Configure Integrations with SAML Identity Providers
Cisco Secure Access enables you to connect securely to the internet, web resources in private and public clouds, your organization's on-premises private resources, and Software as a Service (SaaS) applications. To create more granular access rules and to authenticate users connecting from networks or network tunnels or with Zero Trust Access (ZTA), you can integrate a Security Assertion Markup Language (SAML) identity provider (IdP) in Secure Access. The SAML IdP provides single sign-on (SSO) authentication for users and Secure Access establishes a trust relationship with the IdP.
Secure Access integrates with various SAML 2.0 IdPs: Azure Active Directory (Azure AD), Duo, Okta, Ping Identity, Active Directory Federation Services (AD FS), and OpenAM.
Once users in your organization are configured to use SSO, the SAML IdP manages all authentication requests. A user authenticates to the SSO IdP, automatically signs in to Secure Access, and is authorized to connect to certain resources.
Use Cases
Secure Access uses SAML authentication to provide seamless connections to web resources and private resources from user devices.
Secure Internet Access—Networks and Network Tunnels
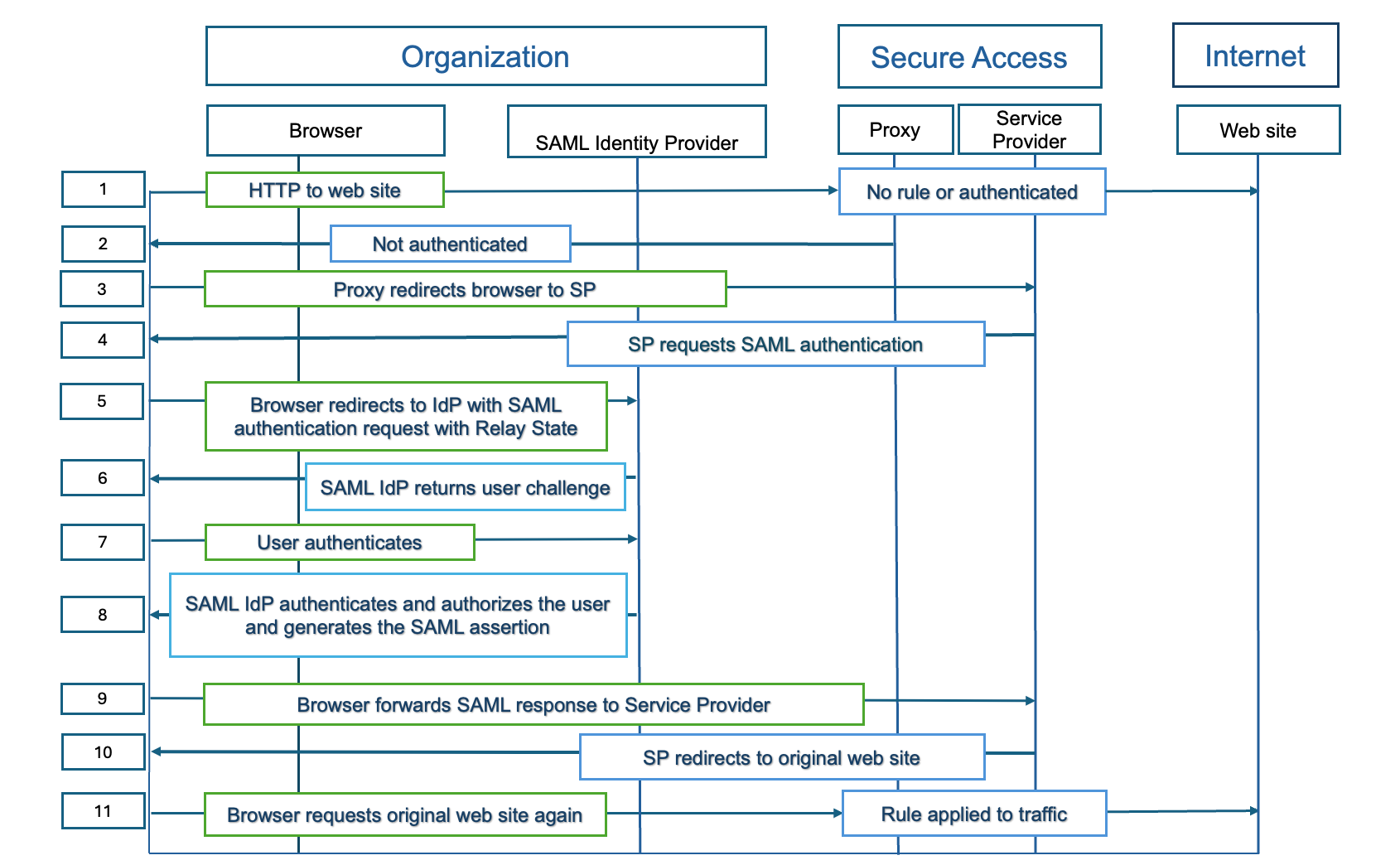
- Secure web gateway—The Cisco Secure Access secure web gateway (SWG) uses SAML to authenticate and authorize web requests from user devices sent over networks and network tunnels. Internet traffic is protected by the Secure Access DNS and Web security layers. The Secure Access SWG is not an open proxy. Secure Access must trust the source that forwards web traffic to it, whether the source is a network or network tunnel.
- SAML uses a cookie surrogate. When a browser sends an HTTP request, Secure Access checks if the request contains the HTTP Cookie header. If the cookie is not set, Secure Access can not authenticate the user.
- Web Security SAML Data Flow.
Zero Trust Access with the Cisco Secure Client
- Secure Access Zero Trust (ZT) uses SAML to authenticate and authorize requests to an organization's private resources from a user device where the Cisco Secure Client is deployed.
Zero Trust Access with an Unmanaged Device
- Secure Access Zero Trust (ZT) uses SAML to authenticate and authorize requests to an organization's private resources from an unmanaged device.
Configure Identity Providers for SAML Authentication
- Configure Microsoft Entra ID for SAML
- Configure Okta for SAML
- Configure AD FS for SAML
- Configure Duo Security for SAML
- Configure Ping Identity for SAML
- Configure OpenAM for SAML
Configure Microsoft Entra ID for Open ID Connect < Configure Integrations with SAML Identity Providers > Prerequisites for SAML Authentication
Updated 6 months ago
