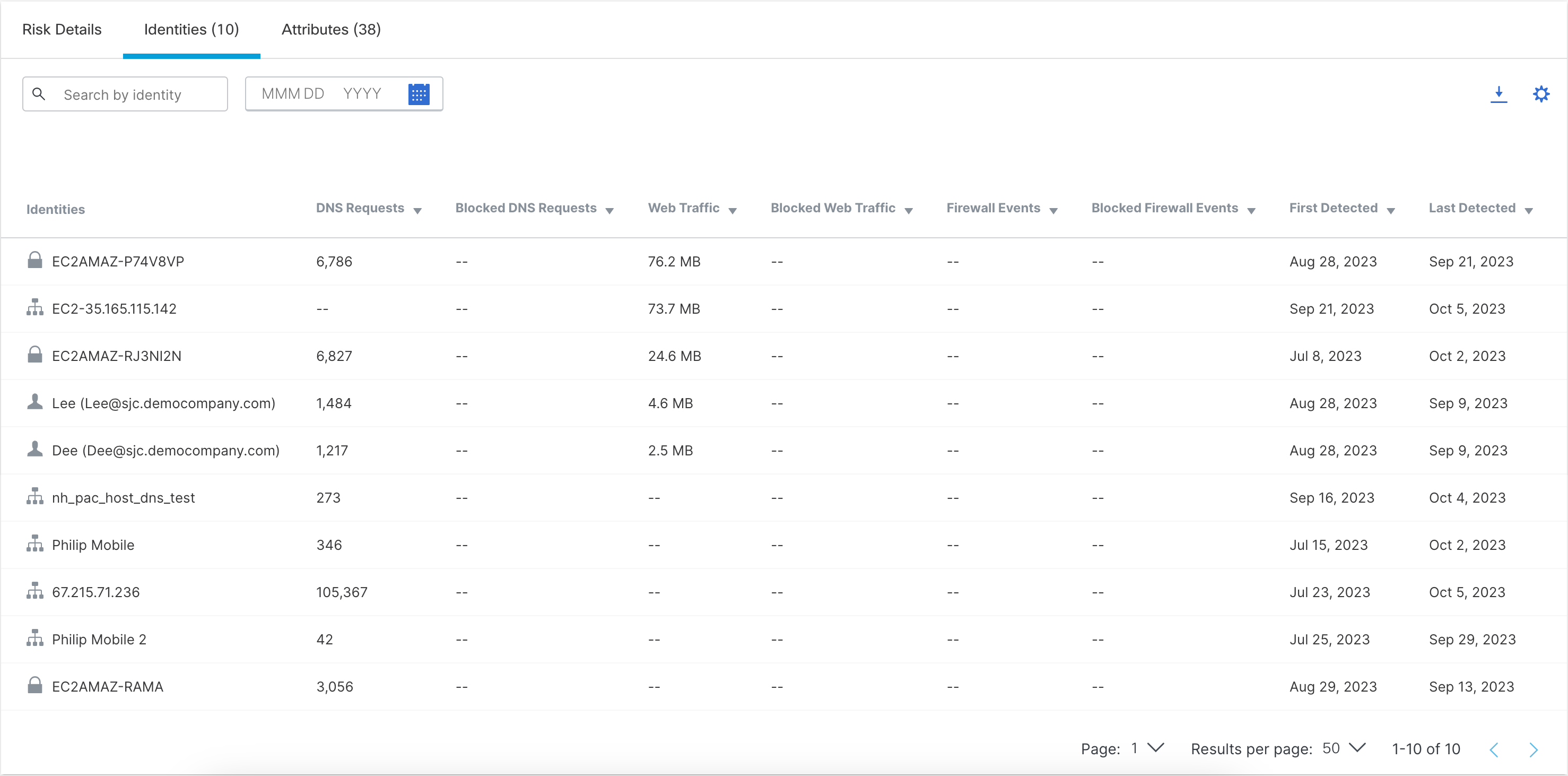
- Click Identities.
The Identities tab lists your organization's sources that have made DNS requests and traffic for this app.
