Configure Tunnels with Cisco Catalyst SD-WAN
Follow these steps to connect a Cisco IOS XE Catalyst SD-WAN device through an IPsec (Internet Protocol Security) IKEv2 (Internet Key Exchange, version 2) tunnel to Cisco Secure Access.
For more information about Cisco Catalyst SD-WAN devices and related topics, see Cisco's SD-WAN product documentation.
Table of Contents
- Prerequisites
- Configure Tunnel in Secure Access
- Configure Cisco Catalyst SD-WAN Templates
- Configure Static Routes
- Verify Tunnel Status
Prerequisites
- You must enable NAT in the feature template that faces the internet.
- You can access the Cisco Catalyst SD-WAN (vManage) console with a web browser. By default, the HTTPS port is 8443, but this may vary based on how your Cisco Catalyst SD-WAN (vManage) is configured.
Note: If you get a "Not Secure" warning when accessing the link, you can ignore it. When the Cisco Catalyst SD-WAN (vManage) login screen appears, enter your credentials.
Step 1: Add a Network Tunnel Group in Secure Access
Secure Access enables fast, reliable, and secure private network connections to your applications through IPsec (Internet Protocol Security) IKEv2 (Internet Key Exchange, version 2) tunnels.
Tunnels and tunnel groups are core concepts in managing connections between your data centers and Cisco Secure Access. A network tunnel group provides the framework for establishing tunnel redundancy and high availability. Connect tunnels to the hubs within a network tunnel group to securely control user access to the Internet and private resources.
- Follow the steps in Add a Network Tunnel Group.
- Make note of the Tunnel ID and Passphrase you enter when configuring the network tunnel group. These values are needed when you configure your Catalyst SD-WAN tunnel.
Note: Secure Access provides the option to download a CSV file with the network tunnel group details. - Remember to select Static routing under routing options. Only static routing is supported.
The new network tunnel group appears in the Secure Access dashboard as Disconnected, and with the Primary Hub and Secondary Hub status showing as Hub Down. The network tunnel group status is updated once it is fully configured and connected with Catalyst SD-WAN.
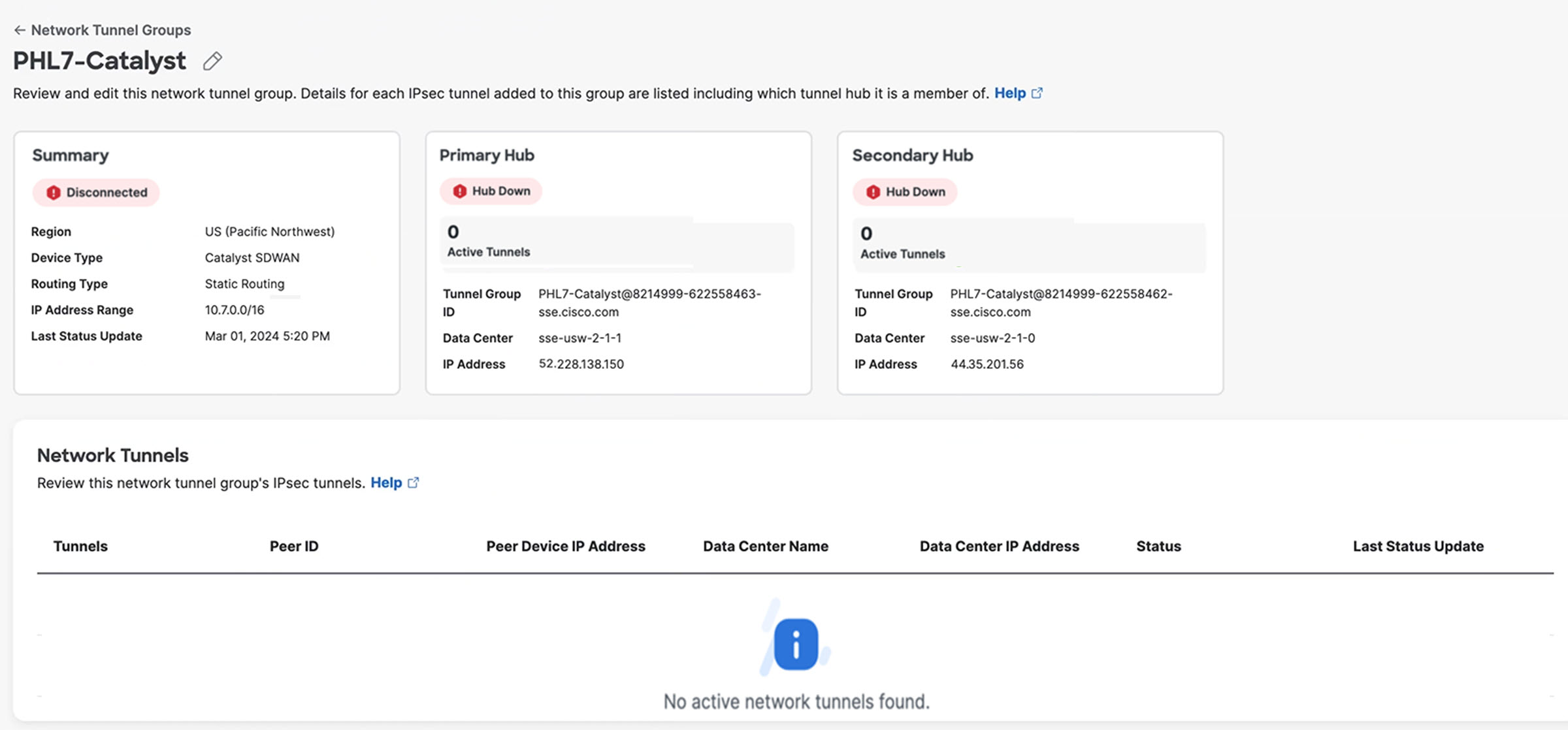
