Manage SAML Certificates for Service Providers
To establish a trust relationship between Cisco Secure Access (service provider) and an integrated SAML identity provider (IdP), certificates are exchanged between Secure Access and the SAML IdP. An administrator uploads the service provider's certificates from the Secure Access XML Metadata to the IdP platform's trust store. Then, an administrator imports the SAML IdP's XML Metadata that contains the IdP's certificates in to Secure Access.
After you integrate an SAML identity provider (IdP) in Secure Access, you can manage the service provider's certificates. Secure Access displays notifications about certificates that may expire. When the service provider certificates expire, an administrator must upload new certificates from the Secure Access XML Metadata to the integrated SAML IdP platform's trust store to prevent connection disruptions.
Secure Access manages the expiration of service provider certificates for various connection methods and SAML IdP integrations. Service provider certificates are used to establish the trust relationship between the service provider and the IdP. The IdP authenticates users that connect to Secure Access with:
- Zero Trust (ZT)
- Networks and network tunnels protected by Internet Security
- Virtual Private Networks (VPNs) with a configured VPN profile
Table of Contents
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- An integration of an SAML IdP with Secure Access. For more information, see Configure Integrations with SAML Identity Providers and Manage Virtual Private Networks.
Procedure
- Download service provider certificates.
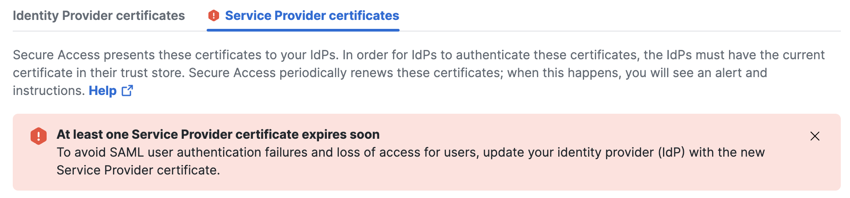
- View notifications about the expiration of Secure Access certificates that are deployed in SAML IdP integrations and VPN Profiles.
View Notifications About Expired Service Provider Certificates
- Navigate to Secure > Certificates > SAML Authentication > Service Provider Certificates.
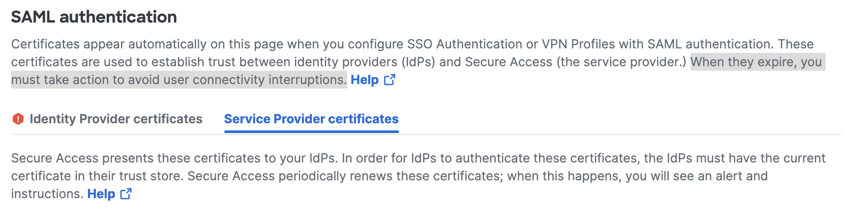
- Secure Access displays any notifications about certificates that may expire.
Download Web Security and Zero Trust Service Provider Certificates
- Navigate to Secure > Certificates > SAML Authentication > Service Provider Certificates.

-
Upload a new Secure Access service provider certificate to the SAML IdP.
a. For Automatic Configuration, copy the Automatic Certificate Updates URL and upload the Secure Access XML Metadata file to your SAML IdP.b. For Manual Configuration, in the list of certificates, click download on a certificate to save the certificate to your local system. Then, upload the certificate to the SAML IdP.
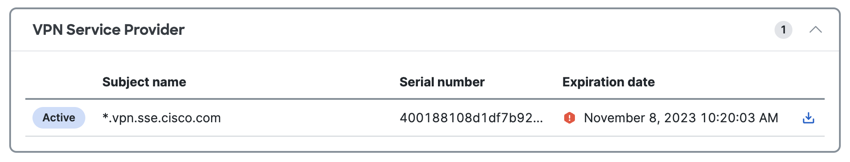
- Subject name—The certificate's common name, which defines the entity that manages the certificate.
- Serial number—The serial number of the certificate.
- Expiration date—The date when the certificate is no longer valid.
Download Virtual Private Network Service Provider Certificates
- Navigate to Secure > Certificates > SAML Authentication > Service Provider Certificates.

- For VPN Service Provider, click download on a certificate in the list to save the certificate to your local system. Then, upload the certificate to the SAML IdP.
- Subject name—The certificate's common name, which defines the entity that manages the certificate.
- Serial number—The serial number of the certificate.
- Expiration date—The date when the certificate is no longer valid.
Manage CA Certificates for SAML Authentication < Manage SAML Certificates for Service Providers > Manage SAML Certificates for Identity Providers
Updated over 1 year ago
