Verify and Monitor Context Sharing
This topic describes how to verify context sharing between Cisco ISE and Secure Access works for Security Group Tags (SGTs).
Table of Contents
Verify Context Sharing in Secure Access
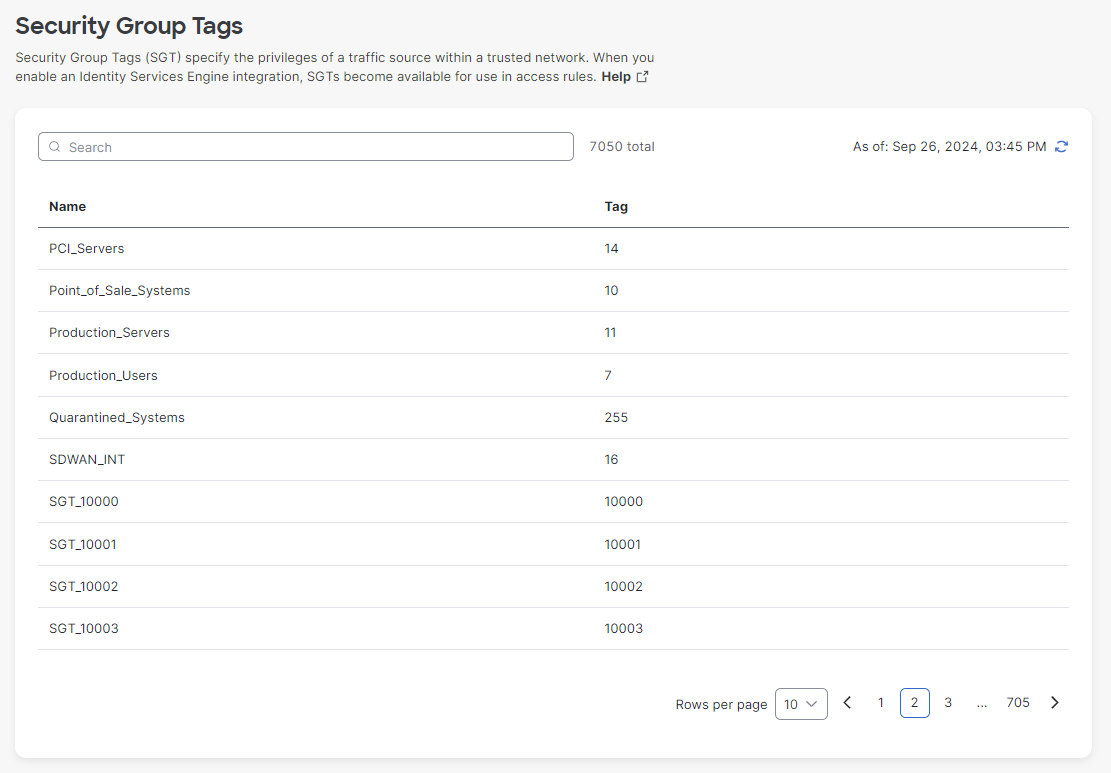
Security Group Tags (SGTs) are added to Secure Access as source resources when Cisco ISE is integrated with Secure Access. Once added, these SGTs can be used when configuring access rules.
- Navigate to Resources > Sources and Destinations > Security Group Tags to verify that the SGTs are shared as resources.
- Navigate to Secure > Policy > Access Policy.
- Click the Add Rule drop down and choose Internet Access to verify that the SGTs are shared as source objects for internet access rules.
