Configure AD FS for SAML
Cisco Secure Access uses Security Assertion Markup Language (SAML) to authenticate and authorize web requests from user devices on networks and network tunnels with Web security enabled, and requests to private resources from user devices with Zero Trust Access (ZTA) enabled. To support SAML authentication and authorization, you must configure the integration of an SAML identity provider (IdP) in Secure Access.
Configure Active Directory Federation Services (AD FS) with Secure Access by uploading the AD FS XML metadata file to Secure Access, or alternatively add the AD FS metadata in Secure Access manually.
For information about provisioning users from AD FS to Secure Access, see Provision Users and Groups from Active Directory.
Table of Contents
- Prerequisites
- Procedure
- Test the Identity Provider Integration
- View the SAML Certificates in Secure Access
Prerequisites
- For information on prerequisites that apply to all SAML IdPs, see Prerequisites for SAML Authentication.
- We recommend that you bypass web traffic to the id.sse.cisco.com domain on the Secure Access secure web gateway (SWG).
Procedure
- Step 1 – Choose an Authentication Method
- Step 2 – Add an Identity Provider
- Step 3 – Add the Identity Provider's SAML Metadata to Secure Access
Step 1 – Choose an Authentication Method
- For more information, see Add User Authentication Profiles.
Step 2 – Add an Identity Provider
- For Identity Provider, choose ADFS. Secure Access supports various IdPs.
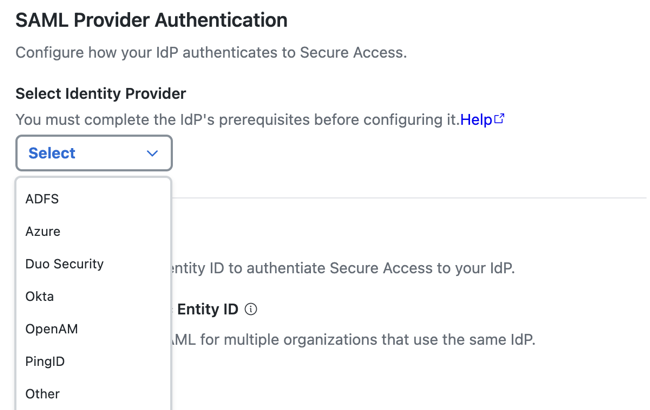
- (Optional) Enable an organization-specific entity ID.
- Organization-specific Entity ID—Choose this option when you have multiple Secure Access Orgs and need to configure SAML authentication for Secure Access Internet Security and Zero Trust (ZT) for these Orgs against the same IdP. The Secure Access SAML default common
EntityIDis saml.fg.id.sse.cisco.com. Secure Access allows you to override the default Secure Access SAML EntityID on a per-Org basis.
- Organization-specific Entity ID—Choose this option when you have multiple Secure Access Orgs and need to configure SAML authentication for Secure Access Internet Security and Zero Trust (ZT) for these Orgs against the same IdP. The Secure Access SAML default common
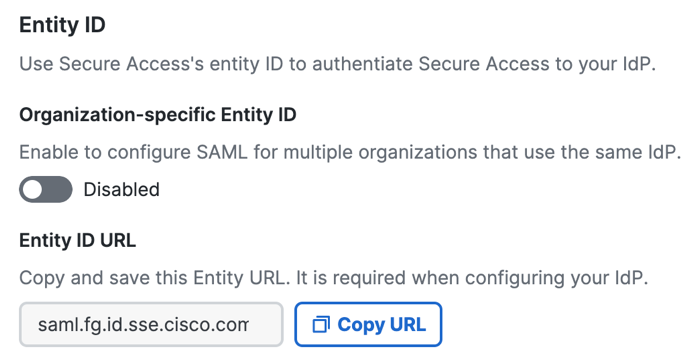
- For Entity ID URL, click Copy URL to make a local copy of the Secure Access Entity ID URL. The Secure Access SAML default common
EntityIDis saml.fg.id.sse.cisco.com.
- Choose a time interval when a user must authenticate with Secure Access, or select Never.
The time intervals are: Daily, Weekly, or Monthly.
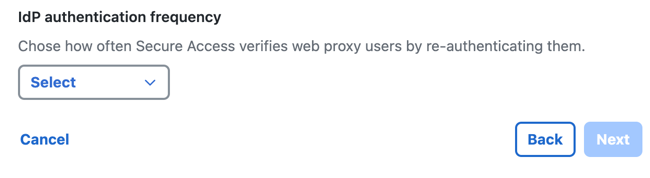
- Click Next.
