View Security Events
The Security section of the User Dashboard displays the allowed and blocked events that occurred when a user's device attempted to access an organizational resource using Zero Trust Access and the rules that triggered the events.
Events are "allowed" when the user and the user's device meet all defined criteria in the security rule. For more information on setting up security rules, see Manage the Access Policy .
Procedure
- From the left menu, navigate to: Experience Insights > Management.
- On the Endpoints summary page, scroll down to the Endpoints list and click a user name.

- On the User Dashboard, scroll down to the Security section.
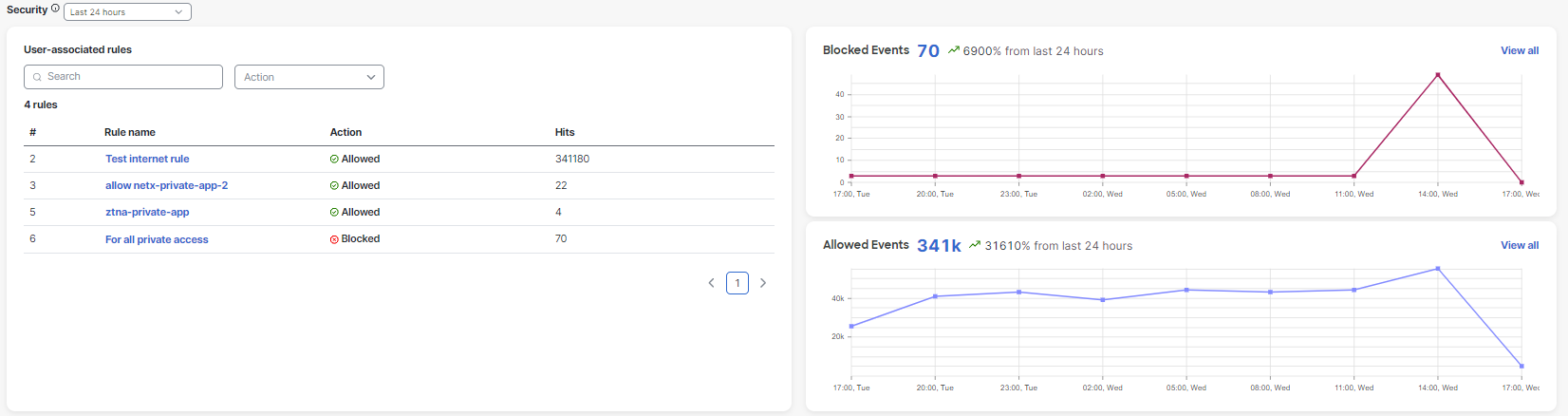
- The User-associated rules section displays the Zero Trust Access security rules that were triggered by the user's device in a specified period, sorted by descending order of frequency.
- Note: When an event is both allowed and blocked, its user-associated rule will display as two separate entries in the table.
- The Blocked Events and Allowed Events graphs display the combined total of blocked and allowed Zero Trust Access events for the user's device within the specified time period.
- To see a comprehensive view of events that are associated with the user, click View all .
View User Dashboard > View Security Events> View Device Path to Secure Access
Updated 16 days ago
