Configure a Site-to-Site VPN tunnel with Microsoft Azure
This document explains how to deploy a site-to-site (S2S) VPN tunnel from Azure Virtual Network to Cisco Secure Access. An Azure S2S VPN in Secure Access will support the following:
- Tunnel redundancy with high availability for branch site connections to Secure Access and your Azure virtual network. For more information, see Throughput and Multiple Tunnels and Failover for Branch Connections in Secure Access Data Centers.
- Connection over IPsec (Internet Protocol Security) with authentication negotiated and traffic encrypted by IKEv2 (Internet Key Exchange, version 2). For more information, see Supported IPsec Parameters.
- Static or dynamic (BGP) routing. For more information, see Routing Options and Guidelines.
Table of Contents
- Overview
- Prerequisites
- Configure S2S Tunnels with Static Routing
- Configure S2S Tunnels with Dynamic Routing with BGP
- What to do next
Overview
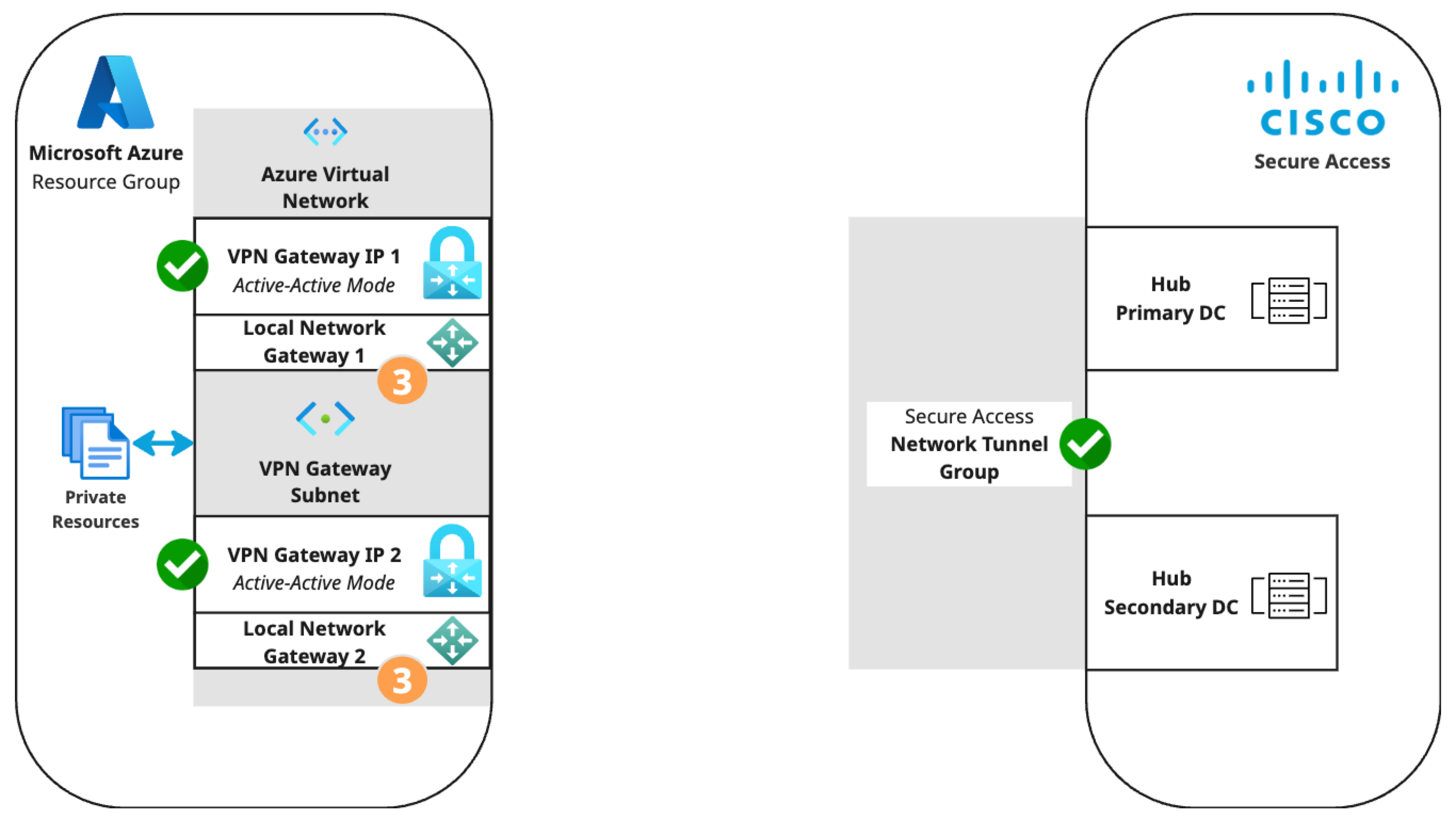
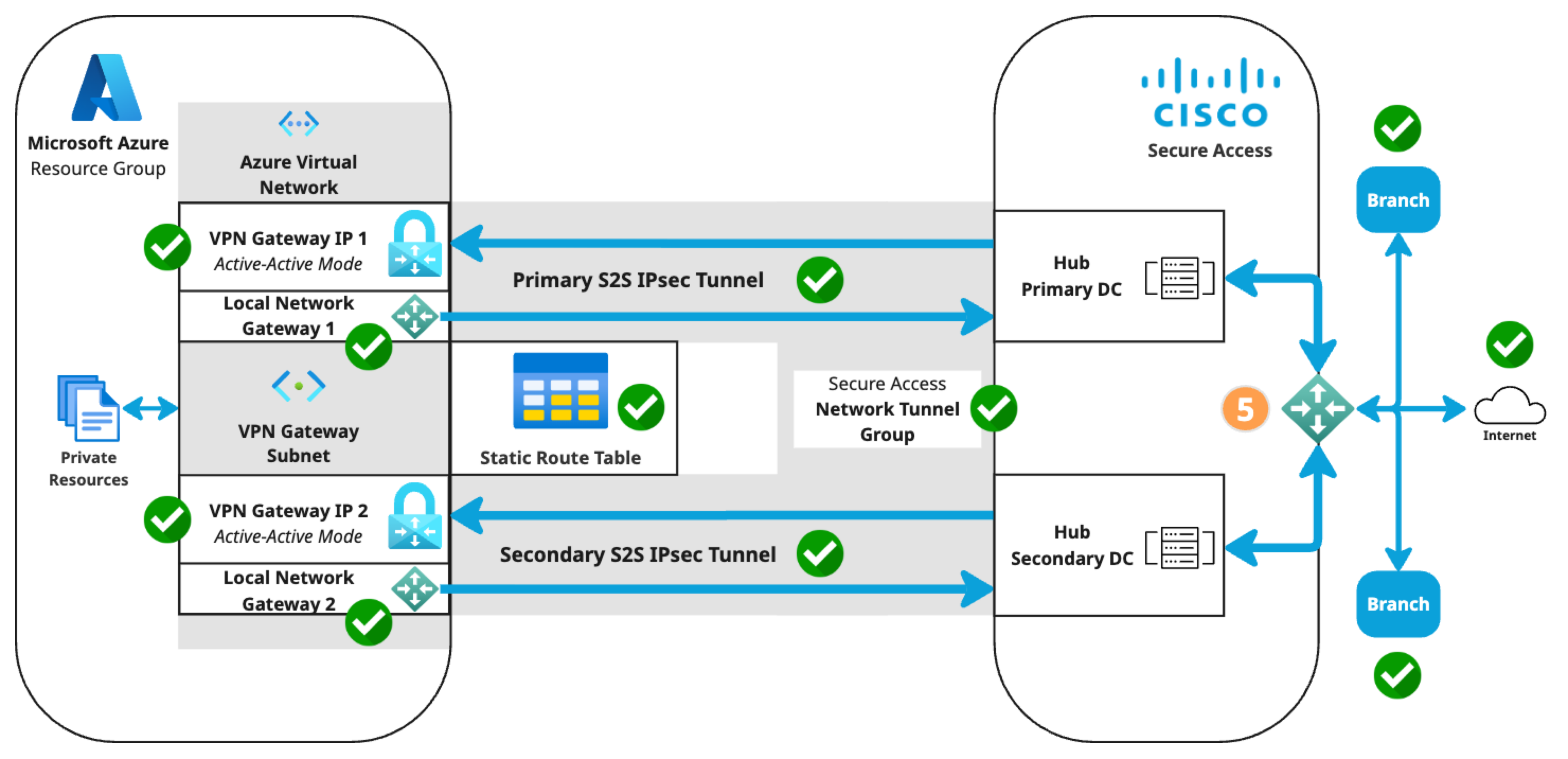
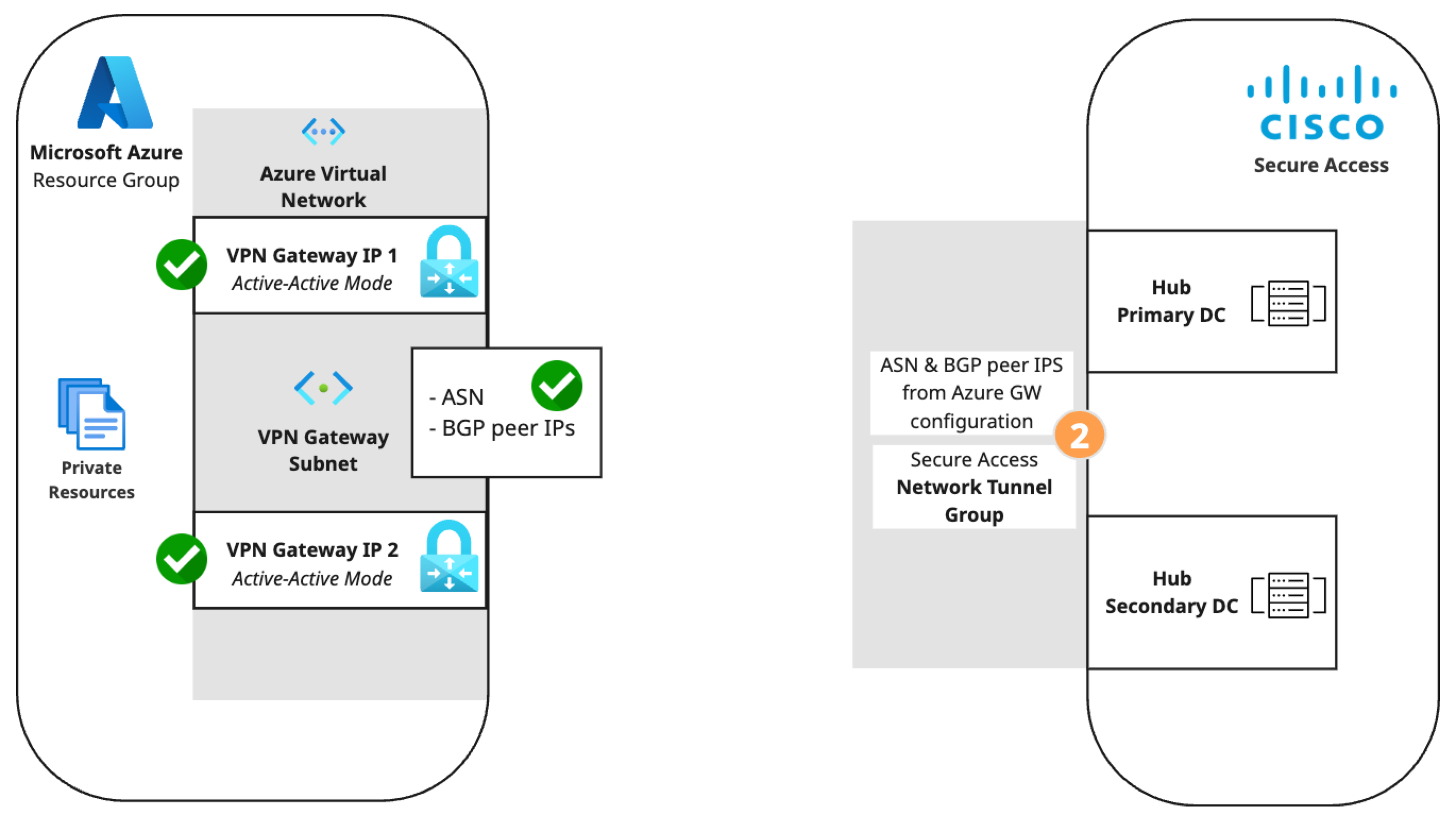
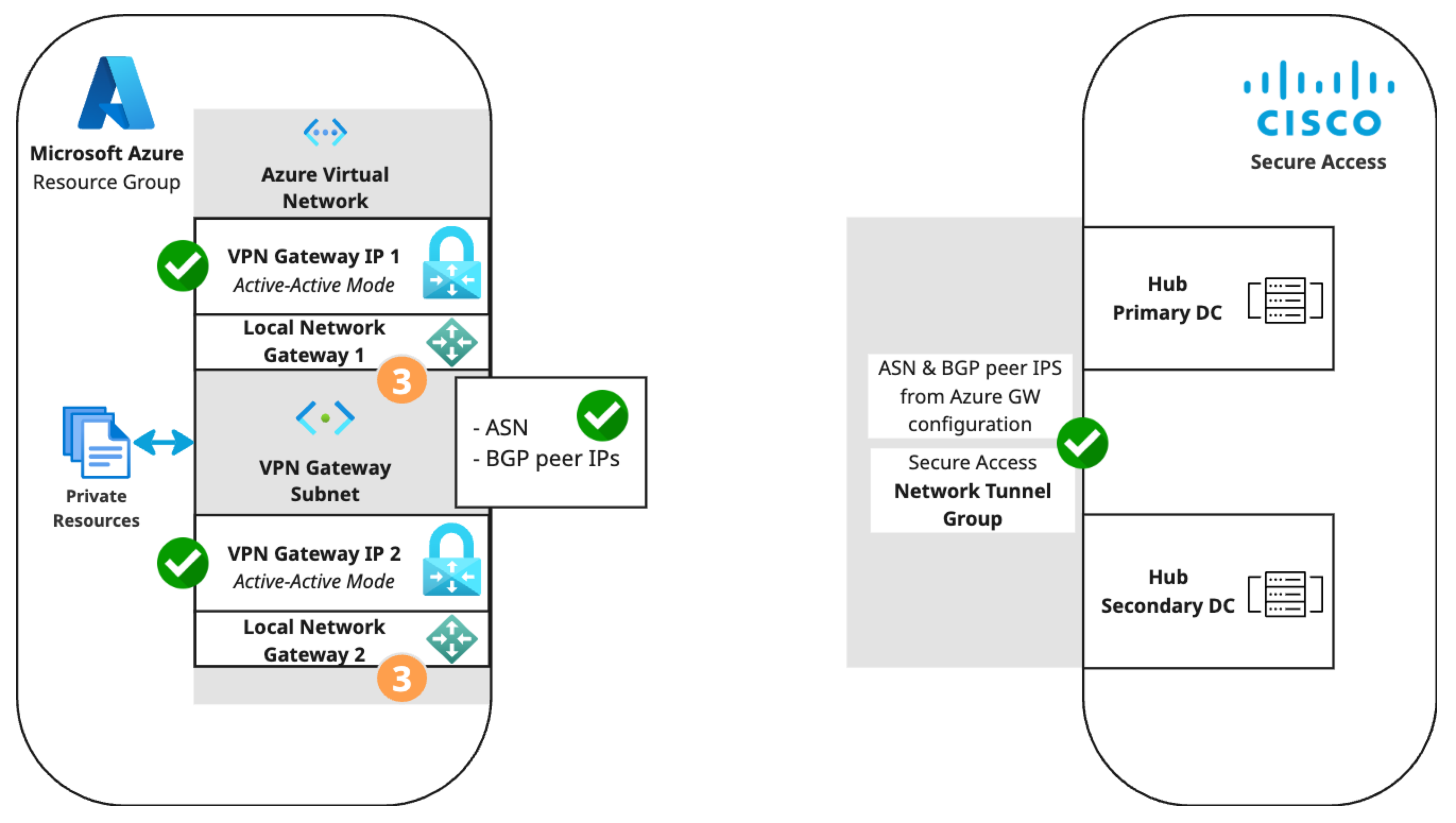
