AD Connector Communication Flow and Troubleshooting
The Cisco Active Directory (AD) Connector is a Windows application and service that communicates with Cisco Secure Access and AD domain controllers. The Cisco AD Connector only syncs the required AD User and Group attributes with Secure Access.
The following information describes the communication flow between a Cisco AD Connector and AD domain controllers, the attributes that sync between AD, the AD Connector, and Secure Access, and the steps that you can take to troubleshoot your Cisco AD Connector deployment. The diagram includes the deployment of the Secure Access Virtual Appliance.
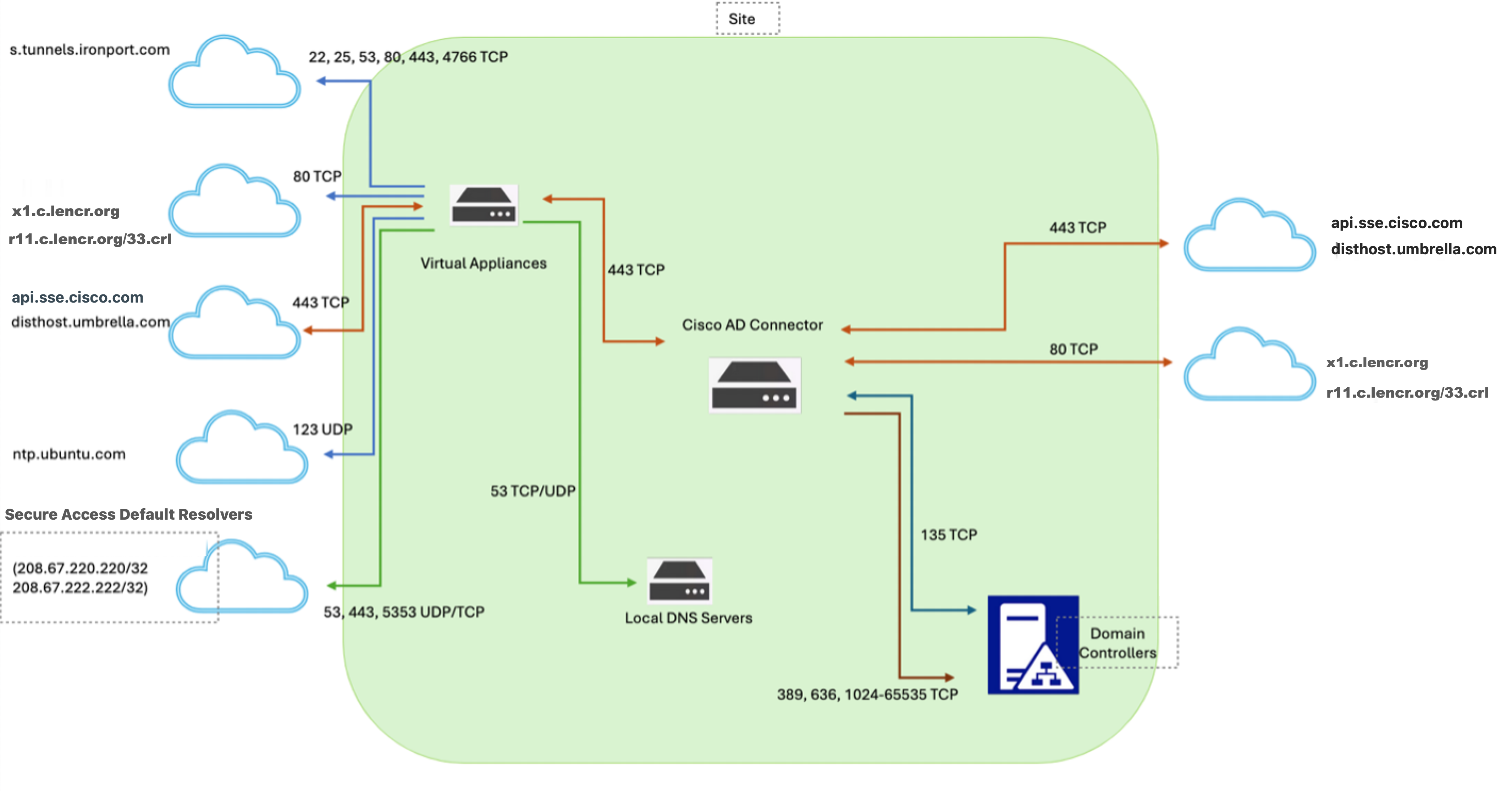
Table of Contents
Communication Flow
- The Cisco AD Connector first attempts to communicate to the AD domain controller over secure lightweight directory access protocol (LDAPS) on port 646. If unsuccessful, the Cisco AD Connector falls back to communicating over LDAP on port 389 using first Kerberos authentication and if that does not succeed, NTLM authentication (Windows NT LAN Manager) over LDAP.