See the Verification and Troubleshooting section for additional information about how to evaluate the network tunnel group status.
Step 2: Configure Cisco Catalyst SD-WAN Templates
Configure a Catalyst SD-WAN tunnel to connect a Catalyst SD-WAN device to Cisco Secure Access.
In Cisco Catalyst SD-WAN Manager, all the features are configured through templates. Once the Cisco Catalyst SD-WAN devices are registered with Cisco Catalyst SD-WAN Manager, you cannot configure anything through the CLI.
You can use the Cisco Catalyst SD-WAN Manager Device and Feature templates to establish a tunnel from the device. First define the device template and then the feature template.
In SD-WAN Manager version 20.9, the SIG template is divided into several sections:
- Device Type, Template Name, Description, and SIG Provider (Umbrella, Zscaler, or Generic).
Note:
In version 20.4/17.4, the only two tunnel types that are offered are Umbrella and Third Party. You can configure Secure Access manual tunnels (IPSec or GRE) using the Third Party option. Starting in 20.5/17.5, the three tunnel types that are offered are Umbrella, Zscaler, and Generic. To configure IPSec or GRE Secure Access tunnels, choose the Generic option. You can configure Secure Access manual and automatic tunnels (IPSec or GRE) using the Generic option. Secure Access recommends you use automatic tunnels if available.
- Tracker: Allows you to configure custom L7 health check tracker information.
- Configuration: Allows you to specify different tunnel type (IPSec or GRE) and other tunnel characteristics, such as
tunnel name, tracker name, tunnel source, whether the tunnel is attached to a primary or secondary data center
(which is specified or discovered later) and advanced options, like IP MTU and other tunnel settings. - High Availability: Allows you to choose up to 4 active tunnels or 4 active/standby tunnel pairs by choosing the
tunnels defined in the Configuration section under the Active or Backup column. You can also modify traffic ratios
for the tunnels. - Advanced Settings (if applicable): Allows you to define primary or secondary data centers and Secure Access location name if desired, and advanced Secure Access settings (XFF Forwarding, Enable IPS Control, etc).