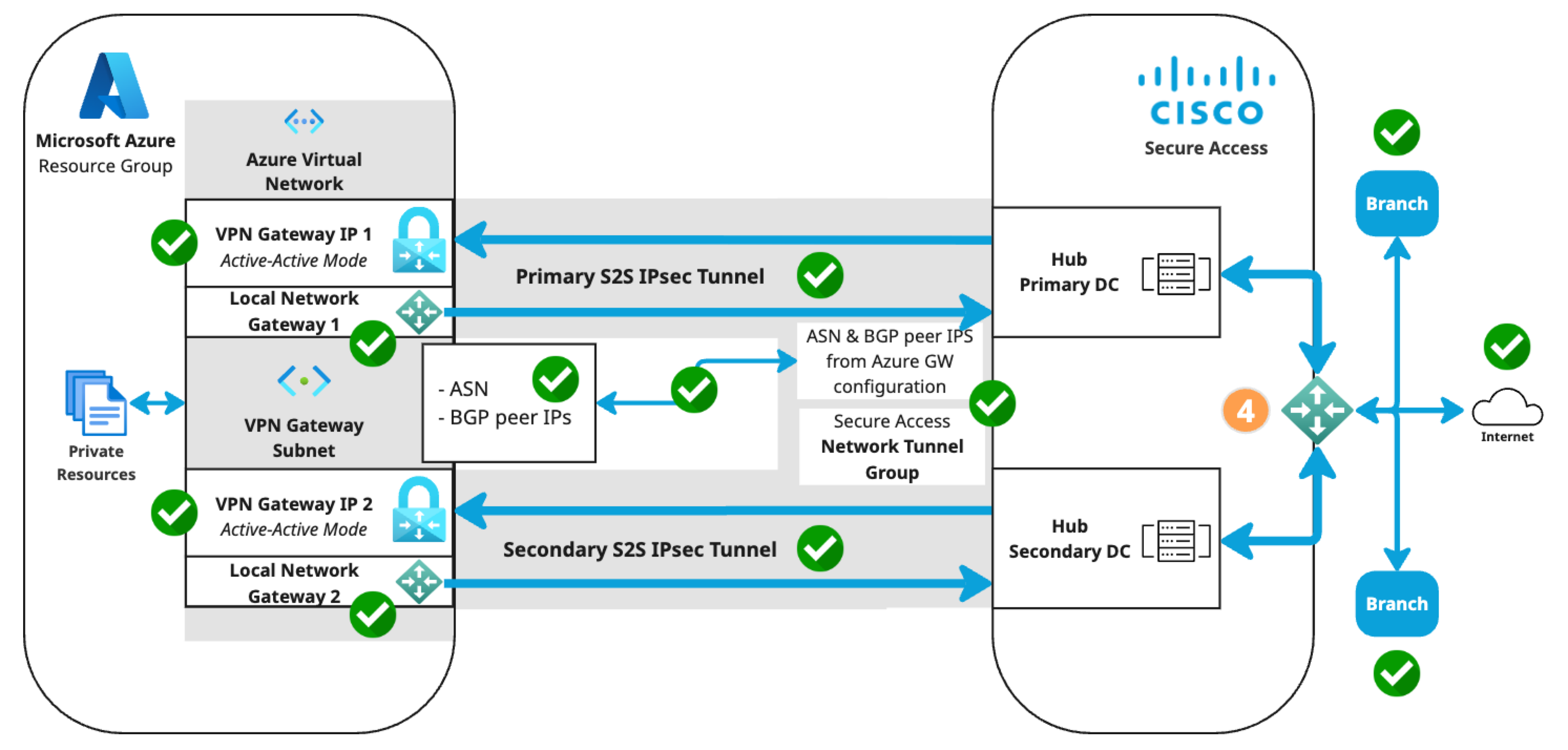
Microsoft Azure supports several methods of connecting to its VPN Gateway. The S2S VPN topology depends on components configured in the following order. Components in the diagram are numbered by order of configuration.
- An Azure virtual network with a VPN gateway in active-active mode for tunnel redundancy. In active-active mode, Azure provides two VPN gateway IPs that Secure Access can use to establish a network tunnel group. Traffic will use the primary tunnel. In the event of a tunnel failover, the switch to the secondary tunnel will be automatic, immediate, and without interruption.
- A Secure Access network tunnel group with two IPsec/IKEv2 tunnels and a pre-shared key (PSK) for connection with the Secure Access cloud native head end (CNHE) service.
- Two local network gateways in Azure that establish S2S connections between the Azure VPN Gateway client and the Secure Access CNHE.
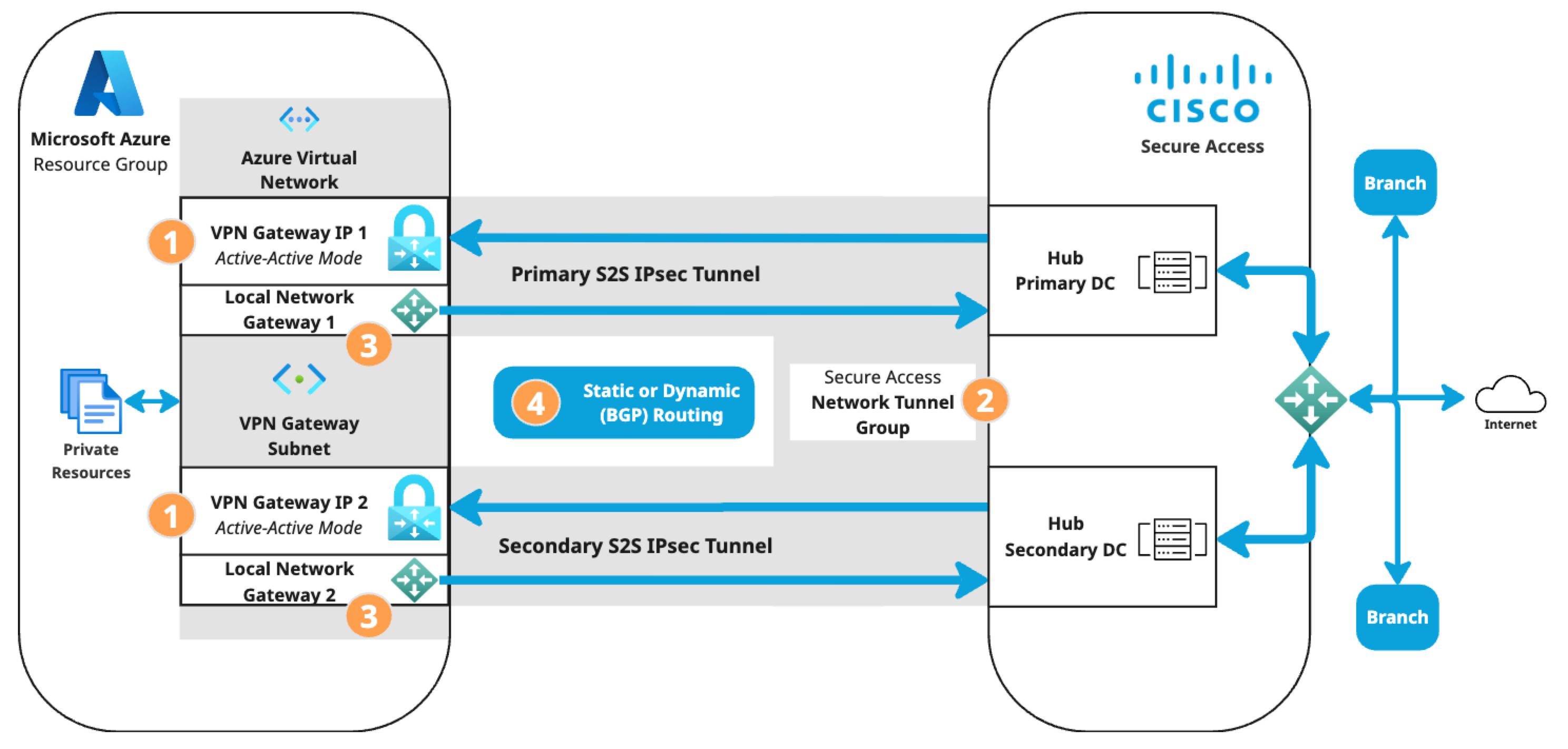
- Branch and internet routing.
- The static routing use case requires an Azure VPN Gateway route table.