Step 3 – Add the Identity Provider's SAML Metadata to Secure Access
Download the Secure Access Metadata XML file and use the service provider file to configure your instance of AD FS.
The Secure Access service provider metadata includes the service provider Issuer ID, the assertion consumer endpoint URL, and the SAML request signing certificate from Secure Access. The Secure Access metadata is required when configuring your IdP.
Your IdP must send the Cisco Secure Access User principal name in the NameID attribute in the SAML assertion.
- Step 3a – Download the Secure Access Service Provider files
- Step 3b – Add the Secure Access Service Provider Metadata to AD FS
- Step 3c – Add the AD FS SAML Metadata to Secure Access
Step 3a – Download the Secure Access Service Provider files
Note: Encrypted SAML assertions are a compliance standard in many industries and mitigate the risk of intercepted SAML assertions. For more information, see Prerequisites for SAML Authentication.
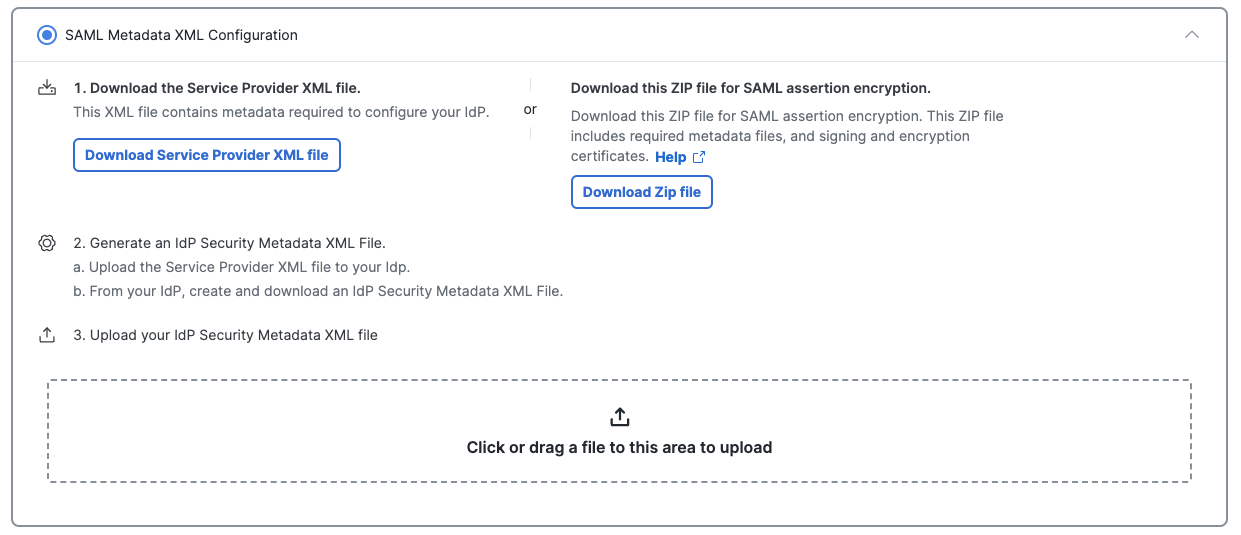
- Check SAML Metadata XML Configuration or Manual Configuration.
- Choose between unencrypted or encrypted SAML assertions.
- Click Download Service Provider XML file for the metadata XML file with the Secure Access root certificate that supports unencrypted SAML assertions, or
- Click Download Zip file for the metadata XML file and signing and encryption certificate files required for encrypted SAML assertions. This metadata XML file includes the root certificate metadata for both the signing and the encryption certificates.
- Open the Cisco_SSE_SP_Metadata XML file.
- Copy the certificates from the Cisco_SSE_SP_Metadata XML file to a new file and save. Use the certificate file in the next step when you create the app integration in AD FS.
Step 3b – Add the Secure Access Service Provider Metadata to AD FS
Add the Secure Access service provider metadata to your instance of AD FS, then download the IdP metadata file to finish configuring Secure Access in the next step.
Contact Microsoft for assistance. For more information on configuring your IdP, exporting your IdP metadata, obtaining your IdP details, or downloading your IdP's signing certificate, refer to your vendor's documentation.