Click the Download CSV icon to download this information as a CSV file.
- Click Attributes.
The Attributes tab lists the various attributes associated with this app.
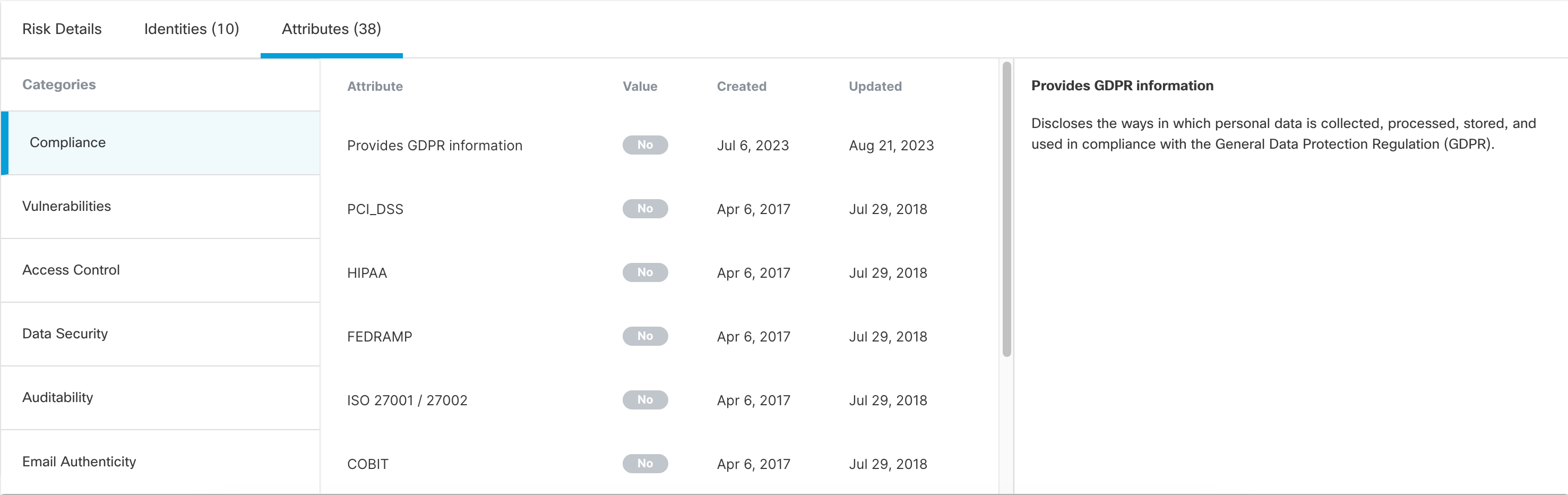
Attributes are divided into categories. Click a category name to view the attributes associated with it. (Not all applications will show all attribute categories.)
For each displayed attribute, Secure Access shows whether the attribute applies to the application and the dates when the attribute information was collected and updated. Use the attributes to evaluate the risk that the application will expose your environment to data breaches, identity theft, financial fraud, and other cyber threats.
The attribute categories are:
- Compliance attributes — Indicate whether the application complies with the requirements of a number of certifications such as GDPR, HIPAA, and FEDRAMP.
- Vulnerabilities attributes — Indicate whether the application is vulnerable to exploits that attackers could use to compromise the security of the affected systems, steal sensitive data, or cause other types of damage.
- Access control attributes — Indicate the methods the application supports to manage and restrict access based on a user's identity, role, and authorization level.
- Data security attributes — Indicate the practices and technologies the application uses to protect data from unauthorized access, use, disclosure, modification, or destruction.
- Auditability attributes — Indicate the abilities the application provides for an administrator to review the activity and transactions of a system, to ensure that it is operating in a compliant and secure manner.
- Email authenticity attributes — Indicate what methods the app provides to verify that email is actually from the sender that it claims to be from, and that the message has not been tampered with or altered in any way during transit.
Review Apps in the Apps Grid < View App Details > Change App Details
Updated 5 months ago