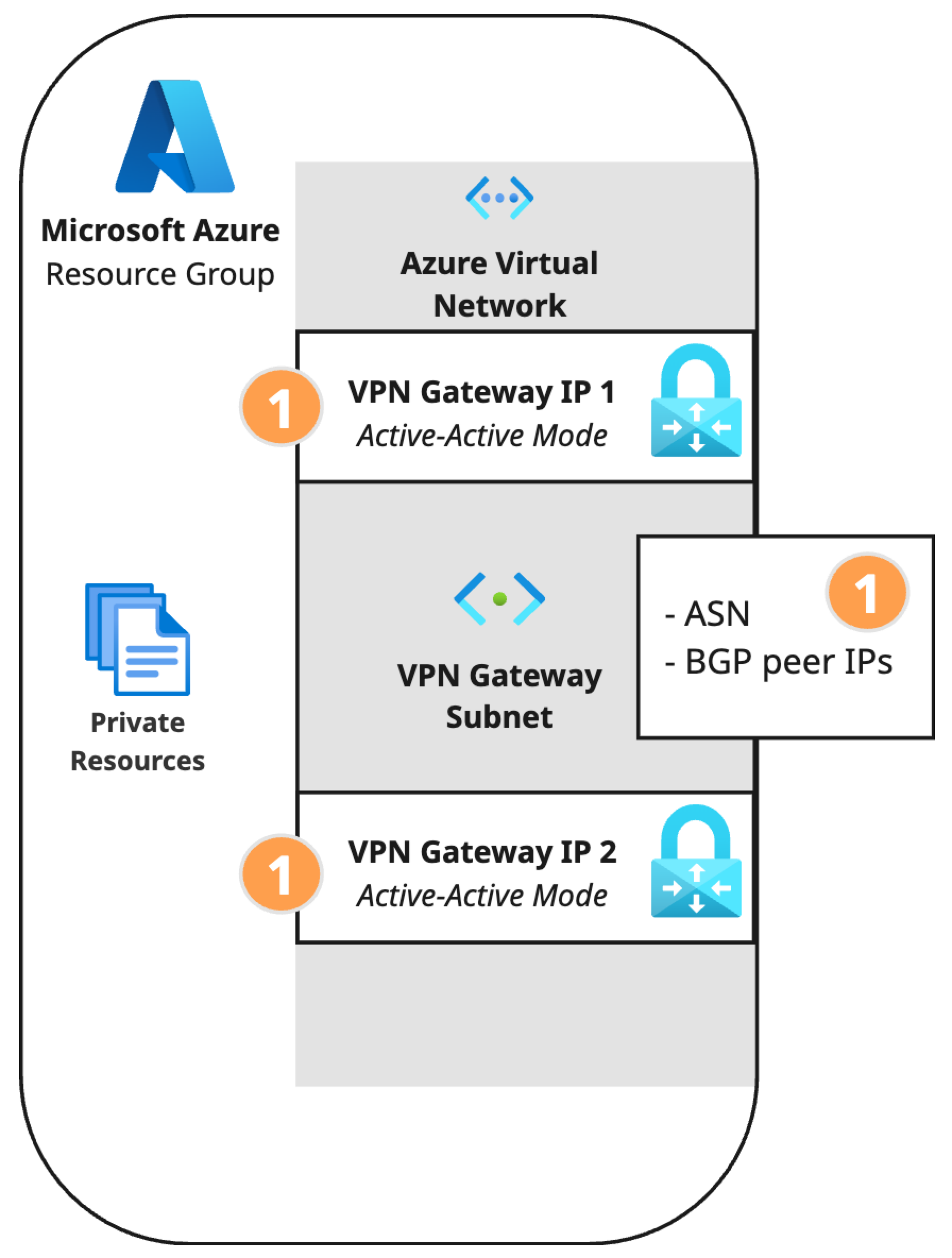
- The dynamic routing use case requires an Azure VPN Gateway autonomous system number (ASN) and Azure local network gateway BGP peer IP addresses.
For more information about VPN and tunnels in Secure Access, see Manage Virtual Private Networks and Manage Machine Tunnels.
For more information about Azure, see Microsoft documentation:
- What is Azure VPN Gateway?
- Azure VPN Gateway topology and design: Site-to-site VPN
- Design highly available gateway connectivity for cross-premises and VNet-to-VNet connections: Active-active VPN gateways
- Tutorial: Create a site-to-site VPN connection in the Azure portal
- Azure: Create, change, or delete a route table
- Azure: BGP and routing
Note: Microsoft may update their documentation without notice.
Prerequisites
- A valid Cisco Secure Access account.
- An Azure account with an active subscription.
Configure S2S Tunnels with Static Routing
Use static routing for small, simple networks where predictable routes are needed and manual configuration is manageable. For more information, see Static Routing.
Follow these five steps to create an S2S tunnel connection on IPsec/IKEv2 between Microsoft Azure and Secure Access, using an Azure route table for static routing to branch and internet destinations.
- Step 1: Create a VPN Gateway in Microsoft Azure
- Step 2: Create a network tunnel group in Secure Access
- Step 3: Create two local network gateways in Azure with S2S connections
- Step 4: Create a static route table in Azure
- Step 5: Verify tunnel status in Secure Access
Step 1: Create a VPN Gateway in Microsoft Azure
The Azure S2S IPsec tunnel is sourced from the VPN Gateway. If you have already deployed a VPN Gateway in your Azure environment, skip ahead to step 2.
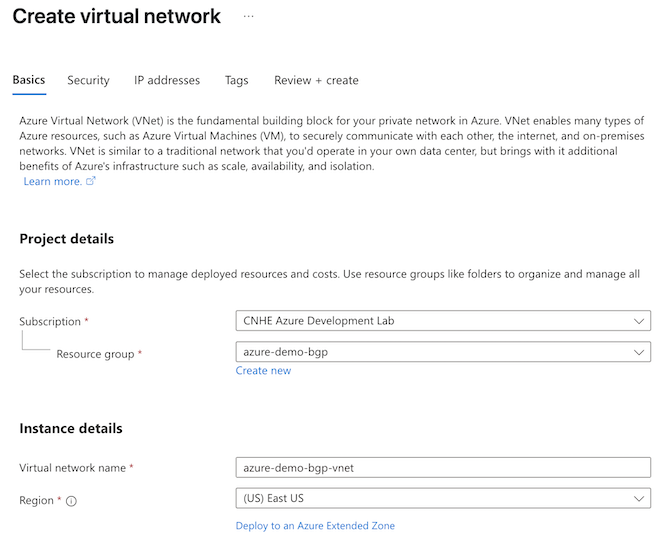
- In the Azure admin portal, navigate to your resource group and click Create.
- Search the marketplace for Virtual network, then click Create.
- Configure the virtual network.
- Basics: Select the Subscription and Resource group with the resources that you want to make available via the S2S VPN tunnel.
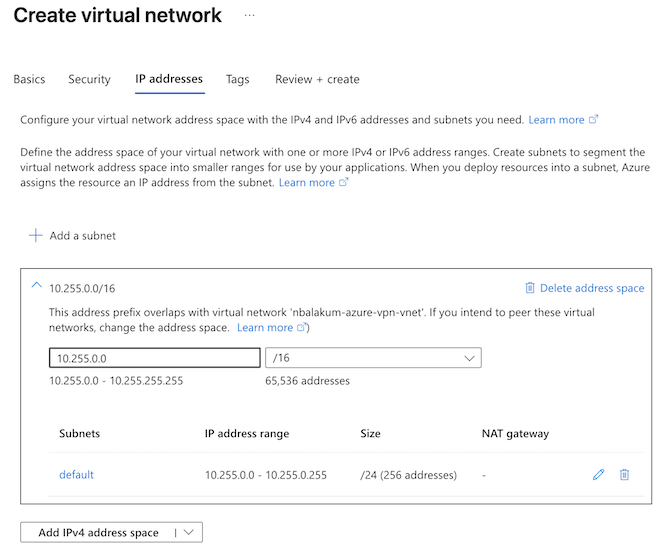
- IP addresses: Configure a virtual network address with the IPv4 addresses and subnets you need. This example uses the range 10.255.0.0/16.
- Review the configuration and click Create. Azure will deploy the virtual network and update the dashboard when deployment is complete.
- Create the gateway subnet.
- Navigate to Go to resource > Settings > Subnets.
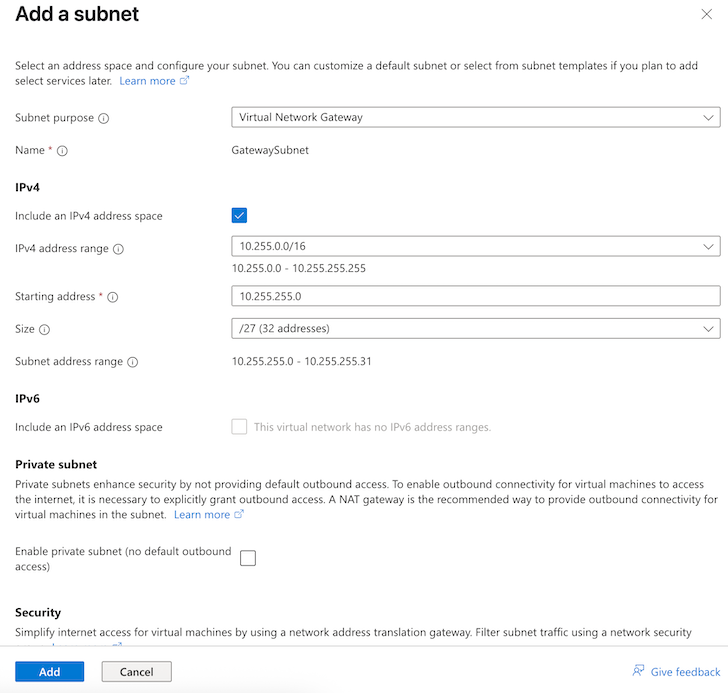
- Click + Subnet and configure the following:
- Subnet purpose: Virtual Network Gateway
- Enable Include an IPv4 address space (it is enabled by default)
- IPv4 address range will default to the address space you configured when you created the virtual network. This example uses the range 10.255.0.0/16.
- Starting address: This example uses 10.255.255.0.
- Size: This example uses /27 (32 addresses)
- Click Add.
- Create the virtual network gateway.
- Navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Virtual network gateway, then click Create.
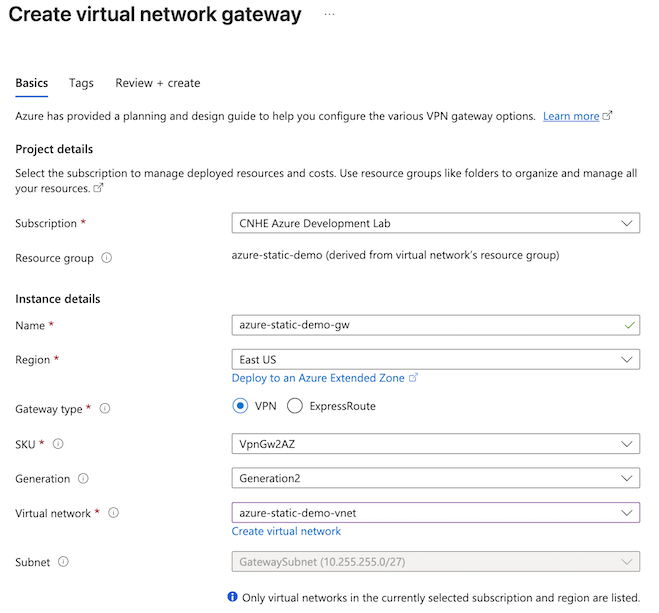
- Configure the virtual network gateway:
- SKU: VpnGw2AZ. For more information, see About gateway SKUs.
- Generation: Generation2
- Virtual network: Select the virtual network you created in the previous step.
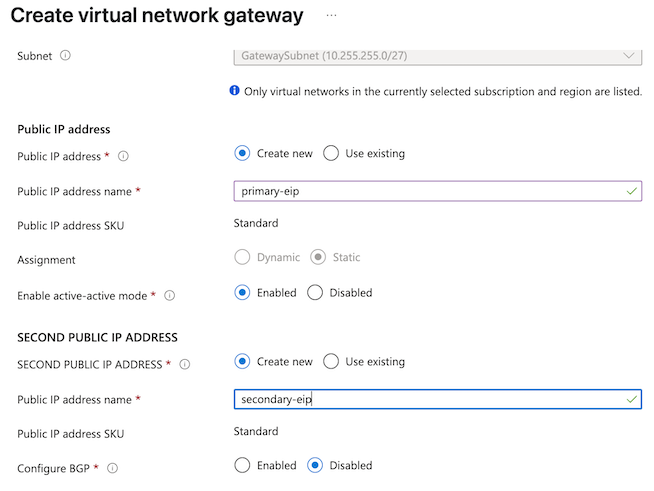
- Public IP address: Create new.
- Public IP address name: Enter a descriptive name for the primary IP address.
- Enable active-active mode: Enabled.
- SECOND PUBLIC IP ADDRESS: Create new.
- Public IP address name: Enter a descriptive name for the primary IP address.
- Configure BGP: Disabled.
- Review the configuration, then click Create. Azure will deploy the virtual network gateway and update the dashboard with the two public IP address resources when deployment is complete.