- Log into AD FS and navigate to Server Manager > Tools > AD FS Management.
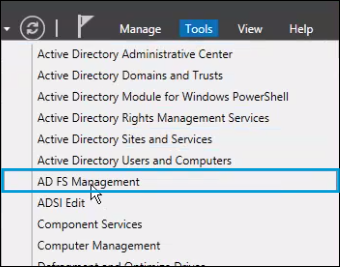
- In the AD FS Manager, right-click on Trust Relationships and navigate to Relying Party Trusts > Add Relying Party Trust and select Start.
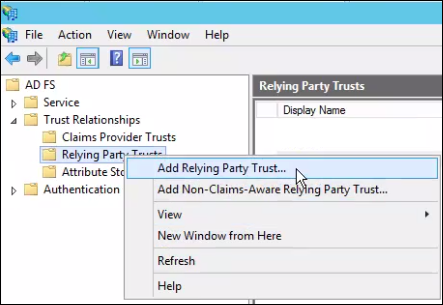
- Choose Import data about the relying party from a file and browse for the metadata.xml file downloaded from Secure Access.
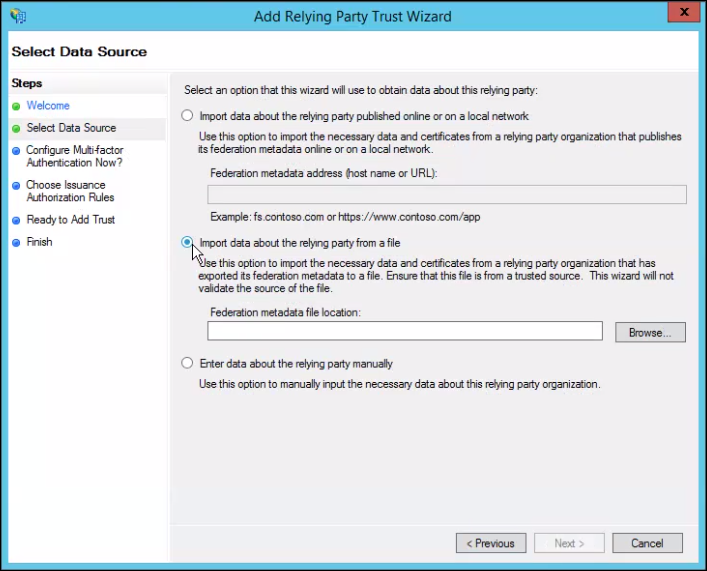
- For Display name, provide a meaningful name for the trust connection, and then click Next.
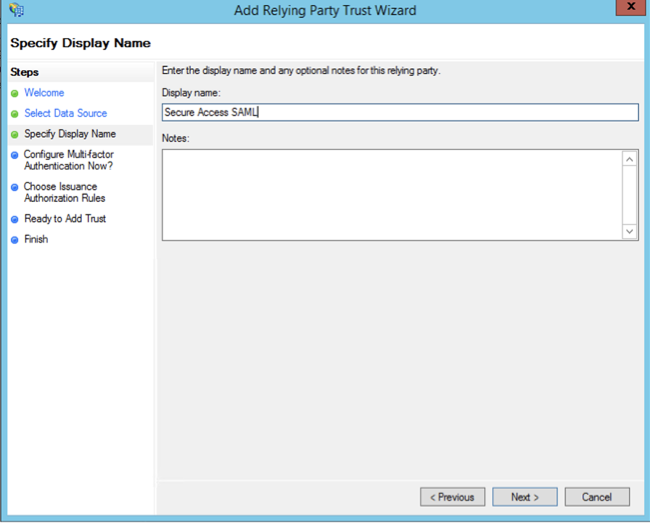
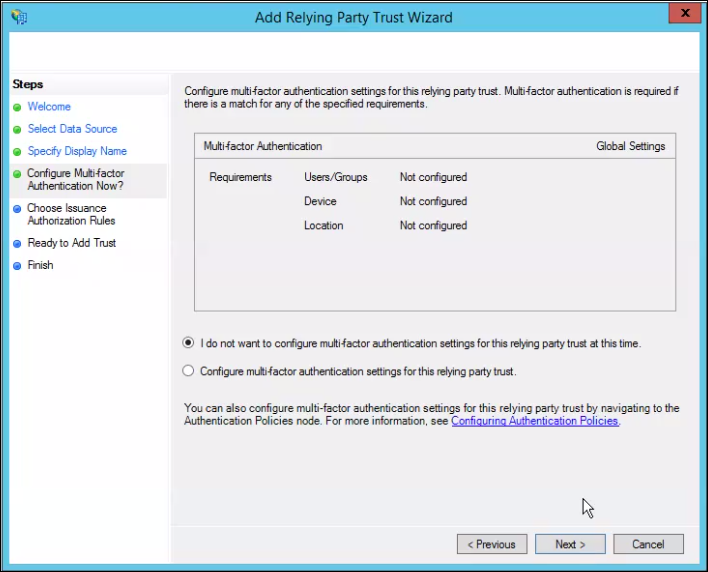
- Select I do not want to configure multi-factor authentication settings for this relying party trust at this time and click Next.