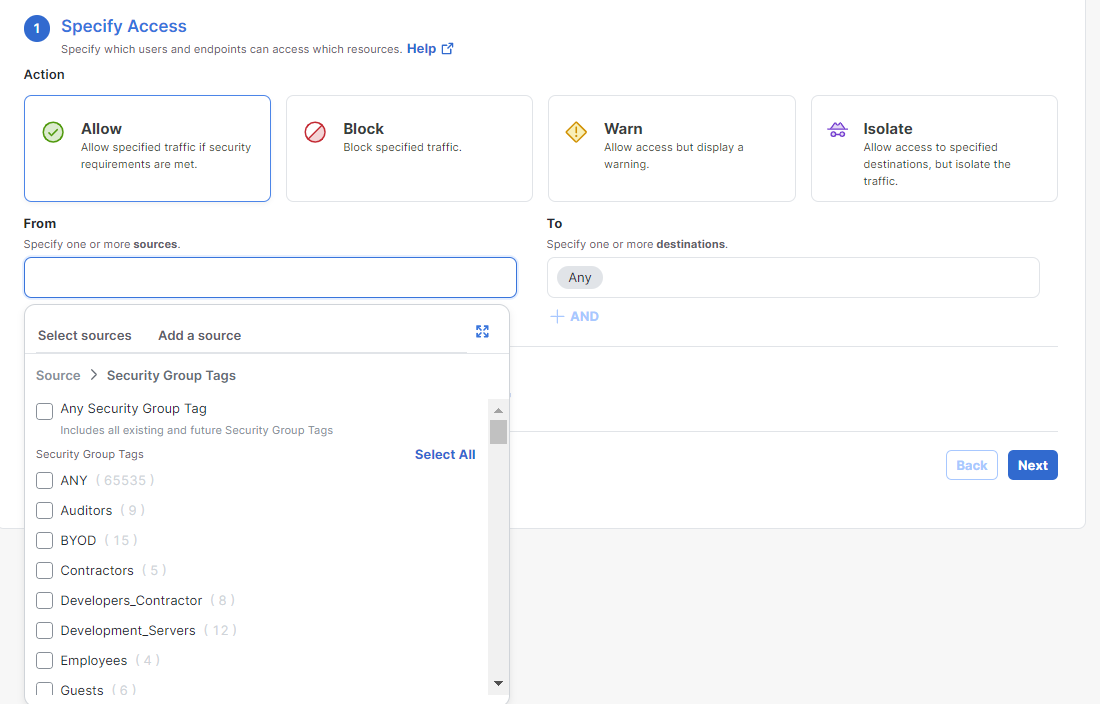
- From the Select sources drop down, choose Security Group Tags as a rule source.
From there, you can select Any Security Group Tag, which will include all existing and future SGTs in the rule. Alternately, you can select any (or all) existing SGTs for more granular internet access rules.
Activity Search in Secure Access
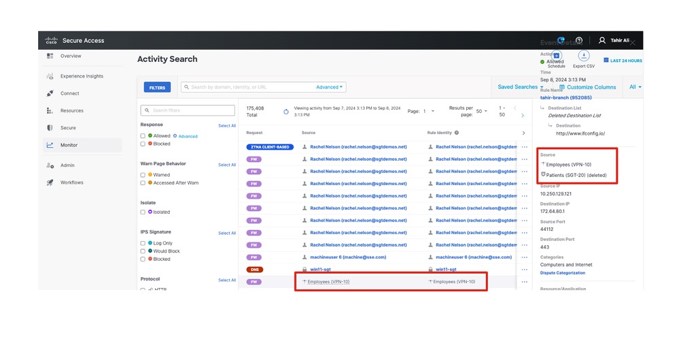
To search for activity from the sources in your environment over a selected time period, use the Activity Search report. The report lists all security (and non-security) activity for the sources reporting to Secure Access for the selected time period.
-
Navigate to Monitor > Reports > Activity Search. This takes you to the default view of the Activity Search report, which lists all of your identities and the internet requests or traffic events for your organization, tracked over time.
-
Hover over individual column values to apply it as a search filter or to exclude it from the search.
Related Information
For more information:
Integrate Cisco ISE with Secure Access < Verify and Monitor Context Sharing > Integrate Catalyst SD-WAN with Secure Access
Updated 14 days ago