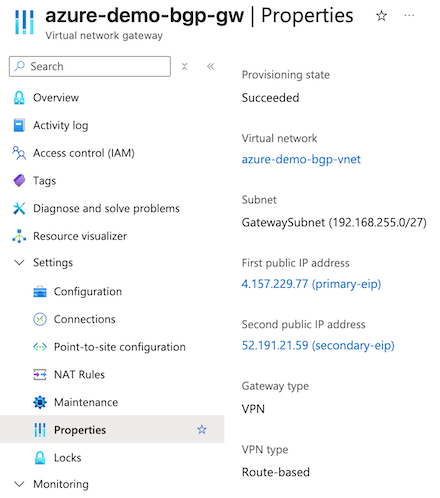
- To review your configuration after deployment is complete, navigate to Settings > Properties.
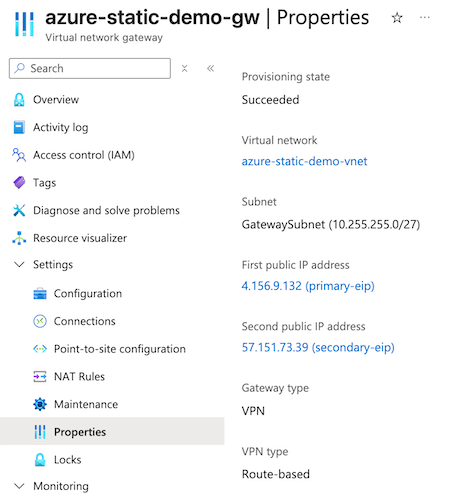
Step 2: Create a network tunnel group in Secure Access
Create a network tunnel group in Secure Access with the following configuration. For a more detailed procedure, see Add a Network Tunnel Group.
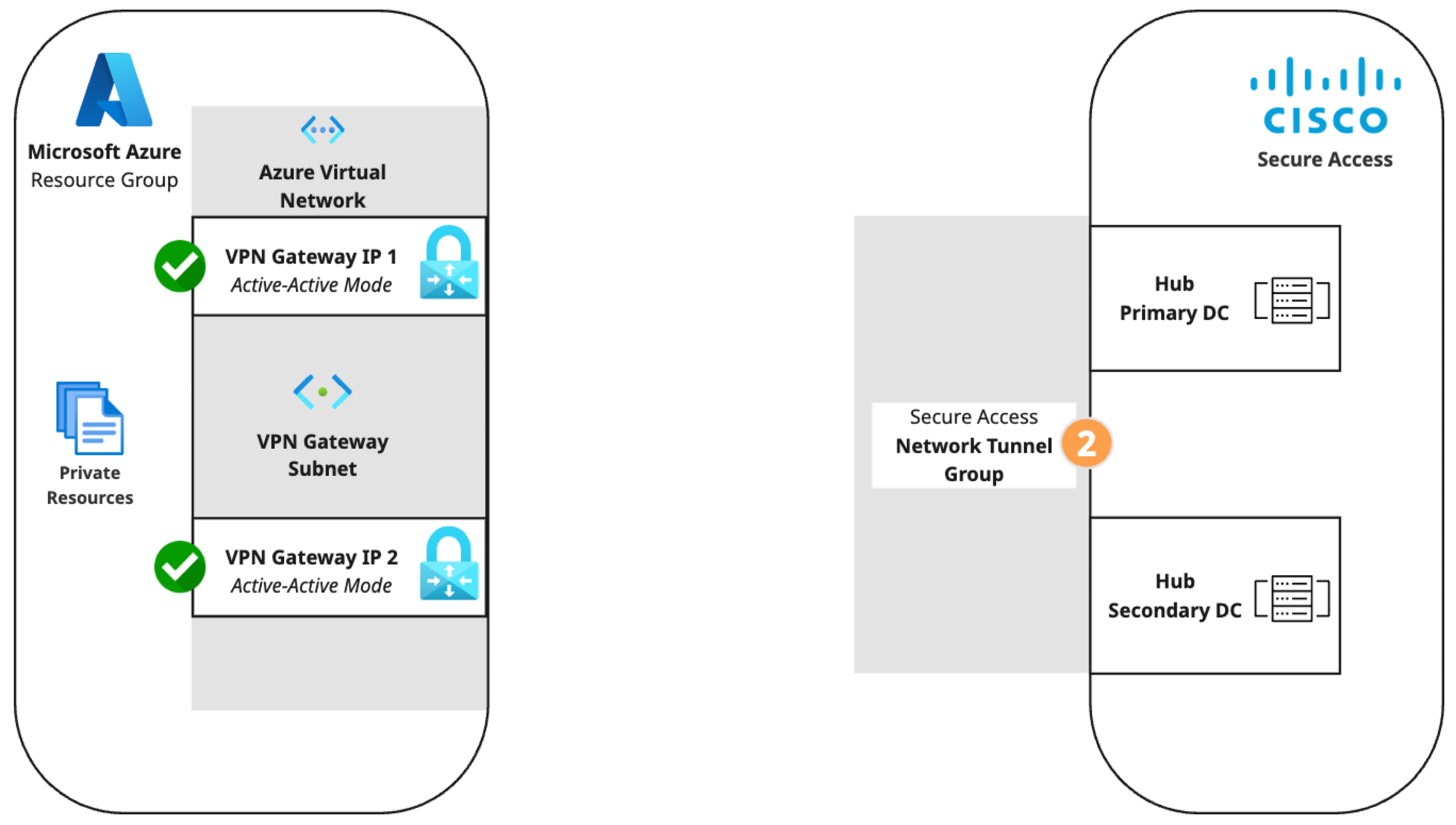
- Step 1 - General Settings: Set Device Type to AZURE.
- Step 2 - Tunnel ID and Passphrase: Enter the primary and secondary public IPs from the Azure virtual network gateway and create a passphrase.
- Step 3 - Routing
- Option 1, Enable NAT / Outbound only: Enable NAT / Outbound only if you determine that the IP address space behind the tunnel group overlaps with other IP address spaces in your network. Note: Enabling NAT for outbound traffic disables the routing options described below. Private applications hosted behind these tunnels will not be accessible.
- Option 2, Static routing: Add all public and private IPv4 address ranges used internally for your Azure virtual network. This example uses the range 10.255.0.0/16.
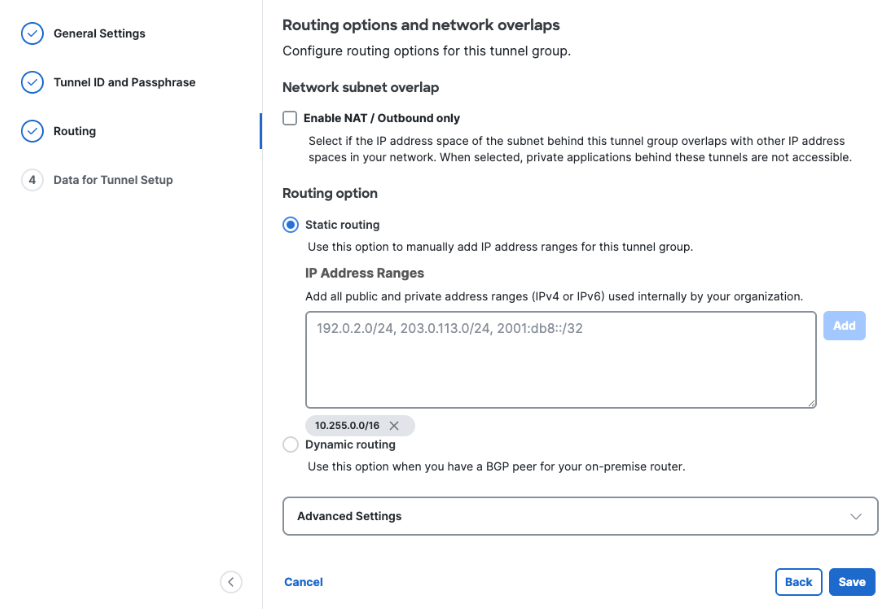
- Step 4 - Data for Tunnel Setup: Copy or download the primary and secondary tunnel IDs, data center (DC) IP addresses, and the passphrase you created. Note: This is the only time your passphrase will be displayed.
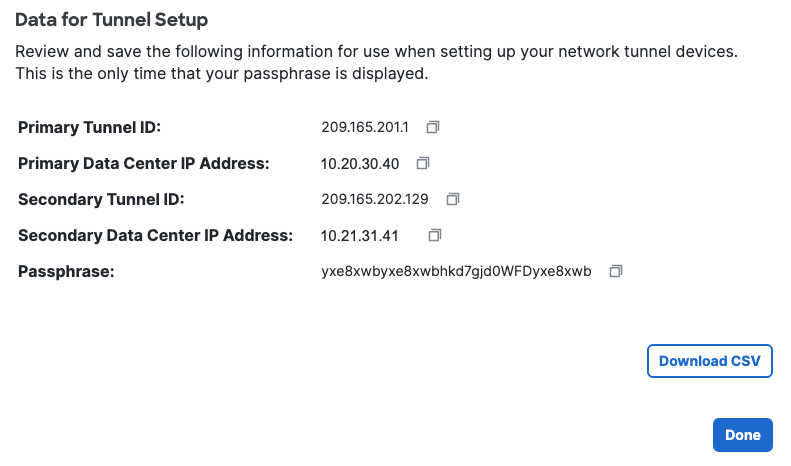
Step 3: Create two local network gateways in Azure with S2S connections
Create and configure two local network gateways in Azure, then connect them to Secure Access. The local network gateway acts as the remote site connected by tunnel to the Secure Access CNHE DC.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Local network gateway, then click Create.
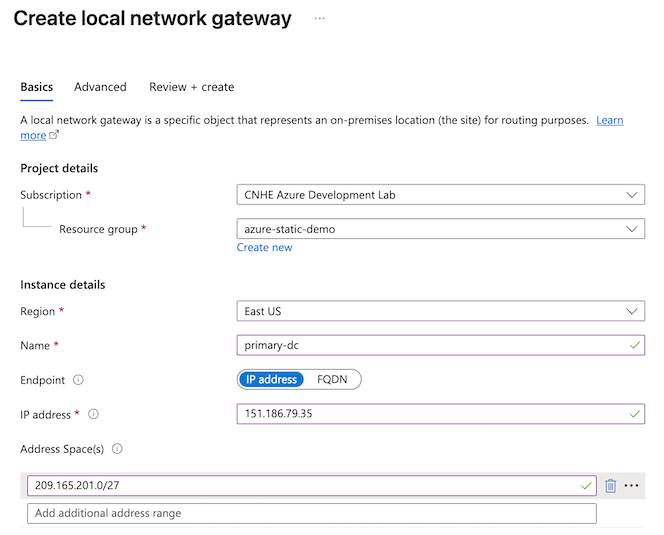
- Configure the Basics tab of the first local network gateway.
- Select the Subscription and Resource group of your virtual network.
- Name: This example uses primary-dc.
- Endpoint: IP address
- IP address: For the first local network gateway, enter the Primary DC IP Address from Secure Access Step 4 - Data for Tunnel Setup.
- Address Space(s): Add one or more IP ranges for branch sites that will connect to the Secure Access network tunnel group. Address spaces should not overlap with other IP ranges in your network. This example uses 209.165.201.0/27.
- Review the configuration, then click Create. Azure will deploy the local network gateway and update the dashboard with the local network gateway resource when deployment is complete.
- Repeat step 3 to create the secondary local network gateway with the Secondary DC IP Address from Secure Access.
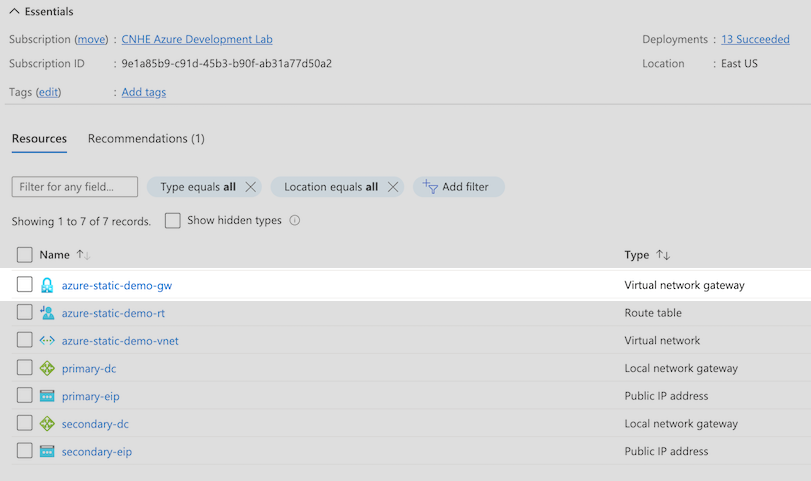
- Create the S2S connection for the primary local network gateway.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > Resources, then click the name of your virtual network gateway.
