Connect Active Directory to Secure Access
Cisco Secure Access Active Directory (AD) Connector integrates Secure Access with users and groups provisioned from Microsoft Active Directory. Before you can provision users and groups from Active Directory, you must connect your instance of AD to Cisco Secure Access.
Table of Contents
- Prerequisites
- Step 1 – Choose a Provisioning Method
- Step 2 – Register a Domain Controller or Domain in Secure Access
- Step 3 – Install the Secure Access AD Connector
- Step 4 – Configure Updates on Deployed AD Connectors
- Step 5 – Verify That the Connector Syncs with Secure Access
- Specify AD Groups of Interest
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- Connector Server
- Outbound Network Access to Secure Access
- Connector Account
Connector Server
You must configure a server that is a member of the AD domain with the following environment:
- Windows Server 2012, 2012 R2, 2016, 2019 or 2022 with the latest service packs and 100MB free hard disk drive space.
- .NET Framework 4.5 or newer.
- If a local anti-virus application is running, allow the OpenDNSAuditClient.exe and OpenDNSAuditService.exe processes.
You may deploy the Secure Access AD Connector directly on the domain controller. In this case, the domain controller must meet all prerequisites. Only one AD Connector is required to provision users and groups from an AD domain, with an optional second connector for redundancy if required.
Outbound Network Access to Cisco Secure Access
The Connector server requires the following outbound access:
- 443 (TCP) to api.opendns.com for syncing.
- Access to additional URLs on port 80/443 (TCP) may be required for Windows to perform Certificate Revocation List and Code-Signing checks. For a complete list of ports, see Communication Flow and Troubleshooting.
- 443 (TCP) to disthost.umbrella.com (for downloading upgrades).
If you are using a transparent HTTP web proxy, ensure that the above URLs on port 80/443 are excluded from the proxy, and not subject to authentication.
Connector Account
The connector deployment requires that you to create a new user account in the AD domain. This account should have:
- The logon name (sAMAccountName) set to
OpenDNS_Connector. You can login with a custom username that has the required permissions. - 'Password never expires' selected
Note: Passwords must not include backslashes, quotations (single or double), greater-than or less-than chevron brackets (< >), or colons. - ‘Read’ and ‘Replicating Directory Changes’ permission assigned. Alternately, you can make the connector account a member of the built-in ‘Enterprise Read-only Domain Controllers’ group which will automatically assign these permissions.
Note: The Connector does an initial synchronization of the AD structure to Secure Access. After the sync, it detects changes to the AD structure and communicates these changes only. The detection of changes requires the ‘Replicating Directory Changes’ permission, so the Connector cannot function without this permission. The ‘Replicating Directory Changes’ permission is different from the ‘Replicating Directory Changes All’ permission which enables retrieval of password hashes. The Connector does not read password hashes and hence does not require the ‘Replicating Directory Changes All’ permission.
Step 1 – Choose a Provisioning Method
- Navigate to Connect > Users and Groups > Users and click Provision Users or Connect > Users and Groups > Groups and click Provision Groups.
- For Provisioning Method, click Active Directory.
- Click Next.
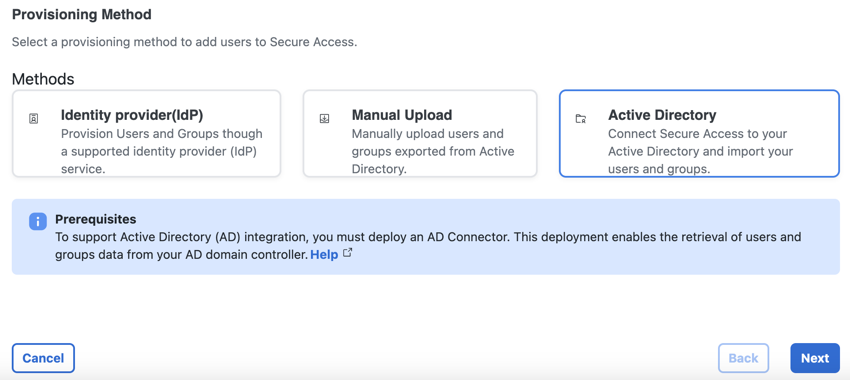
Step 2 – Register a Domain Controller or Domain in Secure Access
Choose the AD component type and configure the component to sync with Secure Access.
Active Directory integration requires that you register an AD domain controller or AD domain in Secure Access. The Connector performs an LDAP sync against this domain controller or domain to retrieve the users and groups. The Connector server must be able to communicate with the domain controller on ports 389/636 over TCP for LDAP sync or LDAP over SSL.