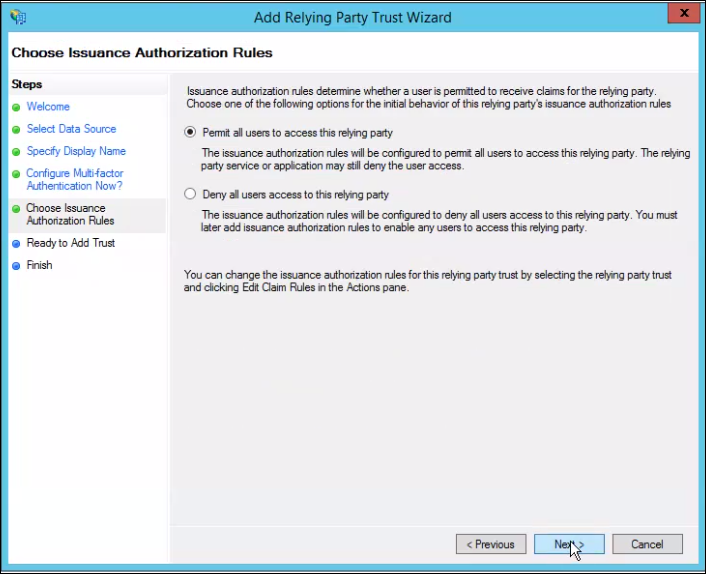
- Select Permit all users to access relying party and click Next.
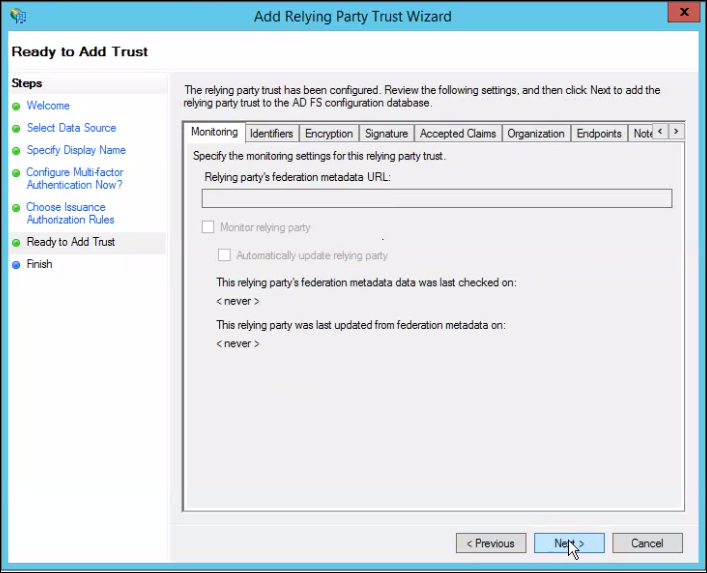
- Verify settings and click Next.
- Right-click on the recently created relaying party and select Edit Claim Rules.
