Secure Access Reporting
For general information about Cisco Secure Access's reports, see Get Started with Reports.
As a mobile device administrator, the key Secure Access reports for you to review are:
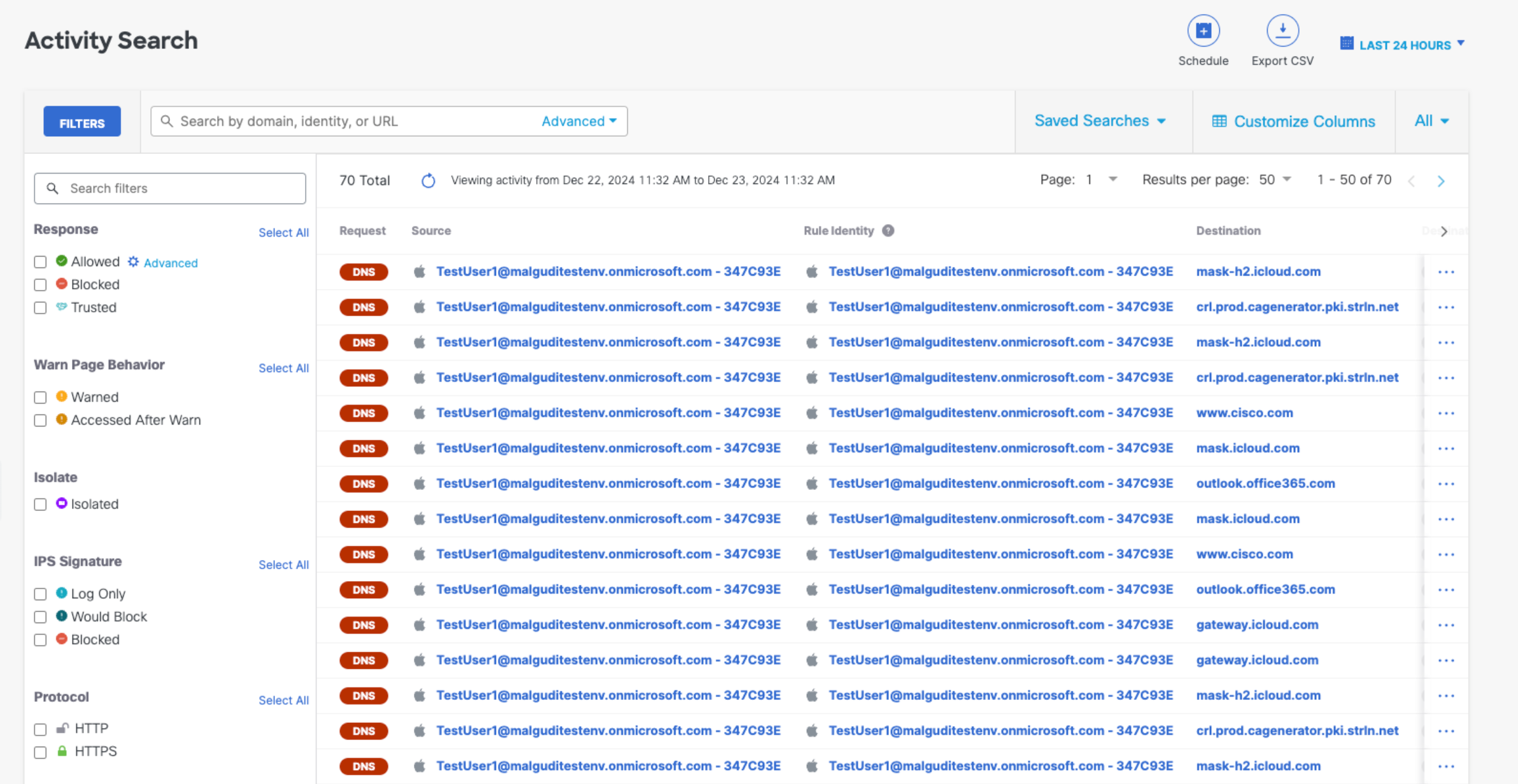
Activity Search Report
In real-time, you’ll see up to 30 days of activity for any device (including iOS), on any network (even cellular). You filter and search this activity based on response, protocol, identity type, security, or content category—even for 100,000s of devices, users, and networks. The Activity Search report lists all security (and non-security) related activity for your mobile device identities. For more information, see Activity Search Report.