- Navigate to Connections, then click + Add.
- Configure the Basics tab of the connection.
- Select the Subscription and Resource group of your virtual network.
- Connection type: Site-to-site (IPsec).
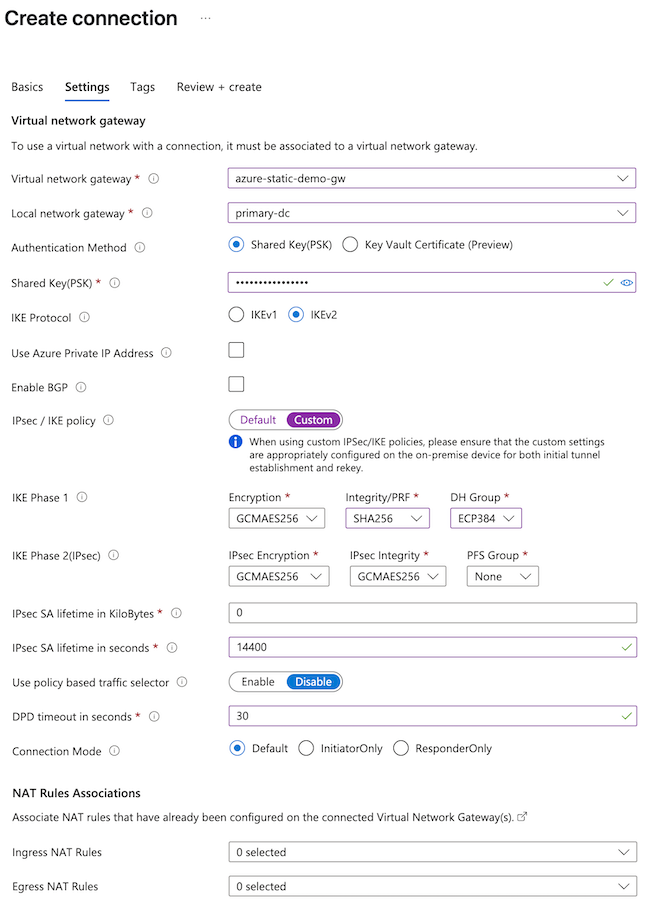
- Configure the Settings tab of the connection.
- Select your virtual network gateway.
- Local network gateway: Select the primary gateway.
- Shared Key (PSK): Enter the passphrase configured for the Secure Access network tunnel group in step 2.
- IPsec / IKE policy: Custom.
- IKE Phase 1: The following configuration is recommended.
- Encryption: GCMAE256.
- Integrity/PRF: SHA256.
- DH Group: ECP384.
- For information about cipher parameters supported by Secure Access, see Supported IPsec Parameters. For information about cipher parameters supported by Azure, see Microsoft documentation on Default IPsec/IKE parameters.
- IPsec SA lifetime in seconds: 14400
- DPD timeout in seconds: 30
- Review the configuration, then click Create. Azure will deploy the S2S connection and update the dashboard when deployment is complete.
- Repeat step 5 for the secondary local network gateway.
- Both S2S VPN tunnels are now established with static routing between your Azure virtual network gateway and the Secure Access cloud native head end (CNHE) service.
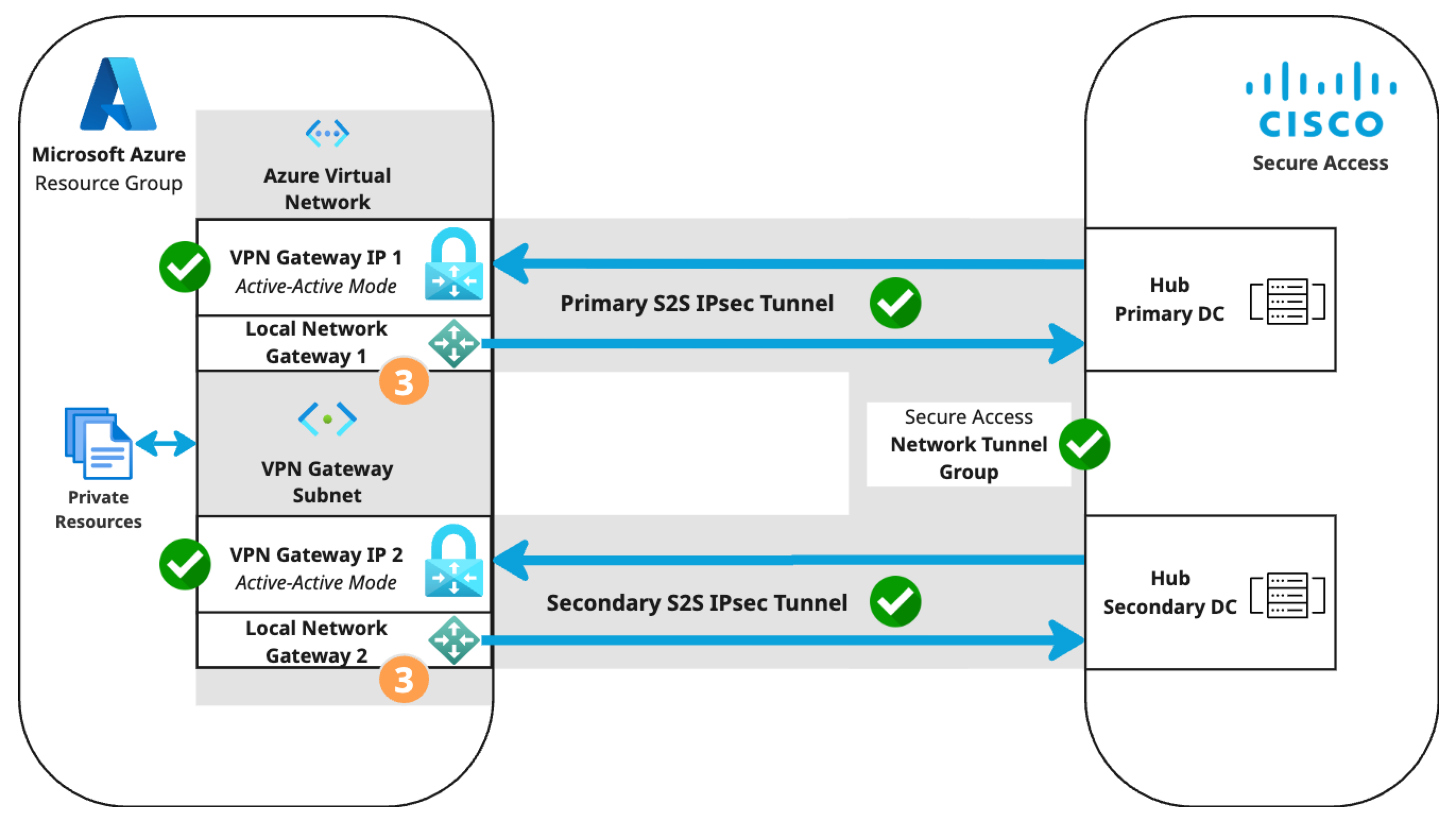
Step 4: Create a static route table in Azure
Add a table of branch routes and internet routes to the primary VPN gateway and associate the route table with any required subnets. For more information, see Azure: Create, change, or delete a route table.
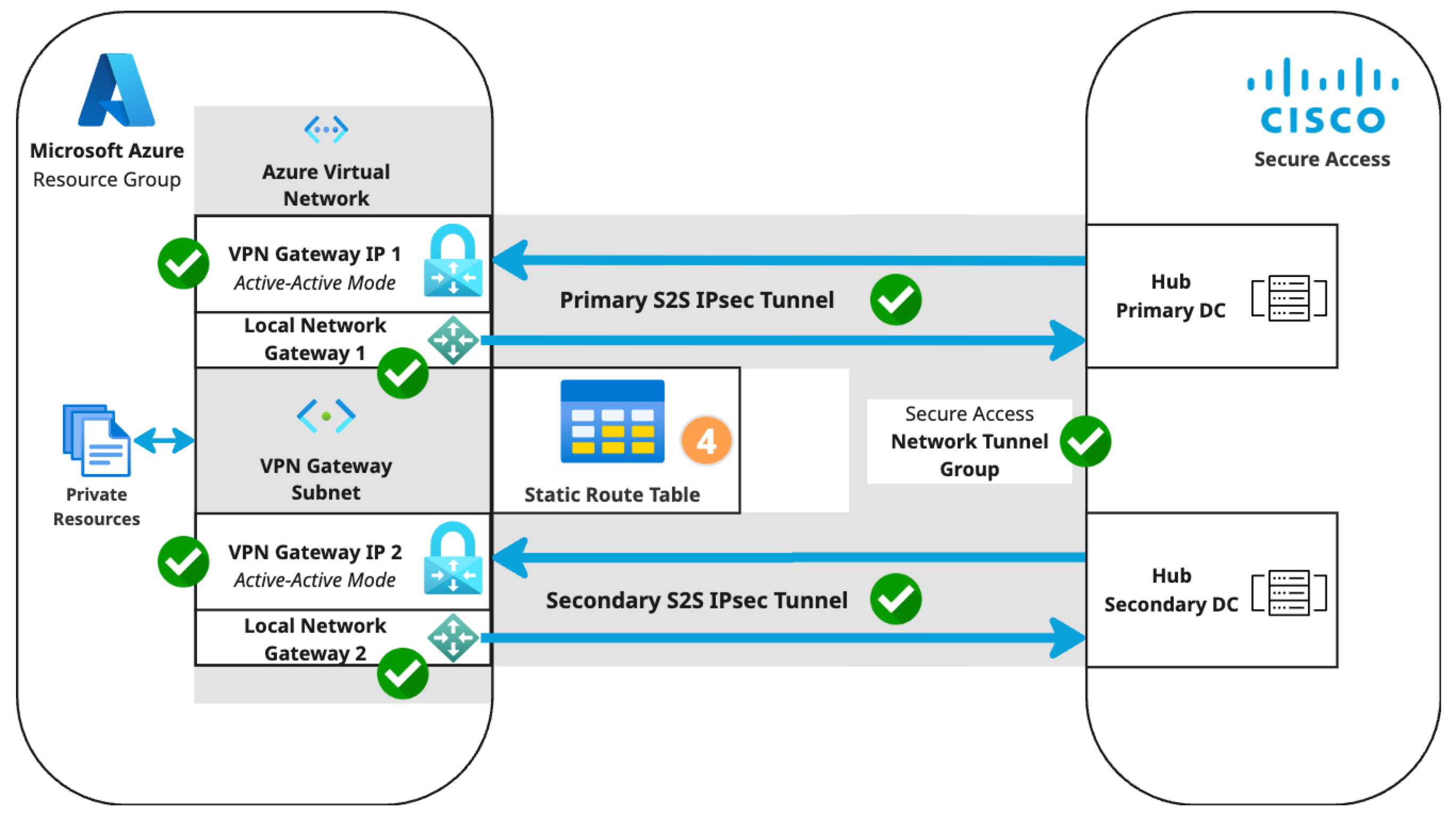
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Route table, then click Create.
- Configure the Basics tab of the route table.
- Select the Subscription and Resource group of your virtual network.
- Review the configuration, then click Create. Azure will deploy the route table and update the dashboard when deployment is complete.
- Navigate to Overview > Resource group (click the name of your resource group) > Resources, then click the name of your route table.
- Click + Add.
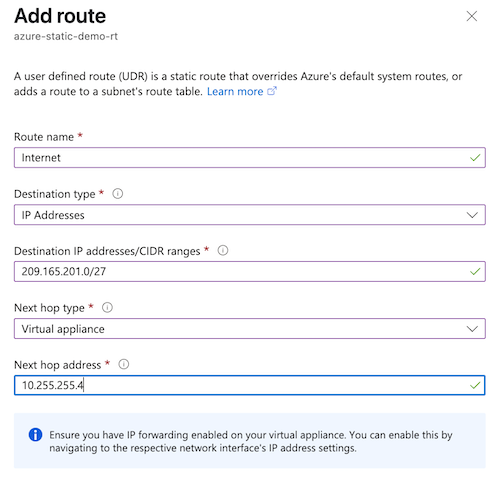
- Configure a route.
- Route name: The example in the image is Internet.
- Destination type: IP Addresses.
- Destination IP addresses/CIDR ranges: Enter the IP ranges for branch sites configured as address spaces for Azure local network gateways. This example uses 209.165.201.0/27.