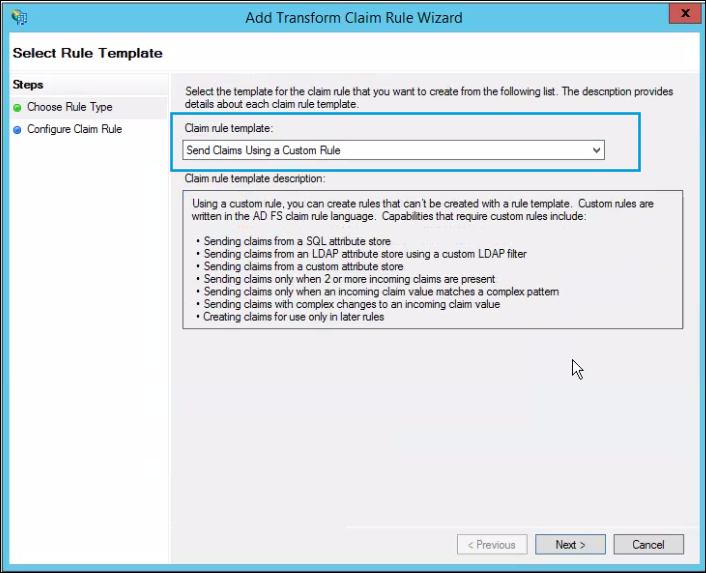
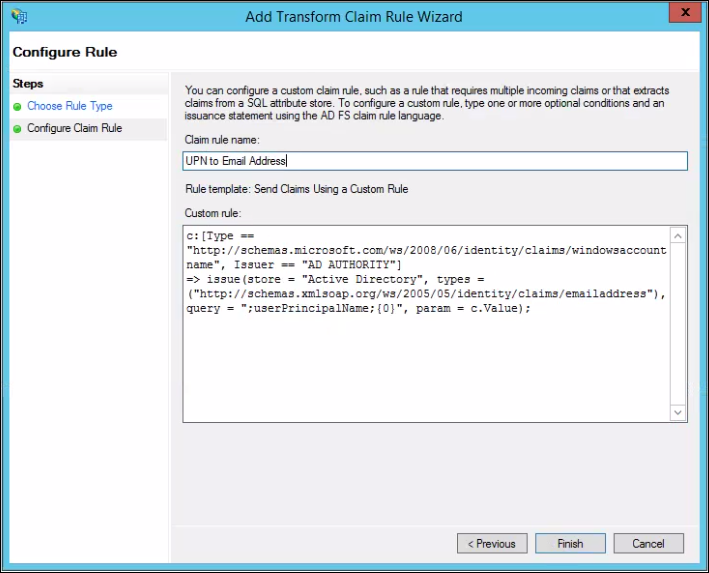
- Under Issuance Transform Rules, click Add Rule, then choose Send Claims Using a Custom Rule with the following configuration:
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"), query = ";userPrincipalName;{0}", param = c.Value);
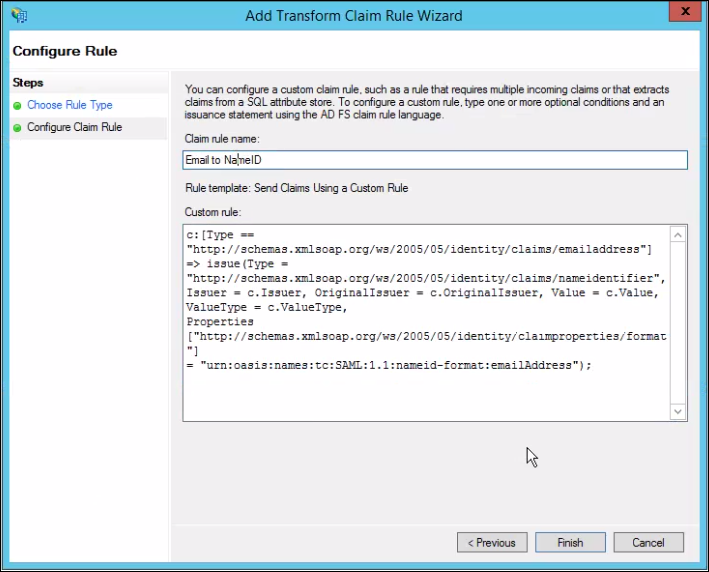
- Repeat the previous step with the following configuration.
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");
- Download the AD FS metadata XML file and save the file on your local system.
Step 3c – Add the AD FS SAML Metadata to Secure Access
If you used SAML Metadata XML Configuration in step 3a above, upload your configured AD FS SAML Metadata XML file to Secure Access, then click Done.