Define the Feature Template
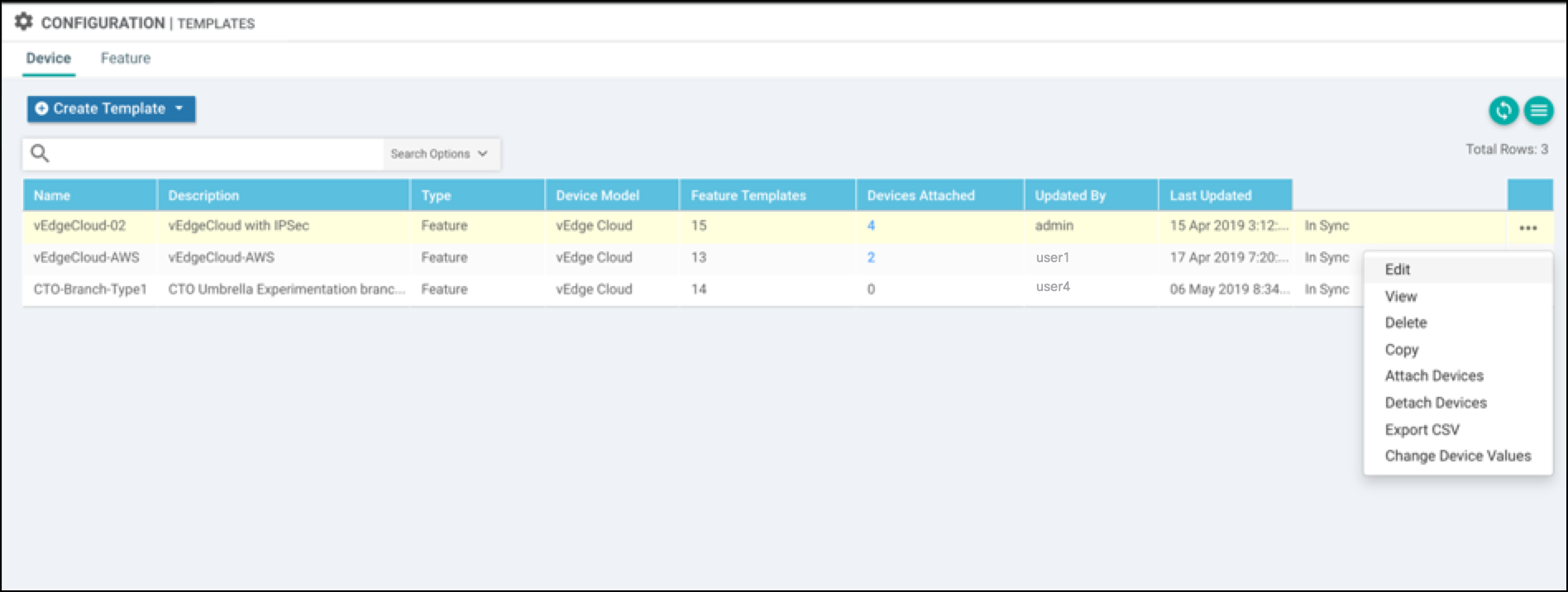
- Log into the Cisco Catalyst SD-WAN Manager console and navigate to Configuration > Templates.
- Confirm that the Feature Templates tab is selected, then click Add Template.
- Choose the device for which you are creating the template.
- Under VPN, click Cisco Secure Internet Gateway (SIG).
- Under Select Services select device types, then choose VPN Interface IPSec WAN.
- Configure Tunnel Parameters:
a. Choose a template name and description for the Tunnel interface.
b. Under Basic Configuration, set Shutdown to the global option and choose NO.
c. Choose the Interface Name from 1 to 255. For example,ipsec1.
d. Configure the IPv4 address by selecting the Global attribute and set the IP.
e. Set the IPSec Source Interface toge0/0. This must be the WAN interface in VPN 0, which has the internet connectivity.
f. Set the IPSec Destination to the closest data center).
g. Dead Peer Detection Value: Leave this at the default setting unless you have a specific requirement otherwise.
- Choose the Global Attribute to change any IKE and IPSec defaults:
IKE Settings
- Set the IKE Version to 2.
- Set the IKE Rekey Interval to 28800.
- Leave the default Cipher Suite, which is AES-256-CBC-SHA1.
- Set the IKE DH Group to 14 2048-bit Modulus.