- Next hop type: Virtual appliance.
- Next hop address: Enter the first IP address returned by this Azure CloudShell command. In this example, the next hop address is 10.255.255.4.
az network vnet-gateway show --resource-group \<Resource Group Name> -n \<VNET Gateway Name> | jq .bgpSettings.bgpPeeringAddress
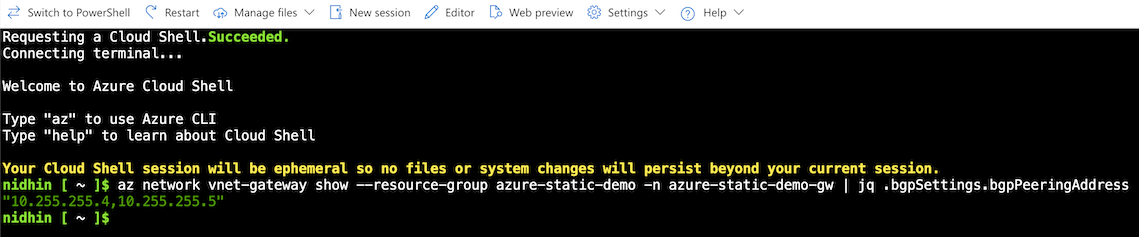
The CloudShell command returns the BGP peering addresses for the primary and secondary local network gateways.
By creating a static route to the primary local network gateway connection, Azure will route all traffic to the primary DC via the primary S2S tunnel when both tunnels are up. When the primary tunnel is down, Azure will route all traffic to the secondary DC via the secondary S2S tunnel.
- Associate a subnet.
- Navigate to Settings > Subnets.
- Select the virtual network.
- Subnet: default.
- Click OK.
Step 5: Verify tunnel status in Secure Access
In Secure Access, navigate to Connect > Network Connections > Network Tunnel Groups and click the name of the network tunnel group to review the connection status with Azure.
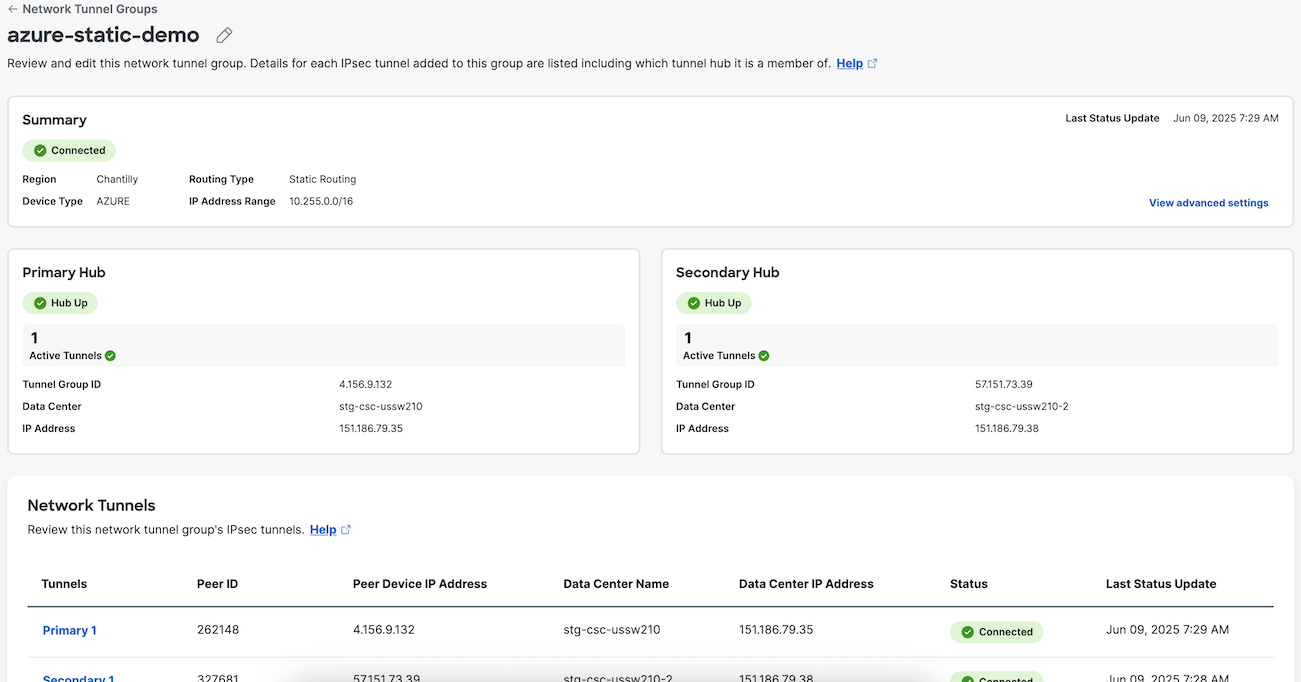
Resources in your Azure virtual network are now protected by the site-to-site (S2S) IPsec/IKEv2 VPN tunnel with Cisco Secure Access.
Configure S2S Tunnels with Dynamic Routing with BGP
Use dynamic routing for large, complex networks with multiple connections where automatic route updates and optimal path selection are crucial, especially when dealing with internet connectivity or service provider traffic. For more information, see Dynamic Routing with BGP.
Follow these four steps to create an S2S tunnel connection on IPsec/IKEv2 between Microsoft Azure and Secure Access, using Azure BGP for dynamic routing to branch and internet destinations.
- Step 1: Create a VPN Gateway in Microsoft Azure
- Step 2: Create a network tunnel group in Secure Access
- Step 3: Create two local network gateways in Azure
- Step 4: Verify tunnel status in Azure and Secure Access
Step 1: Create a VPN Gateway in Microsoft Azure
The Azure S2S IPsec tunnel is sourced from the VPN Gateway. If you have already deployed a VPN Gateway in your Azure environment, you can skip this section.
- In the Azure admin portal, navigate to your resource group and click Create.
- Search the marketplace for Virtual network, then click Create.
- Configure the virtual network.
- Basics: Select the Subscription and Resource group with the resources that you want to make available via the S2S VPN tunnel.
- IP addresses: Configure a virtual network address with the IPv4 and IPv6 addresses and subnets you need. This example uses the range 192.168.0.0/16.
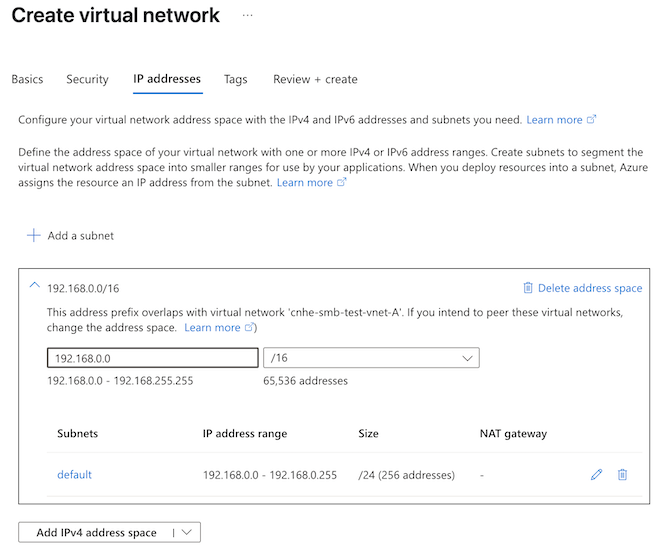
- Review the configuration and click Create. Azure will deploy the virtual network and update the dashboard when deployment is complete.
- Create the gateway subnet.
- Navigate to Go to resource > Settings > Subnets.
- Click + Subnet and configure the following:
- Subnet purpose: Virtual Network Gateway.
- Enable Include an IPv4 address space (it is enabled by default).
- IPv4 address range will default to the address space you configured when you created the virtual network. This example uses the range 192.168.0.0/16.
- Starting address: This example uses 192.168.255.0.
- Size: This example uses /27 (32 addresses)
- Click Add.
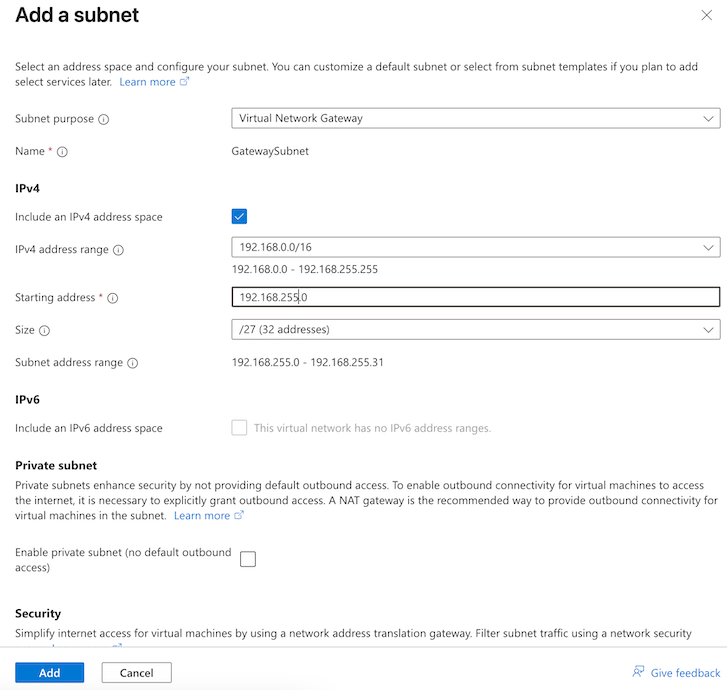
- Create the virtual network gateway.
- Navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Virtual network gateway, then click Create.
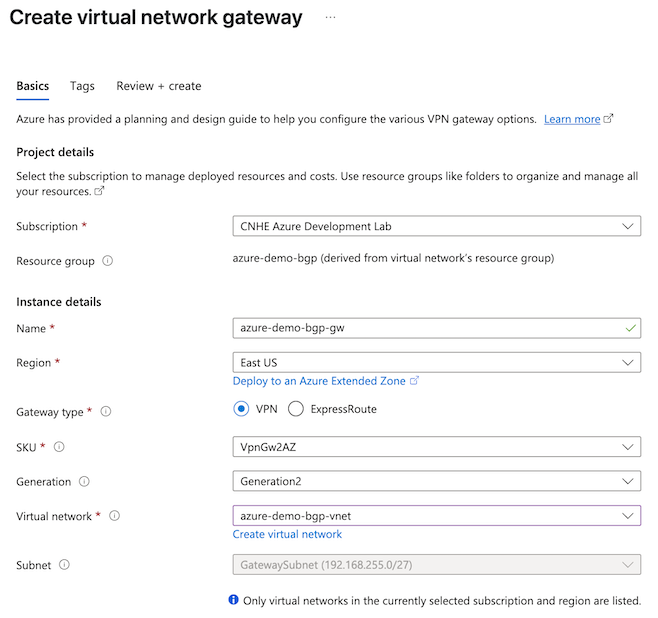
- Configure the virtual network gateway.
- SKU: VpnGw2AZ. For more information, see About gateway SKUs.
- Generation: Generation2.
- Virtual network: Select the virtual network you created in the previous step.
- Public IP address: Create new.
- Public IP address name: Enter a descriptive name for the primary IP address.
- Enable active-active mode: Enabled.
- SECOND PUBLIC IP ADDRESS: Create new
- Public IP address name: Enter a descriptive name for the primary IP address.
- Configure BGP: Enabled.
- Autonomous system number (ASN): Enter an ASN that is not in use by your other branches and that is not reserved by Azure or IANA. For more information, see Microsoft Azure documentation on BGP and routing. This example uses ASN 64515.
- You do not need to enter custom Azure APIPA BGP IP addresses.
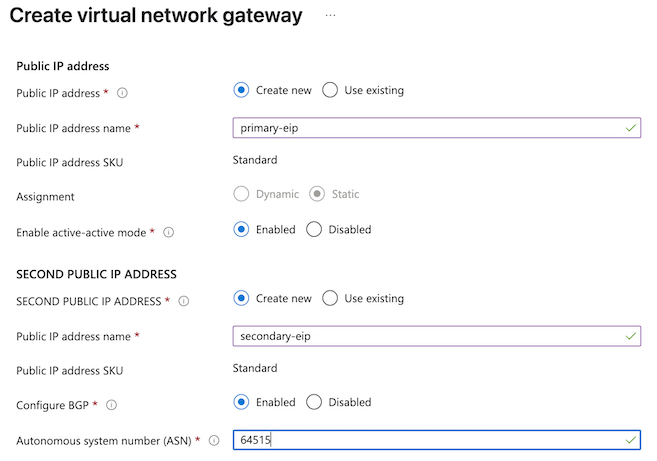
- Review the configuration, then click Create. Azure will deploy the virtual network gateway and update the dashboard with the two public IP address resources when deployment is complete.