- The Cisco AD Connector retrieves the AD Users, Groups, and Endpoint Devices details only. Secure Access stores these required attributes from each object:
cn—The common name.dn—The distinguished name.dNSHostName—The device name as it is registered in DNS.memberOf—The groups that include the user.objectGUID—The group ID of the object. This property is sent to Secure Access as a hash.primaryGroupId—The primary group ID that is available for Users and Groups.primaryGroupToken—The primary group token that is available only for Groups. Passwords or password hashes are not retrieved. Secure Access uses theprimaryGroupTokendata in the access policy and configuration and reporting. This data is also required for each user or per-computer filtering.sAMAccountName—The username that you use to sign into the Cisco AD Connector.userPrincipalName—The user's principal name.
Note: If there are updates, the Cisco AD Connector sends the AD data every five minutes using an HTTPS connection on TCP port 443. However, it can take an hour or longer for changes to reflect in Secure Access.
- The Cisco AD Connector stores the AD User and Group data locally in .ldif files.
The local AD User and Groups data is contained within this folder:
C:\\Program Files (x86)\\Cisco\\CiscoADConnector\\ADSync.Review the files in the .ldif files in the ADSync directory to confirm that the Cisco AD Connector synchronized the AD Users and Groups data to Secure Access.
Note: When you install the Cisco AD Connector, you have the option to turn off the local storage of
.ldiffiles.
Troubleshooting
Recommendations for troubleshooting the communications with the Cisco AD Connector.
Network Requirements
The Cisco AD Connector communicates with Secure Access and the deployed domain controllers. Ensure that you allow certain domains and services on your firewalls. For more information, see Network Requirements for Secure Access.
| Port and Protocol | Source | Destination | Note |
|---|---|---|---|
| 443/TCP | AD Connector | api.sse.cisco.com disthost.umbrella.com | - Initial registration with Secure Access - Automatic updates - Health status reporting in Secure Access |
| 80/TCP | AD Connector | x1.c.lencr.org r10.c.lencr.org r11.c.lencr.org/33.crl | Check for certificate revocations through the Certificate Revocation List (CRL). Certificate Distribution Points (CDPs) are dynamic and may change based on the certificate signing criteria. Note: The URLs for these partitioned CRLs generally follow the pattern: https://[intermediate_id].c.lencr.org/[crl_number].crl - [intermediate_id] refers to the specific intermediate certificate (e.g., r11, e1).- [crl_number]is the partition number for that intermediate (e.g., 1, 2, ..., 128). To retrieve the latest CRL CDP, run the following command: echo | openssl s_client -servername api.sse.cisco.com -connect api.sse.cisco.com:443 2>/dev/null | openssl x509 -noout -text | grep -oE 'URI:http[^[:space:]]+' | grep 'lencr.org' | sed 's/^URI://' |
| 389/TCP 636/TCP | AD Connector | Domain controller or domain | Sync with LDAP/LDAPS |
Note: The Digicert domains resolve to various IP addresses based on a CDN and are subject to change.
If you experience any issues communicating with Secure Access, we recommend that you check for any Layer-7 application proxies, which may block or drop data sent to Secure Access. A common case is the inspect feature on Cisco devices that communicate on DNS, HTTP, or HTTPS. For more information, see Cisco Security Appliance Command Line Configuration Guide, Version 7.2.
Restart the Active Directory Connector
You can restart the Cisco AD Connector service on the AD Connector server. Restarting the Cisco AD Connector triggers a full synchronization of the AD Users and Groups, not only the changes from the previous sync to Secure Access.
If your Cisco AD Connector is not in the Okay state, contact Support. For more information, see Contact Cisco Secure Access Support.
Change the Connector Account Password < AD Connector Communication Flow and Troubleshooting > Edit AD Authentication Properties
Updated 2 days ago