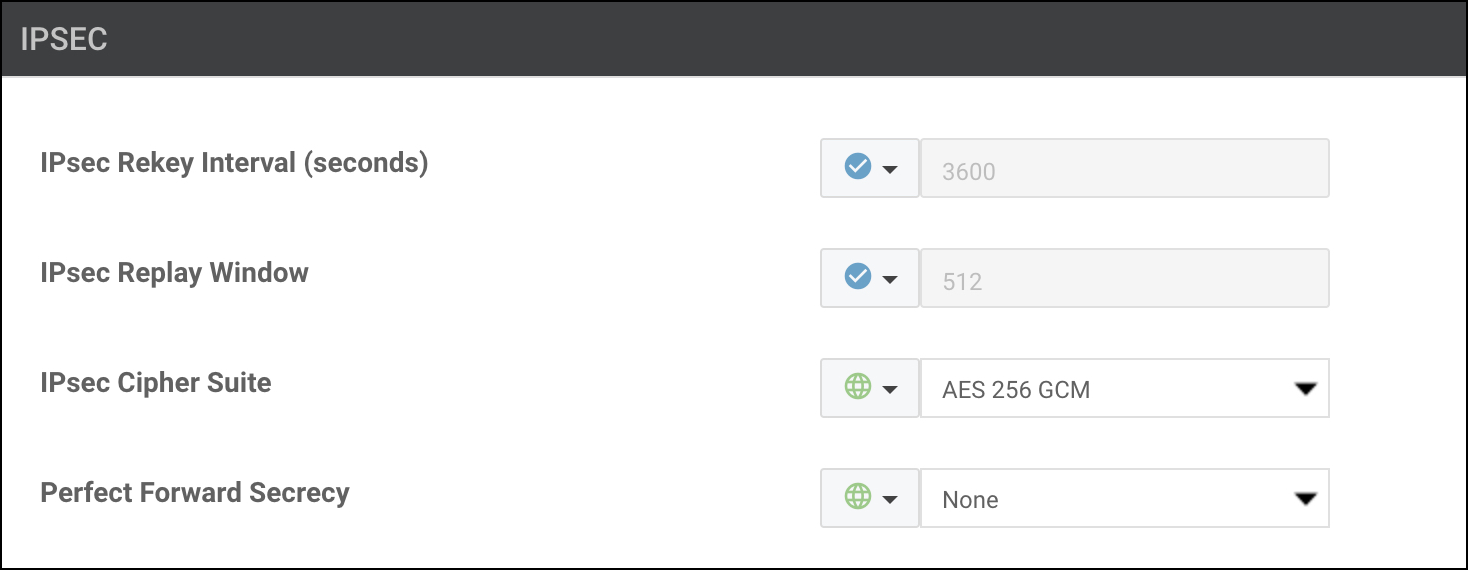
IPsec Settings
- Leave the IPsec Rekey Interval & Replay Window values at their defaults.
- Use the default Cipher Suite
AES 256 GCM. - Set the Perfect Forward Secrecy value to "NONE".
Cipher Suite Encryption
If performance is an issue with the default cipher, both
AES 256 CBC SHA1andNull SHA1are also supported. You can test these to determine whether one offers better performance for a particular platform. Note thatNull SHA1isn't necessarily faster than the defaultAES 256 GCMbecause of the cost of the SHA1 hashing. In addition,Null SHA1is not recommended due to security concerns of unencrypted transport.
- Click Update to save the configuration template.
Add the IPsec Interface Template
- Navigate to Configuration > Templates > Device and then choose the device template for the CDFW tunnel.
- Select Edit from the rightmost dropdown menu.
- Add the VPN IPSec tunnel interface in the VPN 0 Transport & Management VPN section.
Choose the VPN Interface IPSec that you added as part of the feature template.