The Connector can only retrieve users and groups from a single domain controller. If you register multiple domain controllers in Secure Access, the Connector only attempts to perform an LDAP sync against the first domain controller in the list. Ensure that the domain controller you are registering is not subject to any AD replication delays. Read-only Domain Controller (RODC) registrations are supported for retrieval of users and groups.
If you need to periodically bring down your domain controller for maintenance or updates or your domain controllers are behind a load balancer that does not support LDAP queries, we recommend that you register the domain instead.
Register a Domain Controller
- Choose Domain Controller to register the AD domain controller component.
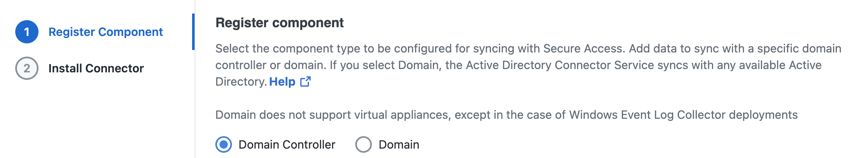
- Enter the hostname, internal IP address, and domain of the domain controller. Choose an Active Directory tag to identify the AD component.
The Active Directory connector attempts to connect to your newly added domain controller. If all the required permissions have been configured, you should not experience any issues. If there are errors, review Prerequisites or contact Support.
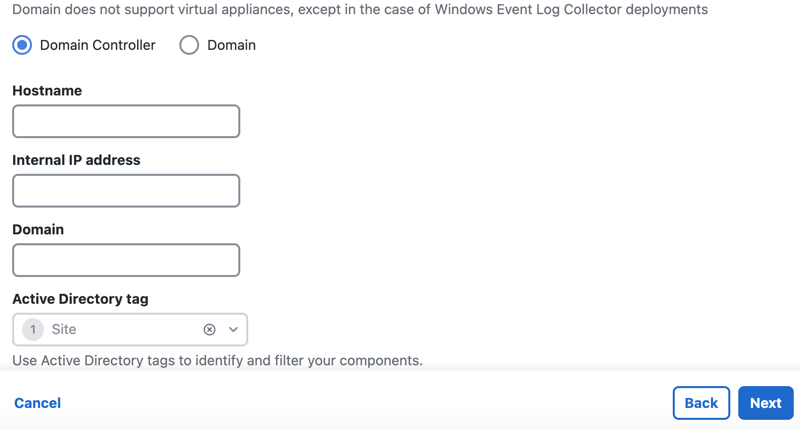
- Click Next and then follow the instructions in Step 3 – Install the Secure Access AD Connector.
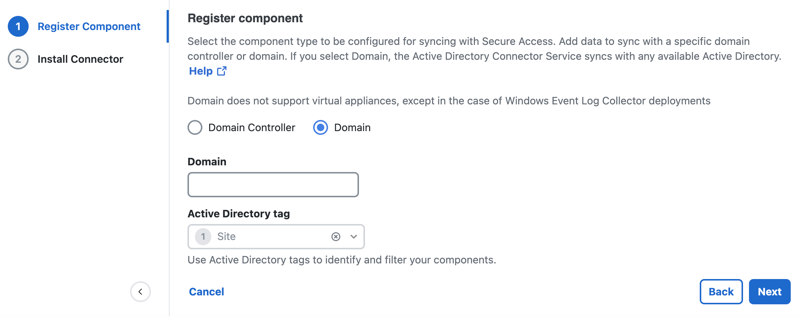
Register a Domain
- Choose Domain to register the AD domain component.
- For Domain, enter the domain name. Choose an Active Directory tag to identify the AD component.
- Click Next, and then follow the instructions in Step 3 – Install the Secure Access AD Connector.
Step 3 – Install the Secure Access AD Connector
Download and install the Secure Access AD connector on your server.
- On the server that you have configured to deploy the Secure Access AD Connector, sign in to Secure Access.
- Navigate to Connect > Users and Groups > Users and click Provision Users or Connect > Users and Groups > Groups and click Provision Groups.
- For Provisioning Method, click Active Directory and choose the AD domain component. Click next and then click Download to save the AD connector to the local system.
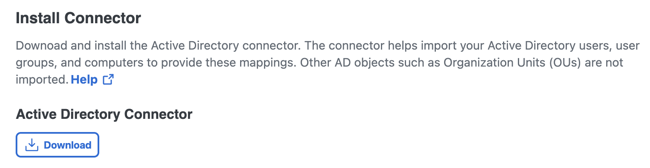
Note: You must download the ZIP file to the local machine where you plan to run it or copy it locally from another machine. We do not recommend that you install the AD Connector from a network drive or run the setup.msi directly from the compressed file.