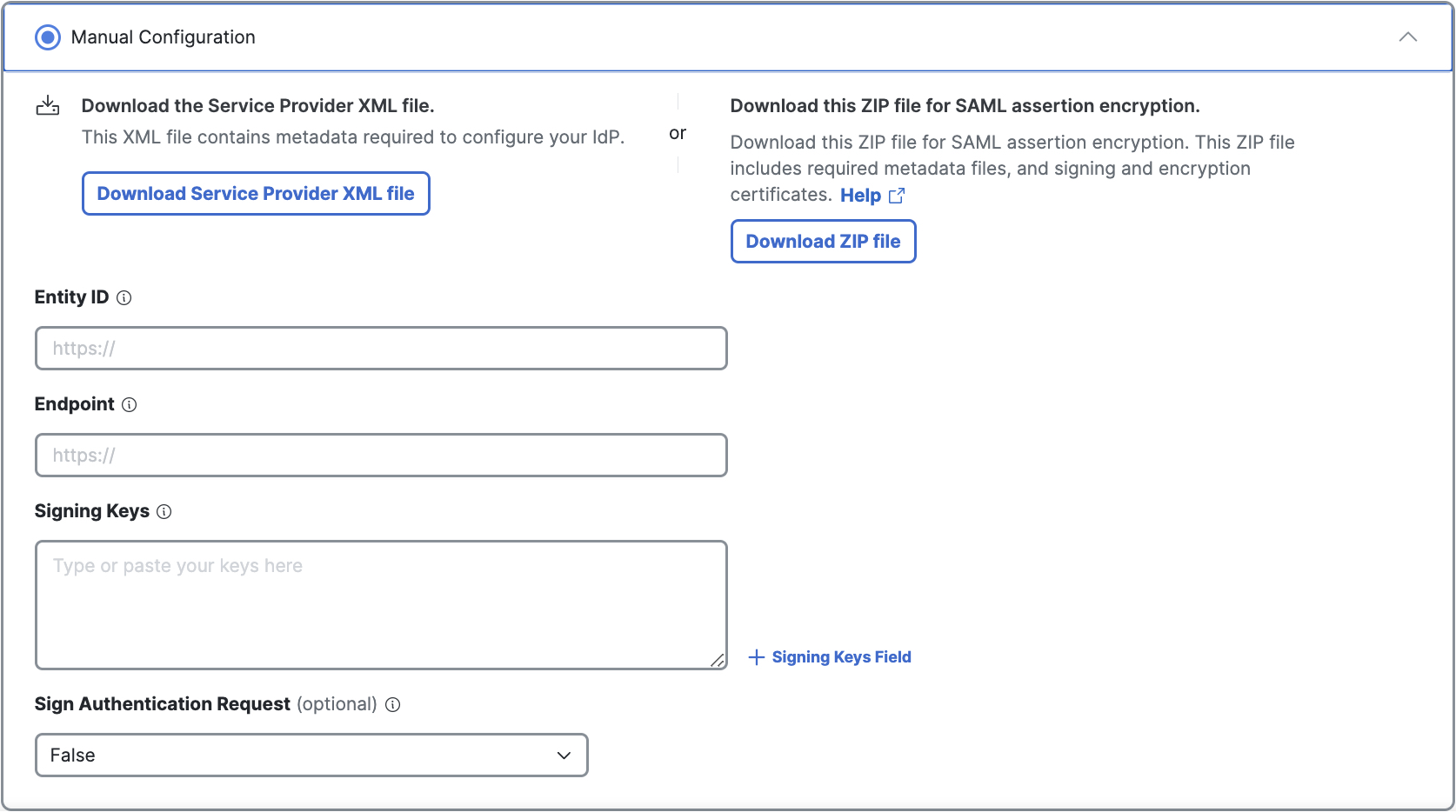
If you used Manual Configuration in Step 3a above, enter your AD FS SAML metadata for the following Secure Access settings, then click Done.
- Entity ID—A globally unique name for an identity provider.
- Endpoint—The URL used to communicate with your identity provider.
- Signing Keys—Your identity provider’s x.509 certificate that is used to sign the authentication request.
- Signed Authentication Request (optional)—Choose whether you can sign the authentication request for the IdP.
Test the Identity Provider Integration
To complete the integration of the SAML IdP with Secure Access, evaluate the single sign-on authentication through the IdP. For more information, see Test SAML Identity Provider Integration.
View the SAML Certificates in Secure Access
Once you have completed the integration of an SAML IdP in Secure Access, you can manage the root certificates used in SAML authentication for Secure Access (service provider) and the SAML IdP. For more information, see Manage Certificates.
Configure Okta for SAML < Configure AD FS for SAML > Configure Duo Security for SAML
Updated 7 months ago