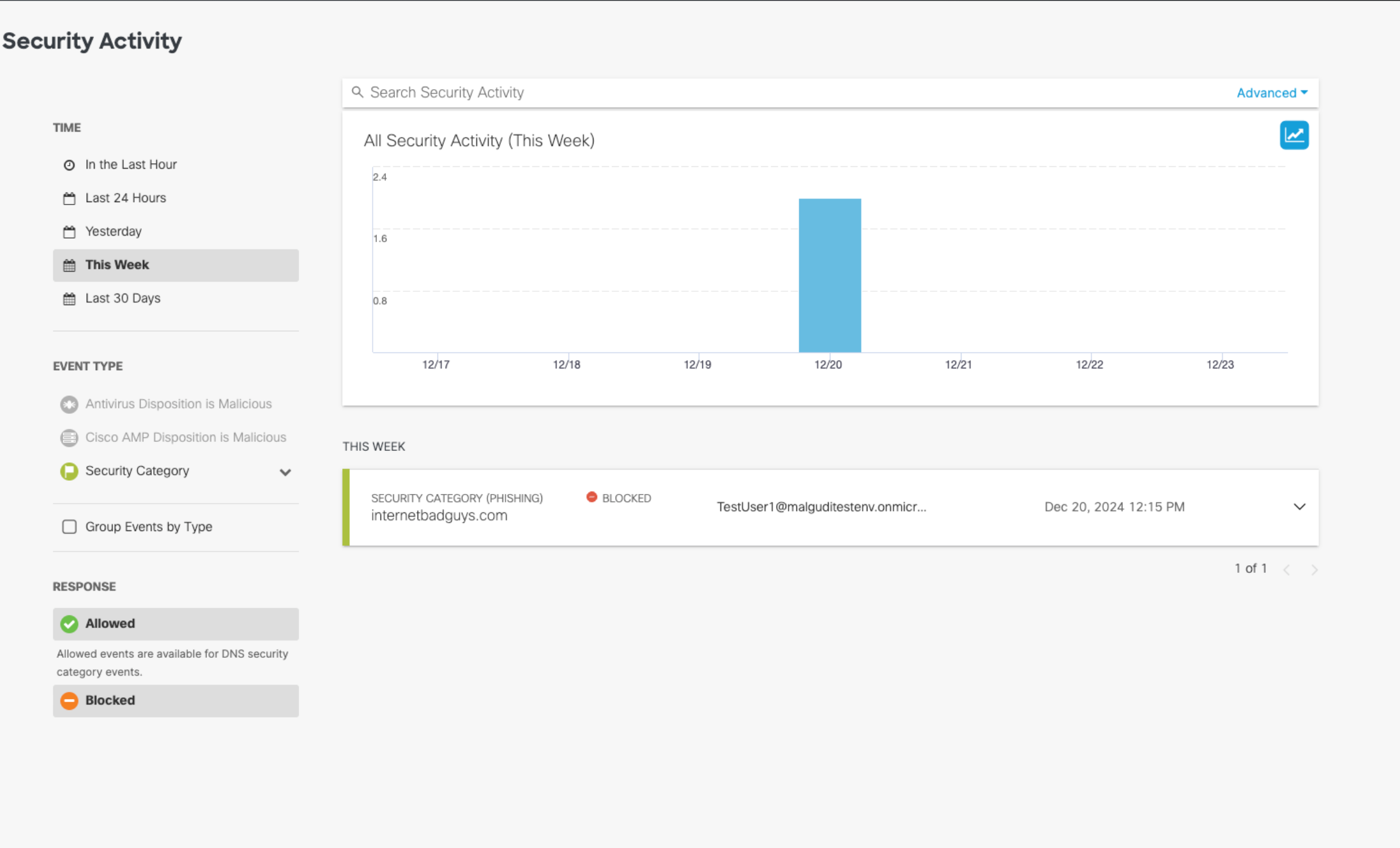
Security Activity Report
A common use case for Cisco Mobile Security is ensuring that iOS users don’t fall prey to phishing attacks. On mobile devices, users don’t verify links (due to no hover-over capabilities) and mobile-optimized websites often look different than regular websites, which makes it very difficult for users to identify fraudulent URLs themselves. The Security Activity report makes finding these examples in your mobile fleet easy. For more information, see Security Activity Report.