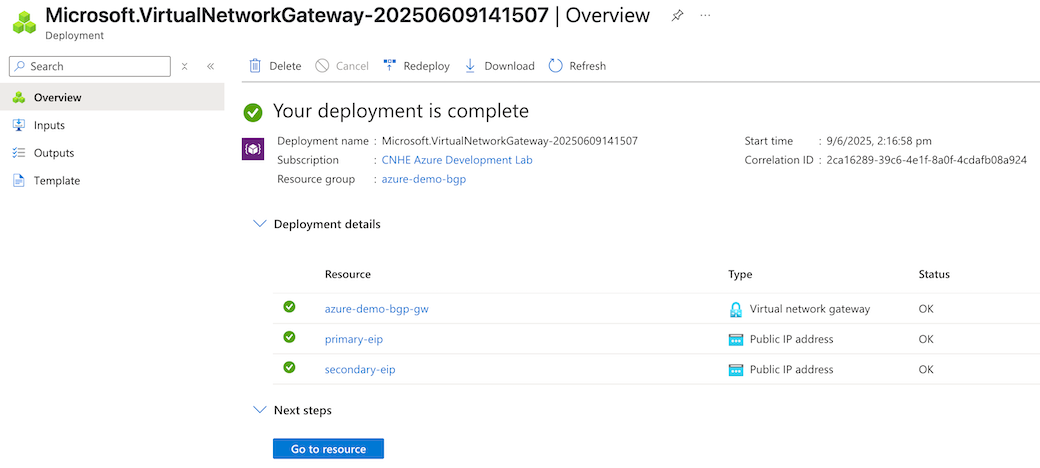
- To review your configuration after deployment is complete, navigate to Settings > Properties.
Step 2: Create a network tunnel group in Secure Access
Configure a network tunnel group in Secure Access. For a more detailed procedure, see Add a Network Tunnel Group.
- Step 1 - General Settings: Set Device Type to AZURE.
- Step 2 - Tunnel ID and Passphrase: Enter the primary and secondary public IPs from the Azure virtual network gateway and create a passphrase.
- Step 3 - Routing
- Select Dynamic routing.
- Device AS Number: Enter the ASN configured for the Azure virtual network gateway. This example uses 64515.
- BGP peer IP address 1 and 2: Enter two private IP address ranges (RFC1918). This example uses 10.255.255.254/32 and 10.255.255.255/32.
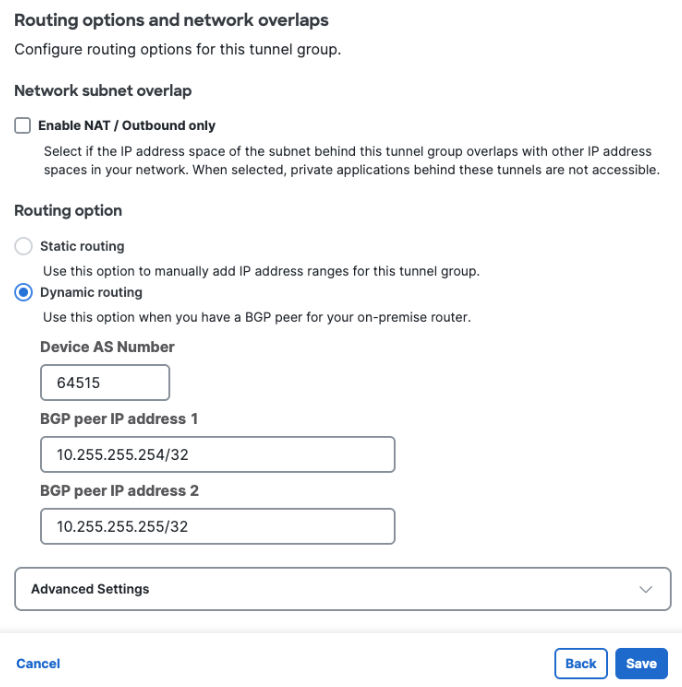
BGP peer IP address compatibility between Azure and Secure Access
By default, Secure Access CNHE listens for BGP peer requests in the the APIPA address range 169.254.0.0/24. Azure does not initiate BGP connections to peers in the range 169.254.0.0/16. To work around this limitation, configure the Secure Access tunnel group to listen for BGP peer requests from two RFC1918 private IP ranges. These ranges should not overlap with 169.254.0.0/16 or with ranges assigned to your other branches that connect to Secure Access.
- Step 4 - Data for Tunnel Setup: Copy or download the primary and secondary tunnel IDs, data center (DC) IP addresses, and the passphrase you created. Note: This is the only time your passphrase will be displayed.

Step 3: Create two local network gateways in Azure with S2S connections
Create and configure two local network gateways in Azure, then connect them to Secure Access. The local network gateway acts as the remote site connected by tunnel to the Secure Access CNHE DC.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Local network gateway, then click Create.
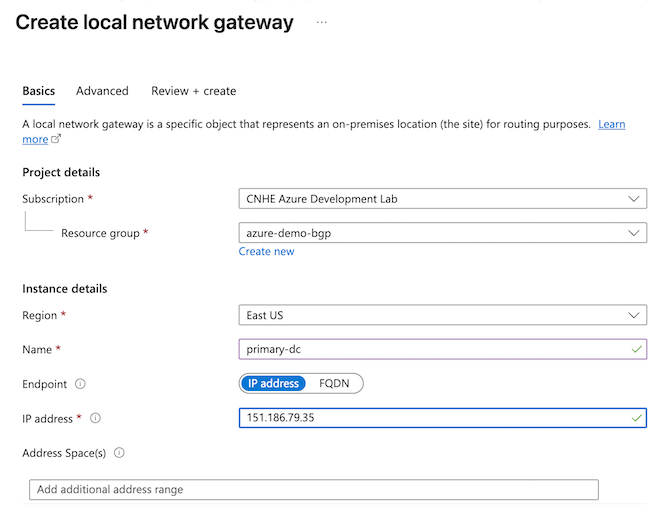
- Configure the Basics tab of the first local network gateway.
- Select the Subscription and Resource group of your virtual network.
- Name: This example uses primary-dc.
- Endpoint: IP address.
- IP address: For the first local network gateway, enter the Primary DC IP Address from Secure Access Step 4 - Data for Tunnel Setup.
- Leave Address space(s) blank.
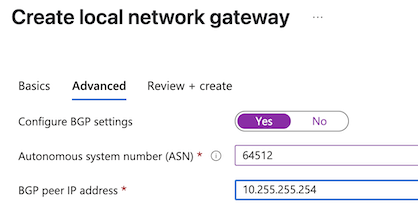
- Configure the Advanced tab of the first local network gateway.
- Configure BGP settings: Yes.
- Autonomous system number (ASN): Enter the Peer (Secure Access) BGP AS number from the Secure Access network tunnel group created in the previous step. This example shows the ASN 64512. You can also find this ASN in the Summary section of your network tunnel group in Secure Access.
- BGP peer IP address: For the first local network gateway, enter the BGP peer IP address 1 that you configured in Secure Access Step 3 - Routing. You can also find the BGP peer IP address in the Summary section of your network tunnel group in Secure Access.
- Review the configuration, then click Create. Azure will deploy the local network gateway and update the dashboard with the local network gateway resource when deployment is complete.
- Repeat steps 3 and 4 to create the secondary local network gateway with the BGP peer IP address 2 and the Secondary DC IP Address from Secure Access.
- Create the S2S connection for the primary local network gateway.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > Resources, then click the name of your virtual network gateway.
- Navigate to Connections, then click + Add.
- Configure the Basics tab of the connection.
- Select the Subscription and Resource group of your virtual network.
- Connection type: Site-to-site (IPsec).
- Configure the Settings tab of the connection.
- Select your virtual network gateway.
- Local network gateway: Select the primary gateway.
- Shared Key (PSK): Enter the passphrase configured for the Secure Access network tunnel group in step 2.
- Enable BGP: Check the box.
- IPsec / IKE policy: Custom.
- IKE Phase 1: The following configuration is recommended.
- Encryption: GCMAE256.
- Integrity/PRF: SHA256.
- DH Group: ECP384.
- For information about cipher parameters supported by Secure Access, see Supported IPsec Parameters. For information about cipher parameters supported by Azure, see Microsoft documentation on Default IPsec/IKE parameters.
- IPsec SA lifetime in seconds: 14400
- DPD timeout in seconds: 30
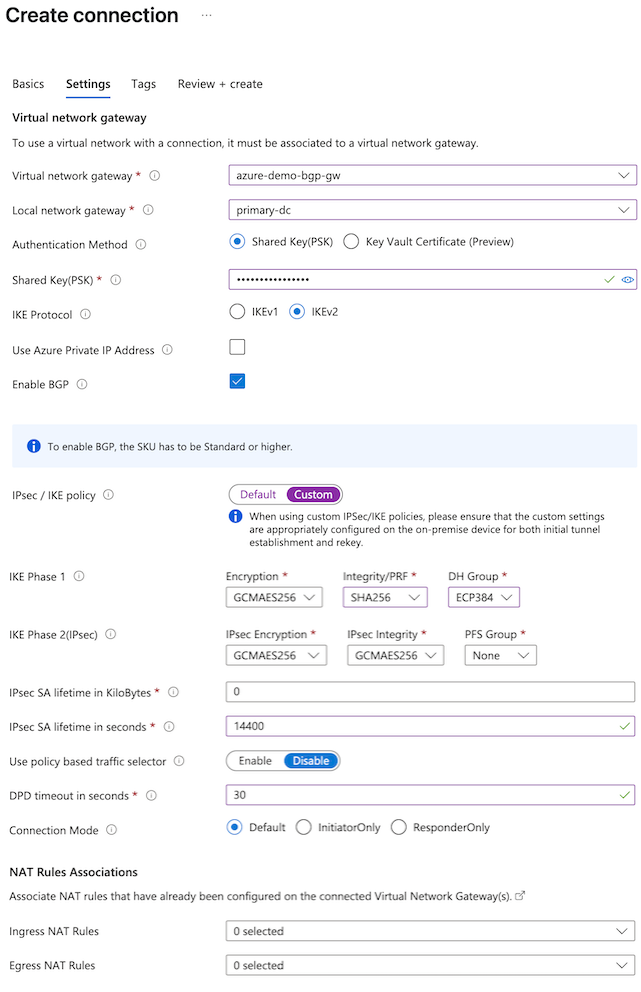
- Review the configuration, then click Create. Azure will deploy the S2S connection and update the dashboard when deployment is complete.
- Repeat step 6 for the secondary local network gateway.
- Both S2S VPN tunnels are now established with dynamic routing with BGP between your Azure virtual network gateway and the Secure Access cloud native head end (CNHE) service.