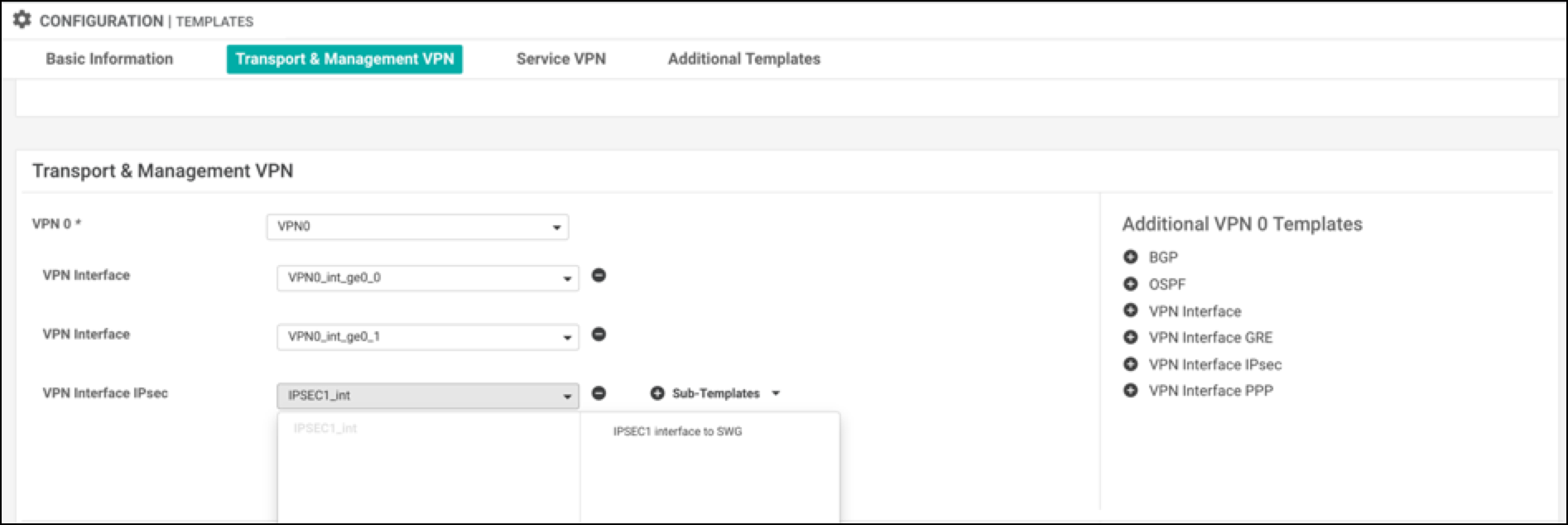
- Click Update. A success message appears.
Configure Static Routes
After configuring a template, you need to add static routes from the service VPN to redirect the traffic through the IPSec tunnel to CDFW headend.
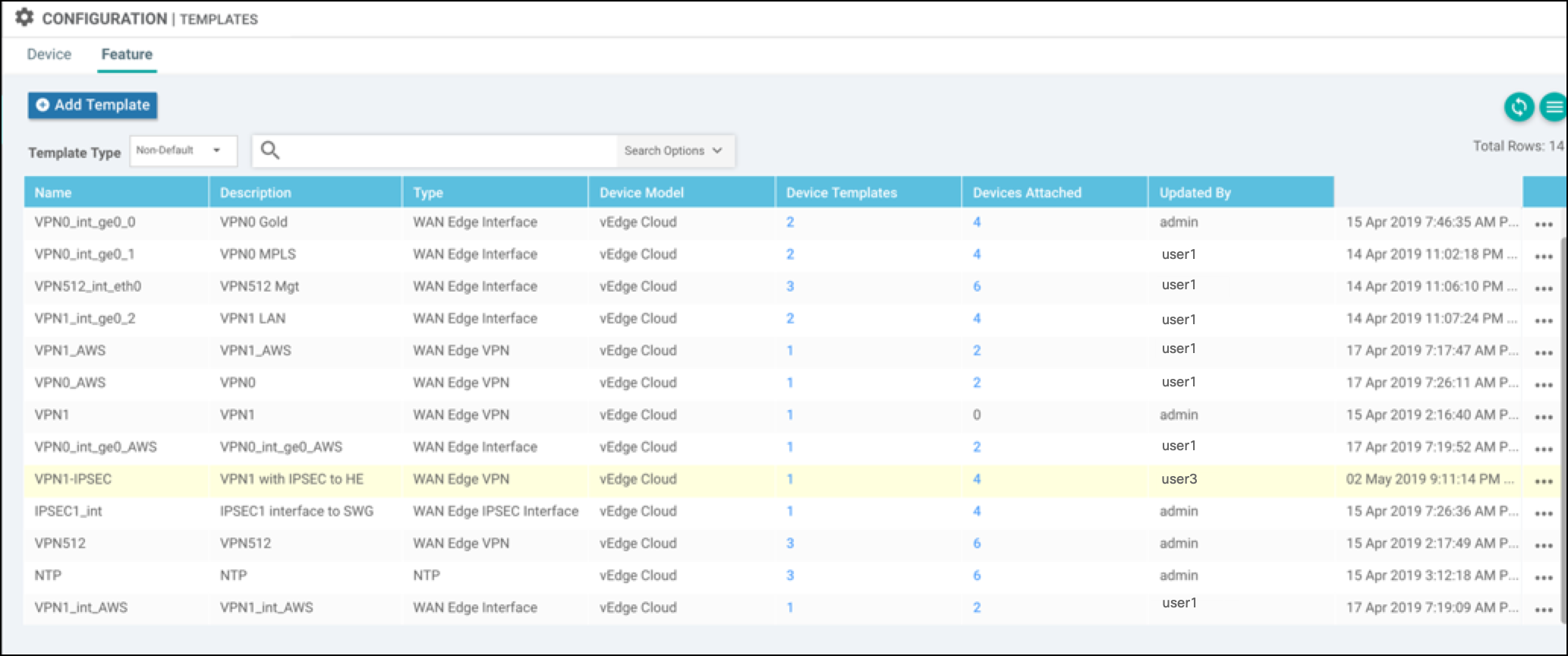
- Navigate to Configuration > Templates > Feature.