- As an administrator, extract the contents of the ZIP file you downloaded to a folder and then navigate to that folder.
Note: If you run the AD Connector installer files from the root directory of your device, you may encounter installation errors. - Run setup.msi.
- Enter the username of the Connector user (OpenDNS_Connector or custom username) and the password. See Prerequisites.
- Follow the prompts in the setup and when finished, click Close.
- Return to Secure Access. Verify that the connector is in the same Secure Access Site as the domain controller or domain that it needs to communicate with.
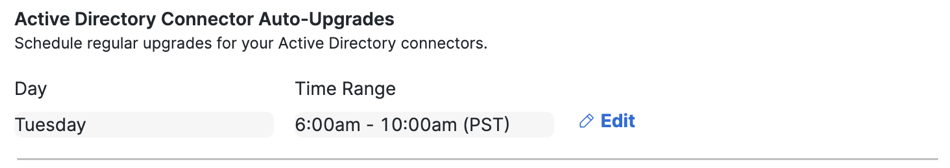
Step 4 – Configure Updates on Deployed AD Connectors
Schedule the date and time that Secure Access updates the Active Directory Connector software on your deployed AD Connectors. When scheduled, Secure Access checks if the AD Connector has the latest version of the software. If a new version is available, Secure Access removes the installed AD Connector software from your systems and deploys the latest version of the AD Connector.
- Navigate to Connect > Users and Groups > Configuration Management.
- For Provisioning, expand Active Directory.
- Navigate to Active Directory Connector Auto-Upgrades, and then click Edit.
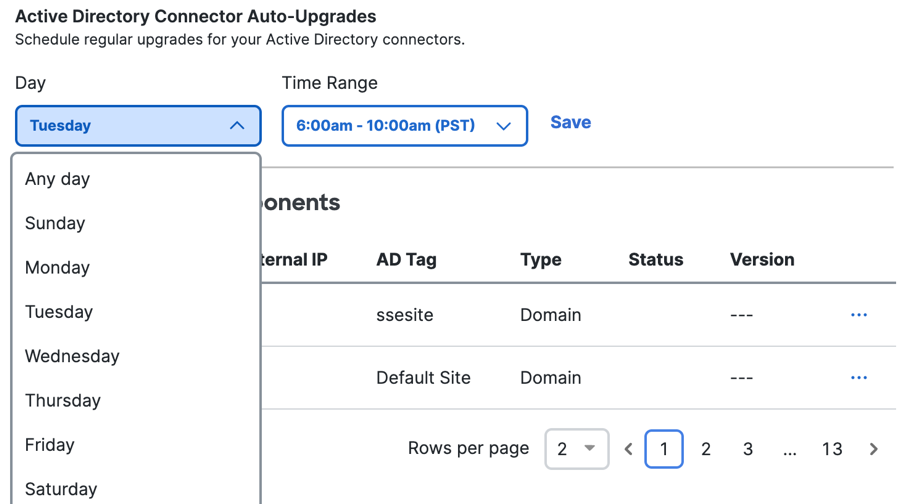
-
For Day, choose the day of the week to update the AD Connector software.
Note: The default Day is Any day—On every day of the week, if a software update is available, Secure Access attempts to redeploy the AD Connectors with the latest version of the software.
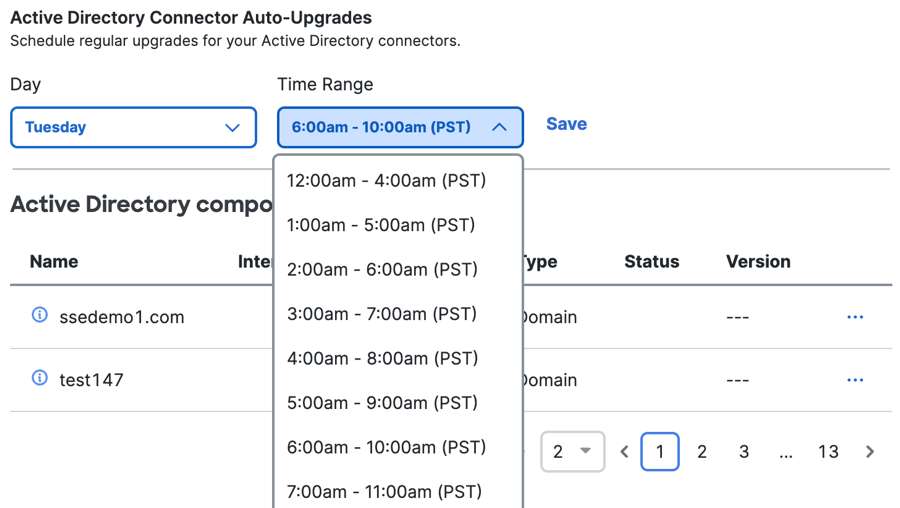
- For Time Range, choose the four-hour time period to update the AD Connectors on the scheduled day.
