Components for Private Access Rules
You can create access rules by adding rule components that you or others have configured to a rule. Components described in this topic are reusable. You can use the same component (such as a source) in multiple rules, speeding and simplifying rule creation. For example, you can define a set of users as a source, then use the same source in an internet access rule and in a private access rule for the same set of users. Some components are profiles, or groups of settings bundled together that you choose as a unit when configuring a rule.
Table of Contents
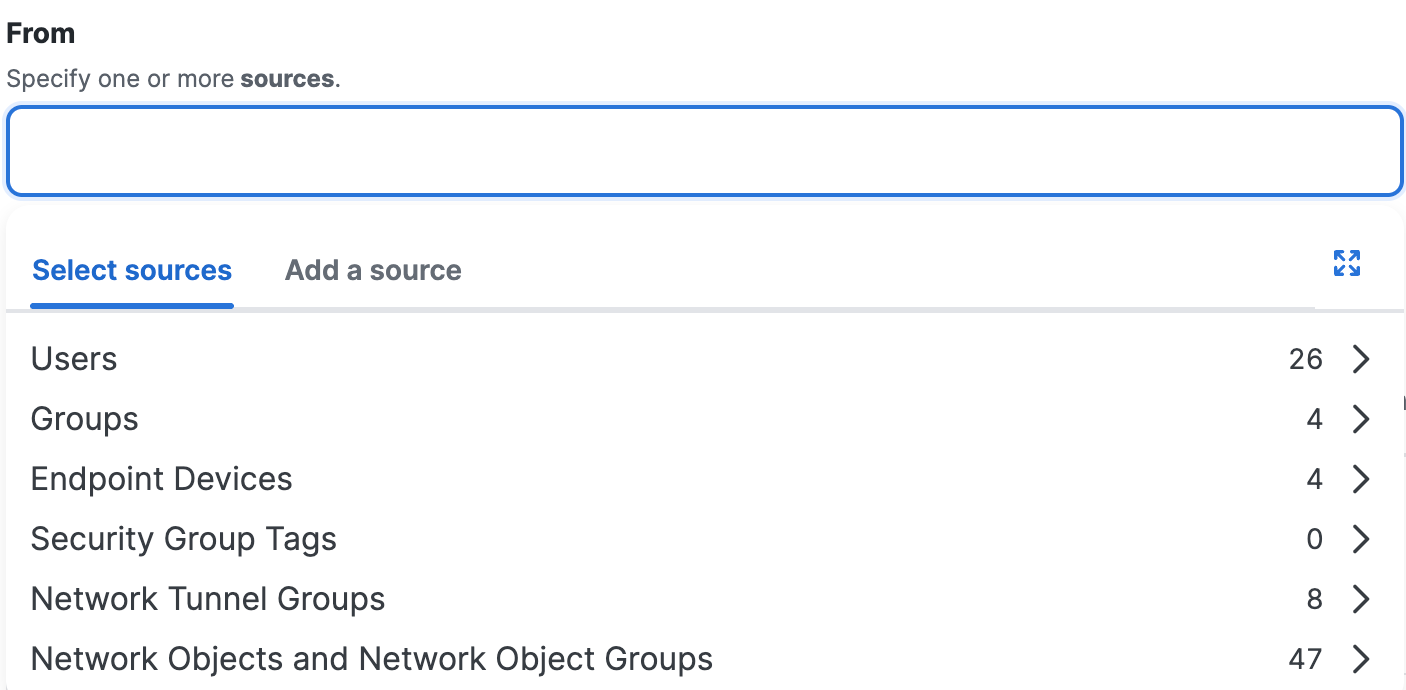
Sources
In a private access rule, add reusable source components. You can also specify sources by entering IP addresses, subnets, and ports, but these are not reusable source components. For more information, see About Configuring Sources in Private Access Rules.