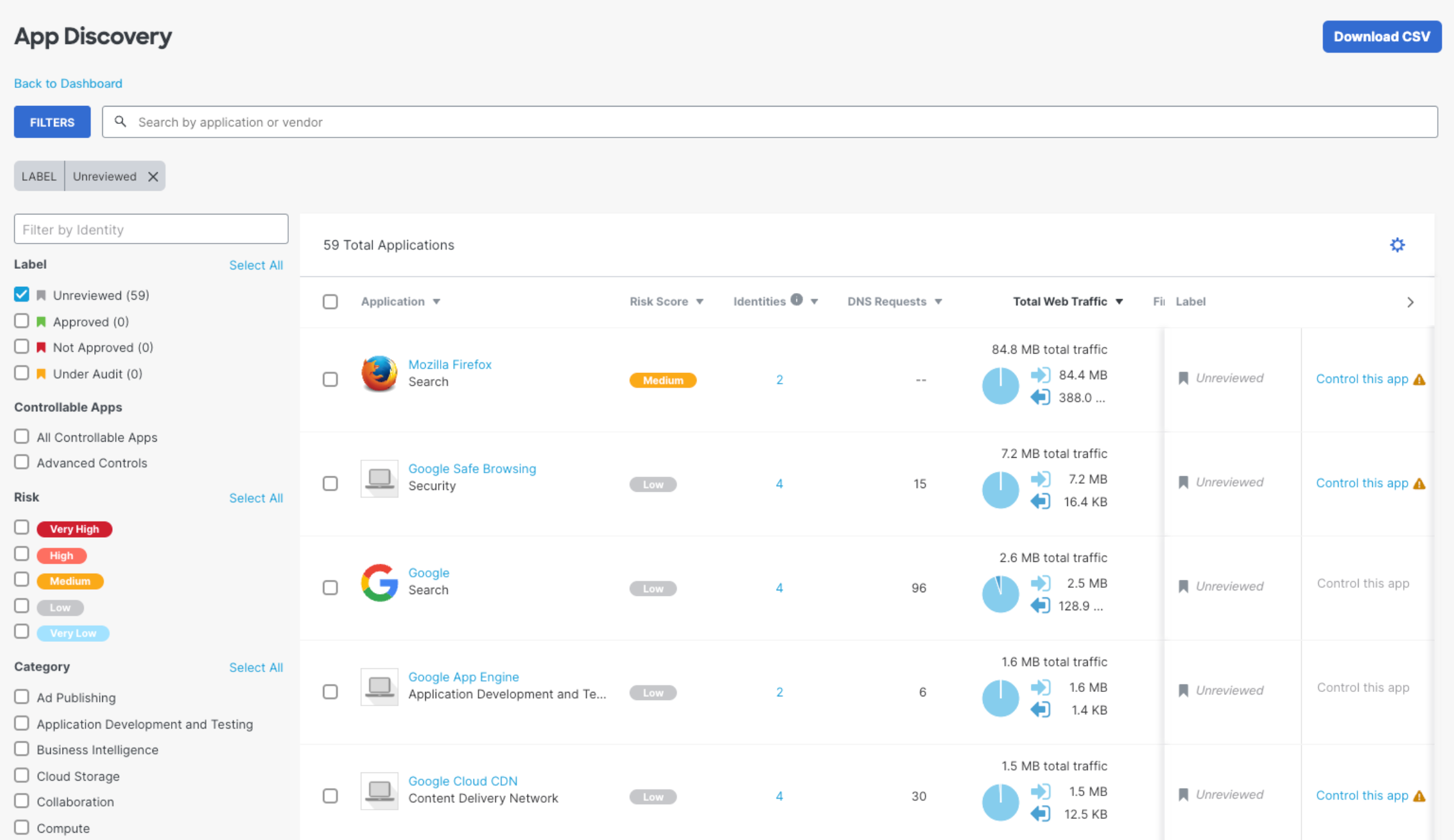
App Discovery Report
Another report that’s helpful for mobile administrators is the App Discovery report, which displays information about apps being used in your environment. This can help you when looking into why a user wants to use an app or service. For more information, see App Discovery Report.
Apply an Access Policy to Your Mobile Device < Secure Access Reporting >Anonymize Devices
Updated 2 months ago