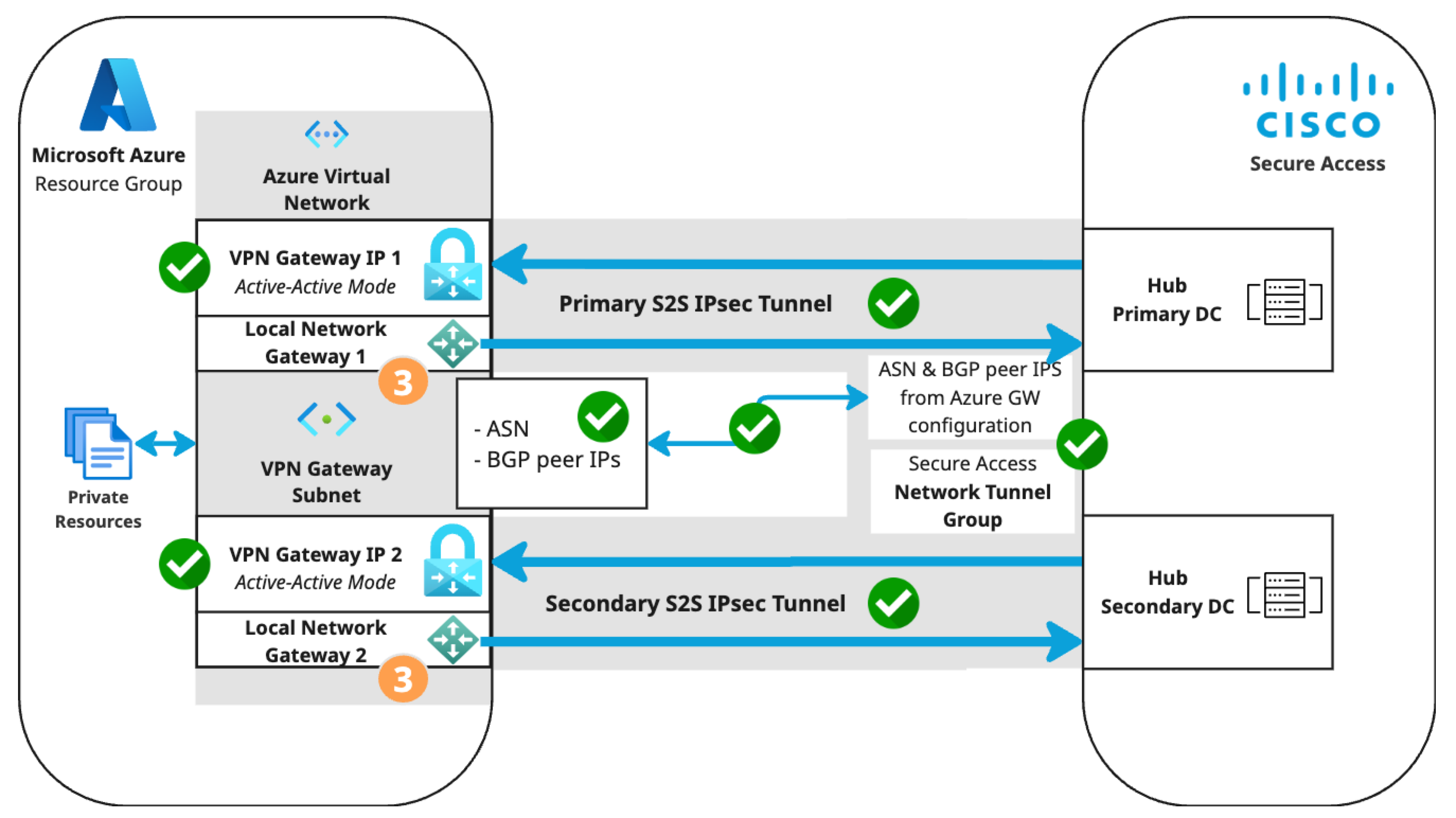
Step 4: Verify tunnel status in Azure and Secure Access
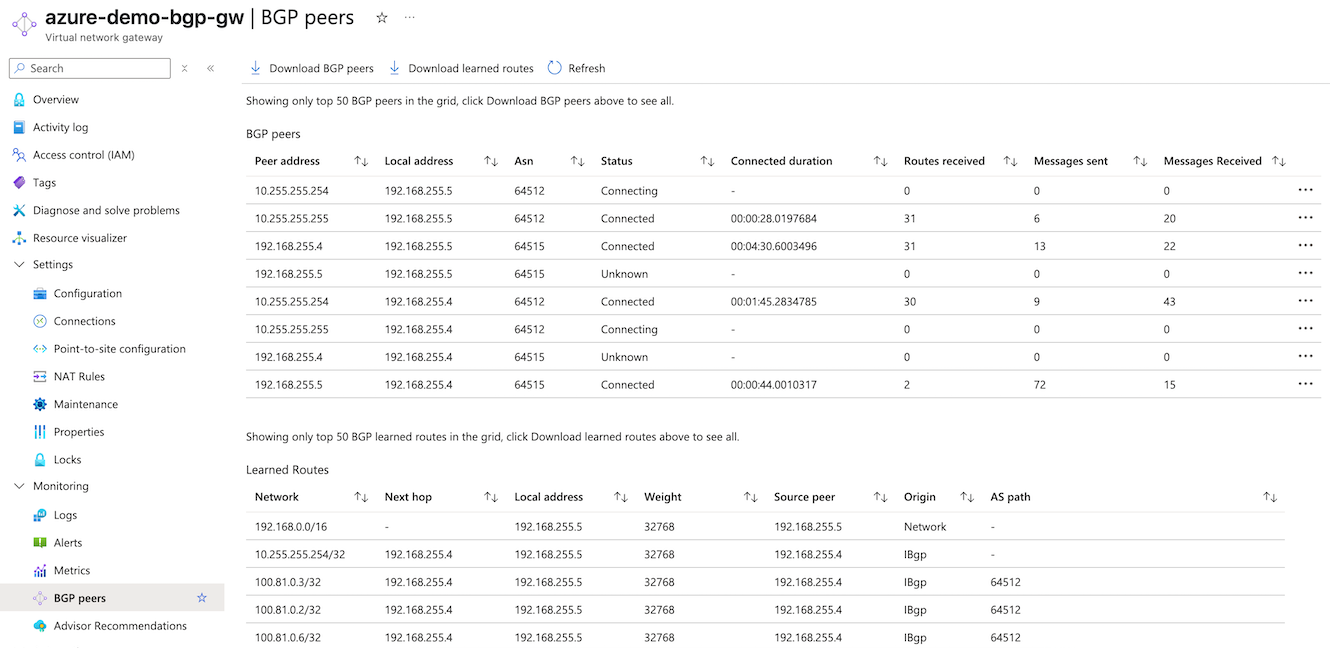
In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group), then click the name of your virtual network gateway. Navigate to Settings > BGP peers to review the table of Learned Routes received by your Azure virtual network gateway and the Secure Access cloud native head end (CNHE) service.
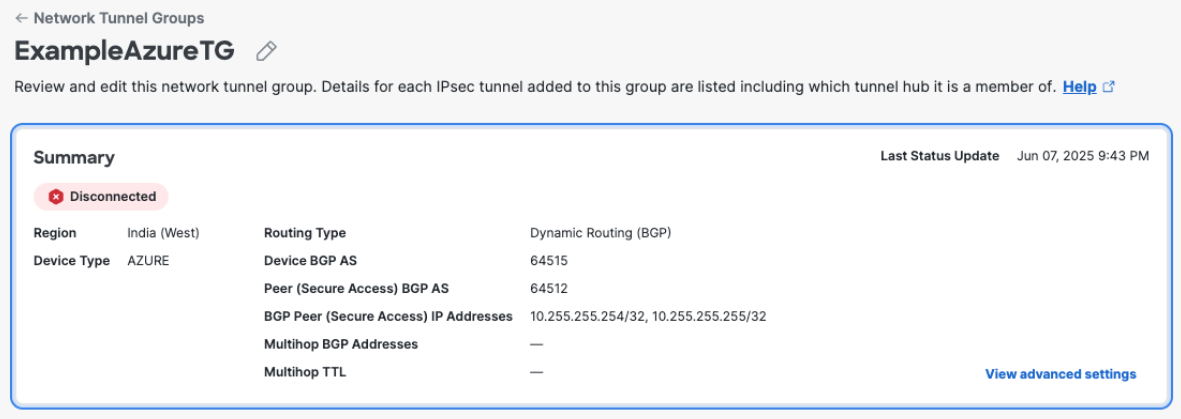
In Secure Access, navigate to Connect > Network Connections > Network Tunnel Groups and click the name of the network tunnel group to review the connection status with Azure.
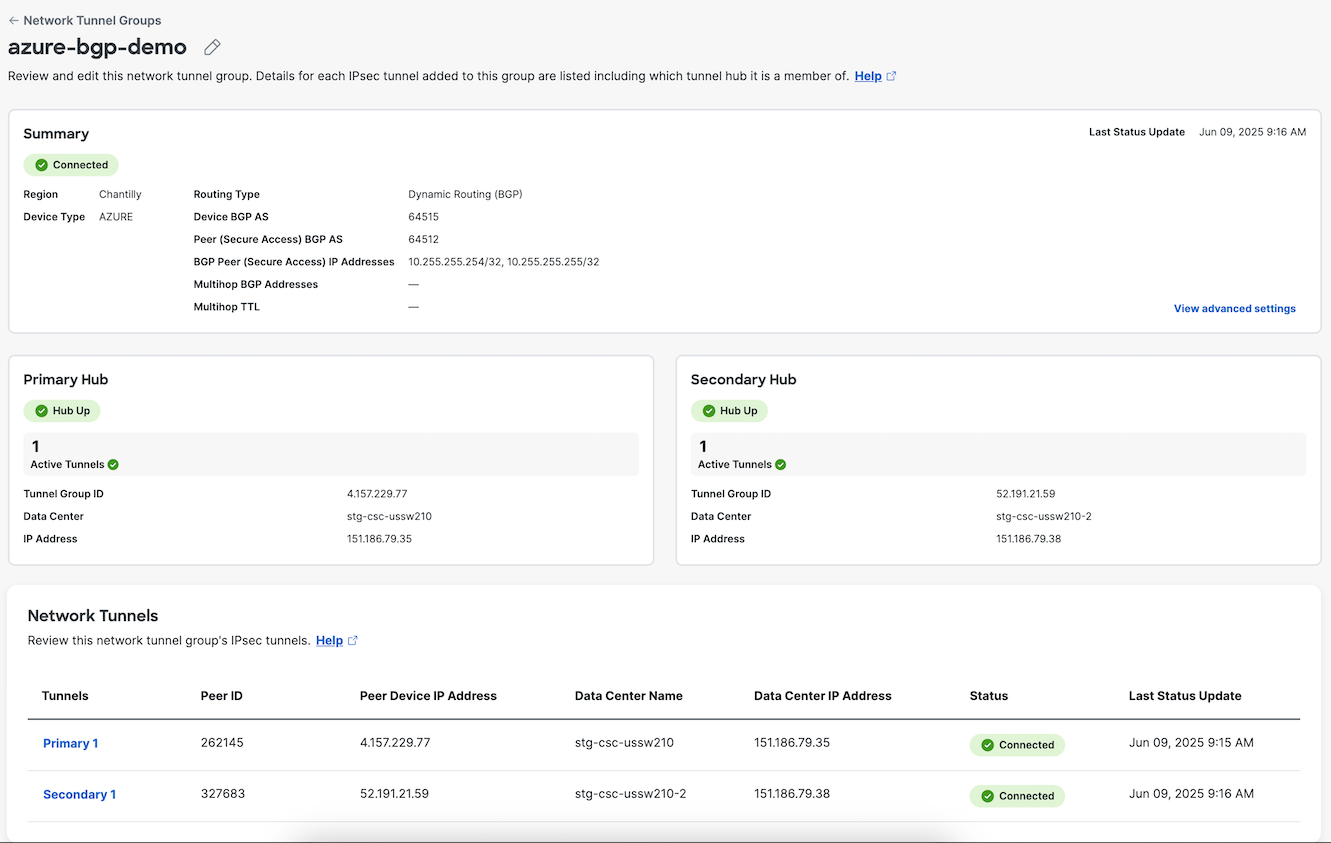
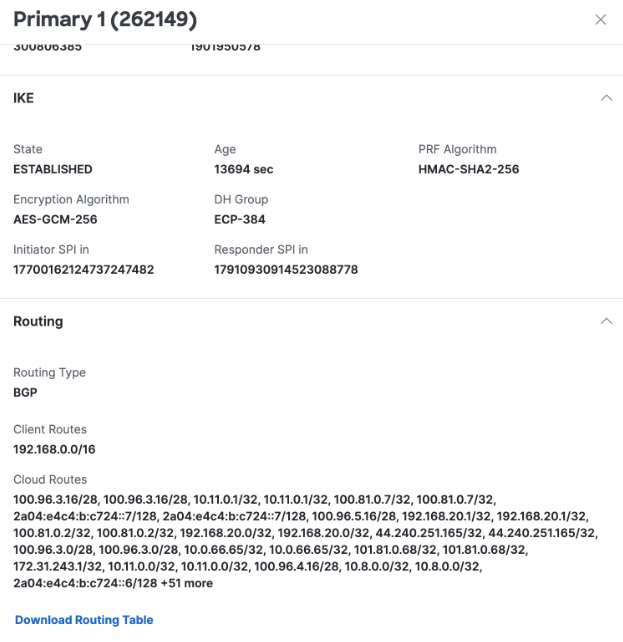
Under Network Tunnels, click a tunnel name to review Routing details. Client Routes show routes advertised by Azure to Secure Access via BGP. Cloud Routes show routes advertised by Secure Access to Azure via BGP.
Branch access to resources in your Azure virtual network is now protected by the site-to-site (S2S) IPsec/IKEv2 VPN tunnel with Cisco Secure Access.
What to do next
For information about managing and monitoring your network tunnel group, see Manage Network Tunnel Groups.
Configure Tunnels with NEC IX2000 Series Router < Configure a Site-to-Site VPN with Microsoft Azure > Configure a Site-to-Site VPN tunnel with Amazon Web Services
Updated 4 days ago