-
Users
You can apply rules to the traffic for the users in the organization. -
User Groups
You can apply rules to the traffic for the groups of users in the organization. -
Security Group Tags
You can apply rules to traffic originating from IP addresses in network segments that include Security Group Tags. -
Network Tunnel Groups
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Tunnel Groups. -
Network Objects
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects. -
Network Object Groups
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects in Network Object Groups. -
Endpoint Devices
You can apply private access rule security controls to any endpoint device in Secure Access. Endpoint devices in Secure Access include the following:- Any user device provisioned from an on-premise Active Directory (AD) domain controller (DC) integrated with Secure Access.
- Any user device that has enrolled with Zero Trust Access on the Cisco Secure Client.
- Note: Be aware that rule-level security features (Configure Security > Intrusion Prevention (IPS) or Configure Security > Security Profile) are not compatible with access rules that have ZTA-enrolled devices as a source (Select Sources > Any Endpoint Device > ZTA Enrolled Devices). Configuring access rules with this combination is not recommended.
- Once enrolled or provisioned, user devices are available as sources in private access rules. You can select all endpoint devices in the organization, any AD device, any ZTA enrolled device, ZTA enrolled devices with specific host operating systems (macOS, Windows, iOS, or Android), or individual endpoint devices identified by device name.
For more information about the Cisco Secure Client and enrolling in Zero Trust Access, see Manage Zero Trust Access using Cisco Secure Client on Windows and macOS Devices.
For more information about AD device provisioning, see Manage Users, Groups, and Endpoints Devices.
Destinations
In a private access rule, add reusable destination components. You can also specify destinations by entering IP addresses, subnets, ports, and protocols, but these are not reusable destination components and have serious limitations. For more information, see About Configuring Destinations in Private Access Rules.
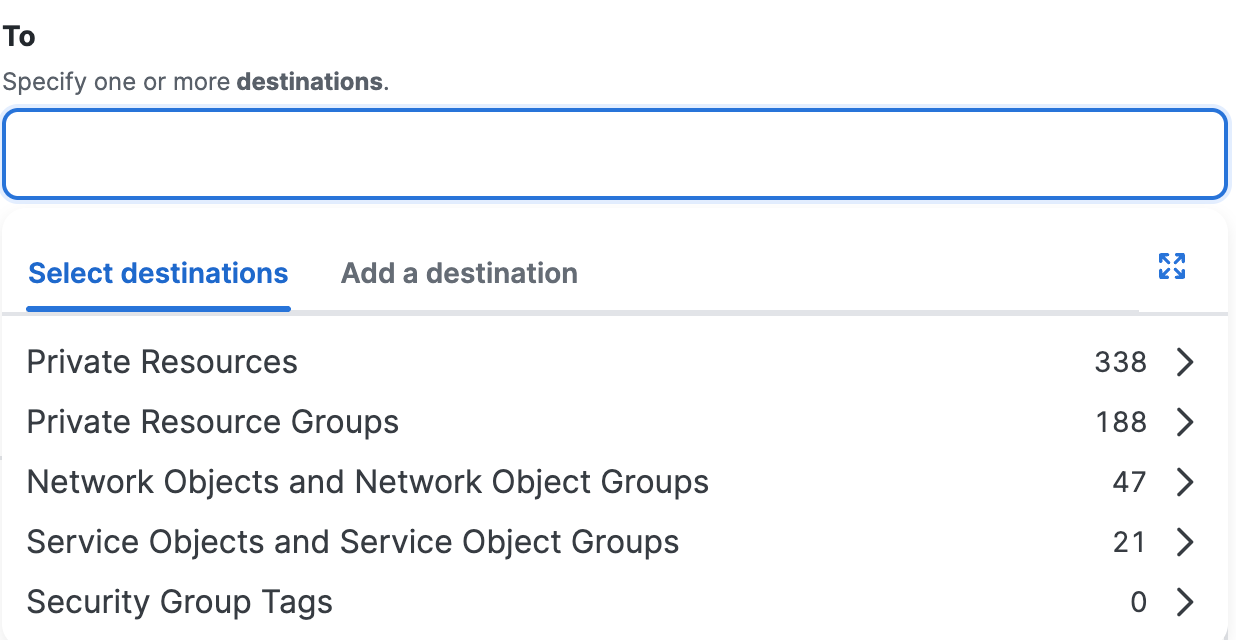
- Private Resources
- Private Resource Groups
- Network Objects
- Network Object Groups
- Service Objects
- Service Object Groups
Private Resources
Secure Workload routes traffic securely to applications and other resources on your network, based on Private Resource configurations.