Note: The default Time Range is 2:00 am - 6:00 am PST.
Step 5 – Verify that the Connector Syncs with Secure Access
- Navigate to Connect > Users and User Groups, and then choose Configuration Management.
- Expand Active Directory to view your deployed domain controllers, domains, or AD Connectors.
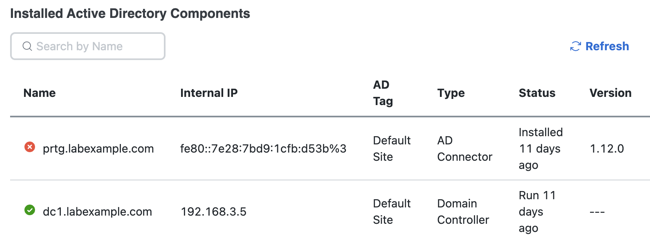
- Name—The hostname of the Windows computer where you installed the AD Controller.
- Internal IP—The internal IP address of the AD Controller.
- AD Tag—The unique label that identifies the AD component.
- Type—The type of AD component, either Domain Controller or Domain.
- Status—The state of the AD component.
- Version—The version of the AD component.
The status of your domain controller and connectors should change from Inactive to Active (green). If the configured domain controller or connectors are not active after a period of time, contact Secure Access Support.
It can take up to four hours for large numbers of AD user, computer and group objects to synchronize for the first time. During this time, the connector status icon may appear as red until the initial sync is complete. After the sync completes, the connector status icon is labeled as "Active" (green).
Seeing your groups listed means the domain controllers have automatically synchronized user and computer group memberships with Secure Access through the connector successfully. Any subsequent changes should also sync successfully.
Note: If the connector does not appear in Secure Access and port 443 is confirmed to be open to api.opendns.com, crl4.digicert.com, and ocsp.digicert.com, the connector server may be missing the DigiCert CA. To confirm, visit https://api.opendns.com/v2/OnPrem.Asset. If a certificate error is presented, download and install the latest DigiCert Global Root CA from DigiCert and restart the Connector service. If it does not appear, contact Support.
Specify AD Groups of Interest
Optionally, you can specify AD Groups of interest for the purpose of policy creation in Secure Access.
- Identify the AD groups of interest. Users and computers belonging to these groups are synchronized to Secure Access.
For each sub-tree, only the parent group needs to be specified. All AD groups, users, and computers that are part of this parent group are automatically included.
Note: If Selective Sync is enabled, AD Users and Computers that are not members of Groups specified in CiscoUmbrellaADGroups.dat or their subgroups are not synchronized to Secure Access and are completely exempt from Secure Access policy rules and reports. - Create a CiscoUmbrellaADGroups.dat file in the C:\ drive of each machine where the connector is installed.
The connector only reads the C:\CiscoUmbrellaADGroups.dat file. If the file is incorrectly named or is not present in the C:\ drive, all groups are imported to Secure Access. - List the AD groups that need to be synchronized in
distinguished name (DN)format in this file.
Supported Organizational Units
CN=My Group,OU=Organizational Unit,DC=sample,DC=local
Unsupported Organizational Units
OU=My OU,OU=Organizational Unit,DC=sample,DC=local
Sample File Entries
CN=Engineering,CN=Builtin,DC=ciscoumbrella,DC=com
CN=Sales,CN=Builtin,DC=ciscoumbrella,DC=com
CN=Marketing,CN=Builtin,DC=ciscoumbrella,DC=com
- Ensure that there are no blank lines anywhere in the file.
Note: If you are running multiple connectors, the file C:\CiscoUmbrellaADGroups.dat should be present on each system running the connector and should be identical on each system.
Total Number of Groups Selected for Synchronization
The total number of groups selected for synchronization—groups specified in the selective sync file and all their subgroups—should not exceed 15,000. Also, these groups should not be nested within more than five OU levels. Selective synchronization fails in both cases. If either of these requirements cannot be met, the selective sync file should not be used so that a full AD tree synchronization can be done instead.
Provision Users and Groups from Active Directory < Connect Active Directory to Secure Access > Connect Multiple Active Directory Domains
Updated 4 months ago