- Right-click the right most column, then edit the template to add IPSec route 0.0.0.0/0 via IPSec1 Tunnel interface.
- Add one more IPsec Tunnel interface (for example, IPSec2), and set that as the secondary tunnel interface.
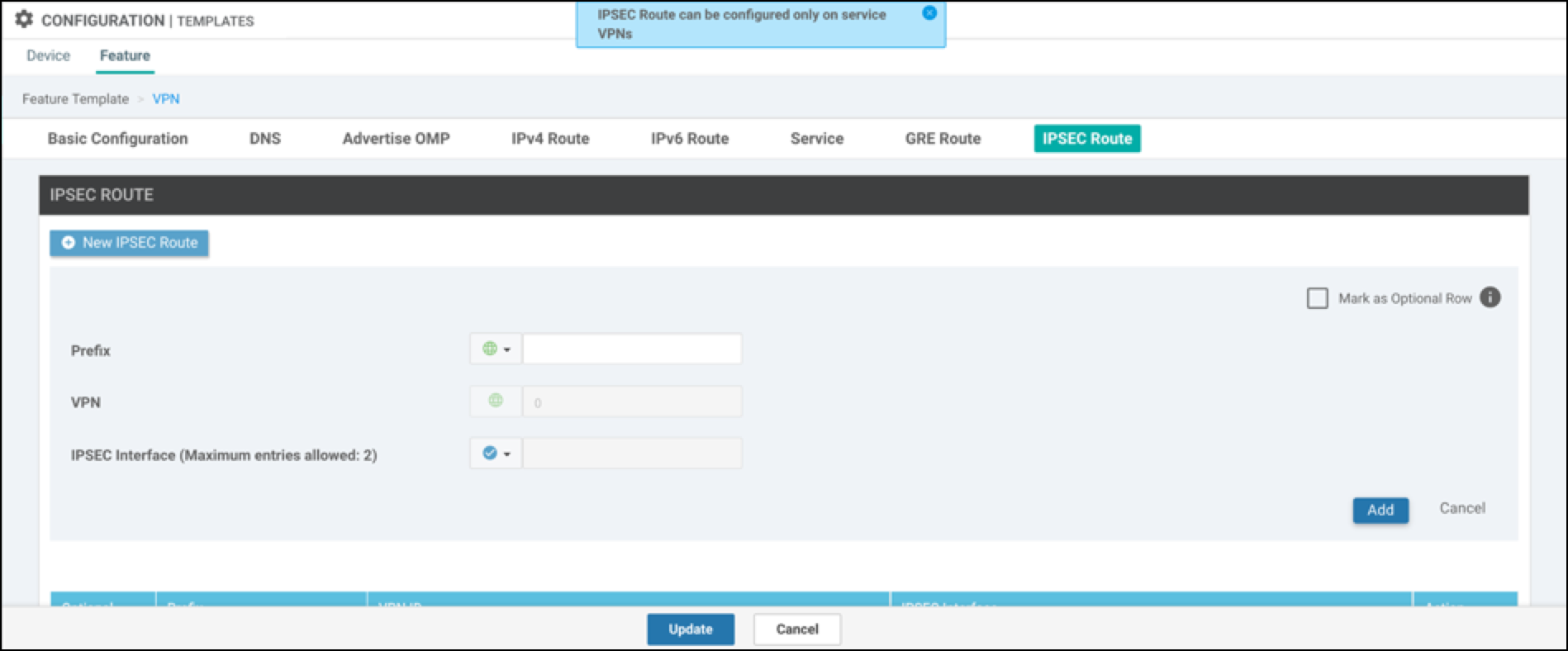
In this example, the default IPsec route is set to the ipsec1 tunnel interface.