Define connection requirements for applications in your data center, including resources on private clouds. You will also specify the types of connections permitted for each resource, including Zero Trust Network Access with and without installed client, and VPN. For more information, see Manage Private Resources.
Private Resource Groups
(Optional) After you add private resources, you can create groups of them for convenience and consistency, to easily apply an access rule to a collection of resources. For more information, see Add a Private Resource Group.
Network Objects
Network Objects represent IPv4 and IPv6 addresses, CIDR blocks, ranges of IPv4 addresses, or wildcard masks. Select the Network Objects on the access rules to apply security controls to the traffic on the networks. For more information, see Add a Network Object.
Network Object Groups
Select the Network Object Groups on the access rules to apply security controls to the traffic on the networks in groups. For more information, see Add a Network Object Group.
Service Objects
Service Objects represent a port, range of ports, protocol, or traffic on any protocols. Select the Service Objects on the access rules to apply security controls to the services. For more information, see Add a Service Object.
Service Object Groups
Select the Service Object Groups on the access rules to apply security controls to the traffic on the services in groups. For more information, see Add a Service Object Group.
Endpoint Posture Profiles (for Endpoint Requirements)
You can require endpoints to meet requirements such as operating system version, firewall, and disk encryption before connecting to a network or resource. These requirements are rule-matching criteria that determine whether a rule matches the traffic.
Endpoint requirements are defined in posture profiles. There are several types of posture profile, depending on the type of connection and characteristics of the end-user device:
- Client-based zero-trust posture profiles: For end-user devices on which the Cisco Secure Client is installed
- Browser-based zero-trust posture profiles: For end-user devices on which the Cisco Secure Client is NOT installed
- VPN posture profiles: For end-user devices that are connected to the network using remote access VPN.
When you configure a private resource, you will specify which of the above types of connections are allowed for that resource.
When you create a private access rule, you will specify a posture profile with device requirements for each type of connection allowed by the private resources specified as destinations in the rule.
You can create different posture profiles, each with a different set of requirements, then choose appropriate profiles for each rule.
You can specify default posture profiles for zero-trust access connections (client-based and browser-based.) Create a profile with the desired default endpoint requirements for each connection type, then specify the default profiles on the Rule Defaults page. See Rule Defaults and Edit Rule Defaults and Global Settings.
Posture profile options apply only to User and User Group sources.
VPN posture is evaluated when the user connects to the network, which occurs before access rules evaluate the traffic.
Endpoint posture is not evaluated for branch connections.
Security Controls
Private access rules have (and need) less varied security controls than internet access rules.
Intrusion Prevention (IPS)
Intrusion Prevention protects your network and assets by inspecting traffic for specified threat characteristics. Threat signatures are collected into collections called IPS Profiles.
When you configure an access rule, you can choose a predefined IPS profile such as Balanced Security and Connectivity or Maximum Security, or create a custom profile using Snort signatures that you choose. You can also choose whether to block or just monitor traffic that matches an IPS profile.
You can specify a default IPS profile on the Rule Defaults page that is automatically selected in each new rule. Default settings apply to both private access rules and internet access rules. See Rule Defaults and See Edit Rule Defaults and Global Settings.
See Manage IPS Profiles.
Security Profile, for File Inspection and File Type Controls
Prevent upload and download of malicious files or file types such as executables in traffic to private resources by configuring at least one security profile for private access and selecting that profile in private access rules.
See Security Profiles for Private Access.
Get Started With Private Access Rules < Components for Private Access Rules > Default Settings for Private Access Rules
Updated 3 months ago