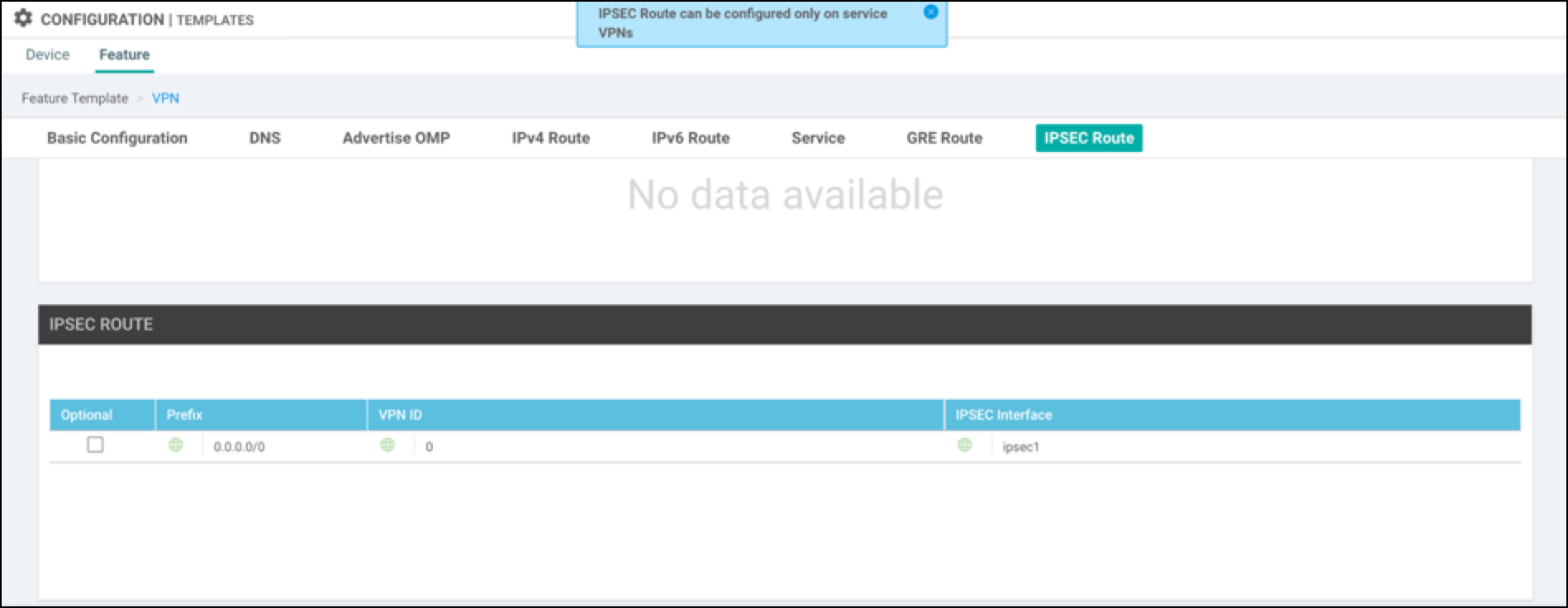
- Save configuration changes.
Verify Tunnel Status
- Log into the Cisco Catalyst SD-WAN (vManage) console and navigate to Monitor > Network > vEdge > Device.
- Choose a device, then choose Interface to check the status of the IPSec tunnel for ipsec1.
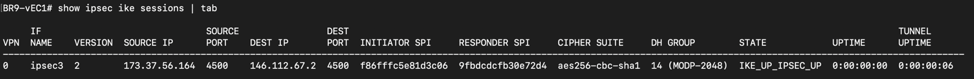
Alternatively, the following is an example of checking the tunnel status through the CLI.
Dynamic Routing with BGP < Configure Tunnels with Cisco Catalyst SD-WAN > Configure Tunnels with Cisco ISR
Updated 10 days ago
